Redirected all DNS to pihole using pfSense. Pihole still showing some hosts as not using the DNS ?
-
I had configured pfSense to redirect all traffic to my pihole. DNS on pfSense is running on forwarder only mode.
I have tested my firewall rules and they seem to be working fine. (You can check my post history if you want to see the rules).However Pihole still shows some devices on my network bypassing it. I do not know how that might be possible ?
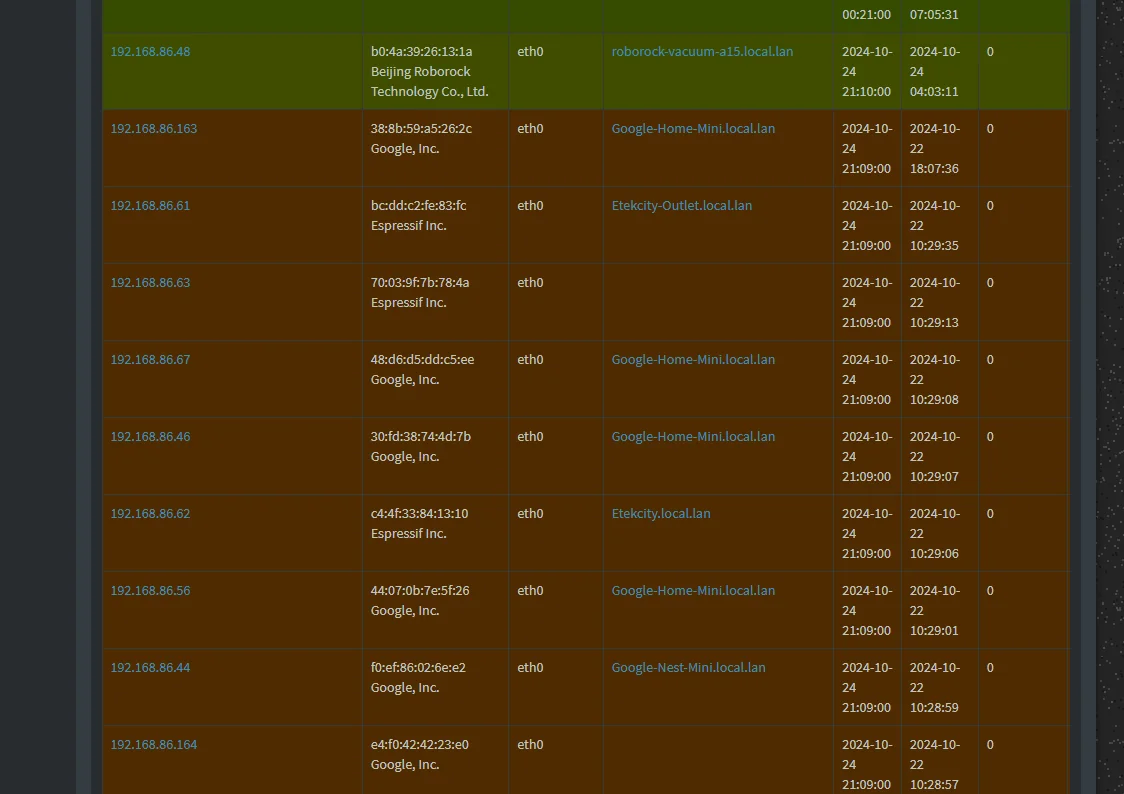
For e.g. my eTeckcity smart plug (192.168.86.62) has only the following connections showing up on pfTop ?
