Using Managed Switch for Company and Private Networks
-
@johnpoz so how do I set up the switch with both of these networks?
bookie56
-
@bookie56 your port 1 would be connected to lan_private interface on pfsense with whatever vlan you want that network to be on your switch.. this would be untagged and pvid would be whatever vlan your using on your switch.
You connect port 17 on your switch to the pfsense interface that is lan company.. This port would be on some other vlan you create on the switch, this port would also be untagged and with a pvid of whatever vlan you created on your switch for this network.
So as example
Here is 3 different networks on pfsense, igb0, 3 and 5
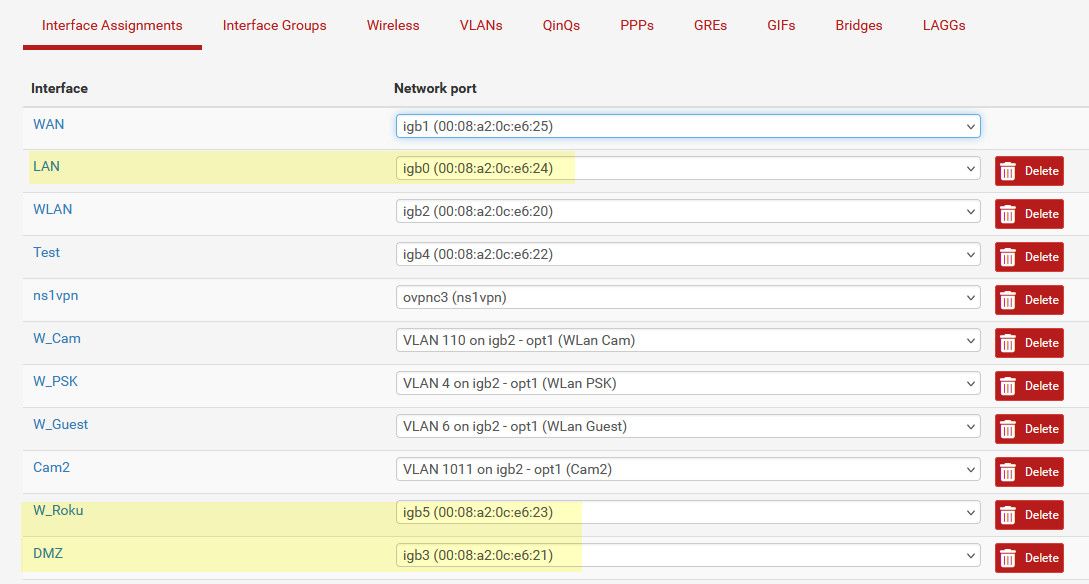
On my switch I have 3 different vlans created 9, 3 and 7 for these networks. I just used the 3rd octet number so its easy to remember.. my lan network is 192.168.9/24 my dmz is 192.168.3/24 and my roku is 192.168.7/24
Might make it easier for you to see if show this on the switch gui vs cli
These are the 3 ports on the switch those pfsense interfaces are connected too
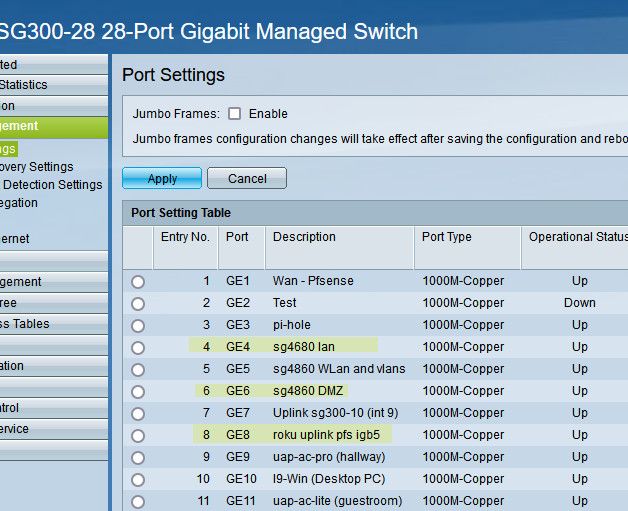
Now those ports on the switch are configured like this
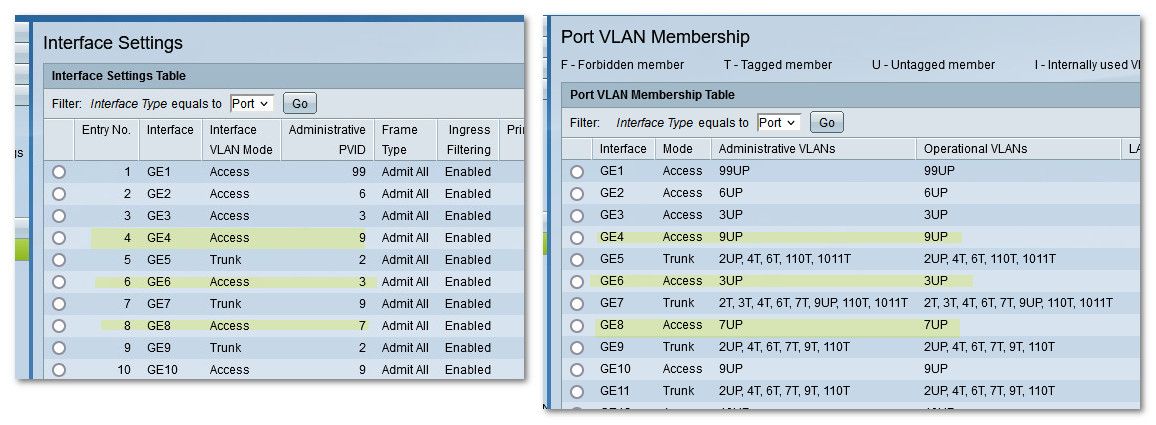
see pvid that is set, which is also shown on the vlan membership page as the P, the UP means Untagged and PVID vlan ID. All a pvid is what vlan on the switch the switch will put traffic that it sees coming in on that port untagged. Before you were isolating your networks with physical different switches. But when you want to keep these networks isolated on a vlan swtich, you have to tell the switch what vlans are what ports, etc even if the traffic is not tagged.
