ip address silently blocked
-
@johnpoz, fair enough, but how do you explain that the minute the firewall packet filter is disabled, the traffic is seen and a ping returned?
Also, why is only that ip address getting a timeout, when every other address I have tried is passed by the filters and a response sent back to a ping?
Also, the on firewall is a physical metal (Sun X2100) machine, whereas the other is a VM on Proxmox. Both have the exact same behaviour.
I'll see what I can do to sniff the traffic on the metal box from the switch.
-
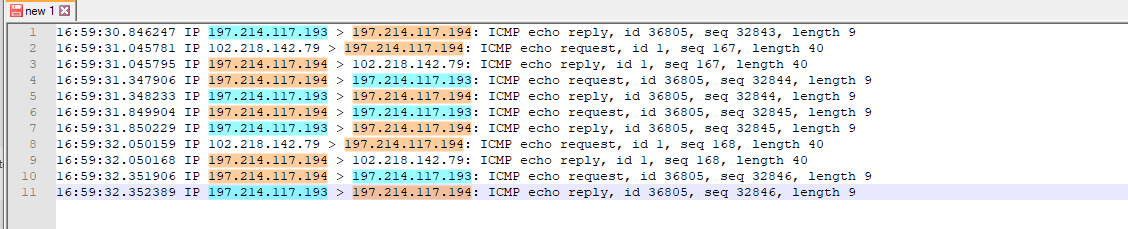
@lifeboy Why are you seeing traffic from 197.214.117.193 going to 197.214.117.194 through the firewall, aren't they both on the same subnet past the pfSense interface?
-
@lifeboy said in ip address silently blocked:
but how do you explain that the minute the firewall packet filter is disabled, the traffic is seen and a ping returned?
I don't - all I can say in 30 some years doing this stuff have never in my life seen a firewall have anyway to control what a sniff sees or doesn't see. If your sniff is not seeing it - then its not there.. Why its not there.. No idea. But nothing can happen with that traffic on pfsense if the traffic is not there.
197.214.117.193 going to 197.214.117.194 through the firewall,
That is not going through the firewall - he is sniffing on the wan.. And that is his dpinger pinging his gateway would be my take on that.. Better filtering on his sniff so he doesn't see that noise, and only sees the source of the pings would of been better idea. For all we know he didn't see the traffic because he filled up his 100 packets before pings even started ;)
-
@johnpoz said in ip address silently blocked:
@lifeboy said in ip address silently blocked:
but how do you explain that the minute the firewall packet filter is disabled, the traffic is seen and a ping returned?
I don't - all I can say in 30 some years doing this stuff have never in my life seen a firewall have anyway to control what a sniff sees or doesn't see. If your sniff is not seeing it - then its not there.. Why its not there.. No idea. But nothing can happen with that traffic on pfsense if the traffic is not there.
Well, the traffic is there the moment I disable the packet filter. So the packet filter is somehow involved in this, that much is clear.
197.214.117.193 going to 197.214.117.194 through the firewall,
That is not going through the firewall - he is sniffing on the wan.. And that is his dpinger pinging his gateway would be my take on that.. Better filtering on his sniff so he doesn't see that noise, and only sees the source of the pings would of been
better idea.Yes, it is dpinger. I didn't filter it out on purpose, simple because I want to see everthing for the duration of the capture, since I'm dealing with an unknown here.
For all we know he didn't see the traffic because he filled up his 100 packets before pings even started ;)
Nope, not the case. I first started the ping (with "ping -t"), then I started capturing and stopped it again. I then disabled the packet filter on pfSense, the ping started getting replies and I captured packets again. In the second capture, the address is present, in the first not. But I did say this all quite clearly and presented the details. It seems people don't read clearly?
My suspicion is that this is some regression that has been introduced in the 2.5.2. This address is pretty close to a bogon network range 102.218.0.0/17. Are bogon network packets just silently dropped?
As a test I have now disabled "Block bogon networks" on the WAN port and lo and behold, pings now are being responded to. As soon as I enable it again, they time out.
