Connected client's wan ip is still getting assigned Wan ip.
-
@viragomann
Thank you for reply. I gave client .ovpn file. He simply imported file and connecting.
Is there still something I need to set on his pc? I spent lots of hours but totally stucked. -
@ozgurerdogan
Again, it's on the client to decide how it sets the routes.
Maybe there is a setting in the client to limit the routes to the remote networks. But without knowing, which client you're using, nobody can tell you. -
@viragomann
He is using openvpn client (https://openvpn.net/client/client-connect-vpn-for-windows)
So he is using conf file I gave him.
I am trying to understand where to play with setting. On client pc side or on vpn server side in pfsense. -
@ozgurerdogan
In the Windows there are no settings apart from the conf file, as far as I know.
In the conf look for a 'route' line. Normally there is none and you push the routes from the server. But the server routes are pushed to all clients in the same way. So probably there is all right.In the server settings you can push routes either with "Local Networks" or 'push "route ..."' in the custom options.
You can do the same for a certain client in the client specific overrides.
-
@viragomann
So you mean I need to force client to not to use pfsense as default route. -
@ozgurerdogan
No, this cannot be done. In the server settings you can either push the routes for certain subnets or for the whole upstream traffic (redirect gateway).I mentioned CSO to check if in case, there is configured any in the server settings.
If there is nothing, check the clients log for hints. You should see a log line for the pushed options.
-
@viragomann said in Connected client's wan ip is still getting assigned Wan ip.:
@ozgurerdogan
No, this cannot be done. In the server settings you can either push the routes for certain subnets or for the whole upstream traffic (redirect gateway).
I am new to this. But can not figure out. What I do not understand is why this is only happening only 1-2 clients but not others. I but think this about routing.. -
@ozgurerdogan
I tried setting "push "redirect-gateway def1"" on a unchecked "Force all client-generated IPv4 traffic through the tunnel." server that caused client to use pfsense as default gateway.
But that client does not have this option. So maybe I can force to use opposite of push "redirect-gateway def1" if there is any :) -
@ozgurerdogan
This option is only in the server settings.What about the client log??
-
@ozgurerdogan said in Connected client's wan ip is still getting assigned Wan ip.:
Other clients' ip remain same as it was before connecting to vpn.
You sure its just not an old state on the client?
If I go to say check my IP, and then connect to vpn, and then check my IP again - it can use the old connection. And still go out his normal wan vs going down the vpn.
Have him look at his routes
before, and then after connection..
Example here is mine
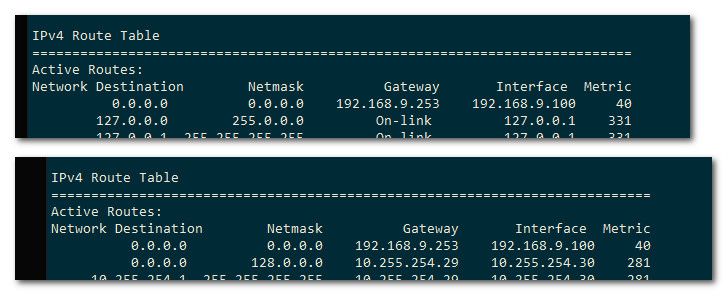
See how a default route got added, the 0.0.0.0 route.. and can see in the connection log it was told to use gateway
2023-10-08 14:16:39 PUSH: Received control message: 'PUSH_REPLY,redirect-gateway,dhcp-option DNS 10.255.254.1,route 10.255.254.1,topology net30,ping 10,ping-restart 120,ifconfig 10.255.254.30 10.255.254.29,peer-id 2,cipher AES-256-GCM' 2023-10-08 14:16:39 Flag 'def1' added to --redirect-gateway (iservice is in use) -
@johnpoz
Yes I am sure ip changes to Pfsense's WAN ip after connecting for that client.
Could this be issue because his OpenVPN client is old version ?
How about If I set pull-filter ignore "redirect-gateway"I will post logs once I got them.
-
@ozgurerdogan
All you can do at the client is adding a line to the config to avoid adding the routes pushed by the server:route-nopulland add the routes manually. E.g.:
route 10.10.0.0 255.255.255.0to route 10.10.0.0/24 to the server.
Not sure if this helps.
-
@ozgurerdogan what are you trying to do - you don't want this client to route through pfsense to get to the internet, and just want them to get to your network behind pfsense via the vpn. Or you do want them to route through pfsense to get to that internet?