Even if the networks on pfsense are not actually vlans on pfsense, ie no TAG.. You still have to isolate that traffic on the switch by creating vlans..
Here are the vlans I have created on the switch
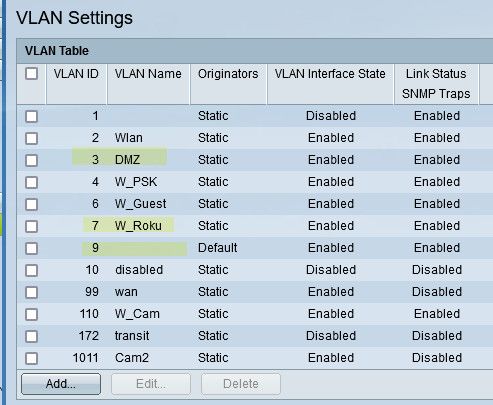
In my case my default vlan is set to 9 on the switch vs 1, the default vlan on most switches is 1 and many do not even allow you to change that.. I just changed mine so the ID would match up with the network I use on my lan of 192.168.9.0/24
You could prob do this on your switch with port vlans.. But using 802.1q is better option. Because now it will allow you in the future maybe to create a vlan on pfsense and carry this over the same physical port.. See for example those ports that are trunked and have multiple vlans listed on them.. Like port 7 on my switch that has 2,3,4,6,7,9,110 and 1011 all Tagged, see the T next to the number other than vlan 9 which is untagged.. you can only ever have 1 untagged vlan on a port.
That port 7 on my switch is an uplink to another switch that sits in my AV cabinet in my living room.. And I can put a port on that switch in any of those vlans.. For example one of my APs connects to that switch in the AV cab, and depending on what SSID you connect to puts you on that network/vlan.
