set up pfSense as additional gateway into VPNs
-
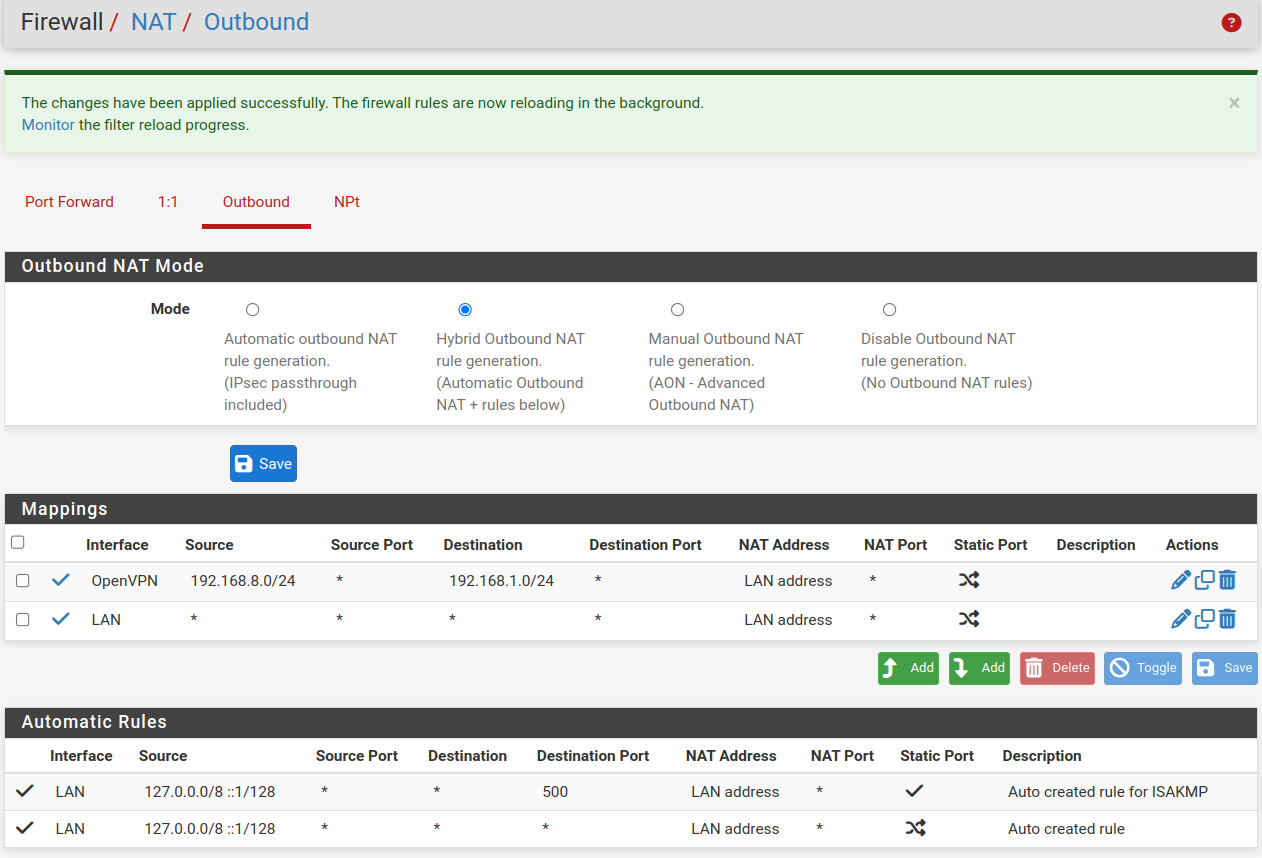
currently it seems to work after adding a NAT outbound rule on the client
OpenVPN 192.168.8.0/24 * 192.168.1.0/24
we test now
-
That outbound rule editing changed something, as if there was something changed under the hood.
Right now the admin there is able to access systems on the other side of the tunnel, as intended.
Nothing changed on the OpenVPN server, btw.
That NATing isn't fully correct still
What I'd like to have:
- server side IP should be able to ping a PC on the client side
- server side VM should be able to access a system on the client side, with a mapped IP in the client LAN
currently I have this, and rebooted for a check, the admin is able to access a server VM via RDP: GREAT, but not 100% yet ;-)
THANKS so far, I think I need some time afk now soon
-
@sgw
Yeah, outbound NAT rules (masquerading) can be used to circumvent missing routes.
I'd rather set the routes properly, but depends on the use-case. -
@viragomann I agree but I repeat: where to set these routes? See question above. Thanks.
-
@sgw
The "Remote networks" field is only available in peer to peer server mode. But this is, what you should set up for your use case. -
@viragomann Ah, that explains why it feels like barking up the wrong tree ;-)
I hope I can run that in parallel to the other openvpn-server? (separate port, sure).
Thanks so far, have a nice weekend!
-
@sgw
Yes, of course you can run multiple OpenVPN servers for different purposes. -
I set that up on the server site pfSense.
For the peer to peer VPN there is no Client Export, so I assume I have to set up a Server on the other site as well, also in Peer2Peer-Mode? For sure I browse the docs in a minute.
looking forward to solve this ;-)
EDIT: I see, seems I can follow this for example. So not a 2nd server but a specific client config. Will try monday or so.
-
I have it working mostly.
One more question: I found out that CSCs won't work for peer-to-peer-OpenVPN?
What is the way to limit access then?
If I have multiple vpn-users connecting to one ovpn-server I could only set fw-rules on the client-side of the vpn-tunnel, right?
thanks for additional insights here, I am right before setting up the 2nd client to test things in parallel (for sure with a 2nd user etc ;-) )
EDIT: CSC seems to work .. dunno where their admin had that info. Still testing things, good progress.
-
The CSC seems to work when assigning a specific tunnel IP to the client.
But it seems not to work for setting (all) the routes, and for limiting the access:
The wish would be to set only one IP for the client to be routed etc
I solved it for now by adding fw-rules on the OpenVPN-interface on the server side:
- allow traffic from tunnel-IP x.y to server-VM a.b.c
- reject traffic from tunnel-subnet to rest of server-LAN
Seems to work right now, suggestions welcome ;-)