Incoming connections to pfsense box from Facebook?
-
@rasputinthegreatest it could just be your isp as well.. But normally a reboot wouldn't fix that, but it would break all current connections if something was uploading in the background.
Do you run any p2p software? Windows has the ability to share out updates - even to the public internet, you could look there.. But the traffic graphs can show top talking..
example - here I kicked off a speedtest so you could see example of showing top talking..
You can see when it was uploading, my 192.168.9.100 pc - my upload bandwidth is 50mbps..
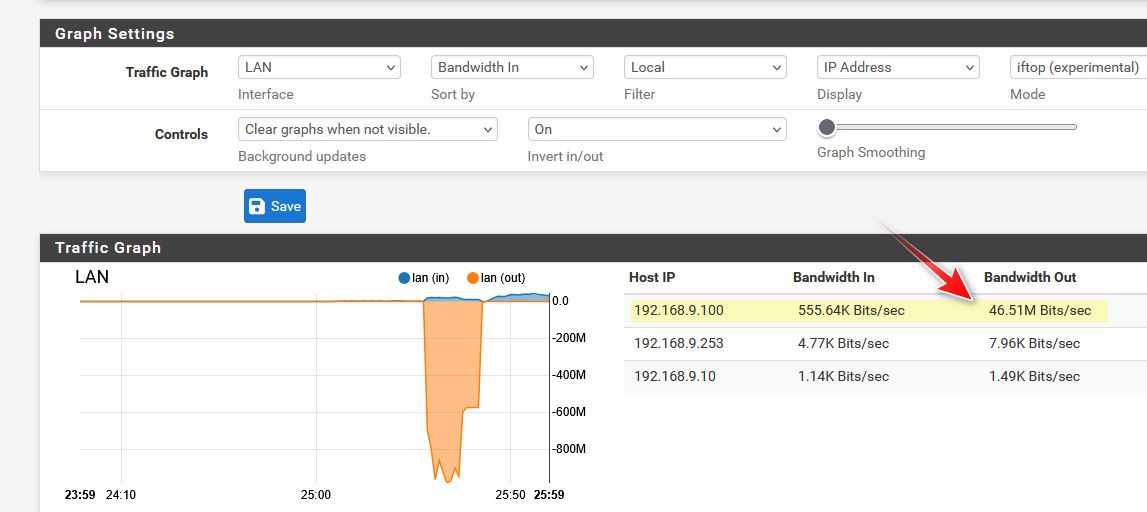
The large orange portion was the download part of the speedtest.
The windows thing I mentioned
To it being your isp with issues with upload - I see it now and then.. Where not seeing my full 50mbps up.. Could be just in prime time and lots of people on same connection in your neighborhood.. A reboot shouldn't really fix that - but maybe if your ip changes and you use a different gateway in your isp maybe?
But yeah its a good idea to rule out just something of yours using up a chunk of the pipe.
-
@johnpoz Unfortunately I am not running any p2p software. I also have that Windows network sharing feature disabled. Often no device is even running but one computer or laptop when I am doing the speedtests. Only thing that is always connected is a FireTV stick, my smart TV and my phone. It also doesn't happen during prime time. Very often just after I get up in the morning I notice it around 6-7am on my work computer. I work from home and sometimes use a remote desktop connection to my workplace and it is very laggy. This is why I even noticed it in the first place. Since then I am doing multiple speedtests every day. But there is no real pattern. Sometimes it can happen around 12am. Then 7pm. My traffic stats in the fritzbox shows around 1/10th upload traffic compared to my download traffic. So nothing out of the ordinary. A restart fixes it for at least a day and sometimes longer. Since the ISP can't find any issues with the connection and I have replaced the cables and router it is very strange. I also have no unknown devices in my wifi and don't allow connections between my wifi devices that could share data between them. I'm in the dark and looking for any clues. When it happend this morning I checked the logs and just saw that Akami stuff but nothing else. But pfsense should block any malicious traffic shouldn't it? Maybe it has to do with me having a static public ipv4 that is getting attacked?
-
@rasputinthegreatest you would have to be seeing a large amount of inbound traffic to your wan to have effect on your upload to be honest.. I mean a large amount! That is hogging your pipe..
