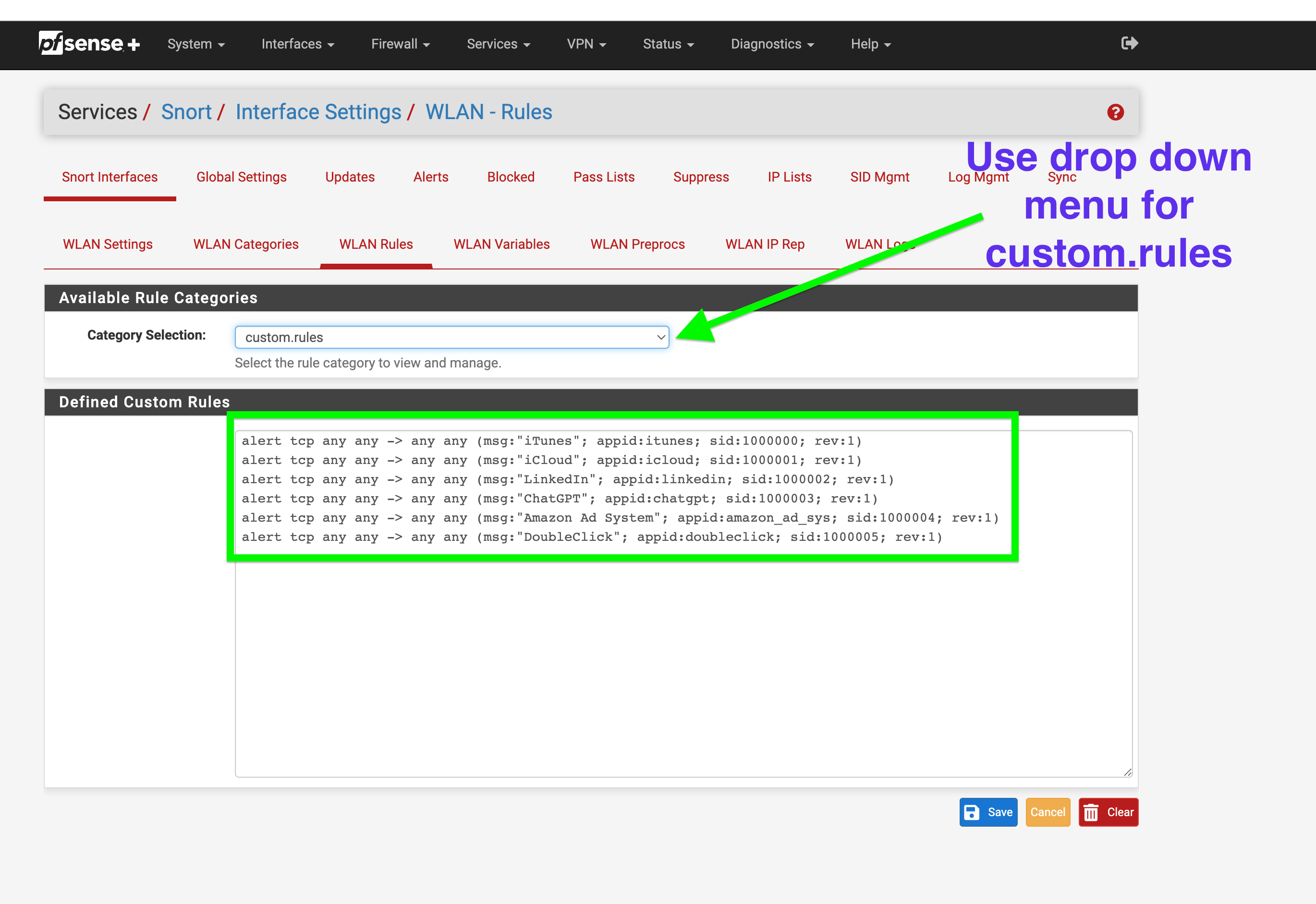
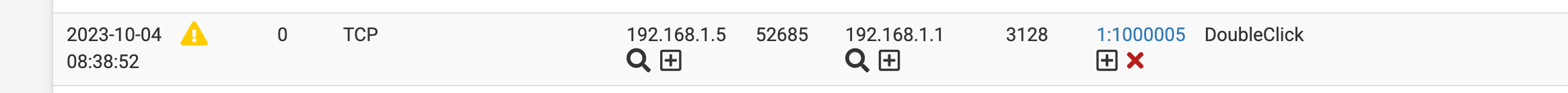
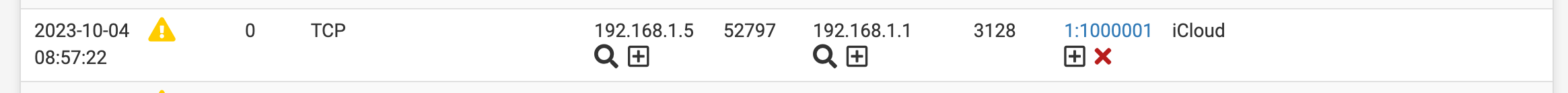
GUIDE: Snort's AppID custom rules Quick Guide to blocking. Example shows OpenAI ChatGPT or Itunes.
