HAProxy with an external modsecurity filter
-
Just sharing this in case others need a web application firewall (WAF) with their HAProxy on their pfSense firewall. I used the modsecurity WAF which I setup in a docker node running behind the firewall based on https://github.com/jcmoraisjr/modsecurity-spoa.
The tricky part was using the pfSense GUI to configure the HAProxy frontend.
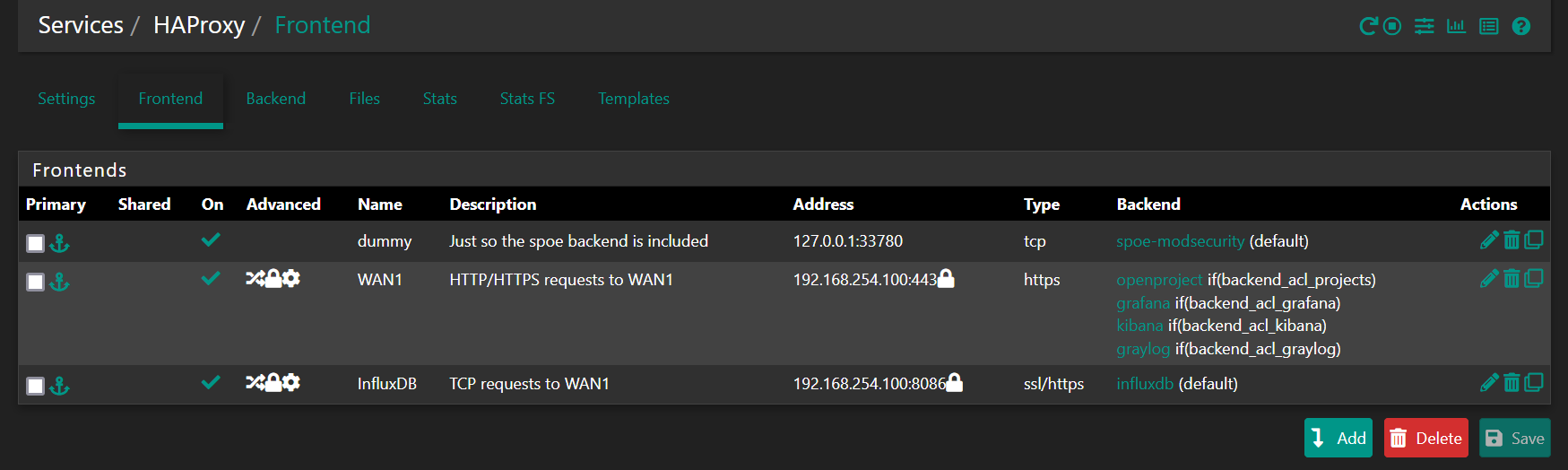
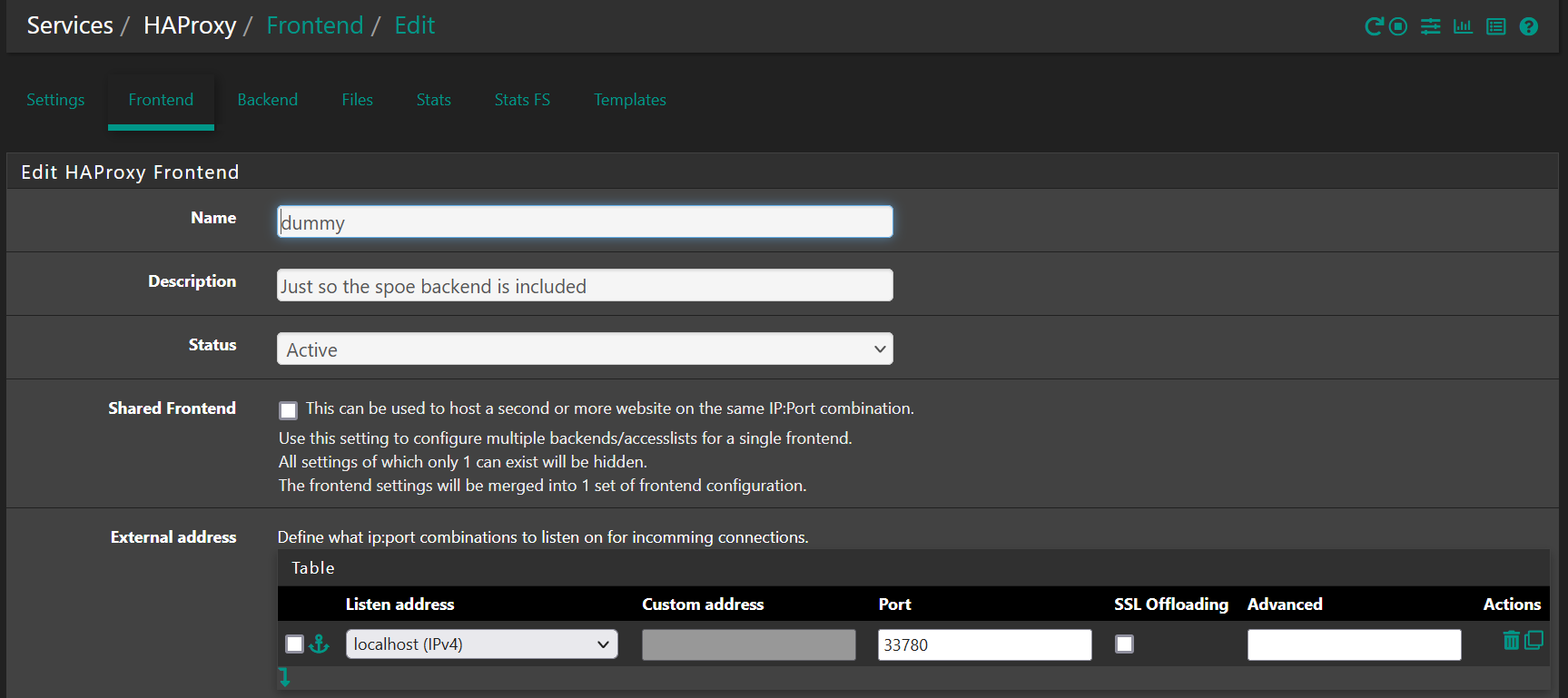
Important to note here is the "dummy" frontend entry that is there only to ensure that the modsecurity spoe backend is included. The port 33780 is just an arbitrary choice which is never intended to be actually used.Here are non-default parts of the dummy frontend entry:
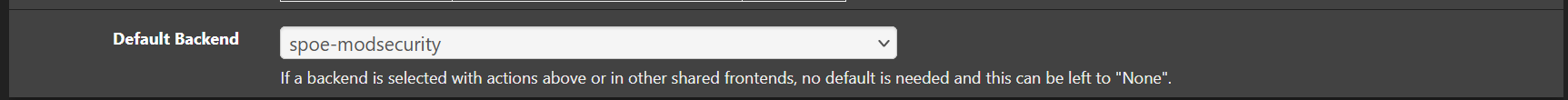
