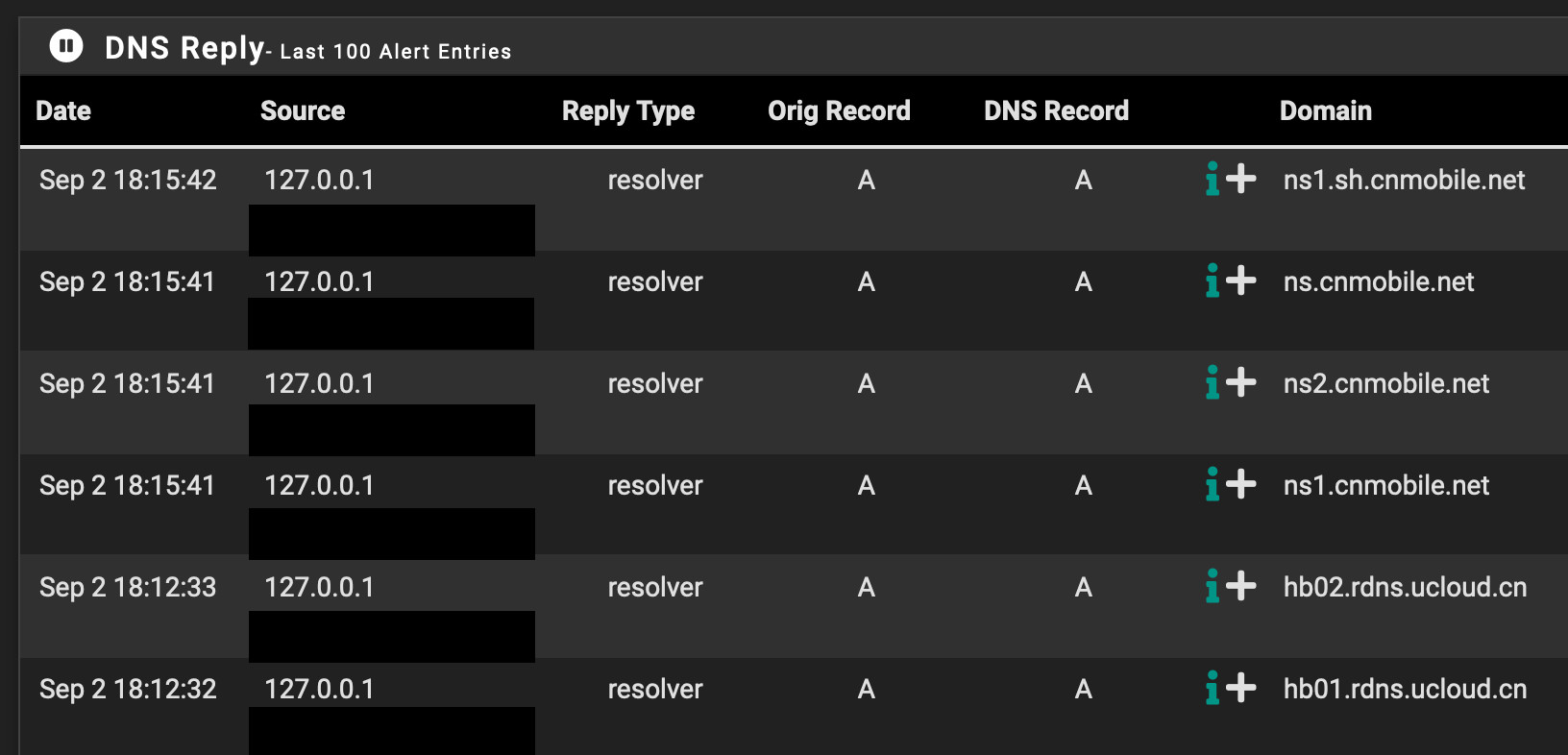
Can someone help me understand why is unbound resolving foreign domains (e.g. China)? Is this normal?
-
@johnpoz said in Can someone help me understand why is unbound resolving foreign domains (e.g. China)? Is this normal?:
@gertjan said : unbound will not prune the cache any more after TTL : it will refresh the content
I'll (should have) add two words :
unbound will not prune the cache any more after TTL reaches zero : it will refresh the content
.@johnpoz said in Can someone help me understand why is unbound resolving foreign domains (e.g. China)? Is this normal?:
and then never ask for it again - it will expire.
Then that was me misunderstanding.
unbound maintains a "popular" indicator ?! (I just earned a visit to the source code repository to find out ;))
I understood that, for any TTL reaching zero, and prefetch is active, it will refresh.
