Snort-3 release
-
anyone knows when the Snort package will upgrade to Version 3. It seems the binary is using the version 2.9.18.1 from Snort.org.
The version 3 looks promising, at least on the website. -
Snort3 is well into the future. I started working on the package a couple of years ago while Snort3 was still in Beta, but the effort proved to be extremely frustrating and I gave up. There is not going to be a way to seamlessly import existing Snort2 settings into the new package on pfSense. So if Snort3 comes to fruition, it will be a green-field install (as in pretty much starting over with the configuration from scratch). I might be able to bring over which interfaces are configured for Snort, and maybe most of the rules. But many other pieces of the configuration won't come over.
I recently got over my original frustration, and started looking at Snort3 again. But as I said at the start of this reply, it's a long way off -- as in months and months away at best.
If someone else wants to volunteer to create and maintain a Snort3 package, they are welcome to give it a shot. I personally am beginning to think Suricata might be a better long-term prospect for the IDS/IPS package on pfSense.
And the final nail in the coffin of IDS/IPS on a firewall is the increasing use of encryption via SSL and TLS. Even DNS is moving to encryption. Without a MITM break of encryption on the firewall, an IDS/IPS has very limited information to work from when analyzing traffic for malicious content. It almost gets reduced to simply looking at source and destination IP addresses and ports, and the firewall already can do that itself without needing an IDS/IPS add-on package.
P.S. -- I am the volunteer pfSense package maintainer for Snort, and the package creator/maintainer for Suricata.
-
@bmeeks thanks for your explanation. well, it seems Suricata is more promising with pf Sense.
It is a pitty that Snort project made such an extreme change that there is no easy way to import an existing configuration and rules. This explains why Snort 3 rules version doesn't work in Suricata.
I have a question: How does the pass list works for Suricata? I created one and assigned an alias that contains some hosts that I trust (e.g. the IP address of my company VPN). Sometimes something in the connection triggers Suricata and it blocks it.
I tried with no success to whitelist that IP using the passlist? I've assigned the passlist in the interface configuration and restarted suricata to make sure the new settinds are in place. am I missing something? -
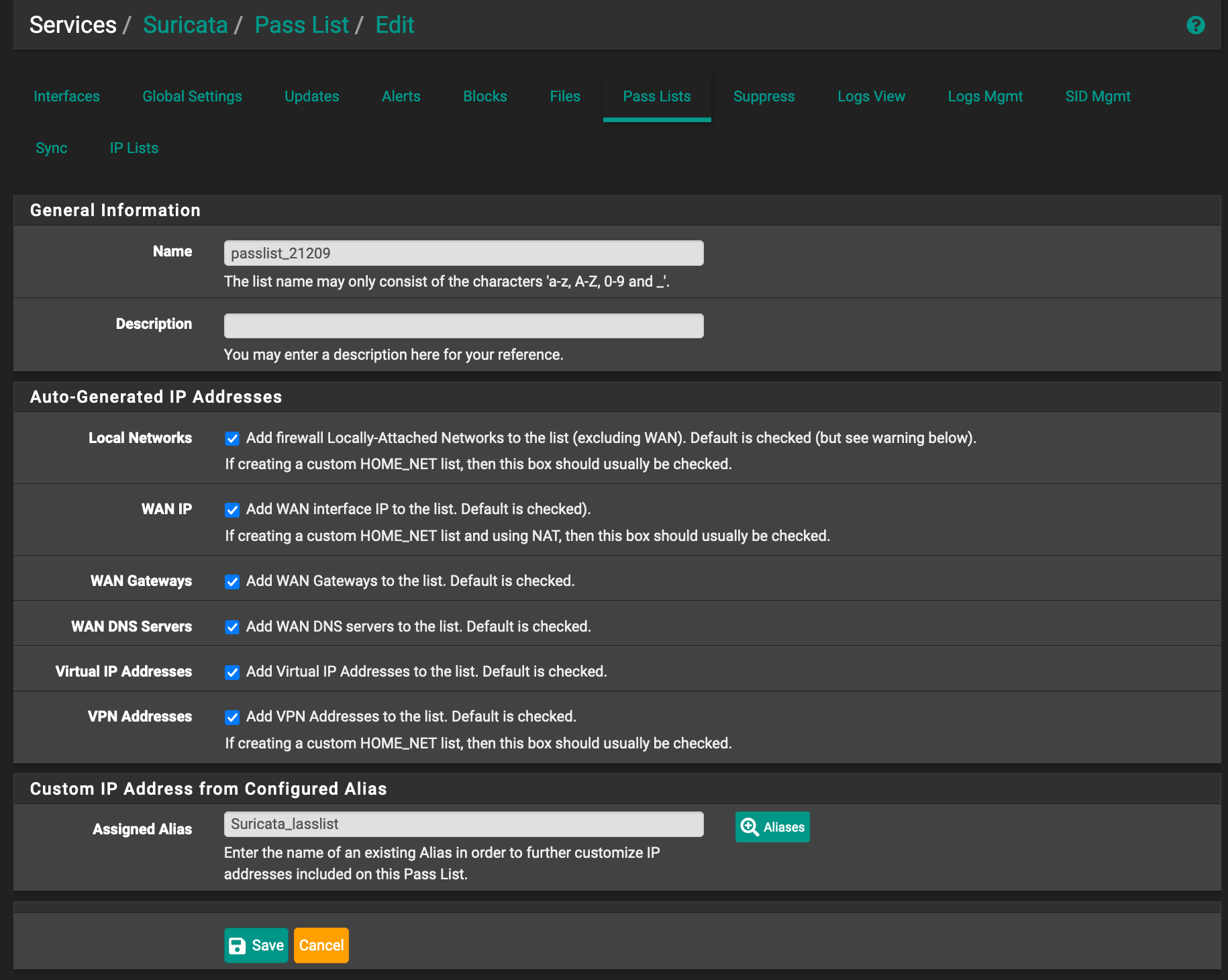
Screenshot of my passlist configuration in SuricataJust had an idea and I found the issue. I've configured as a host in aliases. I changed to network format , using the CIDR notation ip/32 (one ip). I hope this works. at least, now I am seeing the IP when I click View List. It was not showing before.
-
@bmeeks said in Snort-3 release:
I personally am beginning to think Suricata might be a better long-term prospect for the IDS/IPS package on pfSense.