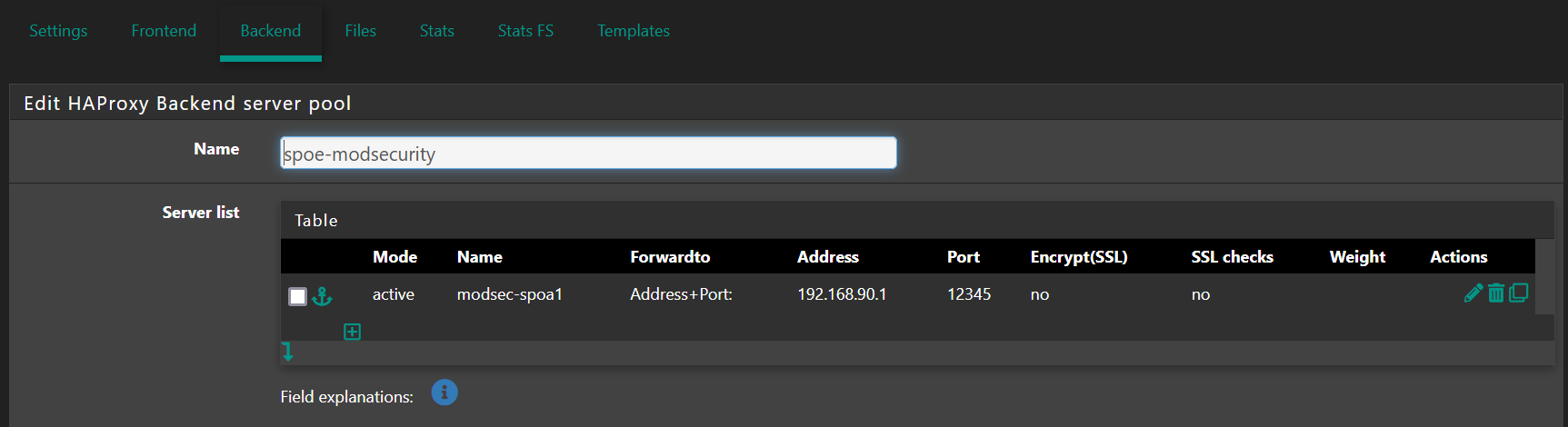
The backend's IP address in my setup is 192.168.90.1, and below is all that is needed:
Finally, the tricky part is the frontend configuration. I've a bunch of web apps on the backend all of which are protected by the modsecurity WAF. Here are screenshots of the "working" frontend's non-default parts:
