Do I Need IPS ?
-
@oznet What do you mean infected?
I assume there is an A/V application installed.
If a more MSP or Enterprise environment there is security apps like Sentinal One or Huntress that may catch it.I suppose an IPS could get lucky and spot an issue from LAN -> WAN but I certainly wouldn't rely on it.
If your "infected" machine is calling out to a domain thats on 443..then what?Most modern security platforms will have MITM enabled so that the firewall could drill down into the URL and see what resource is being requested. From there based on signatures or policy that site gets denied. Thats the power of a MITM + ThreatPrevention tool.
As i stated, pfsense cant do that. Squid and Snort are considered two independent packages. If there was some way to pass decrypted site information to Snort then i would say, yes, absolutely snort is needed. -
@michmoor infected I mean compromised some kind of malware and the AV did not detect it, if IPS is not needed then I am ok with that, just wanted to explore this a bit, I am not a firewall pro just a home user and thank you for your help!
-
@michmoor
I am a home user thinking of using SNORT. I was thinking of the issue with using port 443. Is there a way to know the connection is happening with SNORT? I don't remote into anything anymore as I am an old retired network guy. Will SNORT list the 443 connection whether you use the LAN or the WAN side for SNORT? I know it is outbound traffic but I might I be able to block it on the firewall?Speaking of SNORT, is it better to use the WAN or the LAN. I think I have read on here it is better to use the LAN side. I have a Cisco L3 switch running my VLANs and no vlans are defined to pfsense. If I use the LAN side for SNORT will it read deep enough into the packet to know where the packet originates from or will it all show the L3 switch as the originator?
-
@coxhaus @oznet
Use Suricata not Snort, sounds like Snort may die off on pfSense unless someone takes over the next version.Neither can scan HTTPS traffic so malware can just use that to bypass.
Running on LAN it will show you the LAN device’s IP. It runs outside the firewall so on WAN it will scan everything the firewall blocks.
-
Use pfBlocker and the right lists instead.
You got a very powerfull protection, if you use the right lists.
It is also significantly more efficient than Snort. -
@oznet said in Do I Need IPS ?:
laptop that is infected while on a public wifi or android phone
When a PC/laptop/Phone/pad/whatever connects to a network, it will default to the Public (network) mode.
You've seen this already : on a Windows PC, when you connect the very first time to a network that the device didn't used before, you can chose between a private (or company) network, or a public network.
When 'private' is selected, your device can access other devices in the same connected LAN, and other devices in the same LAN can use resources that are shared on your device, if there are any.
A public : network : only connections to the gateway (Internet traffic) are created, only traffic is end to the gateway, and only traffic coming from the gateway is accepted.So : In a way, some random public Wifi network is more secure then the network you share at home.
The unique and final factor that can make the difference : the user using the device.
If he downloads and executes a trojan, it was because he took action to do so.@oznet said in Do I Need IPS ?:
a data service and then brought back onto the lan? Would IPS then be beneficial?
Good point !
Ones a device is infected, and it is connected to your local private 'trusted' network, then the devices on this (your) LAN can connect to each other without passing through pfSense. So, 'IPS' on pfSense that doesn't see the inter LAN traffic is pointless.
You could even power down pfSense : the LAN still works fine (for some time).You might think that Suricata (or Snort) or any IPS can help you ....
When you investigate this question, you'll reach the opposite side : you don't want IPS to happen.
IPS is means : make the encrypted data stream readable. You need, among others, to be able to 'undo' TLS traffic (== the encrypted data stream) coming from any LAN device to a remote server, analyze it, and when ok, 'redo it' an d send it of. Then, the return TLS stream (for example, from your bank) needs to be 'undone', checked, and when ok, 'redone' to be sent to your PC.While your are doing you best to make the MITM to happen, so you can do IPS, you also know that thousands of network engineers/expert are working hard to make your task as hard as possible.
