Firewall Rule Numbers
-
Ok thanks I've toggled column view a few times and it all seems to work but they root of my problem seems to be just one rule that will not show a description. All the rules on the OPT1 interface have a description but i think i will just have to work it out manually which was what i was hoping to avoid.
Also at the command line running pfctl -vvsr give mess this relating to that number
@40(1000000114) block drop log quick inet proto tcp from any to any port = 0
[ Evaluations: 5321224 Packets: 4737 Bytes: 284220 States: 0 ]
[ Inserted: pid 73290 State Creations: 18446735277732176120]
@41(1000000114) block drop log quick inet proto udp from any to any port = 0
[ Evaluations: 5316129 Packets: 4737 Bytes: 284220 States: 0 ]
[ Inserted: pid 73290 State Creations: 18446735277732176096]Although I'm no clearer where this rule has come from.
Thanks for replies.

 -
Ok thanks I've toggled column view a few times and it all seems to work but they root of my problem seems to be just one rule that will not show a description. All the rules on the OPT1 interface have a description but i think i will just have to work it out manually which was what i was hoping to avoid.
Also at the command line running pfctl -vvsr give mess this relating to that number
@40(1000000114) block drop log quick inet proto tcp from any to any port = 0
Well that does not have any label, it's this stuff in https://github.com/pfsense/pfsense/blob/master/etc/inc/filter.inc#L3157
Try this with System Patches package:
--- a/etc/inc/filter.inc +++ b/etc/inc/filter.inc @@ -2876,10 +2876,10 @@ pass in {$log['pass']} quick inet6 proto ipv6-icmp from ff02::/16 to fe80::/10 i pass in {$log['pass']} quick inet6 proto ipv6-icmp from fe80::/10 to ff02::/16 icmp6-type {128,133,134,135,136} tracker {$increment_tracker($tracker)} keep state # We use the mighty pf, we cannot be fooled. -block {$log['block']} quick inet proto { tcp, udp } from any port = 0 to any tracker {$increment_tracker($tracker)} -block {$log['block']} quick inet proto { tcp, udp } from any to any port = 0 tracker {$increment_tracker($tracker)} -block {$log['block']} quick inet6 proto { tcp, udp } from any port = 0 to any tracker {$increment_tracker($tracker)} -block {$log['block']} quick inet6 proto { tcp, udp } from any to any port = 0 tracker {$increment_tracker($tracker)} +block {$log['block']} quick inet proto { tcp, udp } from any port = 0 to any tracker {$increment_tracker($tracker)} label "Block traffic from port 0" +block {$log['block']} quick inet proto { tcp, udp } from any to any port = 0 tracker {$increment_tracker($tracker)} label "Block traffic to port 0" +block {$log['block']} quick inet6 proto { tcp, udp } from any port = 0 to any tracker {$increment_tracker($tracker)} label "Block traffic from port 0" +block {$log['block']} quick inet6 proto { tcp, udp } from any to any port = 0 tracker {$increment_tracker($tracker)} label "Block traffic to port 0" # Snort package block {$log['block']} quick from <snort2c>to any tracker {$increment_tracker($tracker)} label "Block snort2c hosts"</snort2c> -
Not quite sure i want to do that yet but will just know that this particular rule number relates to the default rules and not worry about it anymore.
Thanks for all your help.
Regards
Rob
-
It's been merged to 2.2.4.
-
Question slightly OT: Is it good practice NOT to log packages blocked by the default deny rule (Settings, first option under "Log Firewall Default Blocks"?
-
Hmmm… depends on how much noise you like, or what you policies are, or whatever. Wouldn't say there's any "best practice" here.
-
Im still trying to work out the best settings since I've only been using pfsense a few months so I've left logging on most things so i can see whats going on unless i really really don't want to know about something.
-
I dont suppose you could do the same for UPnP rules as well?
Thanks
Rob
-
(This is an attempt by me to not clutter up this forum by repeating the same question, but instead information to an already existing thread if that is similar. If I did wrong by doing that I apologize).
I have the same problem as the OT. I suddenly have blocks in my FW log without descriptions. Clicking on the red cross doesn't show any other information.
(I do know this happens when you disable logging for a FW rule which was previously enabled, but I did not do such a thing at all).
Is there a place where I can find all the rule numbers together?
Log:
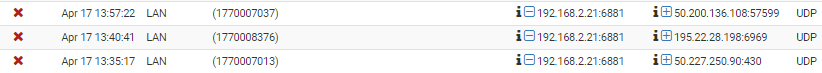
Click red cross:
Bonus: this description isn't right. MULLVAD is a separate interface, it is not the interface VLAN40:
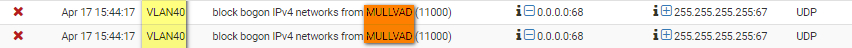
Thank you for help

-
cat /tmp/rules.debugLook at the tracker. -
Thank you. I also discovered
https://pfsense/status.php -
rules.debug is the best place to get the configured rule set all in one place. It is usually one of the first places I go when evaluating a status output, depending on what the trouble is.
I never look at the rules in the config.xml. rules.debug lays them all out for you in a readable format.