Is UPnP the reason my games don't work?
-
Hello, I've been trying to get UPnP working for a few days now and have had little luck so far. I'm on 2.7.2-RELEASE and my firewall has a public IP from my ISP. Behind that I have an ASUS RT-AXE7800 router in access point mode which I have connected my PC wirelessly to.
In particular, I'm trying to play Pavlov VR, but I also tried and failed to play among us, COD BO3 and No Mans Sky. Whenever I try to load in a match I see a lot of blocked requests from my PC to different addresses (blocked by the default deny rule):

I also don't see any active UPnP rules when I start a match. However, what I find so weird, is that when I start my Hamachi client, there are two UPnP rules that get made:

This led me to believe that UPnP (kind of) works? And if so, I am even more confused as to why all the UPnP requests get blocked by the default rule when I try to play a game. When I add an allow any to any rule, I can play the games just fine and the previously blocked requests get passed through that rule. Could there be something else that causes my games to not work? These are my settings for UPnP:

I have not enabled STUN and also no ACL (I first want to get it working before adding an ACL). I have also enabled Pure NAT

I have also enabled static port for the outbound NAT (the games alias is the static IP of my PC):

I have also added pass rules for the UPnP ports. The rule below is to allow the TCP port for the miniupnpd daemon
 .
.So... Is it my UPnP settings that could be blocking my games? Or is it something else? I also have Squid, Snort and PFBlockerNG running, but the blocked requests come from the default deny any rule.
Any help would be greatly appreciated. Thank you in advance! -
What are your firewall rules ?
-
@Uglybrian These are the rules for my OPT2 interface (where my router is connected to) interface:


And these are for my WAN:

To be sure, this is the rule that blocked the requests:

-
Your DNS rule, try OPT2 addressed instead of this fire wall. You can see by the 0/0 that the rule is not affective.
-
@Uglybrian Like this?

Hmm it's still unaffective it seems, and the requests still get blocked -
YES, but sorry it didnt work, I took a second look at your rule set and see you have more DNS rules below.
To me it looks like you have something blocking UDP in your rule set. I am basing this on when you put a any/any rule it works. I will take a third look and see if i spot something. -
@Uglybrian Thank you very much! If I need to provide more screenshots or information let me know!
Another thing I maybe should mention is that I have a PiHole on OPT1 that is set as my DNS server (10.10.10.102) -
Just saw, on the firewall rule that you changed. it should be to addresses not to subnet.
like this: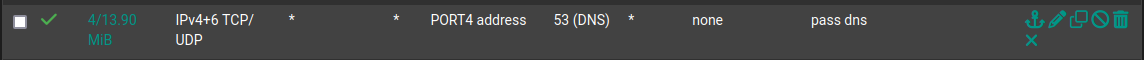
-
@Uglybrian Aah okay I have now changed it to this:

Does the source also need to be any? Because I still see blocked requests in the firewall logsEDIT: that also doesn't seem to be the solution:

-
Is port 22325 in your allowed port aliases?
The source in your DNS firewall rule be either be any or subnets.I have mine as any because i am using this pfSense configuration recipes: https://docs.netgate.com/pfsense/en/latest/recipes/dns-block-external.html
Also for your reference and to double check your settings:
https://docs.netgate.com/pfsense/en/latest/services/upnp.html -
@Uglybrian I followed the UPnP guide from the docs, that's where I got my original configuration from: enable UPnP, no STUN because my WAN interface has a public IP, and enable static port for the outbound NAT rule. The 22325 is not in my alias, so I added it, but I still see the blocked requests and no active UPnP rules :(
I also checked if it was the pfBlockerNG rules, but they don't change anything
-
@semtex99 With UPnP enabled you shouldn't have to set static port, it should work with Outbound NAT in Auto settings. If you play CoD you should see port 3074 show up in the UPnP status page, and probably 28960 as well.
You should not have to add any pass rules for the UPnP ports. You selected the OPT2 interface so that is what it is listening to.You also have an awful lot of rules btw... What is it that you are trying to achieve... why do you have to "allow" pinging 8.8.8.8 for example. Or any of the other allow rules for various thing?
Normally when you have multiple networks, VLAN or using physical ports like you do, you may have general block rules to limit access between them. But if you are ok with OPT2 reaching LAN and OPT1 and reverse, then all you need is one single allow OPT2 to any rule at the bottom, that's it.
And since that one rule is missing, unless you add rules for all the ports that you may or may not need, you will have it blocked by the default rule...IF you run something like PiHole on LAN and want OPT2 devices to use that, yes then you can add a rule sending 53 to the PiHole IP. However, if you use pfsense as DNS, there is no need to add a rule for DNS. It's already the default setting in the resolver (or forwarder), so it will listen and respond on OPT2 already.
The rules to allow from OPT1 and LAN have no effect when placed under OPT2 rules. They need to be under their respective interface ruleset. See the 0/0 B on the left...My guess is that if you cleared up and simplified your rules, a lot, you will get UPnP working fine. Start by putting an allow OPT2 to any rule, just under the pfBlocker rules.
-
@Gblenn Thank you for the detailed explaination! I think you're right, and my initial understanding of how to go about rules was the wrong way around.
My understanding was that it would be considered "unsafe" to allow a pass from OPT2 to any rule, because I read a comment on reddit where someone said that would defeat the purpose of the firewall because it would undo the default deny behaviour. This was how I figured rules should work: deny anything by default and only explicitly allow things you need.
If you say that's better to allow a pass from OPT2 to any rule then that would indeed solve my problem! As i've tried that and that makes it work, but I was under the understanding that it would be bad practice.
To summarize, your advice would be to add a pass from OPT2 to any rule, and then add more rules that block requests below it to fit my needs, instead of what I have now, which is the other way around by going with the default deny behaviour and adding rules for things I want to allow?
-
As an example here is a simplified rule set I use for my iot network.
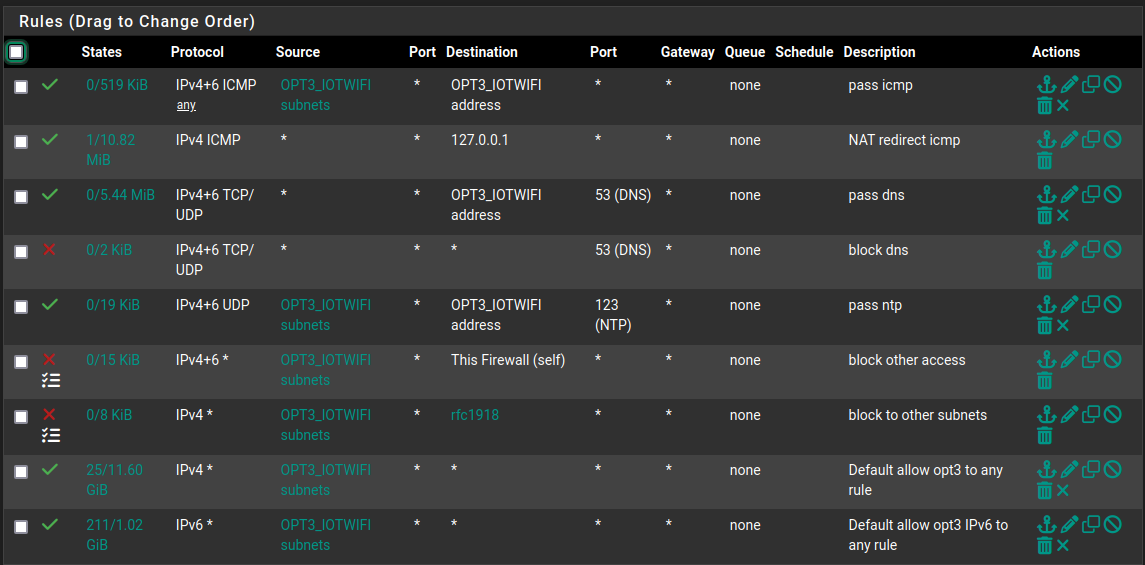
-
@semtex99 said in Is UPnP the reason my games don't work?:
considered "unsafe" to allow a pass from OPT2 to any rule, because I read a comment on reddit where someone said that would defeat the purpose of the firewall because it would undo the default deny behaviour.
Caution reading Reddit. You will tend to get better help here than Reddit.
LAN is born with a default any:any rule. This is outbound. The main purpose of a home firewall is to prevent access in, not out.I suggest you think of your total rules set in the terms of "Outbound block what I want blocked, allow all else." "Inbound, block it all unless I have a reason."
-
@AndyRH @Uglybrian Thanks for the advice! I cleaned up my rules a lot and now have this:

And now the games do in fact seem to be working! Any other things I should consider?Thank you all very much!
-
@semtex99 Looks better now, but there are a few things you might want to consider...
The first rule doesn't do anything since traffic with source and destination OPT2, will not go into pfsense, therefore the 0/0. So remove this rule...
Second rule is your key to getting devices use PiHole so this is good. It's your "policy routing" sending all DNS requests to your PiHole, and then stops processing anothing port "53", perfect!
Third rule doesn't do anything since the second rule already took care of things, remove this.
What is it with SSH that you are trying to block, or protect? Allowing SSH to LAN and OPT1 is catered for by the last, allow to any rule. And a device SSHing from an OPT2 device to another device on OPT2 wouldn't hit the firewall...
Still there seems to be some traffic hitting this Block rule so is there something trying to access something on WAN perhaps? If you want to block that speficially, then change the block rule to have Destination WAN and port 22. And just remove the two Allow SSH rules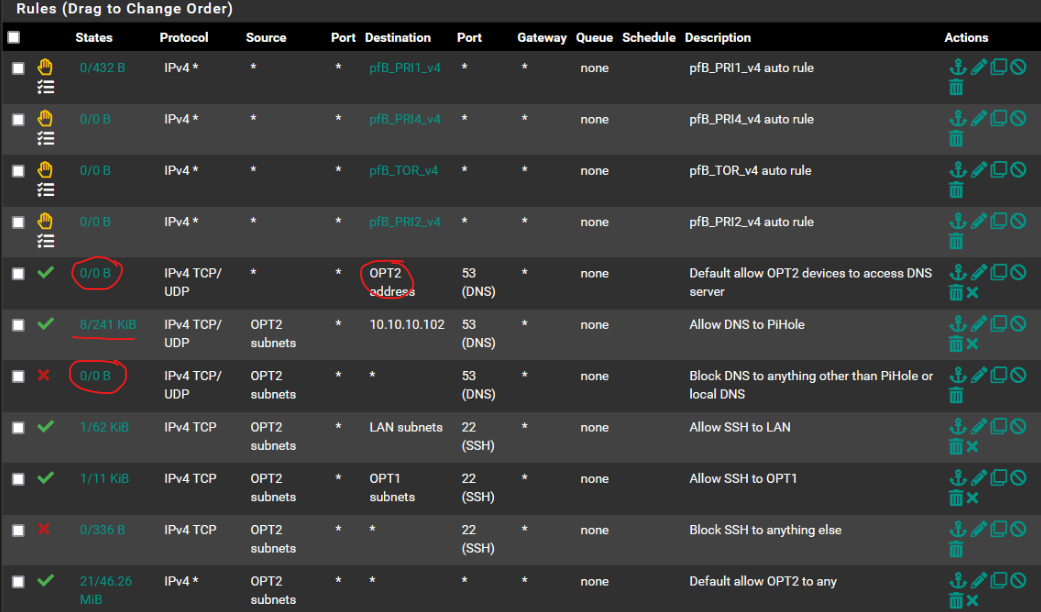
-
@Gblenn Great! I've simplified it even more:

The traffic hitting the block SSH rule was me testing SSH access when I had set the other two rules to OPT2 address by mistake. I want to block SSH access to any destination that isn't in my network, just as a precaution.I think I now understand a bit how the rules are processed. I first thought that any requests that don't hit a specific rule just go down through the rules until it finds one that matches, that's why I had the other block DNS rule: I thought that if a request did not get passed by the pihole rule, it would go through until it hit the allow any rule, and thus be passed. But with your explanation it seems that all traffic with destination port 53 will be blocked if it doesn't meet the requirements for the pihole rule for port 53, and thus won't get processed through the other rules right? Because that rule handles port 53; after it gets blocked by that rule, it isn't processed by any other rules?
-
@semtex99 Yes now it's way simpler and still achieving what you want.
Some thoughts and considerations however...
First of all, without any rule at all under e.g. OPT2, you would still have the default block rule, which blocks EVERYTHING. You don't see it, but it's there...
And this is why we start by adding the "default allow OPT2 to any" rule. It was that default block rule creating problems for you earlier... What CAN work is to start creating allow rules for specific things but, as you have seen already, it makes for a ton of rules and gets complicated very quickly.
And since like @AndyRH said, the LAN side is normally where we want to allow things, it's simpler to start by adding that allow OPT2 to any rule.Now, about the DNS rule though... I'm guessing you have set your PiHole as the DNS for all devices in OPT2, which is done using it's IP, similar to what I have here (in my DHCP Server settings)?
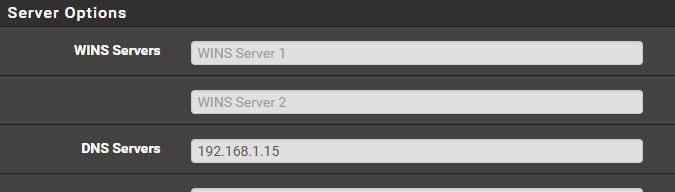
Since you have the allow all rule at the bottom, this will still work, so that rule is sort of redundant. BUT, before you remove it, perhaps you need to consider what your goal is with having three separate networks, LAN, OPT1 and OPT2.
If there are some thoughts about security in this split you have done, then a next step would be to start thinking about what limitations you want to put on each segment. As I wrote earlier, it's common to block communication between segments. It's sort of why we introduce them, like perhaps wifi, IoT/Camera subnets etc. So if we assume OPT2 is used for all your wifi and OPT1 for Cameras and smart devices, you may want to consider two blocking rules in each of those rule sets. Two each because you want to block access to the other two, like LAN and OPT1 from OPT2.
For example, here are the rules in my wifi segment (VLAN) that I have. I do a general blocking of access to any of the other segments from wifi. And then I have allow rules for access only to specific targets like my AdGuard Home server (like PiHole) as well as Chromecast above them. Without those blocking rules, I wouldn't need the allow rules, since the allow all exists at the bottom...
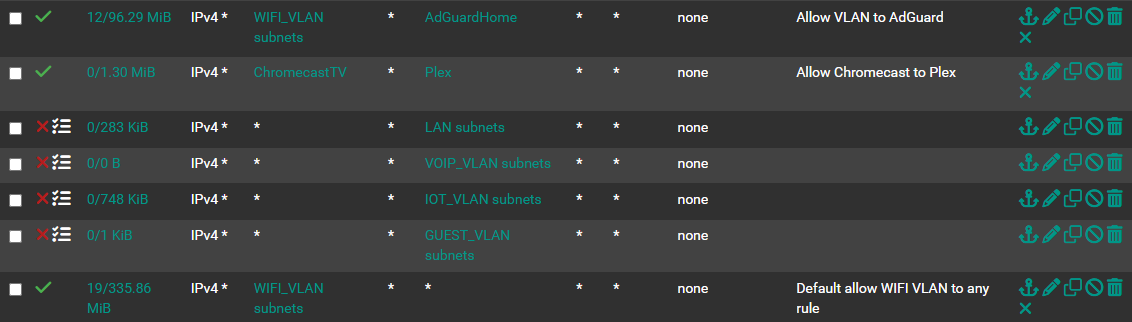
If you have a printer that is connected over wifi, and want to print from a LAN connected PC, you probably need to look at adding the Avahi package. And set it up so that it targets LAN and OPT2 in your case. Perhaps even specify the IP in the printer settings on the LAN connected PC(s).
-
@semtex99 In addition to the rules discussion, there is the gaming aspect...
First of all, you mentioned you have your PC connected over wifi, which isn't an optimal solution. I'd look for ways to connect via cable, but sometimes that's of course not possible, or too difficult.
Although what I said about not needing Static Ports for UPnP to work, it may still be beneficial... I have noticed that it speeds up launching of some games a little bit. Probably since it simplifies some of the negotiations that the games need to make with the servers, about which ports to use.
pfsense will typically give you what's called Symmetric NAT but changing to static ports, you get Port Restricted Cone NAT. You can test it with this tool : https://www.checkmynat.com/. And the rule you used makes sure it only applies to your gaming devices that you put in that alias "games".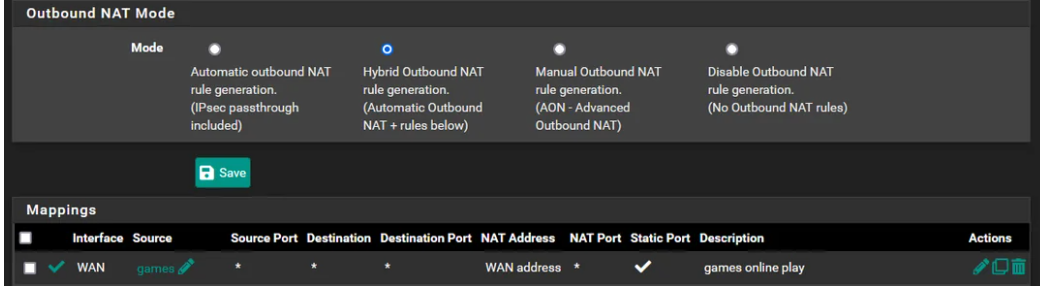
Finally, since UPnP does indeed reduce security in your network it's good practice to use the ACL rules. Which you already mentioned was your intention.
With some testing, and checking what ports various games require and checking the status page for UPnP when playing, you can limit the allowed ports dramatically. As an example, I have found that I only need to allow ports 3074-3076 and 28960-28964 for my PC in order for all my CoD games to work and get Open NAT. No need to allow the full 1024-65534 range...