After all, if you could do this at home, then every 3 letter agency could do with the snap of a finger same. Let's image this : they (officially) can't - neither your ISP, nor your neighbor.They told you 'https' == safe. It's time to know why this is actually true

Home user, or not, go have a look at what TLS, or more known as https (== web traffic using TLS) actually is. It's 2023 these days, basic, easy, fast to understand info is now available @Youtube.
I'll promise you : it's worth the effort.In the beginning, and at the end : it's far easier to :
You start with : Explain, teach, make clear, to your network users what the risks are.
At the end : Don't allow 'dangerous' devices (==people) entering your network. I mean : it's ok that people don't want to cooperate, but they are using 'your' network, so you have something to say. -
@oznet do you have experience using an IPS/IDS - its a bit more complicated then just enabling it.. If you want to enable it in monitor mode.. Sure go ahead - there is a lot of config and maint required to run a successful IPS/IDS..
I have run them for many years professionally, and I don't run one on my home network. Its a bunch of work, for very little return.
-
Agree wholeheartedly with @johnpoz here. On a home network, an IPS requires a lot of upfront knowledge to configure and a lot of labor to maintain. Because of the magnitude of encrypted traffic these days, the amount of effort involved with the IPS/IDS vastly overshadows any potential gain in my opinion (in a home network). I say this as the package maintainer for Snort and the package creator for Suricata
 . If you just want to play around with IPS/IDS to learn, then have at it. But just realize there is much, much more effort involved with IPS/IDS than there is with using an anti-virus client.
. If you just want to play around with IPS/IDS to learn, then have at it. But just realize there is much, much more effort involved with IPS/IDS than there is with using an anti-virus client.And as others have mentioned, if someone brings an infected machine back into your local LAN, an IPS running on the firewall could likely not even be aware of the traffic between two hosts on the same LAN as that traffic will be directed by the L2 switch from one port to another on the switch and bypass the firewall's LAN port completely. Only if the malware attempted some kind of network scan would it perhaps "trip" the IDS/IPS on the firewall's LAN port (as that port IP was targeted during a scan). The IPS/IDS could potentially see traffic outbound from the LAN as that would be given to the firewall's LAN interface to route. But encryption will be an obstacle here. For web and email traffic the IDS/IPS has zero visibility into payloads and thus only has the little bit of IP header info to work with.
-
@bmeeks said in Do I Need IPS ?:
Agree wholeheartedly with @johnpoz here. On a home network, an IPS requires a lot of upfront knowledge to configure and a lot of labor to maintain.
Hi Bill,
Long time no "see", but I hope all is well.Very true, but I still love this approach (if I can call it IPS stuff), sure the yes the learning curve can be steep, but let's not take away anyone's enthusiasm.
When you're pushing this in a production environment, you're past a home and/or VM/test system... (I hope so)
(I hope so)BTW:
I'm still impressed by your work
-
@DaddyGo said in Do I Need IPS ?:
sure the yes the learning curve can be steep, but let's not take away anyone's enthusiasm.
I don't mean to discourage someone who wants to try it out for the learning experience, but there are a fair number of users that install it without fully understanding what it is and how to maintain it. They then post here with frustrations because something is blocked. Unintended blocking will happen a lot with a typical home setup unless the admin is skilled in the craft of IDS/IPS.
But this is also a problem with all of the packages that can "block things" such as Snort, Suricata, pfBlocker, SquidGuard, etc. I am always amazed at the posts where someone installs one or more of those packages on their pfSense and then posts asking "... why is pfSense blocking xyz site?". It makes me want to whack them on the side of their head and ask "do you think it could possibly be one of those packages you installed that are intrinsically designed to block stuff? Have you checked if one of those packages is blocking the desired traffic?"
 . And many times it takes two or three rounds of back and forth questions to pry out of them the tidbit that they have indeed installed one (or even several) of the blocking packages.
. And many times it takes two or three rounds of back and forth questions to pry out of them the tidbit that they have indeed installed one (or even several) of the blocking packages. -
@bmeeks The pros and cons of making a product available to the masses.