Typical noise on the internet would not come even close to a fraction of the traffic you would need to be seeing to cause you a problem.
you rdping to something at work - I would hope that is via a vpn.. Are you routing all your traffic through this vpn when you do a speed test? I would disconnect the vpn and test your speedtest.
-
@johnpoz Yes my company has their own VPN servers. But I think my upload issues are unrelated to that since it also happens when I am not using my work computer during weekends. It is actually very strange to pin it down on anything but it has to happen at the router or after it since my ISP is certain it is not their infrastructure. I will watch out what is hogging the pipe next time the issue comes up. I restarted the router in the morning and so far the upload seems fine. Could it be someone hijacking my router? But I had reset the router already. Before I reset my router I did a Wireshark capture directly on the Fritzbox WAN interface with its integrated tools and there was weird read request from a malicious IP. Since then I got a little worried about my security. But maybe it's just noise as well?
There were also a lot of ICMPv6 Neighbor Soliciation entries with my public ipv6 under "source" row but there was also a second ipv6 that was not from my ISP but a different ISP. In Wireshark when capturing WAN the "source" row is what is what is going out of my network or what is coming in? Could that be a sign of my traffic being rerouted somewhere else and that's why my upload is bad?132533 60.378434 146.88.241.144 MY PUBLIC IP TFTP 68 Read Request, File: ay9mfwq7xxmd4w6cz, Transfer type: octet -
@rasputinthegreatest its called NOISE!! a stray packet here is not going to cause your internet to slow down.. Quit looking at random noise on the internet and think its causing you a problem..
Your work computer - DO YOU DISCONNECT the vpn on the weekends.. If you do not disconnect the vpn - then if like every other work vpn on the planet, all traffic is routed through that - you want to go to the internet you go to through the vpn..
My work laptop is pretty much always connected to my companies vpn.. Guess what my internet access is slower than my normal 500/50 internet -- because its routing through the company network, etc. etc.. Its got added overhead of the vpn tunnel itself, etc.
If you want to know if pfsense or your isp is having issues with your upload speed your going to have to take the vpn out of the equation - if not then get with your work IT why their vpn is slow ;)
-
@johnpoz Sorry I might have been unclear. I have my personal computer and a work computer. After work hours the work computer is powered down. The VPN client is also only installed on this particular computer and not on a network level. So it is impossible for it to interfer with the rest of my network. And I do my speedtests on other devices unrelated to my work computer as well.
-
@johnpoz So right now my internet is very slow again. I can't find anything in my traffic graph that uses up any speed. Since I am double natting I also disabled the WLAN of my fritzbox so no devices can use up bandwidth there. Still my speeds vary between 14 to 33mbit/s. After disabling my AP the speed went back to normal. But in the past when it happend and I turned off the AP it didn't do anything. There was also no bandwidth usage by the AP router.
Can the ISP be responsible for that issue?Also do you know what this means? At that time I was only in this forum and on Instagram and that IP leads to facebook
2 UDP Potentially Bad Traffic 157.240.253.63 443 192.168.178.42 5600 140:3 (spp_sip) URI is too longEDIT: I noticed when the graphs spike it doesn't show any IP uploading but the graph spikes. Or it says 2.0M up but on the left I see like 25kbit/s upload. Can there be a device hiding itself?
Or maybe I am reading it wrong. Does bandwith in = LAN (out)?
