malware outgoing blocked - help to interpret firewall log entry
-
Here's the screenshot of the WAN rules:
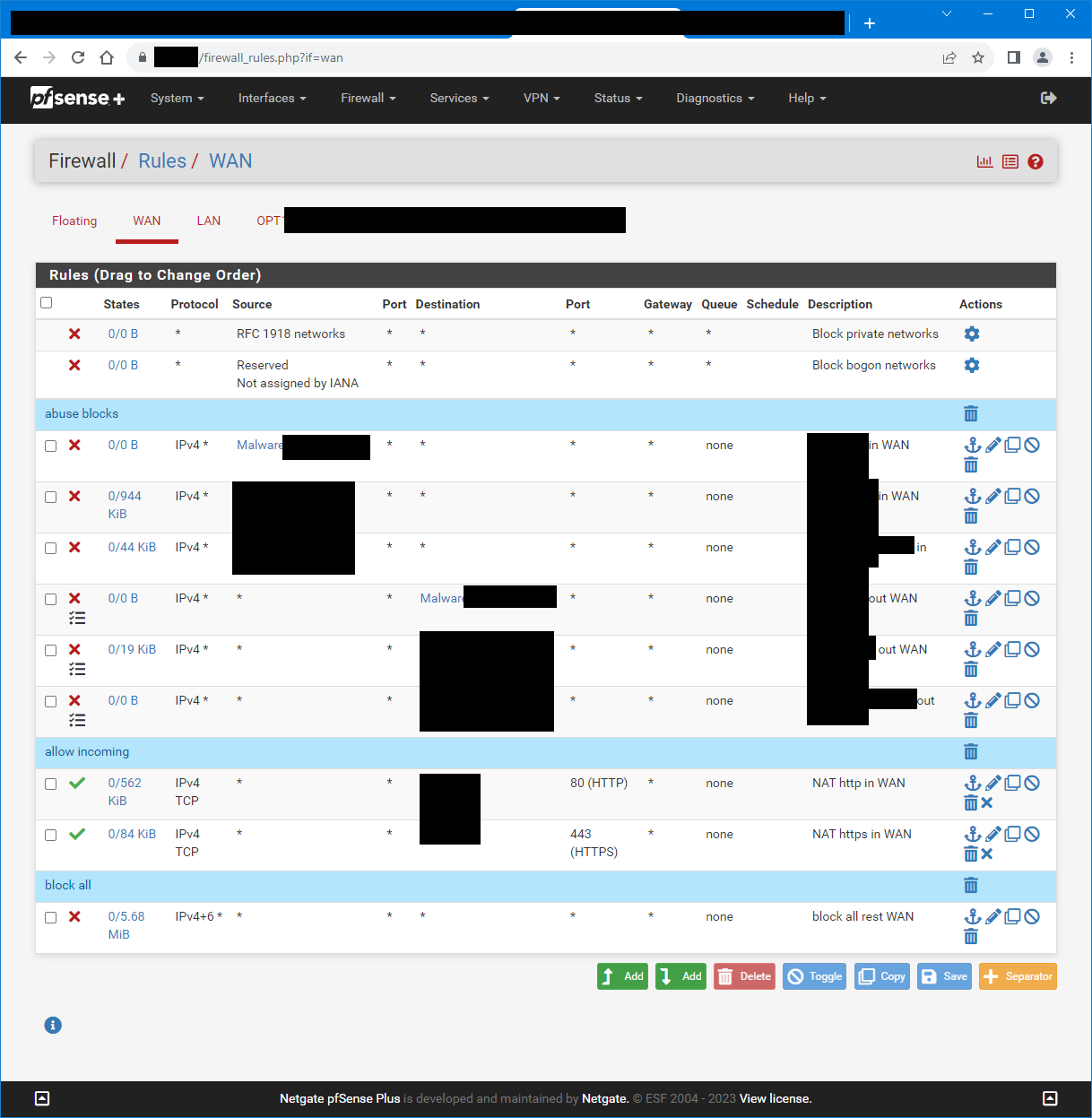
There are three identical rules with different aliases in use. Three for incoming, and another set of three which is unclear which I originally thought was outgoing.I have no floating rules currently.
I cannot share all the LAN rules (many pages), but there are no rules related to the malware aliases from above. Only today I added that as well to make sure outgoing traffic to any malware IP is blocked on the LAN as well.
So coming back to the original question when you say all rules are incoming (from firewall view) rules. What does an incoming rule on the WAN Interface with Source=Any and Destination=external_bad_IP_list then do if it's an incoming rule? Especially if there is another rule first that would block such incoming traffic.
-
@e4ch not helpful to be honest.. looks like gov secret doc.. So alias that malware are they the same alias? If they contain public IPs then that rule there where its destination is never in a million years going to trigger..
How can help figure out if that is going to trigger or not? with destination blocked? Is that your wan IP? in both? Use the wan address if that is what you want. If that is blocking into your wan. Then your 2 allow rules will never trigger
Where is floating? Where is lan
Rules are evaulated as they enter your wan.. You can't stop something on your network with a wan rule, you need to put that on the interface they are connected too, or create an outbound rule in floating
-
not helpful [...]