This implies an that cache will steadily grow over time. Humm, that's good and very bad.
Thanks for the info.edit : for @code4food23 : What I meant to say was : ones you connected your device with "'foreign origins" to your network, you will introduce traffic related these origins in your network. even if you remove them, some related traffic still persists.
@johnpoz makes it clear that this traffic will fade out over time. -
@mer said in Can someone help me understand why is unbound resolving foreign domains (e.g. China)? Is this normal?:
Basically clients get configured to talk to Unbound on the firewall as the DNS resolver, unbound goes out to the "internet" to satsify the request.
Would unbound also try to satisfy requests made by services like pfblocker and suricata? Idk about those scanner-* domains but i saw i have a dnsbl for abuse ch and oisd nl.
@mer said in Can someone help me understand why is unbound resolving foreign domains (e.g. China)? Is this normal?:
Do you have iOT things on your network, like Ring doorbells, Nest thermostats, etc? It is possible something like that is making the request.
I do have two ring cameras. I think i ruled the rasberry pi and tv because I disconnected those and still kept seeing unbound resolve these odd domains.
Could this be a sign that they are compromised?
-
@gertjan said in Can someone help me understand why is unbound resolving foreign domains (e.g. China)? Is this normal?:
you will introduce traffic related these origins in your network
Exactly -- if you ask for www.domain.tld, when you resolve there is going to be stuff that will trigger of that isn't exactly what you asked for. It will have to query roots for tld, it will have to query the gtld servers for ns of domain.tld, it will have to query the ns for domain.tld, it will query the ns of domain.tld for www.domain.tld
It will also have to look up any cnames that stuff might point to, etc.
unbound isn't going to just willy nilly resolve stuff - something had to ask it to resolve X.. once it is asked to resolve something - it will look up other stuff related to looking up X..
That something could be a client, it could be a package running on pfsense, it could be pfsense itself - if you click the little resolve button in your firewall log it will look for the PTR of that IP, it will resolve stuff to look for its update and packages, etc.
But if unbound looked up something - it was asked to do so by something.
edit: nameservers - man you have no idea how many domains it might be the ns for.. could be 10s of thousands of domains.. With millions of total records. The name of some nameserver doesn't have to be ns.domain.tld either.. I could have my ns be called yourfdnow.spyware.net hehe - prob cause some issues we lots of people asking questions and blocking it - but as long as have the ability to put records in spyware.net I could have my ns name be a record in that domain..
When looking up ptr - where those resolve is up to the actual owner of the ip space, unless they have delegated it to someone using their IP space.. You could have some IP used in DE be resolved by NS in china for example - if company in de is using IP owned or use to be owned by china company. Could be business in the US, using IPs from their parent company routed to US with PTR still pointing back to china to resolve..
Quite often when IP space is sold, they forget to update some of these records, etc. Or doesn't get updated until long after when they finally figure out something is not working correctly.
I get abuse letters from IPs I manage with arin - because the guys in the datacenter would assign some ip space to customer, and not let me know - so never delegated that space to them, or work with their IT to get the space being delegated to resolve via their NS for ptrs, etc.
-
@gertjan @johnpoz thanks alot you’ll for the informative discussion. Definitely learned this morning.
@gertjan said in Can someone help me understand why is unbound resolving foreign domains (e.g. China)? Is this normal?:
even if you remove them, some related traffic still persists.
So is there not a way to remove this type of traffic? Or by “them” did you mean if i were to remove the clients?
@johnpoz said in Can someone help me understand why is unbound resolving foreign domains (e.g. China)? Is this normal?:
That something could be a client, it could be a package running on pfsense, it could be pfsense itself - if you click the little resolve button in your firewall log it will look for the PTR of that IP, it will resolve stuff to look for its update and packages, etc.
So for example i have dns block lists with tld of .ch and .nl (abuse.ch and oisd.nl). So pfblocker or suricata could also be generating this traffic?
But actually i never though of that which you mentioned about it being pfsense. I actually have clicked on the resolve ip before on the firewall logs. So am I correct in saying that this is what most likely the cause for unbound resolving those ptr records to those scanner-* domains? This is what got me really worried in the first since i had seen blocks to those domain in my firewall logs.
Also to make sure I understand the discussion above. Essentially, unbound will keep refreshing these even if i didnt specifically told to resolve those at the instant i saw those in my logs. Which is why i see them being requested, right?
Furthermore, this wouldn’t be a sign of compromise then, would it?
