Pfsense + freeradius + Microsoft Active Directory
-
If you uncheck 'disable weak EAP types' does it work? Or produce a different error?
Did you set 'LDAP Authentication Support' in the LDAP setup page?
-
@stephenw10
Sorry for my late answer. No effect, if I uncheck. I try the user management by Active Directory. When I complete the setup, then I try authentication under the diagnostics menu its works. So pfsense can communicate with AD by native. BTW if I search on OPNsense forum this issue, than this problem is occur at OPNsense.I find out an alternative solution. The name is packetfence
I will try that in this weekend.I will let you know what I came up with.
-
Hi, i'm dealing with the same error. I tried different configurations in the EAP tab and no one is working.
The packet from the AP is received by the pfsense well, but i can't find the right config for the freeradius the check against the ldap server.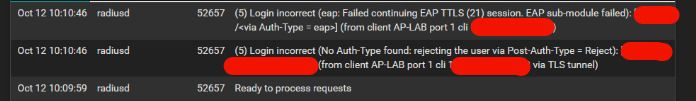
This is the error when i try connect
-
@sebauer @stephenw10
That can solve the problem? Enable LDAP signing on MS AD
According to this, in default the LDAP signing is disable on MS AD?@sebauer which LDAP solution do you use?
-
I'm pretty sure this is because the eap type used means radius can only ever see an authenticated or not type of responce from ldap and it's trying to login itself. Hence the 'no nt password' error.
You have to configure the radius to LDAP link to allow that in order to handle the requests from wireless clients. -
@freenode This is my config on the EAP tab:
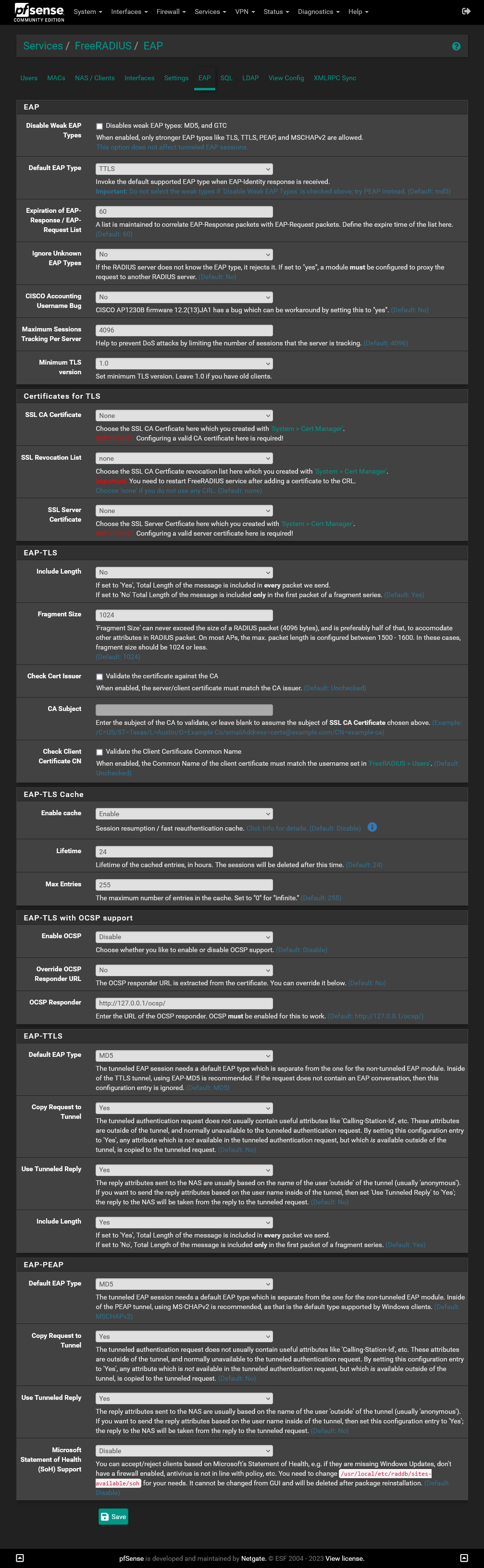
-
And the LDAP config from radius?