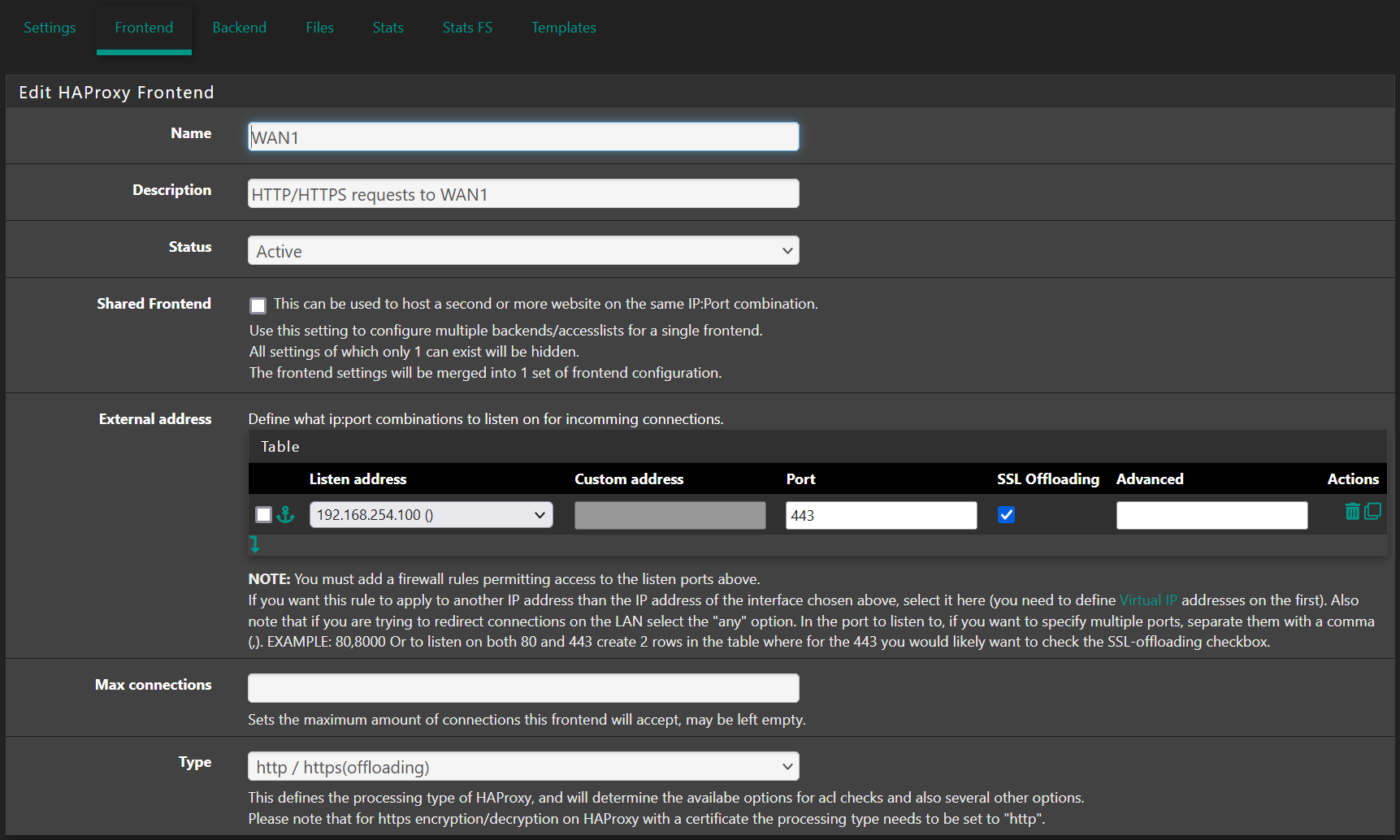
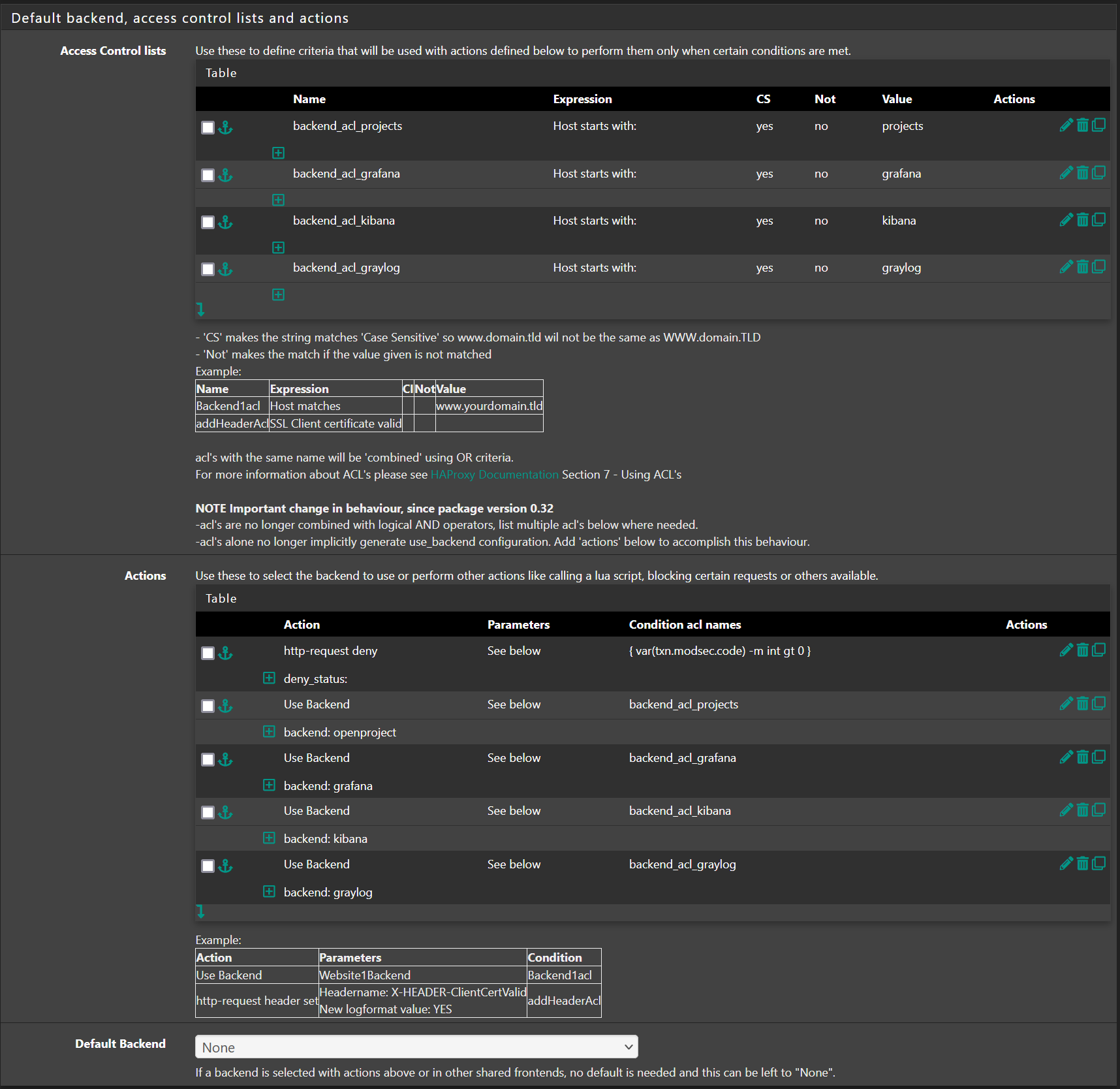
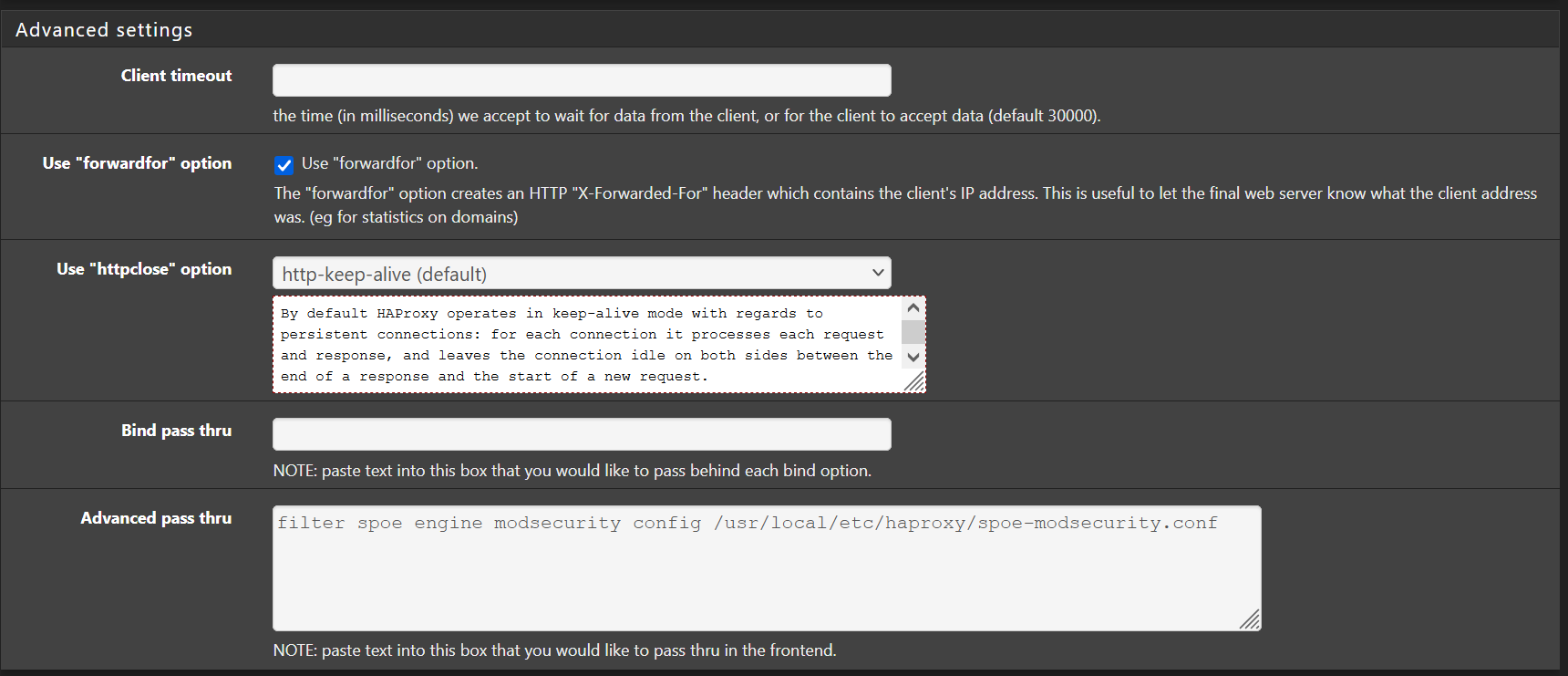
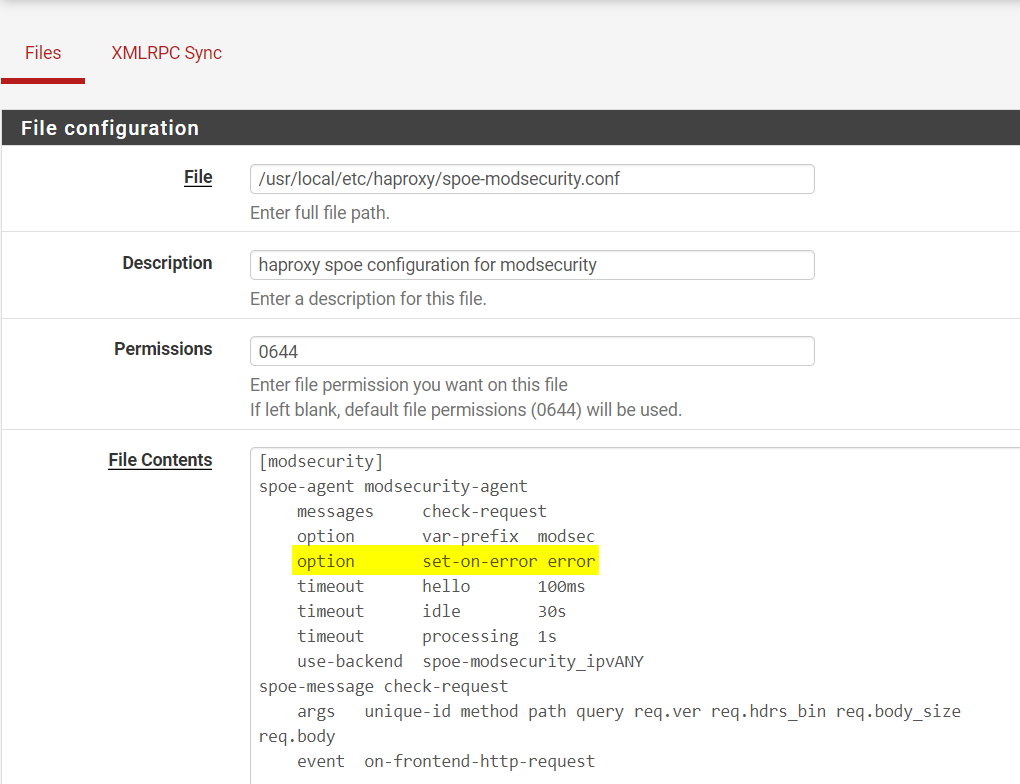
The last screenshot refers to a configuration file needed by haproxy. I used the filer package because I have a HA setup that needs several additional files sync'd to the backup node. You can do a direct edit if you only have one node