-
@gertjan said in Can someone help me understand why is unbound resolving foreign domains (e.g. China)? Is this normal?:
You have a console port on your pfSense, use it.
If not, you have to use the SSH access - and keep the PC on which the SSH cients runs, connected to your LAN.
Now it comes : remove ALL other devices. No exception.Thanks for this suggestion, will definitely try. The intention was originally this when I disconnected my tv and Pi and only clients i had aside from AP, were one ringdoorbell and Mac connected to LAN on the unifi switch.
-
@code4food23 said in Can someone help me understand why is unbound resolving foreign domains (e.g. China)? Is this normal?:
This is what got me really worried in the first since i had seen blocks to those domain in my firewall logs.
Not blocks too. If you click resolve in IP in your firewall logs - that is the PTR of that IP - they scanned you, and it was blocked. Doesn't mean anything on your network tried to go there..
China does a lot of scanning - so yeah your going to see all kinds of IPs from china in your firewall log. If you try resolve those IPs - then most likely NS in china that resolves that space.. Doesn't mean anything on your network tried to go to some domain/ip in china..
edit: example
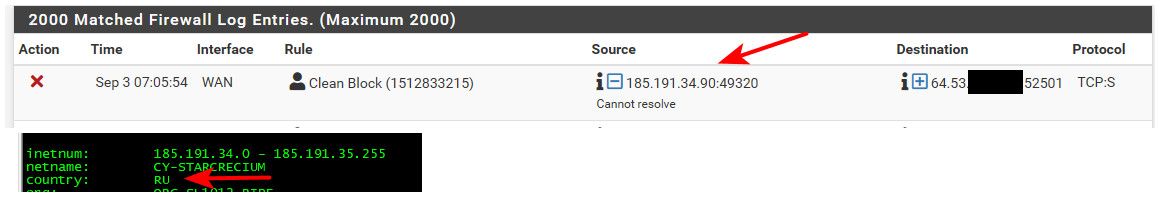
This IP which is RU ip - tried to scan me, now it doesn't resolve - but prob points to some NS in Russia, etc. So very well if looked in my query log even if doesn't resolve prob did some lookup for Russian name server when I clicked the little resolve button on the firewall log.
-
@johnpoz said in Can someone help me understand why is unbound resolving foreign domains (e.g. China)? Is this normal?:
Not blocks too. If you click resolve in IP in your firewall logs - that is the PTR of that IP - they scanned you, and it was blocked.
Thank you for the clear example. And Yes, sorry I meant to say I have indeed clicked on the resolve IP and just as shown in your image ive seen scanner domains and “cannot resolve”.
Would unbound continually resolve those later on? For example, the domains in the first image occurred throughout the day yesterday when i looked at the log.
Also, is there a button to manually prune the cache like in pihole? I didn’t find the option looking yesterday.
-
For example, upon checking my logs again, I am seeing the same activity, I have disconnected my AP where my ring device is connected to and and now the only client connected is my computer aside from the unifi switch which is where I have my latop connected to.
Also thing to note is that this activity was happening overnight as well, when the only thing connected was my Ring device.
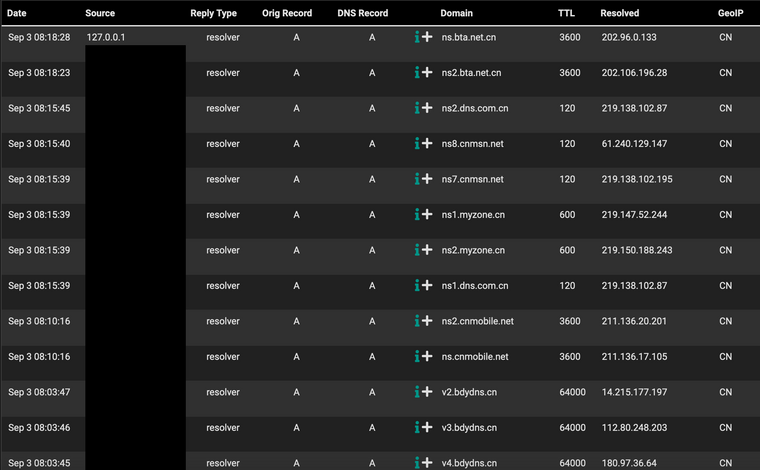
So is this the case of unbound having cached these?
-
@code4food23 why are you blocking out the source of the query? If that was some local IP of yours - then you know what is triggering them. There is little reason to hide rfc1918 space.