-
@bookie56 said in Using Managed Switch for Company and Private Networks:
@Gblenn Sorry I am lost...
I was hoping to have the link for the LAN_PRIVATE which goes to Port 1 on the switch
I then was hoping to have the link for the LAN_COMPANY go to Port 17 on the switch...
If the above can't be done then I will have a separate switch for LAN_COMPANY and leave everything else on the new switch...This is why I have the quad using all 4....
bookie56Ah of course that's perfectly possible, exactly like @johnpoz describes it. You will essentially split your 24 port switch into two logical partitions, replacing your current dumb switches. And for that to work like you want, you don't need to do anything on the pfsense side at all.
So going back to my example with the picture of the TPLink interface, you will do this (using my 16 port switch as an example)
First for PRIVATE (using VLAN tag 5 here)
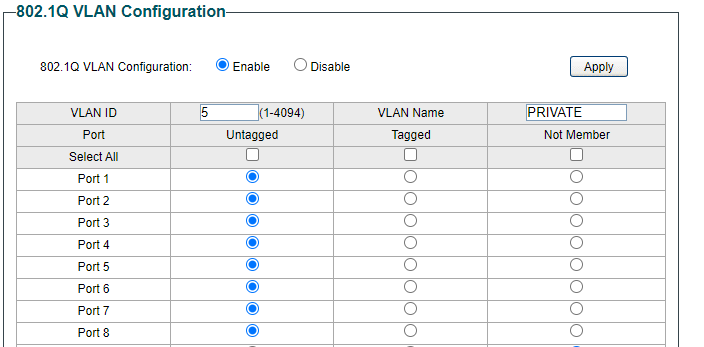