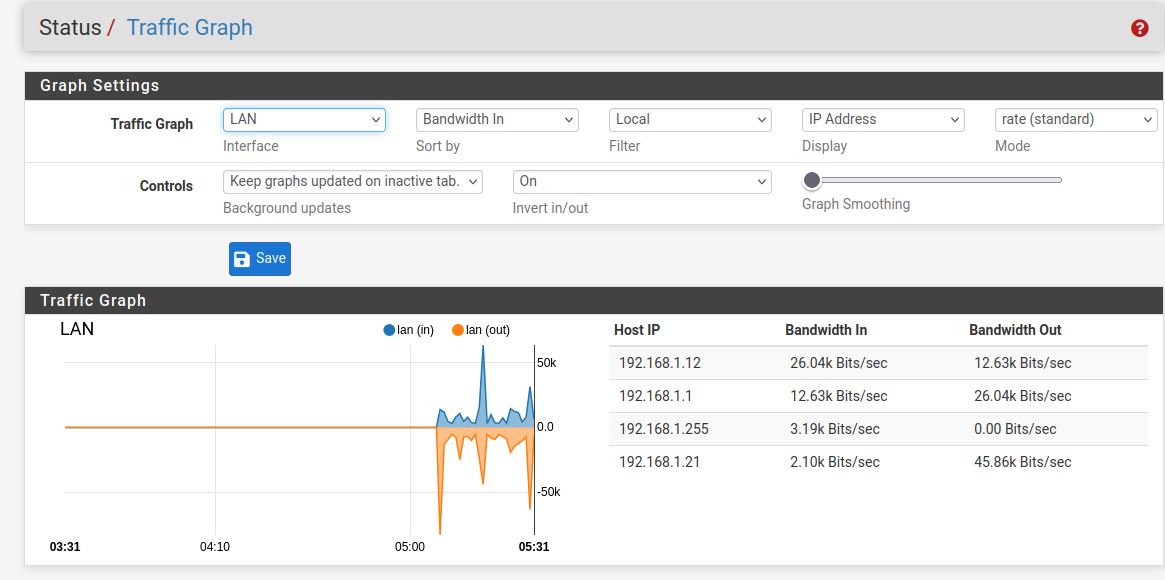
Also why is 192.168.1.255 showing up when it is not assigned?
In general I see a lot of spikes on the orange line which I feel like should be less than the blue one.
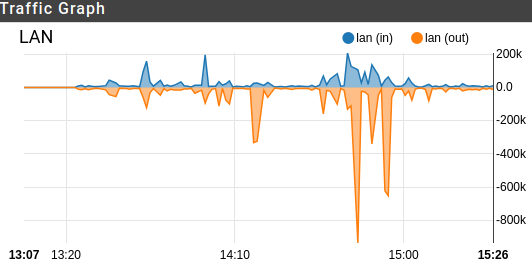
-
I saw a lot of strange IPs. A lot of Amazon servers.
Also 10.0.170.10 is an internal IP but that isn't assigned in my network was showing up for a second
Also this IP showed up and it leads to the Department of Defense in America??? Why in the hell would there be any upload in that direction?
https://www.abuseipdb.com/check/55.222.236.99
Am I going crazy or is this actually worrying?
Also noticed in the firewall log that there was a Destination shown to be a different ISP being blocked.Default deny rule IPv6 (1000000105) [fe80::563a:d6ff:feb9:4ab9]:43546 [2003:xxxxxxxxxx]:443 TCP:S -
@rasputinthegreatest said in Incoming connections to pfsense box from Facebook?:
Also 10.0.170.10 is an internal IP but that isn't assigned in my network was showing up for a second
On WAN ?
@rasputinthegreatest said in Incoming connections to pfsense box from Facebook?:
Also this IP showed up and it leads to the Department of Defense in America???
So, from you, your place ... to them ?
Defense uses IPv6 as it is more 'obscure'.@rasputinthegreatest said in Incoming connections to pfsense box from Facebook?:
Default deny rule IPv6 (1000000105) [fe80::563a:d6ff:feb9:4ab9]:43546 [2003:xxxxxxxxxx]:443 TCP:S
AnIPv6 packet coming into the pfSense WAN and as it is using 'local' IPv6 addresses (they start with fe80) it originates from your upstream router, the fritz.
Frittz - or so other device connected to the LAN of Fritz, and it wants to connect to a https server, present on it's LAN, behind pfSense. The default WAN (IPv6) behavior is : block.
Yeah, that's awkward. -
@Gertjan said in Incoming connections to pfsense box from Facebook?:
So, from you, your place ... to them ?
Defense uses IPv6 as it is more 'obscure'.@Gertjan said in Incoming connections to pfsense box from Facebook?:
Yeah, that's awkward.
Yes it was mostly outgoing traffic
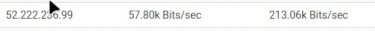
I was looking at my LAN under graphs showing local traffic and remote traffic aka "All"
But the IP shows here as DoD https://www.abuseipdb.com/check/55.222.236.99
What do you mean by awkward? I was looking at LAN traffic. But my ipv6 fe address was going to this public ipv6 that is not my ISP but a different one -
@rasputinthegreatest said in Incoming connections to pfsense box from Facebook?:
52.222.236.99
That's Amazon in Germany.