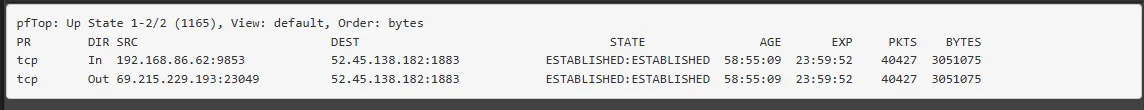
My firewall rules :
NAT
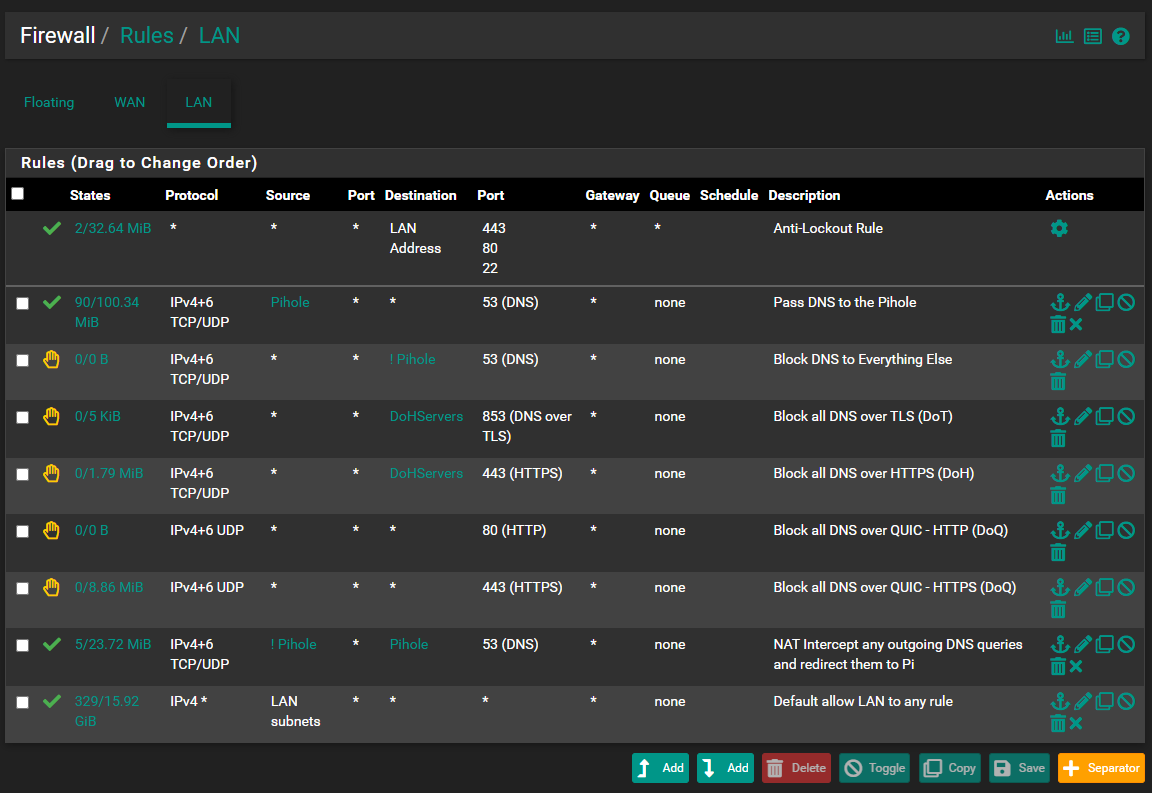
RULES
What am I missing ? How can I redirect the DNS from these devices to my pihole ?
-
@abesh Maybe also check DNSSec (DoT) port 853
And then there is DoH (normal https traffic from browsers DNS settings).//edit: Ah you do... :)
Anything in Floating to immediately apply? I read the order is Floating -> Interface Group -> Interface -
@disi1 Nope, nothing in Floating :( Should I have any ? I am a total noob and have not figured out everything :) I am guessing the Floating rules apply to both interfaces ?
-
@disi1 Updated the rules screenshot. Had made some changes :)
-
@abesh said in Redirected all DNS to pihole using pfSense. Pihole still showing some hosts as not using the DNS ?:
However Pihole still shows some devices on my network bypassing it. I do not know how that might be possible ?
I'm wondering, what this screen shot tell us. How does pihole detect, what's bypassing it?
For e.g. my eTeckcity smart plug (192.168.86.62) has only the following connections showing up on pfTop ?
ditto
This doesn't show a DNS connection. So why do you think, it bypasses the NAT of port 53?Also consider, that the NAT will only work, when you do masquerading on this connections. Otherwise you will run into asymmetric routing and the DNS requests will fail.
-
@viragomann said in Redirected all DNS to pihole using pfSense. Pihole still showing some hosts as not using the DNS ?:
Also consider, that the NAT will only work, when you do masquerading on this connections. Otherwise you will run into asymmetric routing and the DNS requests will fail.
I don't know what Masquerading is, I am pretty new to pfSense. How would I mitigate this situation ?