Then Update and Apply and then similarly for COMPANY (using VLAN tag 10)
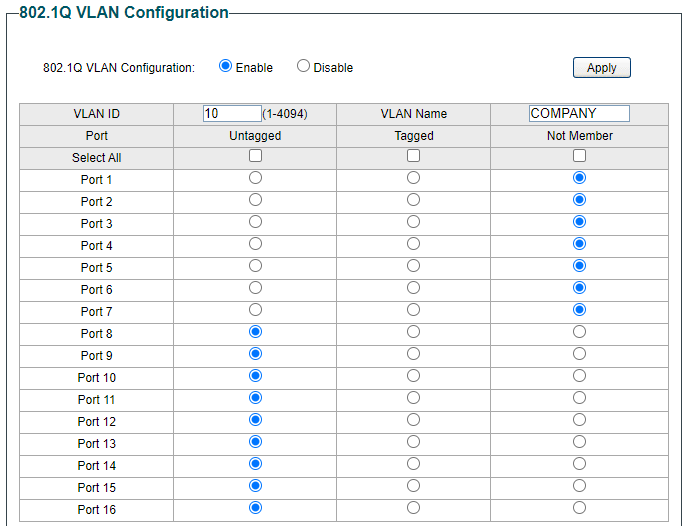
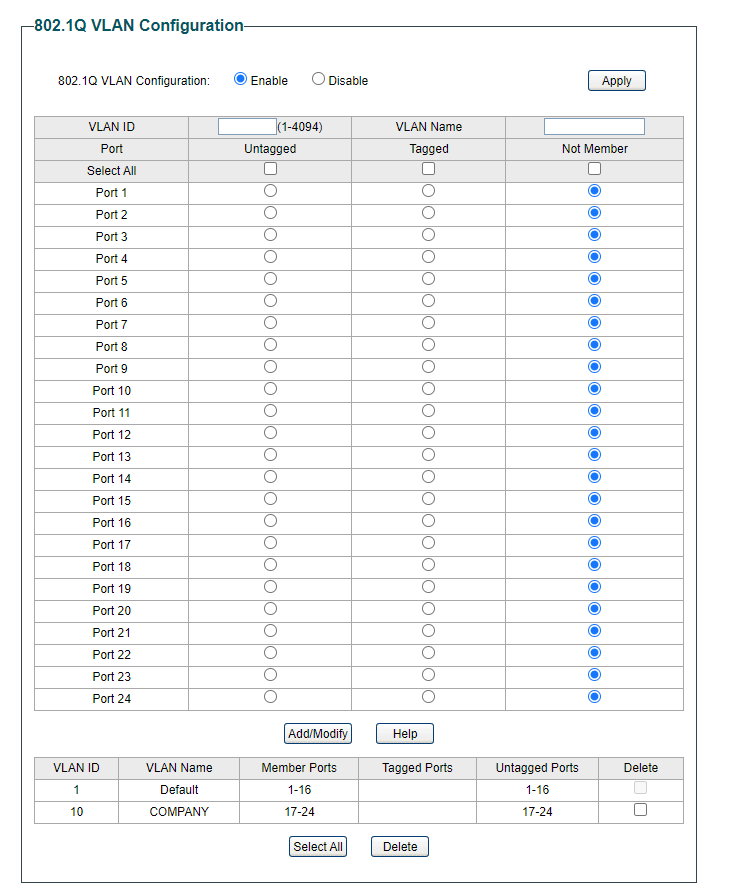
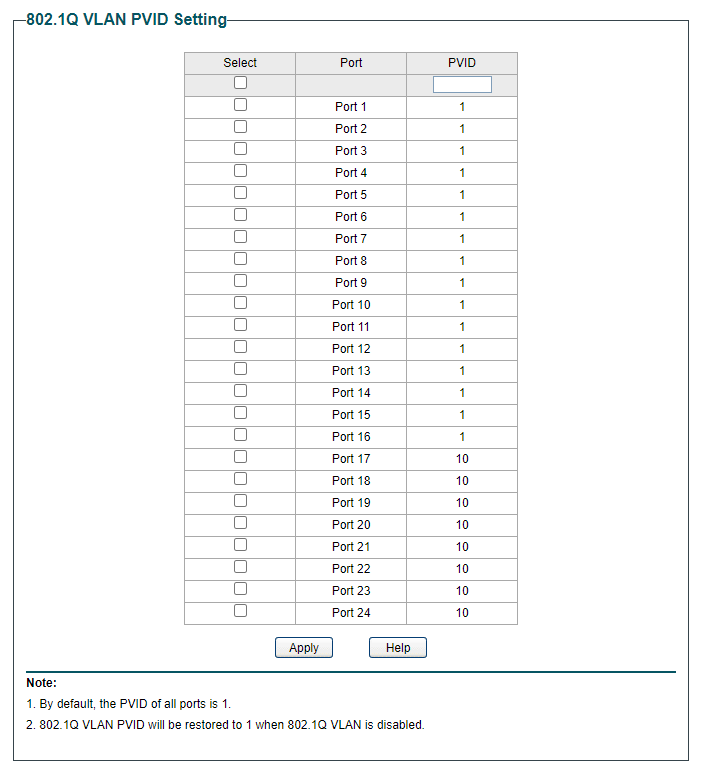
Then on the 802.1 VLAN PVID page you make ports 1-16 members of VLAN 5
And then ports 17 to 24 members of VLAN 10..Like this:
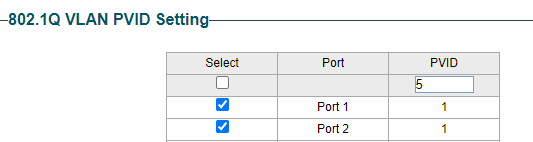
-
@Gblenn yup that works - only thing with those entry level vlan capable switches. He prob wants to use just the default vlan 1 as one of his network. Because this is the vlan the management of the switch will be on..
So for his say lan private, just use vlan 1, then create a new vlan be it 5 or 10 or whatever other ID he wants to use for his lan company..
But I like the idea of just splitting the switch into 2 vlans.. Ie 2 switches in 1 box, which is what vlans are - the ability really to create multiple switches (virtual lans) in one box..