-
@michmoor You have to add your own text files, I created a java program to do the for me based on the database that is downloaded. So that might be why mine has ChatGPT. Yes that list is updated but it does no good unless you generate the text files to match them. I just made a java program to parse over that database and generated a text file based on that. My text file is above but I have not updated that list in a while. I have to run the database in it again.
-
@JonathanLee going to DM you for details
-
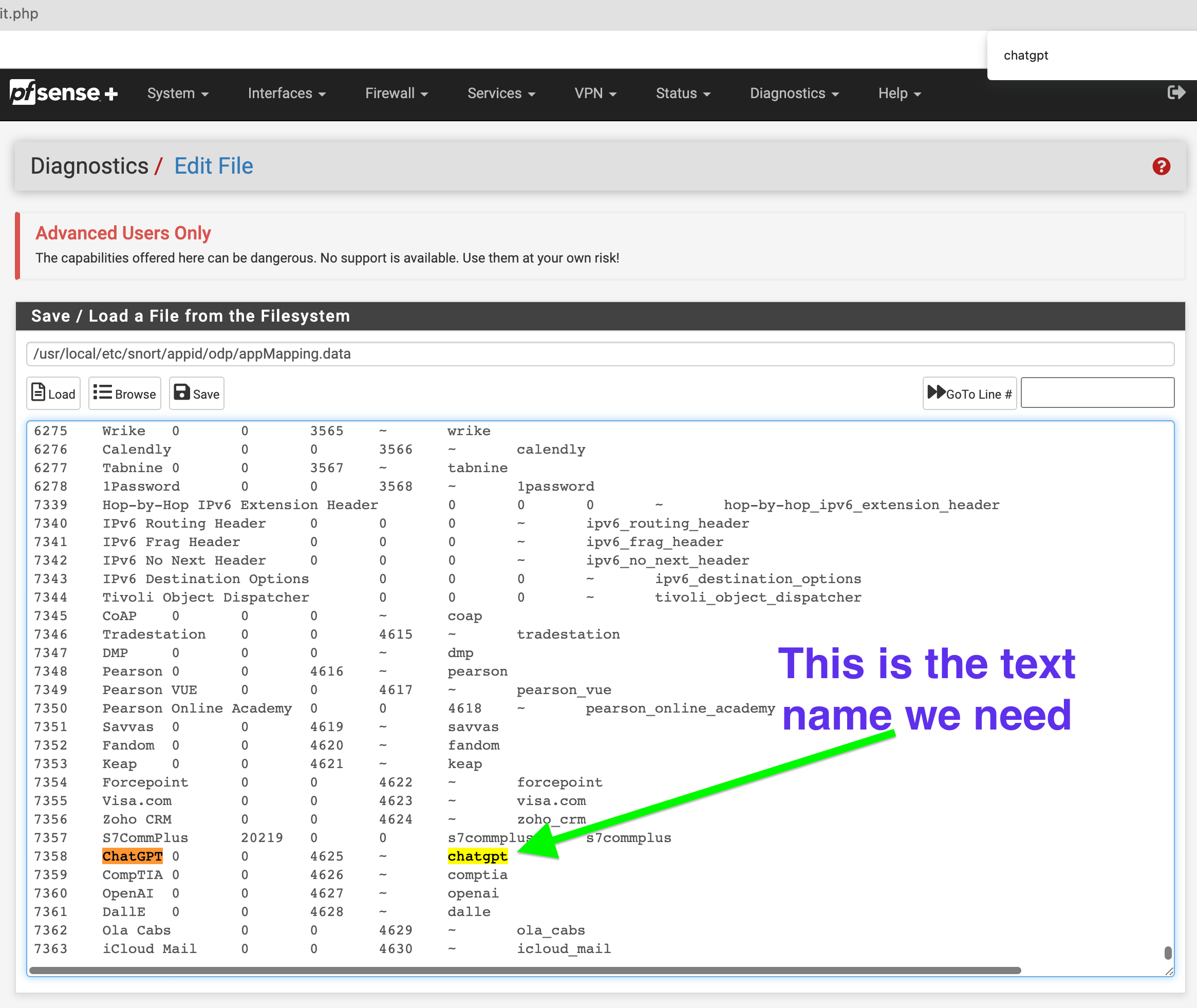
@michmoor In Snort's OpenAppID context, "appMapping.data is a file that maps application names to their corresponding AppID identifiers, which are used for creating rules to identify and control application traffic."