Another example as already mentioned lists being pulled by a package. keep in mind that say I download a list from special.listdomain.com - as went over already looking up that record could trigger lots of other queries. For example what is the NS of listdomain.com? For all we know you have something updating that domain of what that is NS is bta.net.cn?
What packages do you have installed, what are they pulling data from.. Do you have anything set to do lookups. ntop can for example be set to query for IPs it sees.. pfblocker using lists from all over or pfblocker depending on how you have it setup could be resolving domains.. A list using whois regex could resolve domains to IPs, etc.
is there a button to manually prune the cache like in pihole
You can purge specific entries/domains using
unbound-control -c /var/unbound/unbound.conf
and the appropriate command
flush_type <name> <type> flush name, type from cache flush_zone <name> flush everything at or under name from rr and dnssec caches flush_bogus flush all bogus data flush_negative flush all negative data flush_stats flush statistics, make zero flush_requestlist drop queries that are worked on flush_infra [all | ip] remove ping, edns for one IP or allI only use pfblocker to pull geoip and a few other IP based lists.. So I am not really up to speed on all the ins and outs of when, how - why and what it mightr do related to dns queries.. We prob need @BBcan177 to chime in here on what specifically could be causing those queries to happen..
BTW - where exactly are you pulling that info from.. where is shows your geoip there as CN.. I don't recall seeing such a screen/log in pfblocker?
ah -- I found this for example... So clearly pfblocker is kicking of resolving of stuff.. My lists are only IP based.. But when it allowed something it resolved it.. or tried. So your deny list if your blocking CN could be doing the same thing, etc..
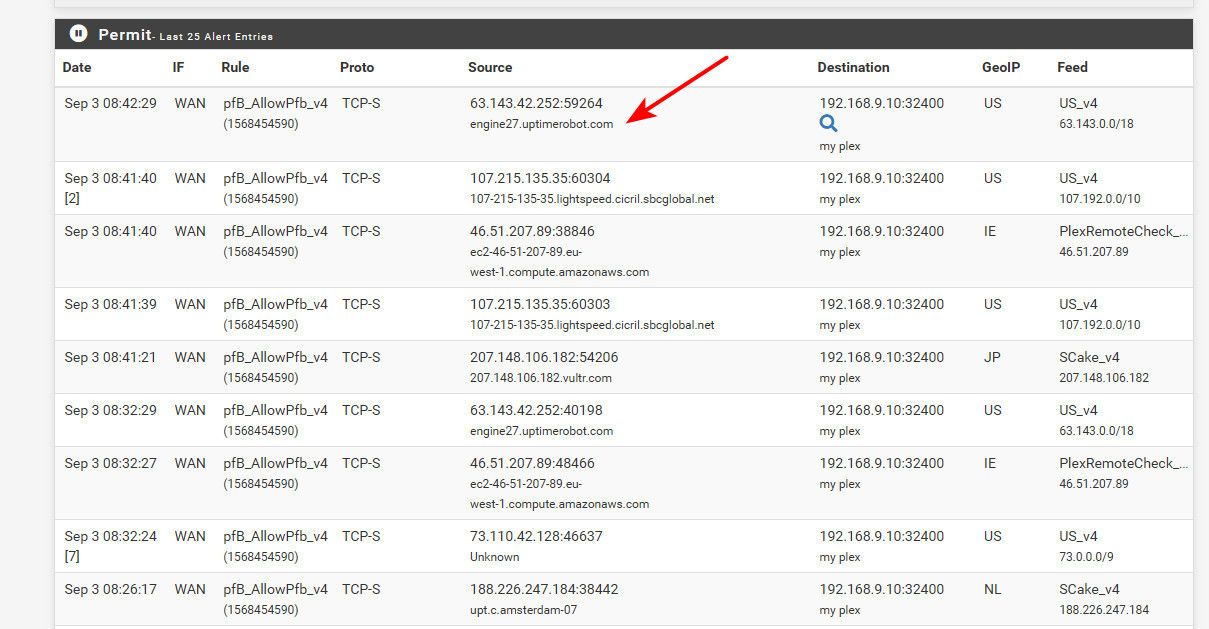
-
@johnpoz said in Can someone help me understand why is unbound resolving foreign domains (e.g. China)? Is this normal?:
why are you blocking out the source of the query? If that was some local IP of yours - then you know what is triggering them. There is little reason to hide rfc1918 space.