And its also a good idea to keep all the ports in 1 vlan together.. So ports 1-8 are vlan 1, and ports 9-16 are the other vlan.. So ports 1-8 are his lan private "switch" and ports 9-16 are his lan company switch.. then port 1 connected to pfsense lan private interface, and say port 9 connected to his lan company interface on pfsense... Easy peasy, lemon squeezy ;)
edit - personally I would connect his AP to the switch as well.. This allows him then to put wired devices on either his wifi private or company network.. He could still leave his pfsense as is without having to create vlans on it.. And just 2 more uplinks from the switch for wifi private and company.
And if he ever wants more network than his 4 ports, then he can start tagging those vlans and use one of the physical uplinks from switch to pfsense to carry that vlan. I would hope his APs allow for vlans - this way he could place his AP in different parts of the house and client can connect to which ever one is closer and provides the best signal - doesn't matter if client is wifi private or company, etc.
-
@johnpoz Yes I just realized that and was meaning to edit my post accordingly, but you beat me to it...

So what johnpoz is saying is to keep the switch at default VLAN settings for all ports except 17-24. Only those ports do you make the changes I showed in the pictures...
You also need to do one more thing, which is to remove the VLAN 1 membership from those ports. So type 1 in the VLAN ID field and click Not Member for ports 17-24.
Similar to this (using 5-8 as an example for your COMPANY ports)
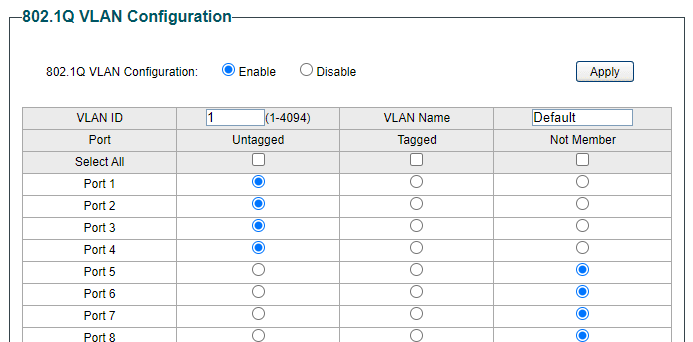
-
@Gblenn great reminder about removing vlan 1 from the ports you put into different vlan.. You would hope the switch would be "smart" enough to not allow you to have more than 1 untagged vlan on the same port.. But those tplinks don't have a great track record for understanding vlans to be honest ;)
There was a whole issue quite some time ago, where they wouldn't even let you remove vlan 1 if you put the port into a different vlan.
-
@johnpoz said in Using Managed Switch for Company and Private Networks:
@Gblenn yup that works - only thing with those entry level vlan capable switches. He prob wants to use just the default vlan 1 as one of his network. Because this is the vlan the management of the switch will be on..
edit - personally I would connect his AP to the switch as well.. This allows him then to put wired devices on either his wifi private or company network.. He could still leave his pfsense as is without having to create vlans on it.. And just 2 more uplinks from the switch for wifi private and company.
Agree but I guess he wants to keep the setup on pfsense untouched, with any rules etc that have already been created for the 4 subnets.
Perhaps move the COMPANY AP to the switch ports 17-24, and drop the WIFI_COMPANY interface on pfsense. There are no static leases on either of the COMPANY networks so why make it more complicated than needed.And if he ever wants more network than his 4 ports, then he can start tagging those vlans and use one of the physical uplinks from switch to pfsense to carry that vlan. I would hope his APs allow for vlans - this way he could place his AP in different parts of the house and client can connect to which ever one is closer and provides the best signal - doesn't matter if client is wifi private or company, etc.
Exactly, and those AP's do actually allow for VLANs and are compatible with Omada centralized management.
-
@Gblenn said in Using Managed Switch for Company and Private Networks:
setup on pfsense untouched, with any rules etc that have already been created for the 4 subnets.
He really wouldn't have to change anything on the pfsense side, he would just move the AP from the port on pfsense to port on the switch.. This would really give him more flexibility going forward.