-
@bmeeks said in GUIDE: Snort's AppID custom rules Quick Guide to blocking. Example shows OpenAI ChatGPT or Itunes.:
appMapping.data
Do you know when this is updated again?
appMapping.data
I have the subscription for Snort but I have not seen this update in a while now.
-
@JonathanLee said in GUIDE: Snort's AppID custom rules Quick Guide to blocking. Example shows OpenAI ChatGPT or Itunes.:
Do you know when this is updated again?
appMapping.data
I have the subscription for Snort but I have not seen this update in a while now.
No. That file comes down as part of the AppID stub rules update. It's up to the Snort VRT for when they update it on their end. I don't know as I have not looked into this for quite some time, but it could be that the Snort VRT is slowly deprecating updates for legacy Snort 2.9.x stuff in favor of Snort3. Snort3 and 2.9.x are not compatible and cannot share things like rules files.
At some point for sure upstream Snort will discontinue updates for the Snort 2.9.x code tree. This is why I've urged Snort users on pfSense to move to Suricata. Of course Suricata does not have AppID support, so Snort users would lose that feature after migration. On the other hand, Suricata has much more intensive logging. If you continue to use Snort 2.9.x on pfSense, then expect to be doing much more hand-holding of the package and your own software maintenance.
-
I have a question. Why can't we get Snort 3 on pfsense since version 2 is being depreciated? I know there's Suricata but like to have options.
-
@Darkk said in GUIDE: Snort's AppID custom rules Quick Guide to blocking. Example shows OpenAI ChatGPT or Itunes.:
I have a question. Why can't we get Snort 3 on pfsense since version 2 is being depreciated? I know there's Suricata but like to have options.
Snort and Suricata are both volunteer maintained packages. That means a volunteer contributes the programming effort required to create and maintain the package without compensation and without any involvement from the pfSense developer team other than that team manually merging code changes submitted by the maintainer into the official pfSense repository. For Snort, I assumed the maintainer role for that package many years ago when the original developer grew weary and moved on. I wanted certain features to be available in the package (flowbits primarily), and so I added the necessary code and submitted the Pull Request to GitHub. It was accepted, and so I offered a few more updates such that over the years I became the defacto maintainer for Snort. For Suricata, I created that package from scratch, submitted the Pull Request to the Netgate team, and have been maintaining it since as a volunteer contributer sharing my work with the pfSense community for free.
For both packages, I am getting ready to step aside. There is no compensation for volunteer maintainers, and since I retired from an IT role in a Fortune 500 US company several years ago, I am slowly disentangling myself from committments to more fully enjoy my retirement. That's one of the reasons you have seen fewer Snort and Suricata updates over the last year.
I tried on two separate occasions in the recent past to create a Snort3 package for pfSense. But I gave up in frustration both times. Partly because my heart was not totally in it for the reasons outlined above (my retirement), but also because it's very hard to do since Snort3 is a radical departure code-wise from Snort 2.9.x on the binary side. It will require rewriting things in C++ and adapting all the old Snort 2.9.x configuration parameters over to Lua scripting. The use of Lua will require substantial changes in the GUI package code.
The only way Snort3 will come to pfSense is if either some other new volunteer steps forward to create the required package, or if Netgate decides to take it over. Everything needed is available on the pfSense GitHub repo here -
Snort Binary Package Code: https://github.com/pfsense/FreeBSD-ports/tree/devel/security/snort
Snort GUI Package Code: https://github.com/pfsense/FreeBSD-ports/tree/devel/security/pfSense-pkg-snortIf Snort3 is important to you, perhaps you might consider stepping into the volunteer maintainer role like I did many years ago and then sharing your work with the pfSense community ...
 .
. -
I didn't mean any disrespect. I and others do appreciate the work that was put into it. I totally understand your situation and respect that.
-
@Darkk said in GUIDE: Snort's AppID custom rules Quick Guide to blocking. Example shows OpenAI ChatGPT or Itunes.:
I didn't mean any disrespect. I and others do appreciate the work that was put into it. I totally understand your situation and respect that.
Your post was fine and no disrepect was felt. I'm sincere about someone else stepping forward to become a maintainer of the package. That's the beauty of open source software.
Just as I fell into the role several years ago, another user can do the same if they feel the urge.
-
@bmeeks your code is epic !!