I have these outbound NAT Rules running in hybrid mode :
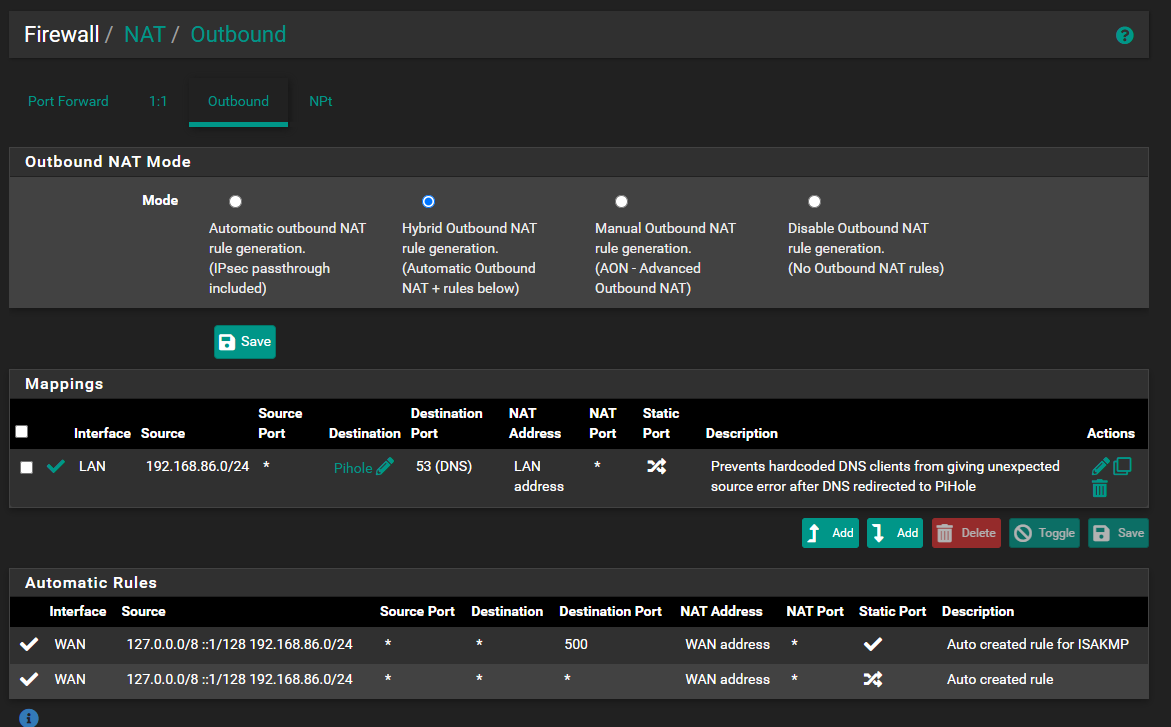
-
@abesh
Yes, that's it. -
@viragomann I can see that mostly all DNS is going through the pihole so dunno why it is showing as those not going through the DNS ?
-
@abesh Pi-hole will highlight devices not using it in red. I don't see any red entries on that first screenshot. Brown simply means that device has not had a query for over 24 hours. Did you see the legend at the bottom of that page which explains this? It could mean that a device has been turned off or not going out to the web, or it could mean that the device only contacts a specific server and it queried it at one point and then stored it in its local DNS cache. The devices could also be using DoH or DoT which your port 53 rules on the NAT will not catch.
You can keep the pfsense DNS settings at their default. You don't have to put it in forwarding mode. I would put that back the way it was. It is best to let pfsense do the queries to the root servers directly. Leave DNS servers as 127.0.0.1 and ::1. Then you have to set Pi-hole to use pfsense as the DNS server. Then in the DHCP settings of pfsense, make sure you enter the Pi-hole address as the DNS server so that any client that get an IP will be using Pi-hole unless they have their own settings which must manually be changed.
-
@Raffi_ Thanks a lot for the explanation of the Brown entries. That makes a lot of sense.
Actually I run unbound locally on pihole and use that. That's why the DNS resolver is in FW only mode. -
@abesh Oh I see. I never tried running unbound on Pi-hole. So you're doing the reverse of what I suggested? Which device is acting as your DHCP server? pfsense or Pi-hole? Is the DHCP server pushing the Pi-hole or pfsense IP for DNS?
-
@Raffi_ So pfSense is the DHCP server and it hands out the pihole's address as the DNS server. The pfSense DNS resolver is configured to forward queries to pihole only. I need the pfSense DNS to resolve local names. Since pihole is not the DHCP server only IPs show up in pihole logs instead of hostnames if I don't do it this way. Pihole queries it's own unbound server at 127.0.0.1#5335 and responds back to the DNS queries.
-
@abesh Interesting sounds a little more round about. To be honest, I can't even see where to enable unbound on Pi-hole natively. Is that officially supported by the Pi-hole project? I'm curious because I must be missing that?
-
@Raffi_ The method is not much different than what I did.
https://forum.netgate.com/topic/156453/pfsense-dns-redirect-to-local-dns-server?_=1663853296484There are plenty of docs on how to install unbound on PiHole. I did it and it works well.
-
@Raffi_ Yup, officially supported by Pihole. Here's the documentation : https://docs.pi-hole.net/guides/dns/unbound/
-
@AndyRH Hey Andy ! Yes, thanks to you I could get this up and running :)
-
@abesh said in Redirected all DNS to pihole using pfSense. Pihole still showing some hosts as not using the DNS ?:
The pfSense DNS resolver is configured to forward queries to pihole only. I need the pfSense DNS to resolve local names.
The DNS Resolver on pfSense will never get a request, since you forward any to the pihole.
-
@viragomann Agree. Maybe I should turn off the resolver and see what happens ?
-
@abesh
You should rather redirect any traffic to pfSense. So it's treated by the DNS resolver and host overrides will take place, while other requests are forwarded to the pihole from the Resolver. -
@abesh Seems your setup is done correctly. Have you considered that the IP of those sessions might be hardcoded into the missing device?
Otherwise it is likely some unknown DNS over HTTPS server you are not blocking - or vendor specific nameresolution method - in play.