Redirected all DNS to pihole using pfSense. Pihole still showing some hosts as not using the DNS ?
-
@viragomann It was hardcoded application IP endpoint I was reffering to - not hardcoded DNS. Aka: The APP on the device just contacts the IP directly - no DNS resolution beforehand.
DoH is a game of Whack a Mole - as is DoT even though most of them can be blocked by blocking port 853.
Unfortunately this is where everything is going (in the name of privacy - even though it is mostly used by vendors to make sure they have the revenue of selling your data rather than your ISP)
-
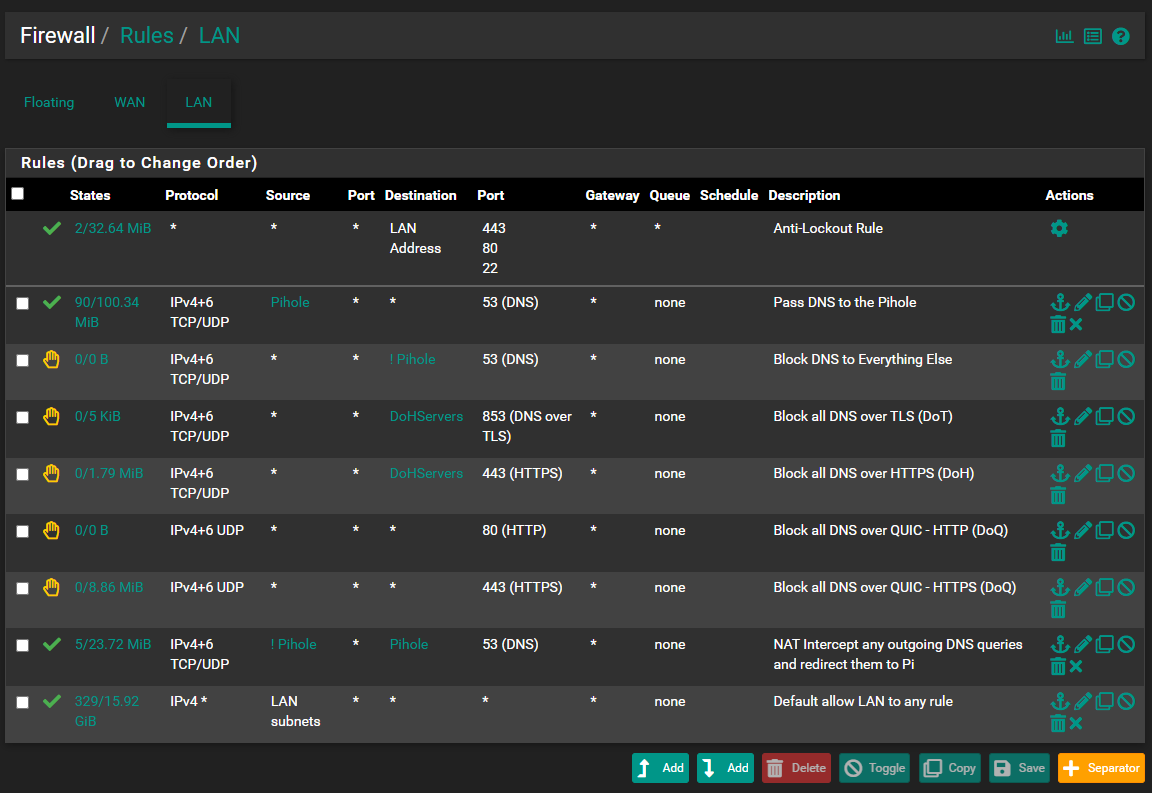
@viragomann I think it will, if it needs to look up hostnames :) I have two lists (you can see one on the Rules screenshot). I block IPs of DoH servers in pfSense and block domains in piHole.
-
@keyser said in Redirected all DNS to pihole using pfSense. Pihole still showing some hosts as not using the DNS ?:
It was hardcoded application IP endpoint I was reffering to - not hardcoded DNS. Aka: The APP on the device just contacts the IP directly - no DNS resolution beforehand.