-
@johnpoz said in Using Managed Switch for Company and Private Networks:
@Gblenn great reminder about removing vlan 1 from the ports you put into different vlan.. You would hope the switch would be "smart" enough to not allow you to have more than 1 untagged vlan on the same port.. But those tplinks don't have a great track record for understanding vlans to be honest ;)
There was a whole issue quite some time ago, where they wouldn't even let you remove vlan 1 if you put the port into a different vlan.
Yes the switch I am using to exemplify is an old one and have had some wierd issues wrt VLAN and picking up, or flipping between two differen IP's for the UI. So sometimes I had to access it via a VLAN and other times I could reach it via the static lease I had given it in pfsense.
I am playing around with another firewall which has it's LAN port connected to a VLAN only existing in my switches. Similar to what this config does with ports 17-24. But apparently it couldn't decide which DHCP server to listen to... I have fixed it now but it was a bit frustrating before I figured out what was going on.
The newer Omada switches I'm using for my network are way better and have not had any problems at all.
-
@johnpoz said in Using Managed Switch for Company and Private Networks:
@Gblenn said in Using Managed Switch for Company and Private Networks:
setup on pfsense untouched, with any rules etc that have already been created for the 4 subnets.
He really wouldn't have to change anything on the pfsense side, he would just move the AP from the port on pfsense to port on the switch.. This would really give him more flexibility going forward.
Agree, like I said about the COMPANY AP, but I suppose there is some reason he wants his wifi separated...
-
Wow you guys have been busy...
Ok I will try and keep to just English.......
Too many years in Sweden....lol
Give me time to digest all of this !
I am so grateful for the support one gets on this forum!
In one word BRILLIANT!bookie56
-
@Gblenn said in Using Managed Switch for Company and Private Networks:
@johnpoz said in Using Managed Switch for Company and Private Networks:
@Gblenn said in Using Managed Switch for Company and Private Networks:
setup on pfsense untouched, with any rules etc that have already been created for the 4 subnets.
He really wouldn't have to change anything on the pfsense side, he would just move the AP from the port on pfsense to port on the switch.. This would really give him more flexibility going forward.
Agree, like I said about the COMPANY AP, but I suppose there is some reason he wants his wifi separated...
No real reason apart from the fact I have a quad and could physically run cables to each AB and LAN networks
-
@bookie56 do you not have enough ports to just connect those 4 ports to your switch... Which then would give you more flexibility..
-
@johnpoz Can we leave at it is for now....

Here are the two settings now:
-
I have gone back to pfsense and added an IPv4 address and then in DHCP Server given it a range ...because I have no need for so many gone from 192.168.121.2 to 192.168.121.25 (example)
The existing firewall rules I had help with.....
What rules do I need to stop this network talking to LAN_PRIVATE and WIFI_PRIVATE?bookie56
-
@bookie56 Under Firewall > Rules you have the LAN_COMPANY and WIFI_COMPANY tabs.
Create new block rules above the allow all rule that look similar to this. In my case it's my GuestVLAN that I don't want accessing e.g. the IoT-network.
Select Block and the interface is your LAN_COMPANY, protocol any and source any.
