Rule order bug?
-
Is there a firewall bug, that i dont know of?
Rules i would like to apply is this (and order)
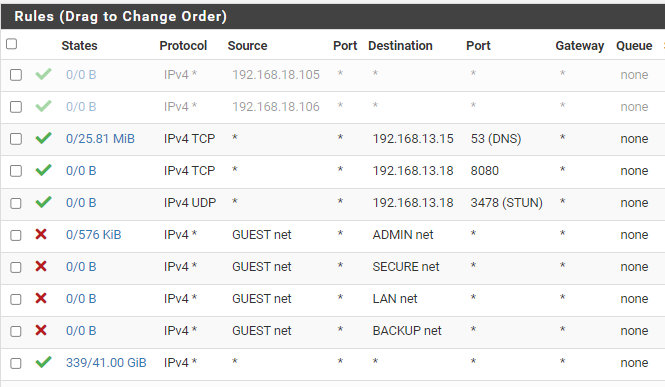
So the intended setup of the rules, on a guest interface is:
- allow DNS, 8080 and 2478, to specific destination.
- Then it blocks all other traffic to internal networks
- And allow everything else (WAN)
It has been working fine before, but suddently stopped working (perhaps after an update(?)). So I then looked at the firewall, and it has ordered it like this, an thus allowing access to all internal networks.
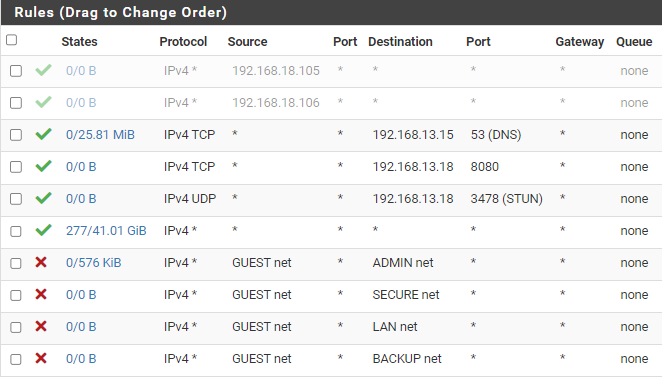
I then reorderd them like the first picture. Saved it, and apply it to the firewall. But it still does not work. If i then log out, and in again. It has reorderd them back to "picture 2" again.If i do any changes to the rules, it works fine and applyes no problem. IE i tried changing the "any any" rule to dest. WAN - but then all traffics stopped working. So the rules/firewall seems to be working. it just wont let me save the ordering.
I have also tried to make the rule on the "admin" interface, with source "guest" and dest "admin" but that does not work either.
Any ideas?
Netgate 7100
BIOS
Vendor: coreboot
Version: ADI_PLCC-01.00.00.11
Release Date: Tue Jan 8 2019Version
23.05.1-RELEASE (amd64)
built on Wed Jun 28 03:57:27 UTC 2023
FreeBSD 14.0-CURRENT -
@fero1233
Did you hit the Save button at the bottom before applying the rules?
Are the block rule manually created?
Hints:
DNS also wants to use UDP. So you should change the protocol to TCP/UDP.It's recommended to enhance security to limit the source in pass rules to the respective subnet, but use any in block rules.
Instead of creating a separate block rule for each internal subnet, create an RFC 1918 alias and add all private network ranges to it. Then use this alias in a single block rule instaed. So the rule might cover all your internal networks and you don't need to add an additional rule if you ever add a local subnet or do some changes.
-
Thanks for the reply.
Yes, Saved and applyed. And tried numerous times to do so. And it rearange it every time.
-
@viragomann said in Rule order bug?:
but use any in block rules.
Why? the default deny would block any oddball traffic anyway.
-
@johnpoz said in Rule order bug?:
@viragomann said in Rule order bug?:
but use any in block rules.
Why? the default deny would block any oddball traffic anyway.
His rule set has an pass any-to-any rule below the block rules. So the default deny would not kick in.
-
@viragomann if I use the lan subnet or optx subnet in all of my rules, why would you use an any in blocks?
Unless the interface is a transit/connector network - I would always use your source network in the rule.
-
@johnpoz In theory there could be a routed network behind this network. Although as "guest" that is probably less likely than the normal amount of unlikely.
@fero1233 If you look at your saved config file for these rules, before and after the reordering, do you see anything of note? Normally rule ordering complaints are tied to automatically created rules from pfBlockerNG but you don't seem to have those in your screen cap.
-
@SteveITS said in Rule order bug?:
In theory there could be a routed network behind this network.
Which why I stated if the network was a transit/connector network ;)
-
@johnpoz said in Rule order bug?:
if I use the lan subnet or optx subnet in all of my rules, why would you use an any in blocks?
Basically, why not? It would enhance security in my opinion.
@SteveITS answered already.
A device within the subnet could act as a VPN client connecting to a remote site and would forward incoming traffic.