The Ips were all 127.0.0.1, I just wasn't sure whether the okay show the hostname that appears below that which to my understanding is that of the pfsense (something like: my_name_domain.home.arpa)
@johnpoz said in Can someone help me understand why is unbound resolving foreign domains (e.g. China)? Is this normal?:
For all we know you have something updating that domain of what that is NS is bta.net.cn?
What could be the reason for this if this is the case? I have the below packages installed:
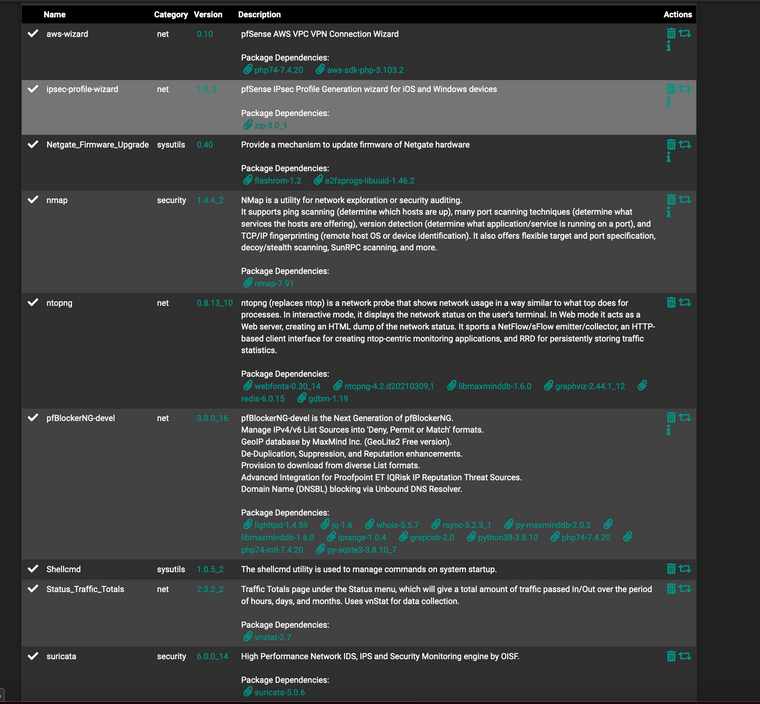
Note i have unchecked the setting in ntpong to enable it. Should probably remove it anyway.
-
@johnpoz said in Can someone help me understand why is unbound resolving foreign domains (e.g. China)? Is this normal?:
BTW - where exactly are you pulling that info from.. where is shows your geoip there as CN.. I don't recall seeing such a screen/log in pfblocker?
ah -- I found this for example... So clearly pfblocker is kicking of resolving of stuff.. My lists are only IP based.. But when it allowed something it resolved it.. or tried. So your deny list if your blocking CN could be doing the same thing, etc..Oh so that is why i see those ips resolved in my pfblocker alerts. It has been done by pfblocker this whole time? And Turning this off, if possible, would stop this from showing up in my logs?
-
@johnpoz said in Can someone help me understand why is unbound resolving foreign domains (e.g. China)? Is this normal?:
But when it allowed something it resolved it.. or tried. So your deny list if your blocking CN could be doing the same thing, etc..
My Permit list is empty, but yes like you said, the deny list is doing the exact same thing. I can't find an option to stop it from resolving those IPs. Any ideas?
-
@code4food23 said in Can someone help me understand why is unbound resolving foreign domains (e.g. China)? Is this normal?:
I can't find an option to stop it from resolving those IPs. Any ideas?
Hmm? Not sure if you can.. @BBcan177 be the man to know for sure - and also have the ability to allow feature to turn off resolution in the logs?
I know there is global setting for logging. And there is logging you can turn on or off for specific lists you create, etc.
I use only a fraction of what pfblocker can really do myself. I use it to maintain some aliases, and then use those aliases in my own rules.
I do have mine set to logging - maybe you could turn logging off and see if your odd queries go away. Either globally or on your specific lists.