Then it's a matter of selecting the destination you want to block, in this case you would pick LAN_PRIVATE and click Save.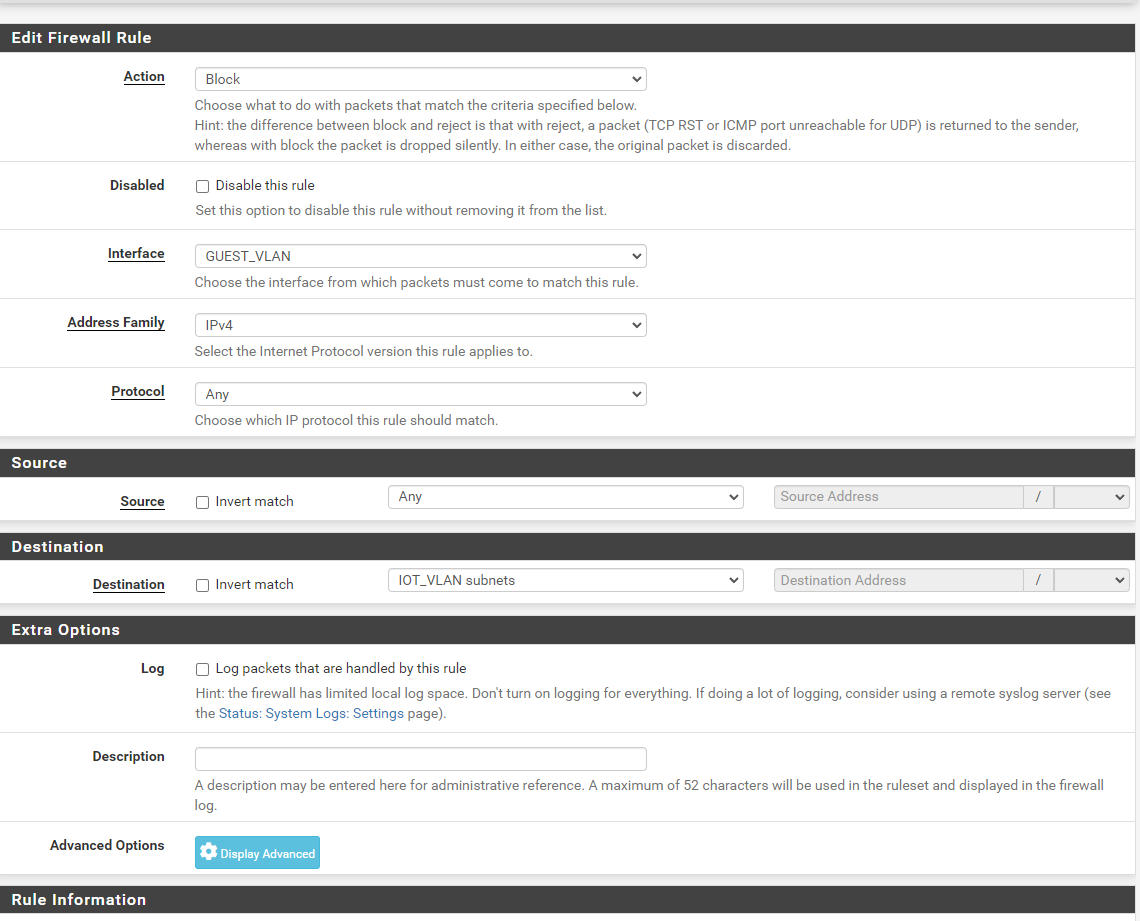
Then you create one more looking exactly the same but select WIFI_PRIVATE as the destination you want to block. Make sure they end up above the allow rule.
To test that it works you can try pinging anything on your PRIVATE netwórk from one of your COMPANY PC's.
-
@bookie56 said in Using Managed Switch for Company and Private Networks:
Can we leave at it is for now
sure.. whatever you feel comfortable with doing, its your network..
So your lan private and lan company are working now.. depending on what port you plug them into on your switch? That switch config looks correct to me for just splitting the switch into 2 virtual switches.
-
@Gblenn said in Using Managed Switch for Company and Private Networks:
@bookie56 Under Firewall > Rules you have the LAN_COMPANY and WIFI_COMPANY tabs.
Create new block rules above the allow all rule that look similar to this. In my case it's my GuestVLAN that I don't want accessing e.g. the IoT-network.

Select Block and the interface is your LAN_COMPANY, protocol any and source any.
Then it's a matter of selecting the destination you want to block, in this case you would pick LAN_PRIVATE and click Save.
Then you create one more looking exactly the same but select WIFI_PRIVATE as the destination you want to block. Make sure they end up above the allow rule.
To test that it works you can try pinging anything on your PRIVATE netwórk from one of your COMPANY PC's.