Got it. There is not really much you can to on the DNS to prohibit this, if it's not used then.
-
@viragomann @disi1 @AndyRH @keyser So from debugging this a bit it seems that these might be showing up as "not using pihole" because maybe they send their DNS queries to pfSense which is then forwarded to pihole. Pihole thinks it is coming from pfSense and not the device itself. How do I configure pfSense so that it also send the device hostnames when forwarding the request ?
-
@abesh said in Redirected all DNS to pihole using pfSense. Pihole still showing some hosts as not using the DNS ?:
@viragomann @disi1 @AndyRH @keyser So from debugging this a bit it seems that these might be showing up as "not using pihole" because maybe they send their DNS queries to pfSense which is then forwarded to pihole. Pihole thinks it is coming from pfSense and not the device itself. How do I configure pfSense so that it also send the device hostnames when forwarding the request ?
This is beginning to sound like an Abbott and Costello sketch. I hope no one queried who's on first. Sorry bad joke.
Have you tried my original suggestion of allowing pfsense to run unbound and then point pi-hole to it?
-
@Raffi_ That was actually the first setup that I ran and I moved on to this :)
-
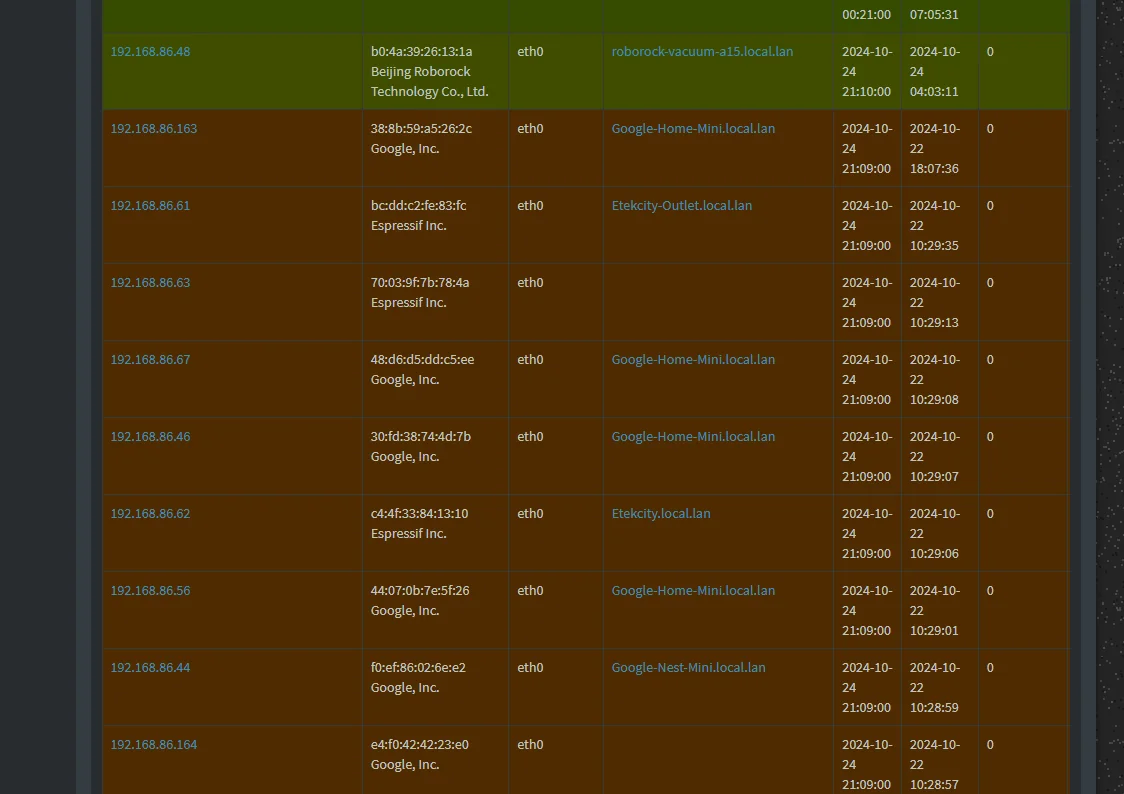
@abesh And we're still talking about brown or red entries? I saw all brown on your screen shot.