-
@sebauer and the LDAP tab:
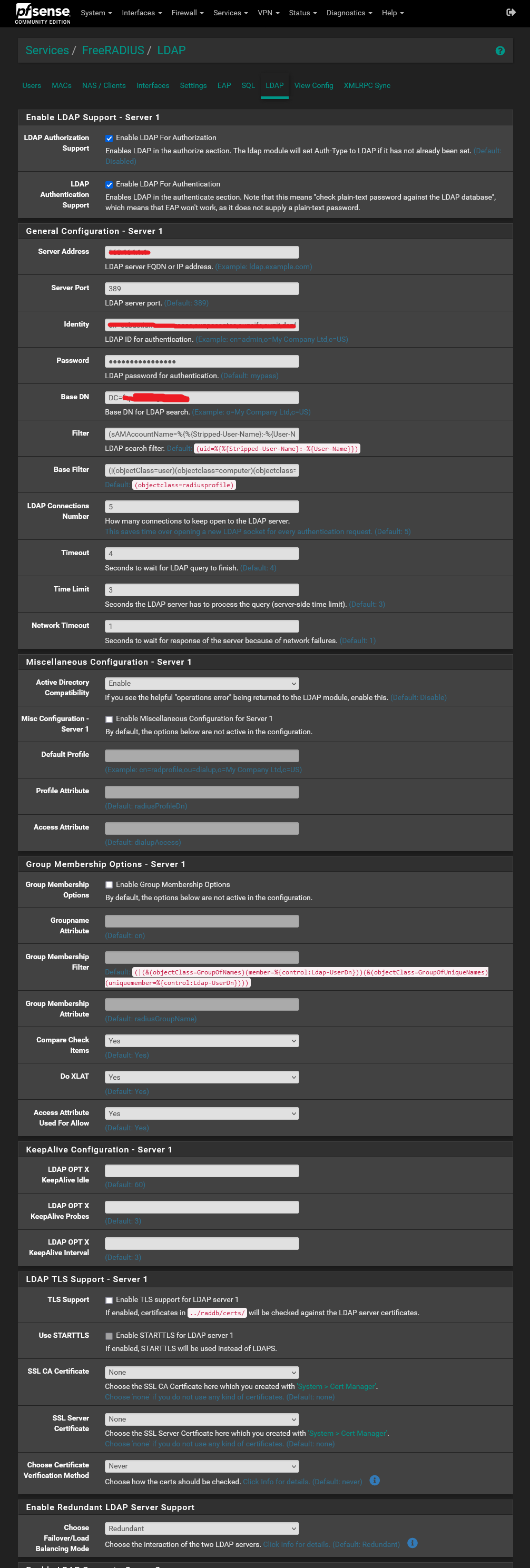
-
Ok, so try disabling 'LDAP Authentication Support'. As it says there that doesn't work with EAP because it requires a plaintext password and radius never has that.
-
@stephenw10 I changed that and I'm getting the same error hahaha.
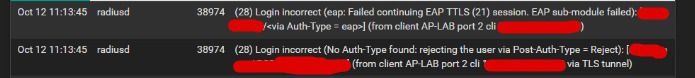
I'm trying this like for a month ago, i'm working in this lab for my work and i never find someone trying something like this until now.
Radius never was very friendly when error happens -
What does the LDAP server show when it tries that?
-
@stephenw10 Don't say nothing. The logs in pfsense are showing nothing of the LDAP.
But i checked changing the IP from the LDAP server for the IP of my pfsense to see if can use the server authentication that i created en pfsense to test the connection to the LDAP server first and the log says: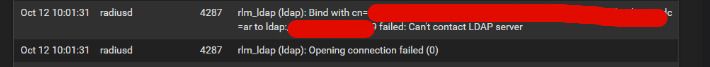
In the LDAP server i can't see anything because I haven't the privileges yet because i'm new in this work
-
Ok, then to test this I would setup an LDAP server you can see the logs in and authenticate against that first so you can see how it fails. Or doesn't.
-
Hi @stephenw10 i was thinking: there is a way to configure the Post-Auth-Type??? Since the error says "(5) login incorrect (no auth-type found: rejecting the user via Post-auth-type = reject)" is there a way to set to the post-auth a value that works with ldap?
-
Only whatever is there in the Freeradius LDAP config AFAIK.
-
Hello @stephenw10, I have some updates regarding the FreeRADIUS configuration against the LDAP server. By capturing packets and analyzing them with Wireshark, I noticed a few things:
-
The first thing is that the LDAP server insists on using EAP for authentication. When we try to authenticate using MD5 or GTC, the LDAP server rejects the packet because the security protocol is not very secure.
-
We tried enabling the "Enable LDAP for Authentication" option, and in Wireshark, we can see a packet exchange in which the user attempting to authenticate to the WiFi network is sent back to pfSense, where we have our FreeRADIUS. However, we are still encountering the error that says: "Login Incorrect (mschap: FAILED: No-NT Password. Cannot perform authentication)."
So, from what I can see, the connection to the LDAP server is working perfectly. What I don't understand is where the issue with the password lies. It could be on the FreeRADIUS side when it receives the request from the Access Point, or it might be in the LDAP server's response.
-
-
#2 there is expected. When using EAP Freeradius never has the password to use to authenticate the user. It can only pass the username to authorise it. As I understand it at least. But I'm pretty confident on that since the option notes that.
-
@stephenw10 I'm completely demotivated; I thought it was going to be simpler than it is, but it's not. The funniest thing is that, while looking at the packet capture in Wireshark, it finds the user I'm logging in with, but the mschap error "No NT-Password" keeps coming up nonetheless. I don't know what else to do. Is there anything that can be adjusted in the mschap file? I wouldn't know what, if anything. Or could something be tweaked in the LDAP attributes?
-
You're seeing that error because one side is expecting password to be sent but the other side never has the password to send.
What I suggest is to disable 'Enable LDAP for Authentication' because that cannot work with EAP types and then try to diagnose the error9s) without that. Which I expect to be an algorithm mismatch.
Steve
-
@stephenw10 should disable that option and change something in some config file? i disable and the error is the same