Look around you, your LAN, someone is doing some shopping with your connection.@rasputinthegreatest said in Incoming connections to pfsense box from Facebook?:
I was looking at LAN traffic
Ah, didn't know what you were looking at, I was presuming WAN.
LAN isn't interesting as that concerns your own devices.
( you know what your own device do, right ?! )@rasputinthegreatest said in Incoming connections to pfsense box from Facebook?:
But what about those ipv6 awkward connections?
The fe80 was also seen on LAN ?
-
@Gertjan said in Incoming connections to pfsense box from Facebook?:
@rasputinthegreatest said in Incoming connections to pfsense box from Facebook?:
52.222.236.99
That's Amazon in Germany.
Look around you, your LAN, someone is doing some shopping with your connection.Oh my god what simple typo can do. lmao Thank you
But what about those ipv6 awkward connections? -
@Gertjan said in Incoming connections to pfsense box from Facebook?:
@rasputinthegreatest said in Incoming connections to pfsense box from Facebook?:
52.222.236.99
That's Amazon in Germany.
Look around you, your LAN, someone is doing some shopping with your connection.@rasputinthegreatest said in Incoming connections to pfsense box from Facebook?:
I was looking at LAN traffic
Ah, didn't know what you were looking at, I was presuming WAN.
LAN isn't interesting as that concerns your own devices.
( you know what your own device do, right ?! )@rasputinthegreatest said in Incoming connections to pfsense box from Facebook?:
But what about those ipv6 awkward connections?
The fe80 was also seen on LAN ?
yes that fe80 was seen on LAN traffic graph. Same for that 10.0 IP which is not assigned in my internal network though. I know all my devices but that IP makes no sense. Only thing I could imagine it could be is my work VPN network. But that one is 10.232.x.x
-
@rasputinthegreatest said in Incoming connections to pfsense box from Facebook?:
Same for that 10.0 IP which is not assigned in my internal network though
Normally ( disregard the first rule ) :
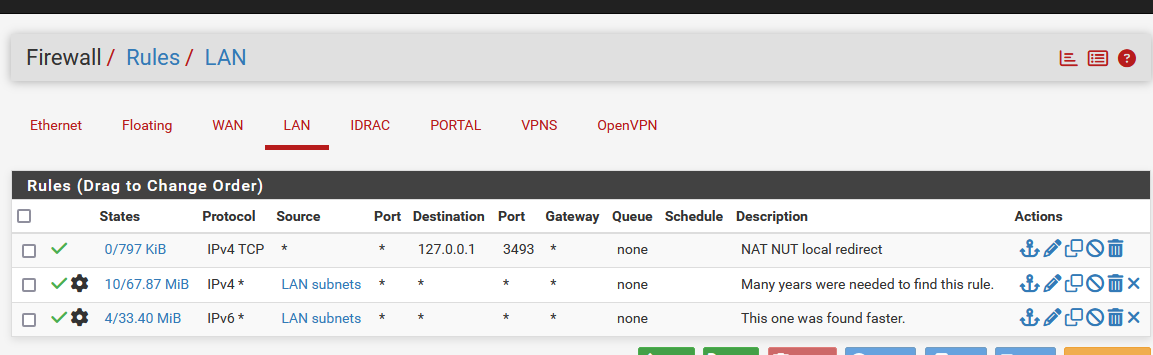
which means that my LAN interface will accept only traffic 192.168.1.0/24 sourced (originates) traffic, as 192.168.1.0/24 is my pfSense LAN.
All other traffic will hit the hidden last rule(s) which look like this :#--------------------------------------------------------------------------- # default deny rules #--------------------------------------------------------------------------- block in log inet all ridentifier 1000000103 label "Default deny rule IPv4" block out log inet all ridentifier 1000000104 label "Default deny rule IPv4" block in log inet6 all ridentifier 1000000105 label "Default deny rule IPv6" block out log inet6 all ridentifier 1000000106 label "Default deny rule IPv6 ```" These are block all rules, present on all pfSense interfaces. This means that if you have a device that want's to use 10.1.2.3 on your LAN, it will go 'nowhere'. Even if it reaches some how your pfSense LAN interface, it will get dropped. You can see the "1000000105" rule which you already found as you've shown it in your post above. -
@Gertjan I also saw this IP right now with in-and outbound traffic and it seems very sus https://www.abuseipdb.com/check/34.107.243.93
Also this IP shows up in my LAN traffic graph https://www.abuseipdb.com/check/40.113.103.199
Why is this not being blocked?Regarding the rules. I have these preconfigured rules. Do I need to add anything to them?