but filer gives you the benefit of the files being part of the config.xml backups. Here is a screenshot of the filer entry needed:
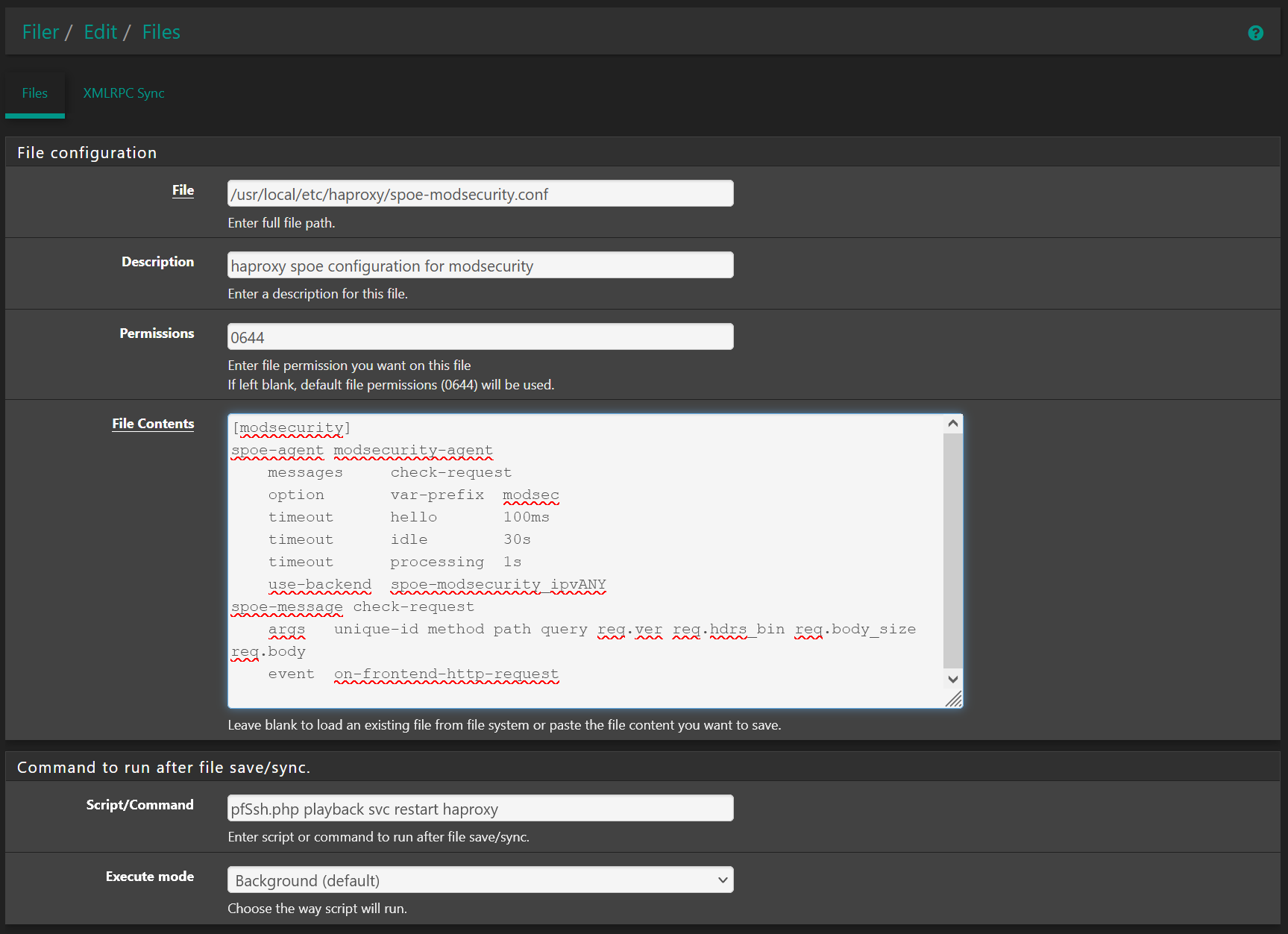
Please take node of the Script/Command entry, and IIRC the indentation used is critical. Also, at least in 2.5.1, you will find a Warning message in your general system log about the last line, which is harmless with present version of haproxy.The setup works but I should add deploying a WAF this way may not be the best of ideas which probably why a WAF is not part of pfSense package lineup.
I tested this using this: https://github.com/wallarm/gotestwaf. The default rules of the modsecurity setup mentioned earlier doesn't score perfectly but shows pfSense interface to the WAF works and that its time to tune :)
-
@lncc63 thanks for sharing.
Set this up myself and worked really well. -
Thanks, cool
-
Have run this for almost a week now and tested this using a WAF tester and got some good results. I have however made some tweaks to the rules as I noticed that if the container is offline and not serving requests for HAProxy the traffic would then go unchecked.