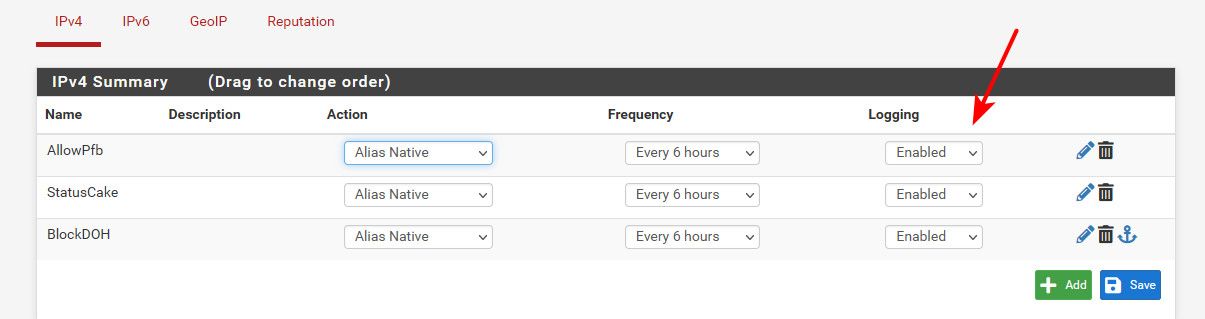
-
@johnpoz said in Can someone help me understand why is unbound resolving foreign domains (e.g. China)? Is this normal?:
Hmm? Not sure if you can.. @BBcan177 be the man to know for sure - and also have the ability to allow feature to turn off resolution in the logs?
Thanks for the suggestion! looks like turning off logging for the lists in IPv4, IPv6, and GeoIP has resolved this. Now I dont see those scanner domains I was seeing before.
These blocks would still show up in pfsense firewall logs right? Although not with the name of the list any more? I noticed now I see a rule number where I used to see the name of the list.
Also, is there a best practice for GeoIP filtering for a home user as myself? I previously had to deny inbound only from all countries then changed it to deny both for certain because of the dns queries made to china for example (although this didnt stop those).
-
@johnpoz said in Can someone help me understand why is unbound resolving foreign domains (e.g. China)? Is this normal?:
Hmm? Not sure if you can.. @BBcan177 be the man to know for sure - and also have the ability to allow feature to turn off resolution in the logs?
actually, after turning off the logging of the lists, my firewall logs are no longer being updated anymore :/
-
@code4food23 said in Can someone help me understand why is unbound resolving foreign domains (e.g. China)? Is this normal?:
after turning off the logging of the lists, my firewall logs are no longer being updated anymore :/
Which rules - pfblocker created rules? Then no they wouldn't because that rule was set to not log. I have rules that don't log as well.
But not logging something that resolves has nothing to do with what is in the alias.. They would still be blocked by the rule where that alias is used if that rule is set to log. But the normal firewall log does not resolve unless you click the little resolve button while viewing the log.. Those reports your showing in pfblocker for deny or permit are not really the firewall log..
is there a best practice for GeoIP filtering for a home user as myself?
What are you wanting to do.. Do you have port forwards? To be honest I wouldn't block based on geoip ever outbound. How do you know there is never going to be site in say china or ru that you want to visit? Do you know where your site you want to go to is hosted? Could be anywhere on the planet..
The only use I personally see for geoip in home - is what you allow to your port forwards. Out of the box everything is blocked anyway. If I allow something - if you don't want to allow the planet, then limit the list to what you want to allow, and not worry about deny.. If not allowed - then its denied by default anyway.
Example - I have zero users outside of US for my plex, so in my forward I only allow US - well not exactly true I do allow my monitor IPs, they could be global - never know so its best to get the IPs they are going to use and add them to your allow list. And I recently added Morocco to my allow - since one of my users is in Casablanca teaching for a couple of years.
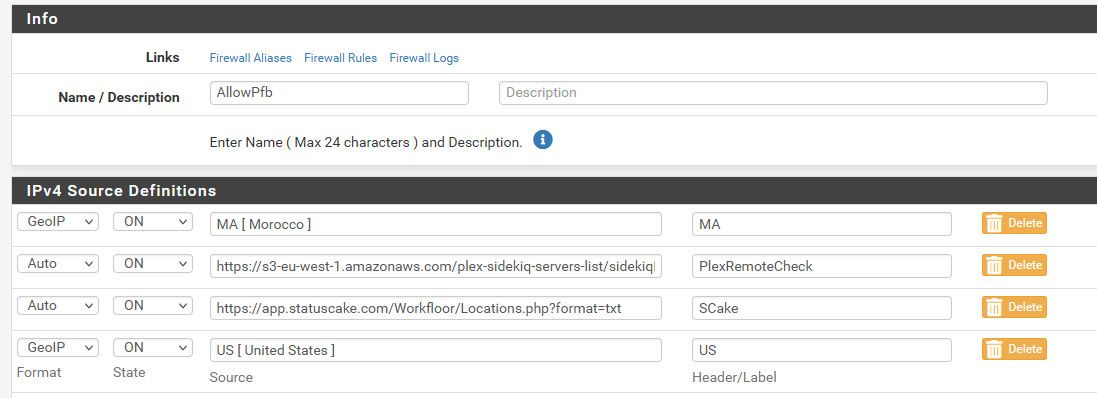
Allow what you want, vs trying to deny all the "possible" bad is normally better - unless you have a "known" list of bad.. Which is rarely going to be a whole geo based anything.. Can you say that RU is "all" bad - or china is "all" bad? I sure can't.. Maybe for what your doing it is? But your list is prob going to be smaller if you just "allow" what you want vs trying to block every country you think "could" be bad.