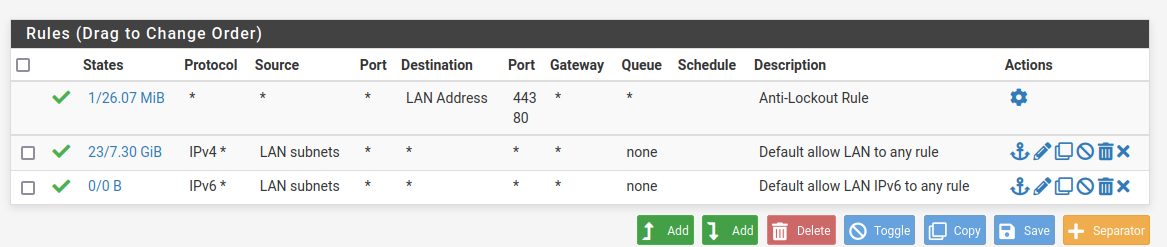
What can I do to block these malicious IPs from making connections to my network?
Also here you can see a bandwidth spike but it doesn't show any IP
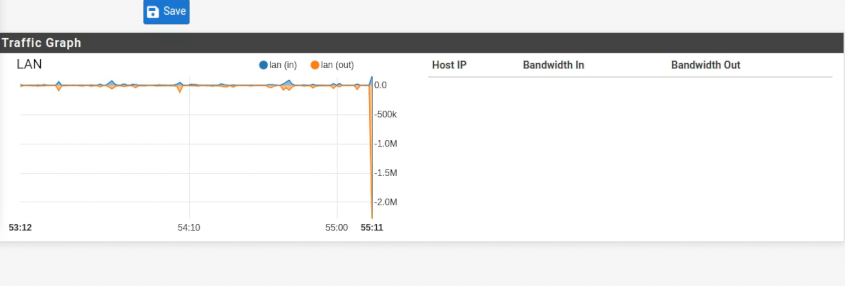
-
Potentially Bad Traffic
If you have the Info rules enabled understand those are not intended for blocking.
If you have Snort running on WAN move it to LAN. On WAN it operates outside the firewall so anything hitting your WAN IP is scanned even if it will be dropped.
-
@SteveITS I am using pfsense out of the box except for snort. I have snort setup on WAN and LAN.
Where do I find the info rules? Snort wasn't even picking up those IPs. I just saw them pop up on the traffic graph for a second.
https://www.abuseipdb.com/check/34.107.243.93
https://www.abuseipdb.com/check/40.113.103.199How can I make sure this stuff gets picked up and blocked? And where can it come from if it is showing in the LAN traffic graph.
-
@rasputinthegreatest said in Incoming connections to pfsense box from Facebook?:
I have snort setup on WAN
You're lucky, you have a router front of your pfSense that is protecting it, so no illicit traffic can reach your pfSense. That is, I hope you've set it up like that.
If your pfSense's WAN interface did have your 'real' WAN IP, and you get yourself 'dossed', then every incoming packet 'not requested for' (wasn't a reply from what was requested from your LAN(s), then it gets dropped very (extremely) qyicky by the firewall.
With snort an WAN you said : I want every valid reply packet and also every illicit packet being scanned by snort. So, now every packet will cost you thousands of CPU cycles more.
In case of an incoming dos your CPU will go in overdrive, and this can even take down the system.
Exactly what the dosser wanted, and hew as counting on a bit of your help.Never ever scan (snort, suricata, etc) the WAN port, except if you have 'huge' resources.
Its a wast of time, power, comfort etc etc.
It's like installing that tictoc app so you can see if you can find pure BS .... -
@rasputinthegreatest there is no way some 34.x address is inbound into LAN interface as source.. Unless you were using that internally - of your have something forwarding traffic to your lan interface from some other connection..
To your upload being jammed - I would for starters disable snort.. That can have performance impact.. Does your issue go away?
internet -- wan pfsense lan -- your stuff
How would some internet IP 34.x ever be source of traffic inbound into your lan? Or even outbound for that matter.