The following changes were made which results in a 403 error protecting the backend application if the WAF container is not running.
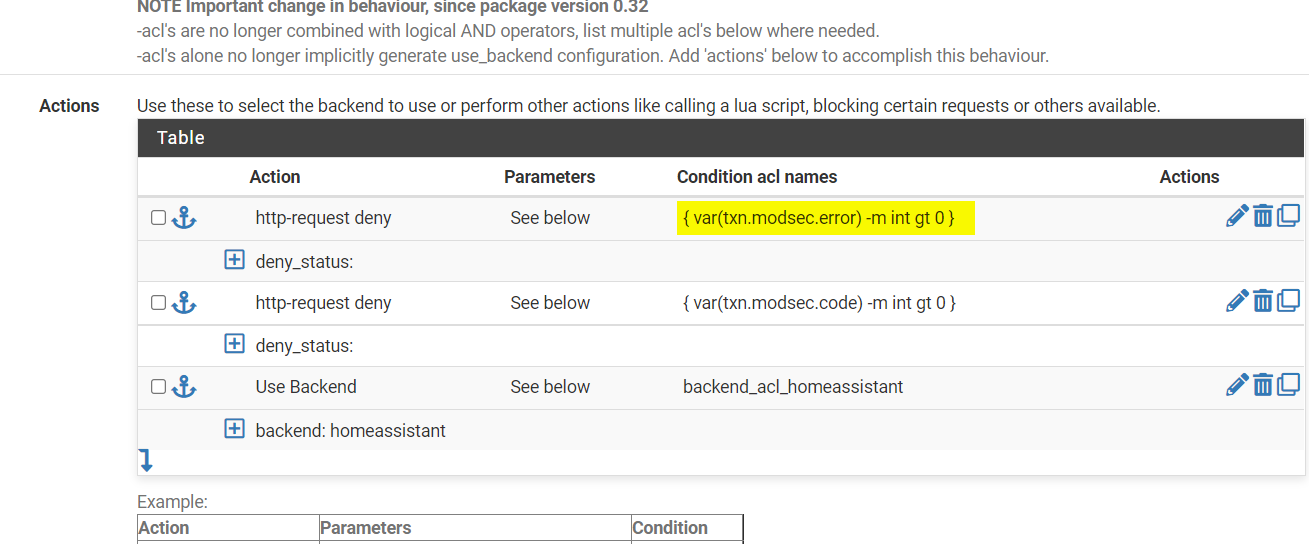
-
For anyone interested in the WAF tester I used the following docker container.
docker run -v ${PWD}/reports:/go/src/gotestwaf/reports --network="host" wallarm/gotestwaf --url={url of application under test} --verbose --skipWAFBlockCheck -
I know this is an old topic, but has anyone got this working lately with pfsense 2.6?
-
@worlddrknss yep, still working well for me. Only thing I noticed is that the config file needs to be done manually and not via filer as this strips the trailing line break which haproxy doesnt like.
-
@paulbr do you know which version of the SPOE image you are using? The latest version 0.8 from the link above gives me the following failure:
See Logs:
1656043101.401659 [00] ModSecurity: LIBXML compiled version="2.9.12"
1656043101.401849 [00] ModSecurity: StatusEngine call: "2.9.5,nginx,1.7.0/1.7.0,8.44/8.44 2020-02-12,(null),2.9.12,d1"
1656043106.408018 [00] ModSecurity: StatusEngine call failed. Query: GIXDSLRVFRXGO2LOPAWDCLRXFYYC6MJO.G4XDALBYFY2DILZYFY2DIIBSGAZDALJQ.GIWTCMRMFBXHK3DMFEWDELRZFYYTELDE.GE.165604310I also noticed there was no communication from haproxy to this instance which stopped my sites from loading after implementing the error options as you described above.
-
Hello,
Sorry for my ignorance but can you provide the way you have dokerized the WAF from jcmoraisjr/modsecurity-spoa ??
May be is not the right place to post this question but on jcmoraisjr git page I can't find any guide to pull the image or so on...Can you provide any help?
Thanks,
Gianluca