-
@johnpoz said in Can someone help me understand why is unbound resolving foreign domains (e.g. China)? Is this normal?:
They would still be blocked by the rule where that alias is used if that rule is set to log. But the normal firewall log does not resolve unless you click the little resolve button while viewing the log.. Those reports your showing in pfblocker for deny or permit are not really the firewall log..
Okay now I understand. I was used to seeing them also show up there as well. In this case is there a reason to have pfBlocker block inbound traffic, and let pfsense "Default deny rule" take care of it? Do the default deny rules take precendence over pfBlockers floating deny rules?
I had previously turned off logging of "default deny rules".
@johnpoz said in Can someone help me understand why is unbound resolving foreign domains (e.g. China)? Is this normal?:
@code4food23 said in Can someone help me understand why is unbound resolving foreign domains (e.g. China)? Is this normal?:
after turning off the logging of the lists, my firewall logs are no longer being updated anymore :/
Which rules - pfblocker created rules? Then no they wouldn't because that rule was set to not log. I have rules that don't log as well.
But not logging something that resolves has nothing to do with what is in the alias.. They would still be blocked by the rule where that alias is used if that rule is set to log. But the normal firewall log does not resolve unless you click the little resolve button while viewing the log.. Those reports your showing in pfblocker for deny or permit are not really the firewall log..
is there a best practice for GeoIP filtering for a home user as myself?
What are you wanting to do.. Do you have port forwards? To be honest I wouldn't block based on geoip ever outbound. How do you know there is never going to be site in say china or ru that you want to visit? Do you know where your site you want to go to is hosted? Could be anywhere on the planet..
The only use I personally see for geoip in home - is what you allow to your port forwards. Out of the box everything is blocked anyway. If I allow something - if you don't want to allow the planet, then limit the list to what you want to allow, and not worry about deny.. If not allowed - then its denied by default anyway.
Example - I have zero users outside of US for my plex, so in my forward I only allow US - well not exactly true I do allow my monitor IPs, they could be global - never know so its best to get the IPs they are going to use and add them to your allow list. And I recently added Morocco to my allow - since one of my users is in Casablanca teaching for a couple of years.

Allow what you want, vs trying to deny all the "possible" bad is normally better - unless you have a "known" list of bad.. Which is rarely going to be a whole geo based anything.. Can you say that RU is "all" bad - or china is "all" bad? I sure can't.. Maybe for what your doing it is? But your list is prob going to be smaller if you just "allow" what you want vs trying to block every country you think "could" be bad.
Makes complete sense. Honestly I have no port forwards set at all at the moment. I do plan on starting homelab to learn more like setting up kubernetes server on bare metal, learn more about networking, setup a plex server, etc, but even then I dont see my self exposing any public facing services.
-
@code4food23 said in Can someone help me understand why is unbound resolving foreign domains (e.g. China)? Is this normal?:
In this case is there a reason to have pfBlocker block inbound traffic
Not really - not if you don't have any port forwards. Out of the box all unsolicited inbound traffic is denied anyway..
Until such times you create a port forward, or allow something to hit your wan with a rule - like ssh or vpn, or ping.. Unless you create a rule that would allow something.. There is zero reason to create any specific block rules.. Unless for example you were not logging the default deny - and you wanted to log specific stuff.
I had previously turned off logging of "default deny rules".