I suspect that instead of 102.218.0.0/17 being blocked, 102.218.0.0/16 is being blocked. I cannot find an authoritive list of bogon networks though. Can someone help with that?
-
To answer my own question: https://<firewall>/diag_tables.php and select bogon to view the list. In there 102.218.0.0/17 is listed, but no matches for 102.218.142.79, so there seems to be a buggy bogon filter.
-
@lifeboy said in ip address silently blocked:
there seems to be a buggy bogon filter.
And again even if was bogon - firewall is after sniff!! Nothing you can do in the firewall has anything to do with what you see on the interface via a sniff.. Just doesn't work that way..
Here
https://docs.netgate.com/pfsense/en/latest/diagnostics/packetcapture/index.html"For incoming traffic, captures will show traffic that arrives on an interface on the firewall regardless of whether that traffic will be blocked by the firewall configuration"
If you say it works when not doing bogon - has your bogon be updated recently? Look in diagnostic tables for what cidrs are listed in bogon for pfsense..
-
@johnpoz, look I really don't care about the semantics of what you're explaining (which is not wrong) ...
The fact is that when I turn bogon filtering off, the packets are allowed, and when I turn it back on, the packets silently are blocked. pfSense does that. It has nothing to do with how or whether I sniff the traffic or not.
So, how to do file a bug report?
-
So did you validate what is in pfsense bogon table, look under diag, tables bogon. maybe yours is old..
I don't see that listed..

Should show you when last updated

-
@johnpoz, I explained in detail in my previous reply that I did interrogate the list and didn't find a match. I even speculated that it the /17 might be a filtered as a /16, so again: Why are why going in circles?
bogon filter on: nothing is "seen" by pfSense' packet capture tool. pings time out.
bogon filter off: packets are recording by the packet filter. pings get a reply.Conclusion: There's a problem with the bogon filter.
Clear enough?
Please don't be obnoxious about this, even if you're a global moderator.
-
@lifeboy I just PM you my IP, have that IP ping my IP.. I have bogon blocked, I have it set to log and I allow ping. And running a sniff. If can show its being blocked more than happy to help you fill out a bug report.
-
Ok.. Now we are getting somewhere with info we can work with for bug report.
From my quick look at my bogon table - that should not be blocked. But clearly it is being blocked..
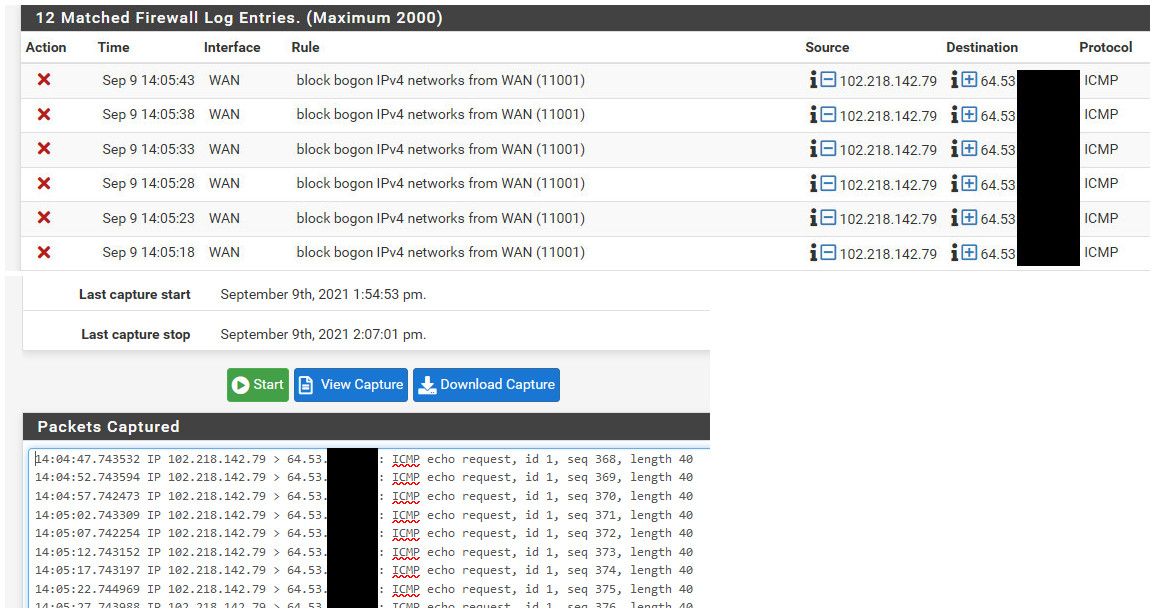
But also seeing it via sniff - so have no idea what going on why your not seeing sniff..