And to be clear, you had the same exact issue with that original setup which prompted you to try something else or were you trying to address something else? In my experience there might be a couple of devices which do not use pi-hole. How many exactly are you noticing?
-
@Raffi_ Yeah, let me wait and observe a bit.
-
@abesh said in Redirected all DNS to pihole using pfSense. Pihole still showing some hosts as not using the DNS ?:
Pihole thinks it is coming from pfSense and not the device itself.
@Raffi_ said in Redirected all DNS to pihole using pfSense. Pihole still showing some hosts as not using the DNS ?:
Have you tried my original suggestion of allowing pfsense to run unbound and then point pi-hole to it?
I don't expect, that this makes any difference on the pihole seeing requests coming from pfSense.(?)
@abesh
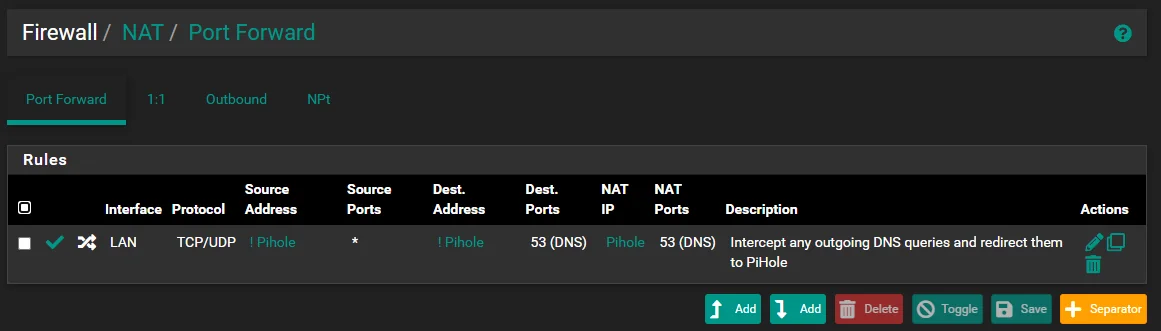
If you want to see the origin client IPs, you have put the pihole into a separated network segment on a different interface, so that you can get rid of the masquerading rule. -
@viragomann That makes a lot of sense. Thank you :)
-
@viragomann Would I get anything else other than local domain name resolution for forwarded queries if I move the pihole to a different subnet ? If not I would just like to keep it as is :)
-
@abesh
There is no benefit else, I can think of at the moment. -
@viragomann Thank you so much !!!
-
@abesh said in Redirected all DNS to pihole using pfSense. Pihole still showing some hosts as not using the DNS ?:
How do I configure pfSense so that it also send the device hostnames when forwarding the request ?
It will never send the hostname. I was not able to figure out how to send the requesting IP. I do not think it is possible because pfSense is "proxying" the request. Even hosts requesting from wrong DNS servers on different subnets show up as pfSense.
DoH is mostly blocked with pfBlocker and DoT is blocked by blocking 853. Not perfect. -
@AndyRH Apparently possible in OPNSense so should also be possible in pfSense. I need to go through this post in detail when I have a bit of time : https://forum.opnsense.org/index.php?topic=34907.0
-
@abesh not exactly sure what your seeing and what you expect..
If I redirect dns queries to my pihole I see who did the query.