The solution would be to gatekeep this behind a VAR and high cost support packages :) -
@michmoor sounds like I will fore go the IPS aspect and stick to blocking ads
-
DO IT!!! IPS/IDS both have fun setting it up too,
I added some alias rules to do not block lists as SNORT takes some time to fine tune, once it's tuned its great!!
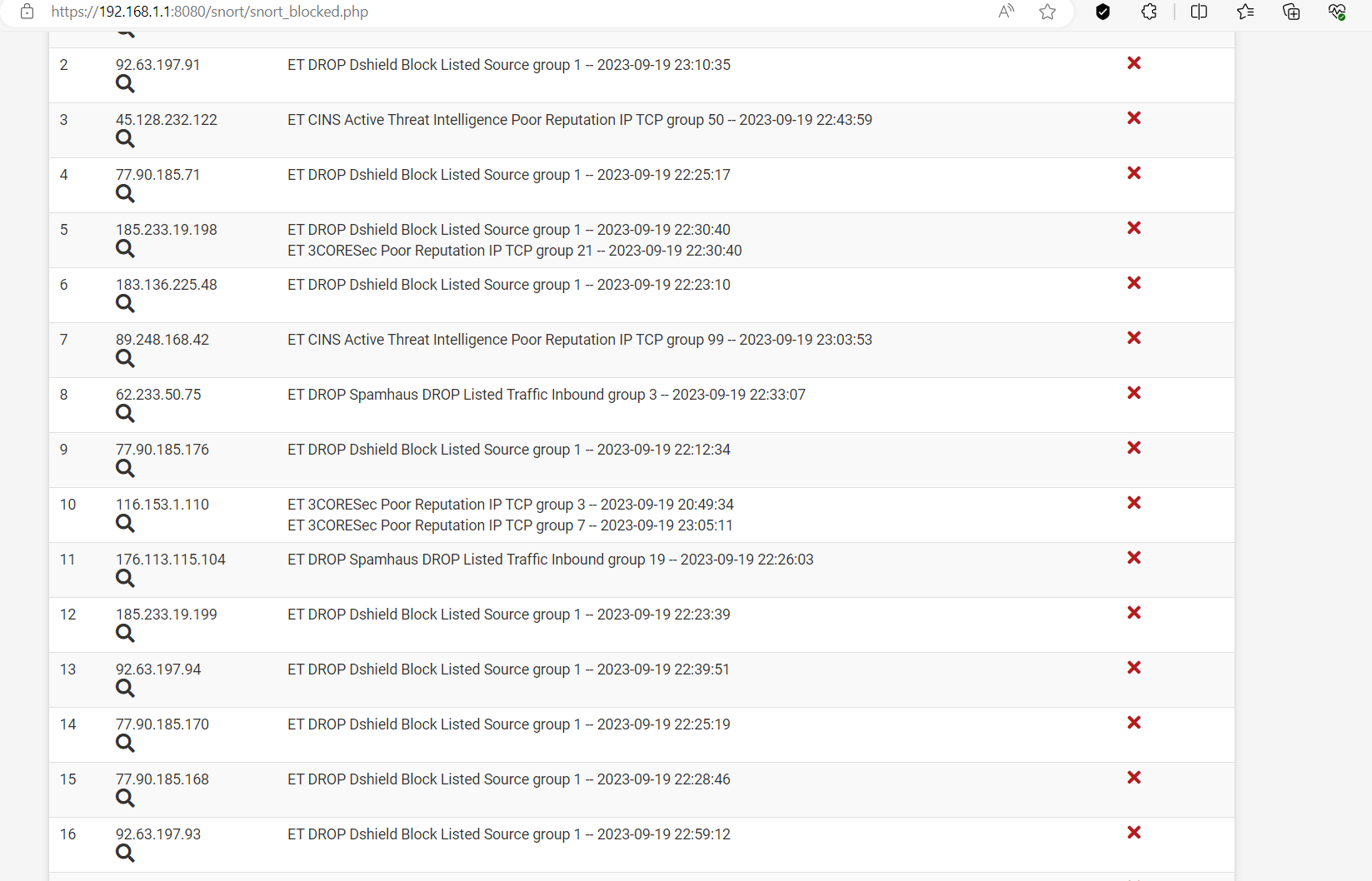
83 plus blocks in 1 hour of invasive actors.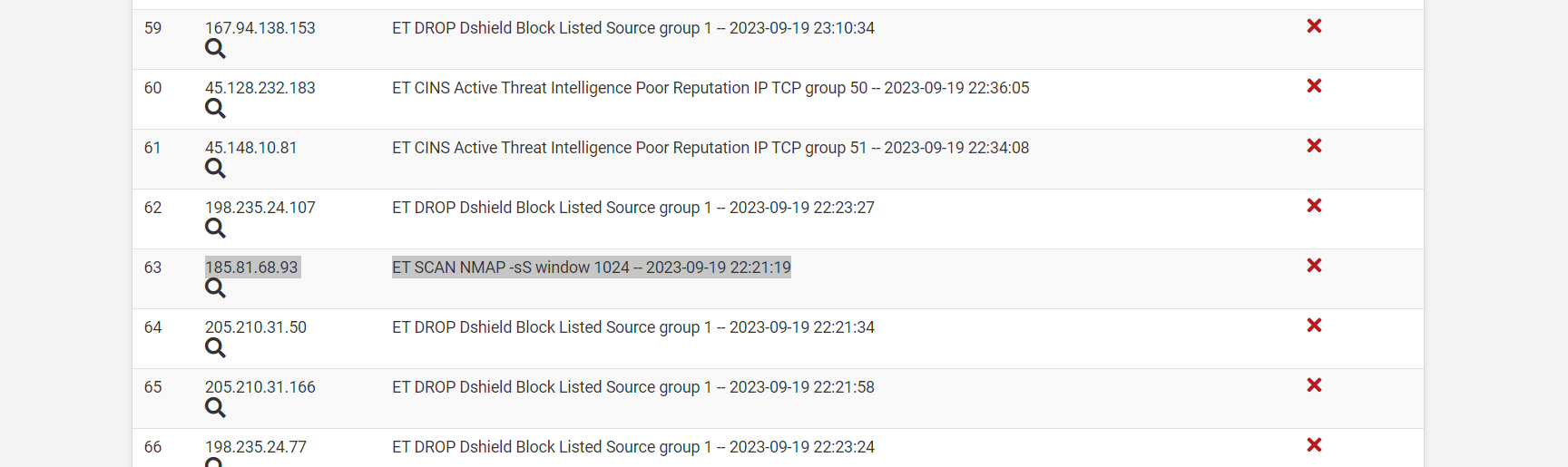
Mine even does auto scan blocking, that was fun to set up as roblox like to scan when it starts up.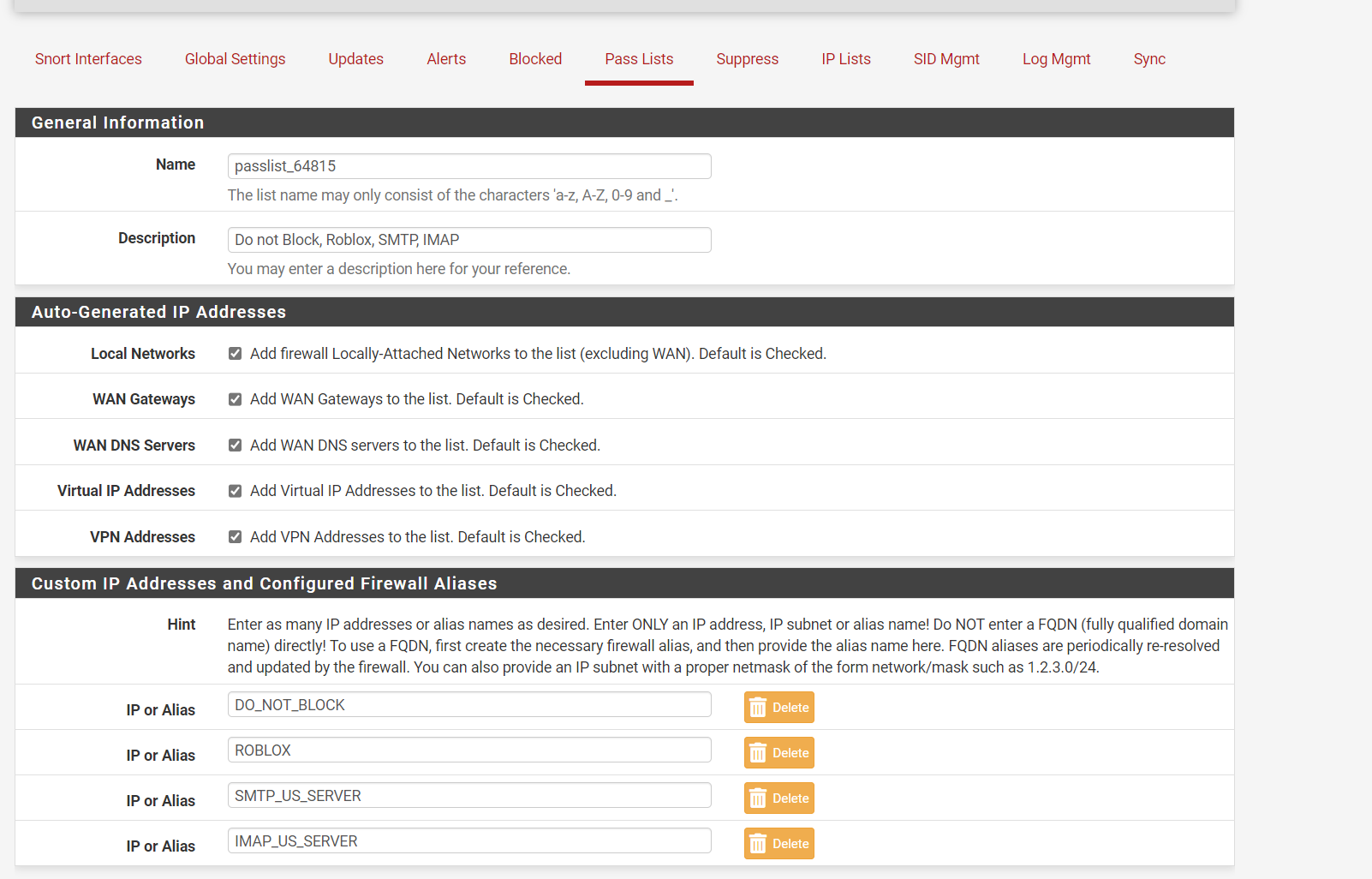