If that is the case - and there is "something" you want to log.. Then yeah you can create specific rules on the wan to log those "somethings" you want to see..
edit: as example... I have turned off default deny logging. And only log these specific rules on my wan
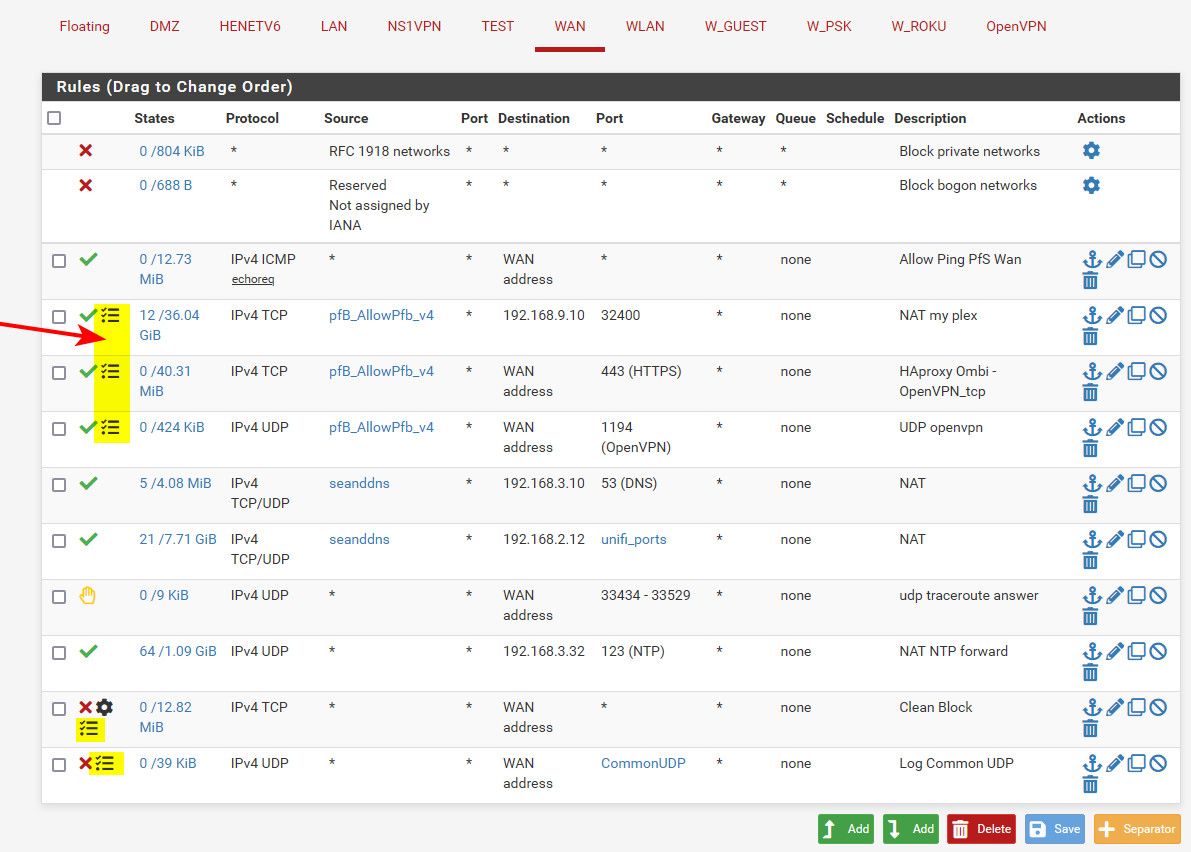
So I log stuff that would hit my plex, vpn and 443 (have some stuff forwarded to https site I host for requesting stuff on my plex). But like ping I allow but do not log, same with ntp services I provide to ntp pool. My son's network talks to my unifi controller, and my pihole - no real reason to log these allows. It could only ever be his IP per the source IP alias.
Then I log tcp SYN only.. if anything else like a broadcast or a Ack, etc. its not logged - only something send a syn is logged. The little gear icon means I have edited advanced stuff on the rule (only syn in my case). And then I log some common UDP ports that would be of interest to me if seeing traffic on those ports..
-
@johnpoz said in Can someone help me understand why is unbound resolving foreign domains (e.g. China)? Is this normal?:
Not really - not if you don't have any port forwards. Out of the box all unsolicited inbound traffic is denied anyway..
Unless for example you were not logging the default deny - and you wanted to log specific stuff.
Got it, as long as everything is blocked, does it make sense to have it log both pfBlocker denies, as well as the "Default deny rules"?
Then yeah you can create specific rules on the wan to log those "somethings" you want to see..
In the end I think this is what I would like, hopefully its doable:
Essentially I am more concerned about logging any unsolicited outbound connections to malicious IPs found in the block lists. As I saw, having unbound resolve denies, makes a lot of noise in my dns reply logs. Is this something that is possible to do? Dont log inbound, but log outbound with pfBlockerNG
-
@code4food23 said in Can someone help me understand why is unbound resolving foreign domains (e.g. China)? Is this normal?:
but log outbound with pfBlockerNG
Yeah just create a rule with what you want to log on outbound..