-
@johnpoz
I want them connect to rdp behind Pfsense. And retain their wan ip as before connecting to Pfsense.
Don't want client to route through pfsense to get to the internet. -
@ozgurerdogan well then uncheck this..
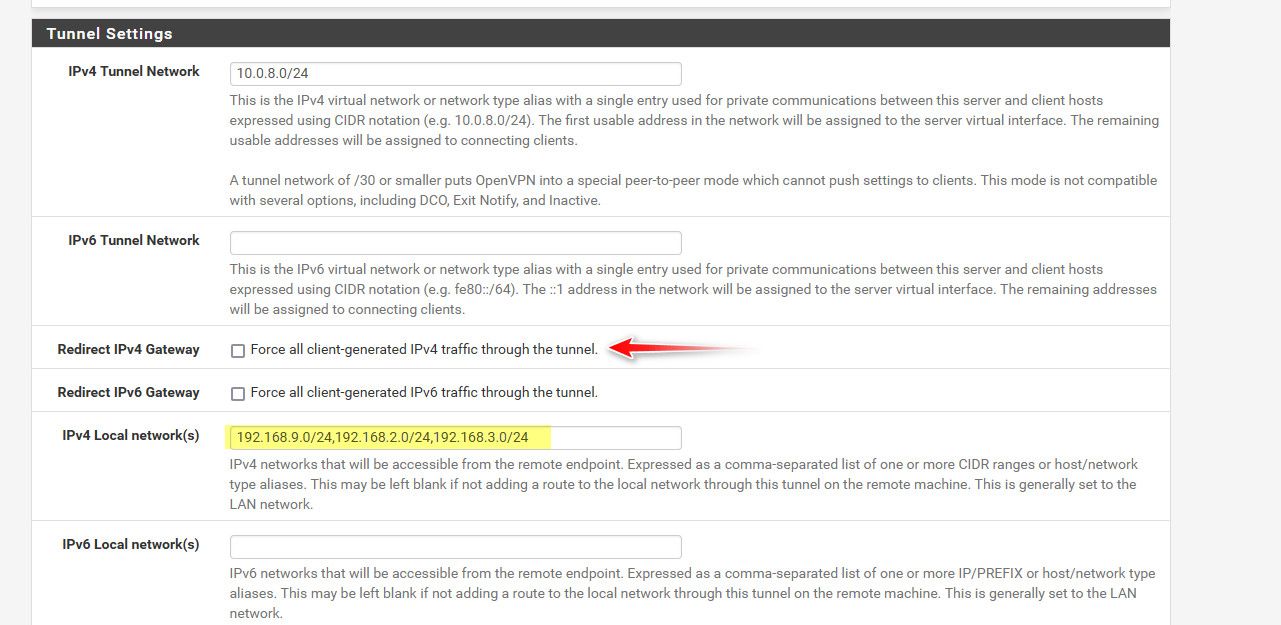
And make sure your network you want them to get to is routed as your local network(s).. See my highlighted.
Your only problem could be when they have the same network.. If their local network is say 192.168.1.0/24 and your local network is the same 192.168.1.0/24 then they going to have a problem..
If you had that checked before, you will need to give them a new ovpn file to use, or have them edit their local copy to not redirect the gateway.
-
I am sorry guys. There was a misunderstaning. :)
Client's wan ip remain same after vpn. And he connects to RDP which has two nics. One for VPN internal network, one with wan ip for users not using VPN.So when client connects to rdp via vpn, his wan ip becames pfsense wan ip. So I need to make other nic as his default route...
-
@ozgurerdogan Huh??
So this remote vpn client rdp to some box on your network 192.168.1.100.. Why would this 1.100 box have 2 nics in the first place??
But sure if if this 1.100 box has 2 nics.. And some remote IP talks to it.. It would use its default route to try and get back.. So take it this 1.100 rdp box isn't using pfsense as its default gateway..
-
Has two nics. One nic with wan ip (no-vpn) has ip restrictions at firewall for certain clients only. And those clients can not be using vpn. And other nic for vpn clients.
So whether it is vpn or non-vpn client, rdp box must be using one default route which must be one nic only. Should I set this at nic settings or with routes..?
-
@ozgurerdogan If you have some box with 2 nics.. You need to make sure it the correct route to get to whatever your vpn tunnel network is.. Or it would just use its default route to try and answer some IP it does not have a route too.
So this other wan connection being used for non vpn rdp into this box, is not pfsense I take it.. Why would this other connection not come into pfsense?