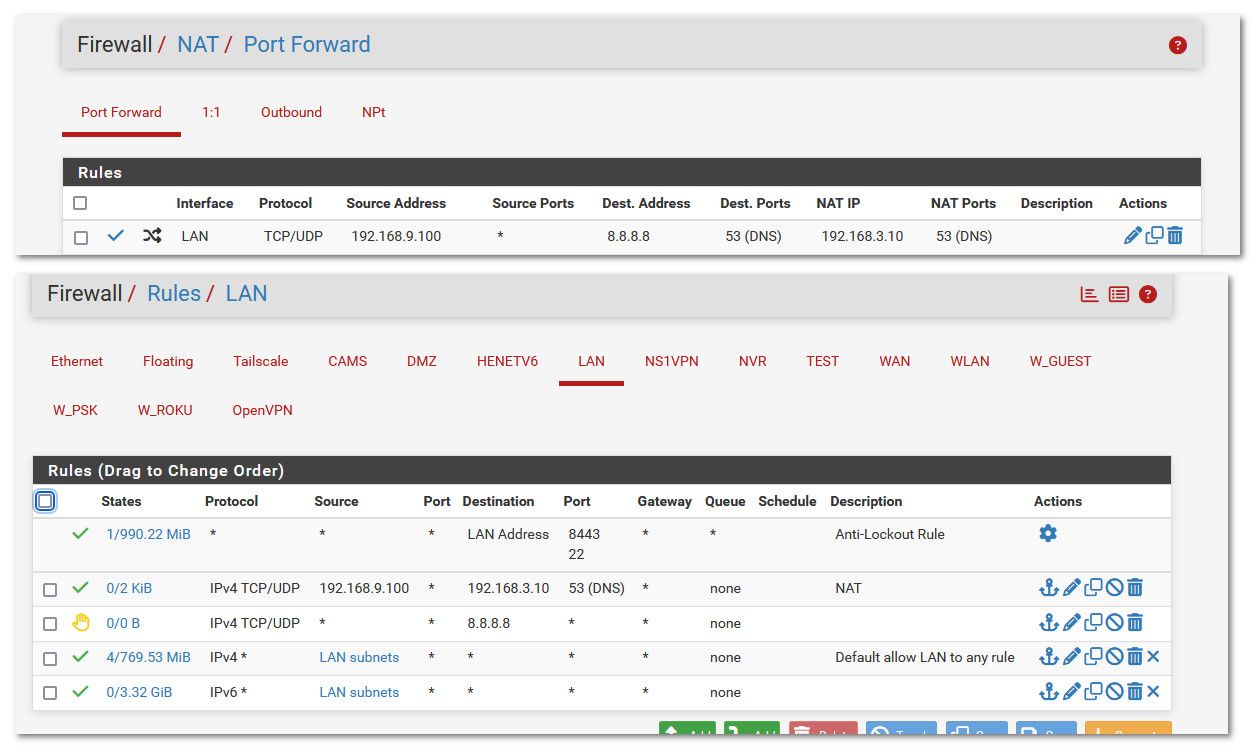
My pc i9-win.home.arpa is 192.168.9.100

This works when your pihole is on a different network than your client.. If the client is on the same network as your pihole your most likely going to run into issues with answer coming from different IP than where the client sent the traffic. Unless you forward to loopback and have unbound query the pihole, this will look like it came from pfsense IP vs the client.
You might be able to use
send-client-subnet:
In your unbound config.. But not sure if that has been enabled in the unbound on pfsense.. I would have to do some testing.
Your best option if you want to forward direct to pihole, and see what source IP asked for something, is put your pihole on a different vlan than your clients.
-
Likely not relevant, but I use Pihole as the LAN DNS and forward to pfSense where it also hits pfBlocker and Unbound (Resolver).
-
@provels that is the better way to do it if you ask me.. That is what I do as well.. Clients ask pihole, pihole asks unbound on pfsense, unbound resolves.
-
@johnpoz Not to trash pfB, but I love the simplicity, efficiency, and ease of management of Pihole, especially when I see numbers like this from a minuscule VM.

-
@provels yeah not meaning to trash pfb either, I use it for my aliases and its great, but been using pihole long time, and yeah the eye candy is nice, etc. etc..