How about you draw up how you have your stuff connected.. Because you must have your lan exposed to the public internet or connected is some odd way if you could ever see internet IPs inbound as source into your lan interface.. In a normal setup that would just be impossible.. Unless you were using 34.x something internally on your own networks.
-
@johnpoz The whole reason I got the pfsense box was because of my upload issues. At the moment my setup looks like this
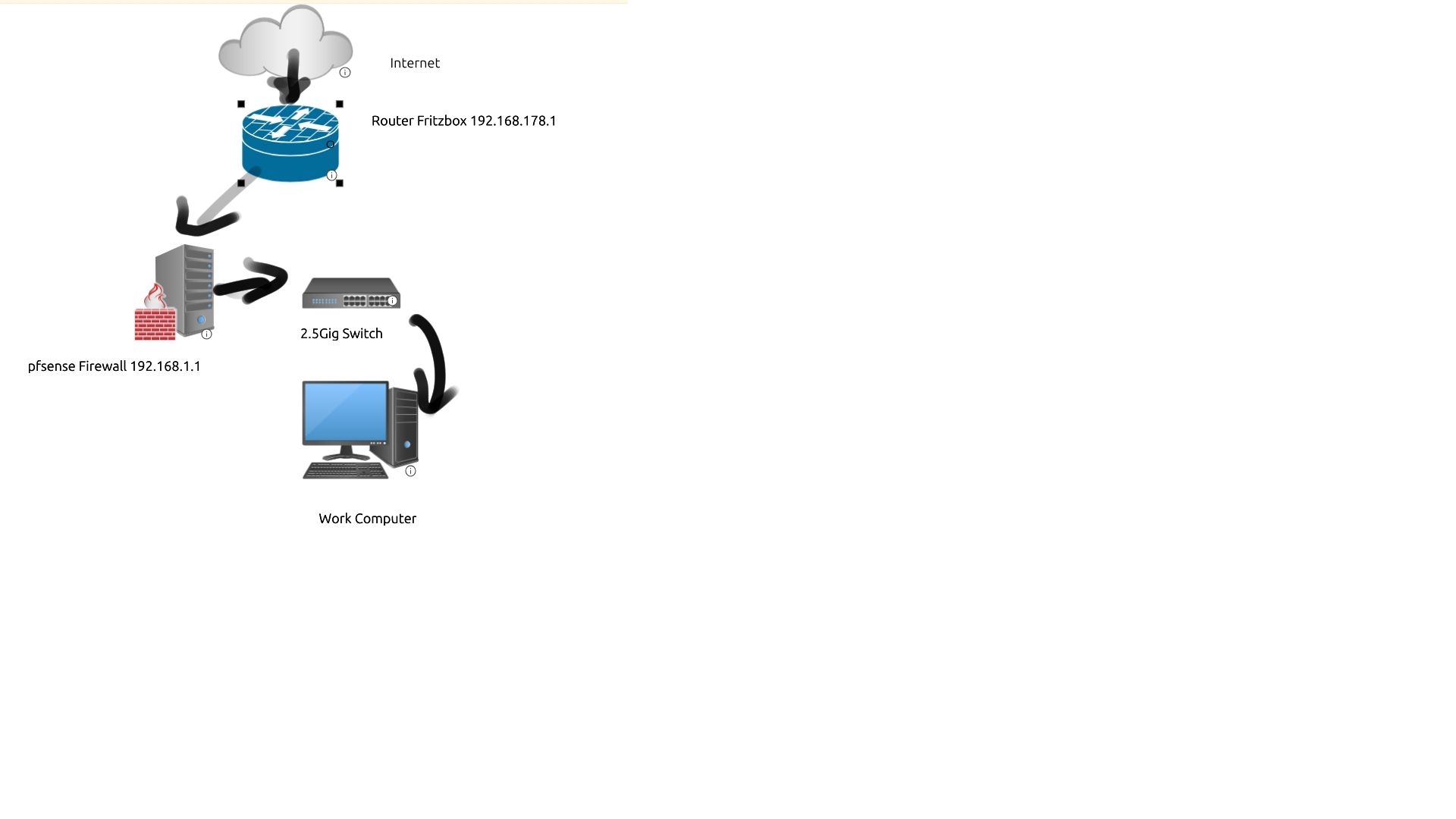
my pfsense box is plugged into the 2.5gig port of my fritzbox
fritzbox goes into WAN port on pfsense box and Lan port from pfsense box goes to a switch where my devices are connected behind.