Sure, without additional configuration faults (not happening to you ;) ), pfSense won't route responses ever back.
However, assumed, the machine running the VPN is stated as gateway on the concerned interface, pfSense would route back any response packet to it, which has created a state before by the pass any source rule on this interface. -
@viragomann said in Rule order bug?:
Basically, why not? It would enhance security in my opinion.
How? If you do not allow the traffic, then the default deny will block it. What is the point of using any in block, when they are blocked anyway.. The habit should be to always use the source network in your rules. explicit rules are best, even just just the admin looking at the rules. Any or cidrs should be limited to where they are actually needed, ie a transit network where there would be downstream networks to be allowed.. If you were putting rules on a transit, I would create an alias or use a cider that covered my downstream networks that would be using this transit network.. So again if your allows are only allowing your networks be it directly attached or your downstream.. using any as source for deny don't really do anything, other than make your rules inconsistent when looking at them.
if you wanted to log specific traffic, ok - if you were not logging the default deny and you wanted to use the rule to catch stuff in your logs for misconfiguration of devices on the network, maybe..
I see no point in created block rules with any as source, when it makes no sense to do so. I just makes the rules inconsistent.. Sure it works and all, I just don't see the point. And it doesn't make it any more secure..
If you would provide an example scenario where it would make it "more" secure - I am all ears..
So for example here is example set of locked down network rules.
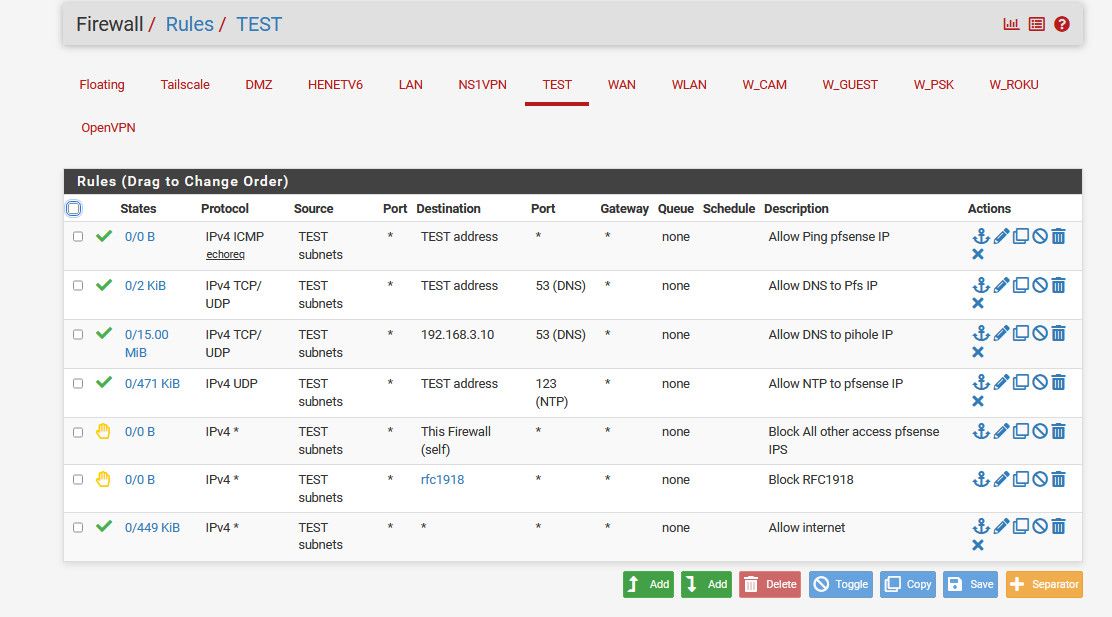
How would changing my rejects there to an any for source in any way enhance security?
if some source other than test subnets was inbound into this network, it would be denied by the default deny anyway. What would be the point in using any in my reject?
-
@johnpoz
Of course, there is all correct with your rule set. :-)How? If you do not allow the traffic, then the default deny will block it.
The point is, the TO has an allow any-to-any rule, but has the block rules restricted to the subnet.
-
@viragomann yeah the OP rules lack clarity that is for sure.. if your going to use any on your source for your allow, makes no sense to use a specific source in your deny.
Unless you had no control over what the downstream networks were using your transit. And you wanted to block a specific source network, etc. But then again all of those blocks after an any any allow are never going to be evaluated anyway.
There are many different ways to create rules that "work" but my question was to your statement to always use any in blocks.
It's recommended to enhance security to limit the source in pass rules to the respective subnet, but use any in block rules.
I am not understanding the point to that statement.
Good habits are to always be as explicit as possible in your rules.. I would never suggest an any any anything on even on a transit allow.. You should create an alias or use a cider that allows just your downstream networks using the transit.
-
Please keep replys on-topic, and discuss other issues in pm, or make a new topic. Thanks.