There are just three different blocklists. I don't want to share publicly which blocklists I'm using. But yes, all are public IPs. For example 43.241.72.160 or 27.111.82.74 that I mentioned earlier is on the list. We can also disable four of these six rules and nothing to my question would change. The remaining two rules are:
- WAN Interface, Source=alias1, Destination=any
- WAN Interface, Source=any, Destination=alias1
(with alias1=43.241.72.160, 27.111.82.74, and more IPs)
I understand that the first rule is correct and blocks the incoming traffic from blacklisted external IPs. The question is about the second rule there.Where is floating? Where is lan
As mentioned, floating is empty. LAN rules don't matter here, assume no blocking rules for now.
You can't stop something on your network with a wan rule, you need to put that on the interface they are connected to, or create an outbound rule in floating
fully understood
So alias that malware are they the same alias?
Not sure what you mean there. Do you mean if it's the same alias for both rules? yes, they are the same alias.
If they contain public IPs then that rule there where it's destination is never in a million years going to trigger.
It does trigger, as the rule is named in the log as being hit. You see that rule has logging enabled from the icon. You can also see it in the screenshot above where it does NOT say "0/0 B", but has some values instead ("0/19 KiB"). And that's exactly my question. Why does it hit, if incoming traffic is already filtered (previous rule above with alias on Source) and we're only filtering incoming traffic on WAN interface. What does such a rule do? It might be wrong, but it obviously does block something.
-
@e4ch said in malware outgoing blocked - help to interpret firewall log entry:
It does trigger,
No its not triggering

if that alias contains bad sites.. How would that ever be destination into your WAN IP? It can't be, so no that rule could never trigger..
How could say a destination of say 1.2.3.4 some bad site on the internet ever come into your wan that is say 4.5.6.7 - its just not possible..
-
@johnpoz The one below says "0/19 KiB". It's just a different alias than the one you highlighted. That's actually the one that contains the mentioned IPs and is in the logs. So that one is triggering. That's what the question is about.
-
@e4ch the one you have hidden to what the destination is - if its not an IP on your wan, or a alias on your wan.. Then its not going to trigger unless your just seeing some broadcast traffic etc..
That traffic has to be inbound into your wan for any of the rules to trigger on the wan.. What is the destination? If its an alias and it contains your wan IP then sure it could trigger.. What is in the alias?
Source=Any and Destination=external_bad_IP_list then do if it's an incoming rule?
That rule would do NOTHING.. rules on your wan are inbound traffic to you wan.. Its not going to trigger unless your wan sees it as inbound traffic.. How would traffic for 1.2.3.4 hit your wan if its 4.5.6.7?
Depending on what might be in that alias - maybe its broadcast traffic.. Show us the log entry - what is the destination.
And it not going to ever do anything either if your client is allowed to talk to the bad IP, any return traffic would be allowed via the state..
Again that alias if has bad Ips would never be inbound traffic into your wan as destination - and even if your IP was in the alias, the return traffic would be allowed, unless your states were reset.
-
I might wonder if the rules aren’t loading as expected, try (IIRC) Diagnostics/Filter Reload.
-
I found the problem.
The one that did trigger was actually the FireHOL level 1 firewall blacklist. Not sure yet if I want to keep that (http://iplists.firehol.org/). It's one of the well-known blacklists, but has a problem.
That list contains all private IPs like 10.0.0.0/8 and 192.168.0.0/16 too. You probably already see where this goes.
So what happened is this: The incoming request is a port scanner for port 80 or 443 or a regular web request. Then the first alias block rule does not trigger, because the sender is not on the blacklist. The IPs mentioned earlier (43.241.72.160 and 27.111.82.74) are actually on none of the lists - I just verified. So they are legit.
Then the port forwarding rule applies and changes my external IP (the destination) to the webserver IP, which is on my private network (RFC 1918 address). Then the second (invalid and useless) rule where the blacklist is on the destination fires, blocks the incoming traffic that should go to the webserver and logs the request. As there is no webserver, this was never noticed (it blocks essentially all web traffic).
So I'll just delete the second rule (those three that you mentioned that will never fire in a million years). They did fire, but only because private IPs are on that blacklist.
As I want to block outgoing traffic to malicious IPs too (in case there's a C2 server), I have to add that on the LAN port with Destination=alias - that is understood. But if such a blacklist now contains private IPs, that might be a problem when internal traffic must go through the firewall (like from LAN to OPT1 or so). I might need a better blacklist or just use the remaining two lists.
Thanks for helping.
-
@e4ch said in malware outgoing blocked - help to interpret firewall log entry:
But if such a blacklist now contains private IPs, that might be a problem when internal traffic must go through the firewall
Put a rule that allows traffic to your other rfc1918 addresses on other networks if you want to allow that.
Rules are evaluated in order top down, first rule to trigger wins - no other rules are evaluated. So if you have rule that allows 192.168.1.0/24 above a rule that blocks 192.168.0.0/16 doesn't matter because your rule above allows to your other network say to 192.168.1.42 or whatever.
-
@e4ch said in malware outgoing blocked - help to interpret firewall log entry:
I might need a better blacklist or just use the remaining two lists.
Just use pfBlocker for all your blacklists, it will remove any private IPs for you but before learning pfBlocker you have to understand the fundamentals: Everything is always incoming/inbound to the firewall interface, not outbound.
That means, if you want to block some bad IP from the internet, you have to create the rule on WAN with source bad IPs.If you want to block hosts on your LAN to reach bad IPs, you have to do it on your LAN interface with destination bad IPs.
The reasons is that all traffic is only evaluated once by the firewall, when it first enters it. If it is not filtered there, the traffic can go everywhere.
I hope this helps.
-
@Bob-Dig Thanks and understood. I'll have a look at pfBlocker.