Where is the error in this setup? I followed Jim's garage setup.
Here are the WAN settings
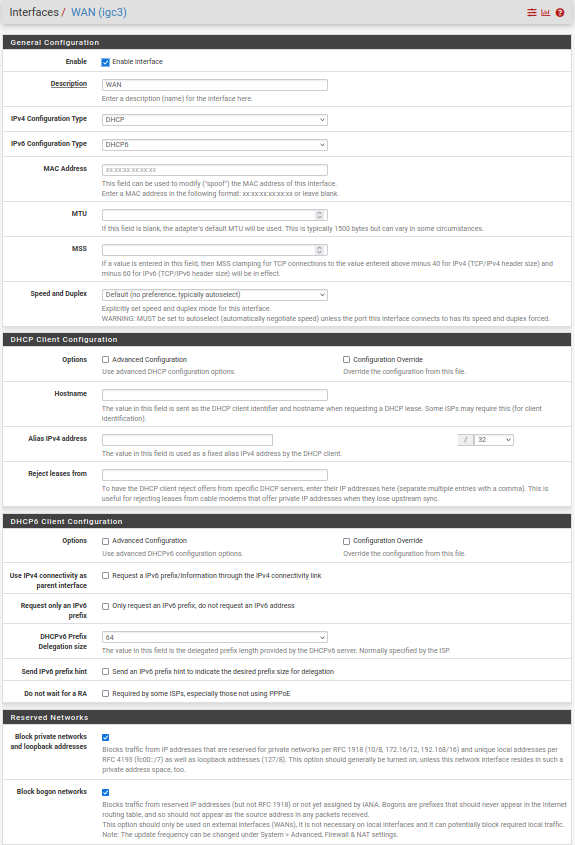
And here LAN settings
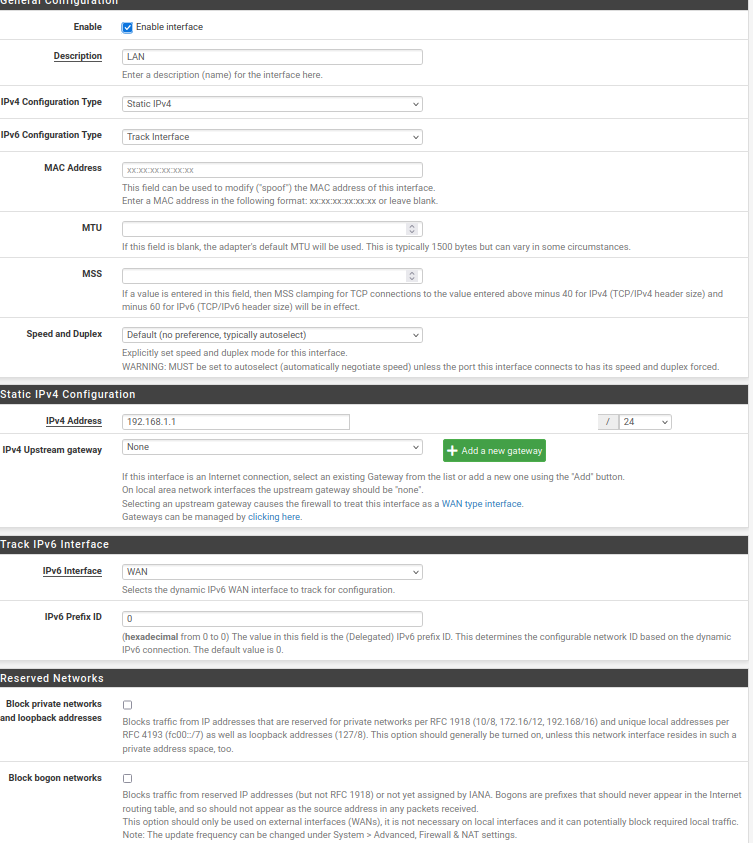
Anything I am missing? Regarding the IP 34.x.x.x I was showing "Remote" in the traffic graph. Should I not be able to see any public IPs in the traffic?