Sorry not understanding this....I have fire rules implemented from LAN_COMPANY and WIFI-COMPANYnot having contact with my private network....but don't I need a rule for the VLAN? Or does that automaticaly fall under the rules for LAN_COMPANY and WIFI_COMPANY
bookie56
-
@bookie56 said in Using Managed Switch for Company and Private Networks:
but don't I need a rule for the VLAN?
what vlans - you didn't create any vlans on pfsense - did you? The vlans are only on your switch.. to keep those networks at layer 2 isolated from each other. At layer 3, pfsense would filter any traffic trying to be routed across pfsense.
I thought you only had 4 networks on pfsense on your quad port nic, your lan private and company, and then wifi private and company that you plug your AP into.
So 4 interfaces, for these 4 networks.. This is where you would create rules.. There are no rules you would put on your switch.. The very act of creating a vlan on the switch isolates those ports in vlan X from vlan Y ports at layer 2.
But if you don not want lan private to talk to any of your 3 other networks, then you would need rule(s) to do that. You could do it in 1 rule if you wanted with alias that contains the networks you don't want to talk to.. When your creating rules that block access to your other networks its common to just create a alias that contains all of the rfc1918 space. 10.0.0.0/8, 192.168.0.0/16 and 172.16.0.0/12 this way you can use the alias in your block rule, and this network would not be able to talk to any other networks that you currently have or in the future might add.
You just need rules above this block rule that allows what you want.. Here is an example of a locked down network that can not talk to any other network I have on pfsense, nor any of pfsense other IPs, like say its public IP..
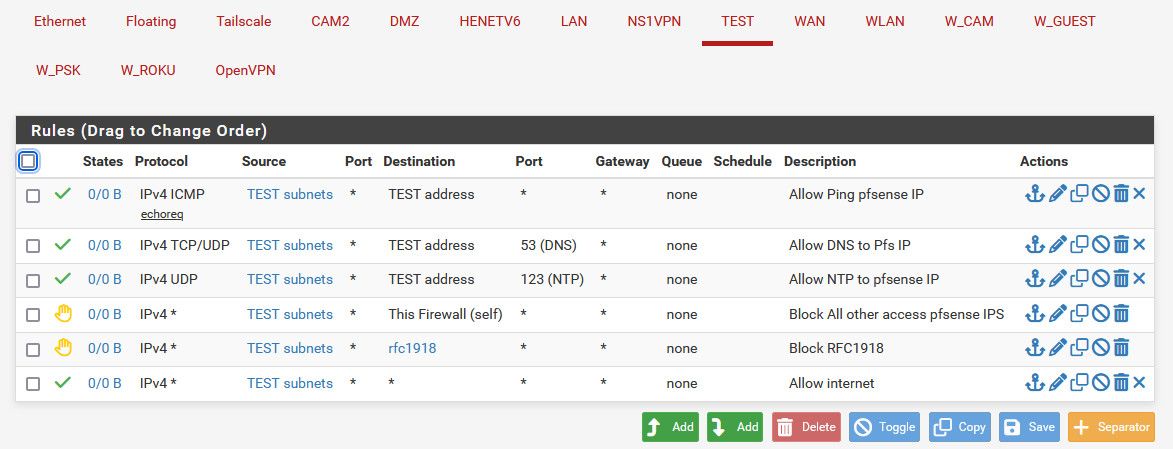
Rules are evaluated top down as traffic interfaces the pfsense interface from the network that interface is attached too, first rule to trigger wins and no other rules are evaluated
These rules allow devices on my "test" network to ping pfsense IP on the test interface, use dns and ntp to this test interface IP. It then makes sure clients on the test can not talk to any other IPs of pfsense, say the want public IP - or devices on this network would be able to access the pfsense web gui for example on its wan IP which is public. The use of the alias helps if that IP might change in the future to some other public IP.
They then block access to any other rfc1918 addresses - ie my other networks.. And then the last rule is what allows devices on this network to talk to any other IPs, ie the internet.
-
@johnpoz so I don't need a vlan on pfsense?
bookie56