-
I updated the firewall to the latest version
From 23.05.1-RELEASE (amd64)
To 23.09.1-RELEASE (amd64)After i did that, and rebooted. The rules ware re-aranged wrong once again.
But then i aranged them correctly, saved and applyed. And then it seems to work now. As well in the config (thanks for that suggestion @SteveITS )
-
@fero1233 said in Rule order bug?:
From 23.05.1-RELEASE (amd64)
To 23.09.1-RELEASE (amd64)Possibly:
https://docs.netgate.com/pfsense/en/latest/releases/23-09.html#rules-nat
"Fixed: Changes in Ethernet ruleset can lead to incorrect rule and separator order #14705"
-> https://redmine.pfsense.org/issues/14705 -
@SteveITS said in Rule order bug?:
Changes in Ethernet ruleset
@fero1233 were you using "ethernet" rules - do you even have it enabled?
-
I checked the rules today, and now the rules are ordered wrong again. All the "block" are pushed to the buttom, and the allow is on top again.
I created the RFC yesterday as well, as recommended. And added it above the "Any any" rule, and it seems after a while yesterday (and if i looked in the config) that it saved the order. But this morning, it was all re-arranged again.
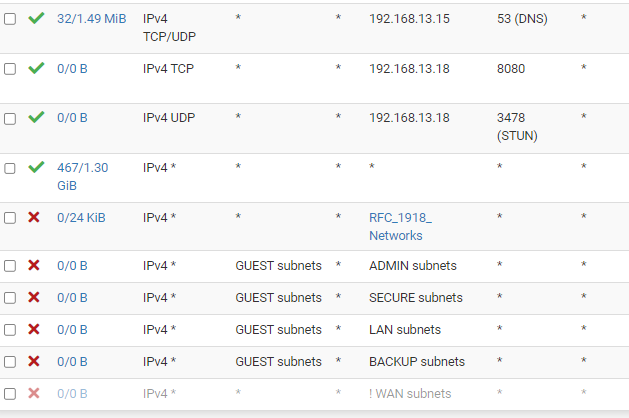
Are there any other/better way to achive this setup?
-
@fero1233 said in Rule order bug?:
But this morning, it was all re-arranged again.
have a look at the "config.xml" file.
There is a section that start with :
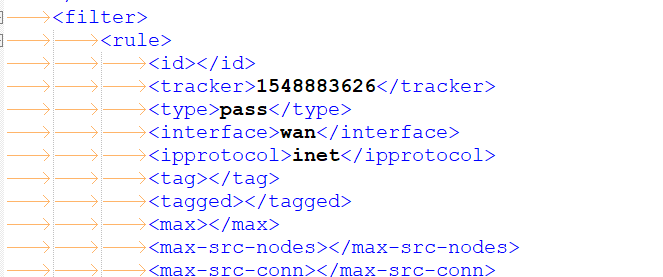
From then on, for every interface (WAN is called WAN, LAN is called LAN, the second LAN is called opt1, etc), in order ( ! ), you rules are listed as they should list in the GUI, and way more important, in the order the firewall rules are listed in 'pf'.
Having a last "pass all" rule, and then it gets listed at the top, that's a security issue (for me).
So : question : is the order in the config.xml also changed ?
If so, that would explain the miss ordering.
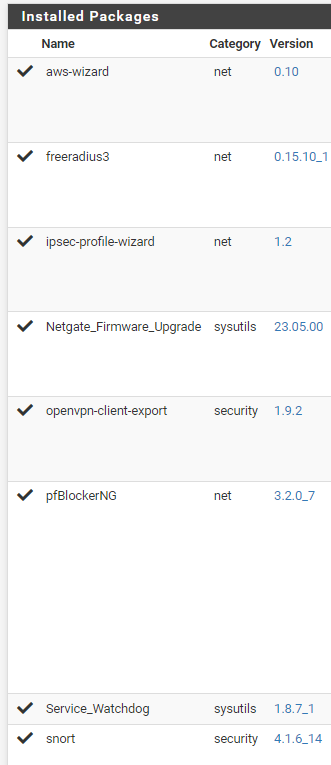
The question now becomes : who/what is saving the config, and what impacts the the firewall rules to be ordered differently ?What pfSense packages do you have installed ?
-
In config, it is also wrong order today. It was correct yesterday just after update/reboot/edit/save/apply
But i found this in config:
<revision>
<time>1707220801</time>
<description><![CDATA[(system): pfBlockerNG: saving DNSBL changes]]></description>
<username><![CDATA[(system)]]></username>And i am using pfblocker. So wondering if it is pfblocker, that changes the firewall(?) I might wanna try disable it.
Other plugins
-
@fero1233 said in Rule order bug?:
And i am using pfblocker. So wondering if it is pfblocker, that changes the firewall(?) I might wanna try disable it.
pfBlockerNG creates rules and rearrange the order on each update according due its settings. That's why I asked, if your have manually created the rules in my second question.