I have a nice ACL for it, plus a ignore scans set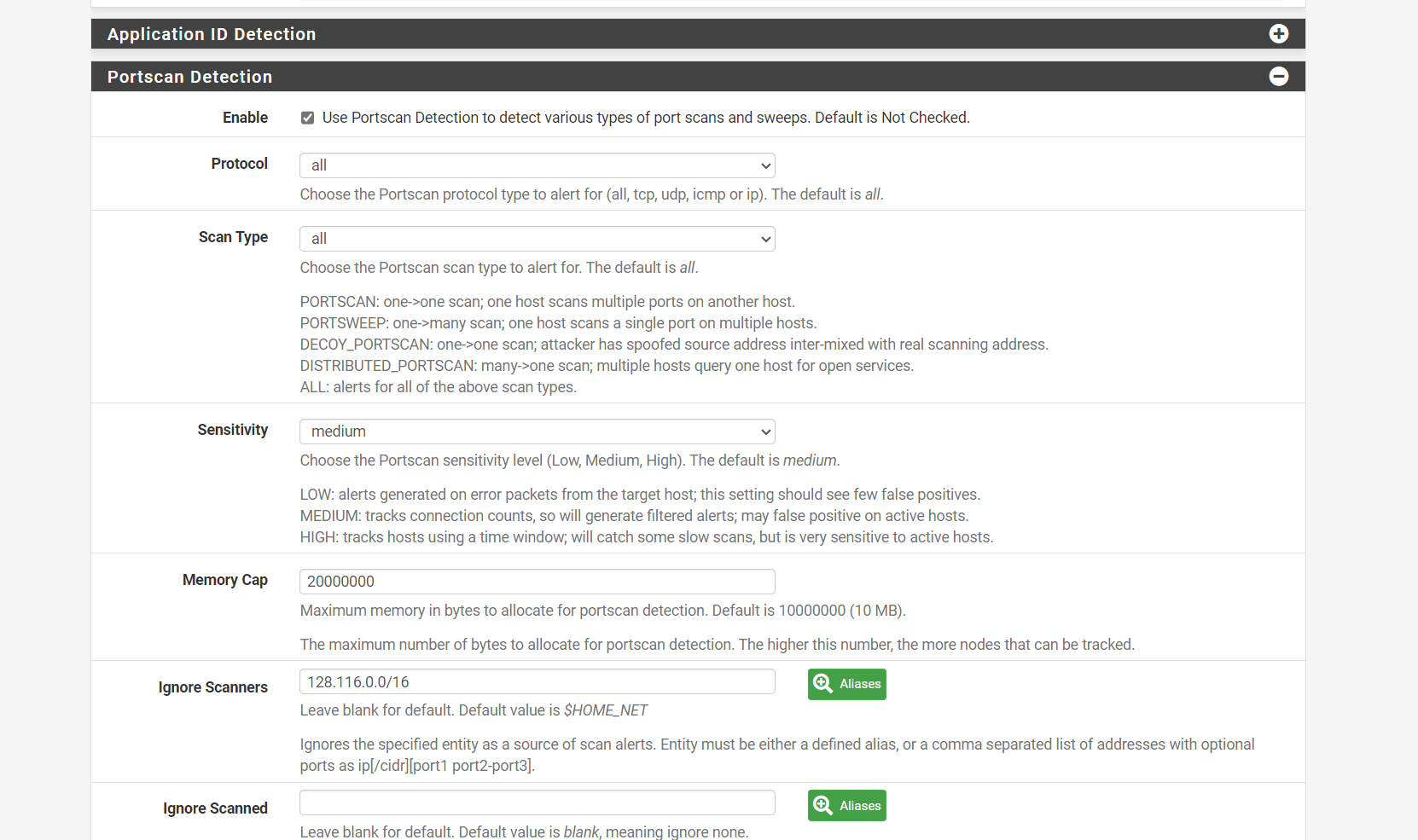
I ignore a pretty big block of addresses that Roblox uses or Snort blocks them all when it sees a UDP scanIt's the 1990s Air-Snort application upgraded, anyone play with that in the 90s, I use to see 0.0.0.0 MACs sometimes back in the day.
-
@bmeeks said in Do I Need IPS ?:
but there are a fair number of users that install it without fully understanding what it is and how to maintain it.
yes, this can be seen in many scenarios and when they fall flat on their face they realise what they have done wrong

+++edit:
at least they will have something to ask here on the forum -
@michmoor said in Do I Need IPS ?:
The solution would be to gatekeep this behind a VAR and high cost support packages :)
that would be quite terrible

-
@JonathanLee
Are you running it on the WAN or the LAN side?I plan to run it. I am waiting for 23.09 first.
Do any of Pfsense's IPS/IDS use Intel's Hyperscan? Maybe that is the real SNORT 3?
https://www.intel.com/content/www/us/en/developer/articles/technical/introduction-to-hyperscan.html
-
@coxhaus WAN it does take a while to configure this way. Most use Lan today
-
@JonathanLee
I used WAN years ago. Never used LAN. -
@coxhaus said in Do I Need IPS ?:
I used WAN years ago. Never used LAN.
I do have some problems with this though, pfS "drop" everything on the WAN by default and it's a noisy interface and look at this one Bill knows it best:
https://forum.netgate.com/topic/76141/snort-on-lan-wan/5?_=1695283899257