edit: Ok it should be blocked by bogon - with this entry
102.218.128.0/19
102.218.128.0 - 102.218.159.255So need to see if bogon is just not updated..
https://www.team-cymru.org/Services/Bogons/fullbogons-ipv4.txt
102.218.0.0/18 102.218.64.0/19 102.218.96.0/21 102.218.104.0/22 102.218.128.0/23 102.218.131.0/24 102.219.56.0/22 102.221.132.0/22 102.221.136.0/21 102.223.180.0/22 102.223.184.0/21edit: Doh I can not read this afternoon - looks like updated list it is removed. That /19 changed to a /23
-
@johnpoz I just had a look at my log setting and see that "Log packets blocked by 'Block Bogon Networks' rules" is not turned on, which explains why I didn't see them in the log. I see the bogon block log now.
-
@lifeboy From what I can tell its still listed as bogon.. So yeah not really a bug of any sort.. Who ever the ISP is that is using that IP needs to get it removed off bogon list.
-
@johnpoz You're quite right, 102.218.128.0/19 does include that ip.
I'll report it to the ISP.
Thanks for your effort and assistance. Much appreciated!
-
@lifeboy Wait... I had a misread - I don't see it listed.. The updated list seems to be good. Just need to get pfsense list to update.. Mine hasn't been updated since aug 20th
well hmmm - that doesn't seem to be working. Still showing aug20th

edit: OK - problem is the bogon list from pfsense/netgate is dated..
https://files.netgate.com/lists/fullbogons-ipv4.txt
last updated 1629435001 (Fri Aug 20 04:50:01 2021 GMT)We can file a bug report on that.. Or can just flag maybe @stephenw10 or @Derelict and maybe they can get the bogon list that is hosted by pfsense updated.. Since I do not show that 102 IP address on the actual current list.
edit: Glad we got to the bottom of this ;) Sniffing sent us on a wild goose chase it seems.. Not sure what is going on with your sniffing.. But sniffing always before firewall, nothing the firewall can do to prevent sniff from seeing traffic that is getting to the interface.
-
@johnpoz Hmmm. How do we know that 102.218.128.0/19 is not on the current list anymore? Mine is also from 20 August, but I was not able to find the authorative source by searching the web.
-
The authoritative list is the one I linked to above..
https://www.team-cymru.org/Services/Bogons/fullbogons-ipv4.txt
team-cymru has been providing bogon list for YEARS and YEARS.. That really is the go to place for current bogon lists.
I would assume that is where pfsense/netgate pulls from - but store on their own resource since they sure wouldn't want every pfsense box to be talking to team-cymru, they prob get pissed ;) How many pfsense install out there - millions? 100s of thousands for sure ;)
They update that list like every 4 hours.
-
@johnpoz, I assume it's safe to disable the bogon filters for the time being then?
-
@lifeboy Could you not create your own bogons aliases from the entries in Diagnostics -> Tables - bogons & bogonsv6 and remove the subnet your having issues with short term, create a firewall rule with the aliases and disable the default bogon rule at the top ?
You could even create the alias from the url that John posted further up and pop a pass rule above it for 102.218.142.79 if the subnet is still in the bogon list.
-
Blocking bogon is not a requirement to be secure..The IPs by the very nature of what a bogon are shouldn't even be able to talk to your wan.. Just turn blocking them off.. Not an issue at all.