A suggestion to switch to Suricata? (no polemic question) Just thinking loud ...
Regards,
fireodo -
@jorgek said in Snort-3 release:
Just had an idea and I found the issue. I've configured as a host in aliases. I changed to network format , using the CIDR notation ip/32 (one ip). I hope this works. at least, now I am seeing the IP when I click View List. It was not showing before.
If you don't see the IP or subnet when clicking View List, then it is not getting loaded properly and Suricata won't see it.
My long-term goal for Suricata (and for Snort3, if it comes to be) is to move away from the Legacy Blocking Mode and the need for pass lists. The Inline IPS Mode is much better, and more and more NICs will now be supported with the move to the
iflibAPI wrapper for network card drivers in FreeBSD 12 and higher. -
@fireodo said in Snort-3 release:
@bmeeks said in Snort-3 release:
I personally am beginning to think Suricata might be a better long-term prospect for the IDS/IPS package on pfSense.
A suggestion to switch to Suricata? (no polemic question) Just thinking loud ...
Regards,
fireodoI would not go that far yet (to suggest switching to Suricata). I probably need to check again, but last time I did look, I did not see an End-of-Life (EOL) date for Snort2 support on the Snort site.
Who knows? The clouds might part, the sun shine, the birds sing, a rainbow form, and I might get a Snort3 package up and running ...
 .
. -
@bmeeks said in Snort-3 release:
The clouds might part, the sun shine, the birds sing, a rainbow form, and I might get a Snort3 package up and running ...





-
@bmeeks Moving away from legacy mode, it would be great.
-
@bmeeks i've tried last year (2.4.5-p1) to move from legacy to inline mode without success. I had problems with the hardware checksum offloading with my ix0 (an intel x520) NIC.
I tried disabling the TXCSUM RXCSUM and my pfsense crashed after a reboot.
Tried to connect via serial and it says : "ix0 drop mbuf needs checksum offload enable" (repeated n times) and no way to resolve it.
I had to install fresh pfsense image and restoring a backup.
Now after one year, with 2.5.2 i want to try it again, but i'm scared about this.
What do you think?p.s. i also have an igb0 (wan) and an em0 (failover wan) , i know there's no problem with these NICs, right ?
Thanks, Marcello.
-
@xm4rcell0x said in Snort-3 release:
@bmeeks i've tried last year (2.4.5-p1) to move from legacy to inline mode without success. I had problems with the hardware checksum offloading with my ix0 (an intel x520) NIC.
I tried disabling the TXCSUM RXCSUM and my pfsense crashed after a reboot.
Tried to connect via serial and it says : "ix0 drop mbuf needs checksum offload enable" (repeated n times) and no way to resolve it.
I had to install fresh pfsense image and restoring a backup.
Now after one year, with 2.5.2 i want to try it again, but i'm scared about this.
What do you think?p.s. i also have an igb0 (wan) and an em0 (failover wan) , i know there's no problem with these NICs, right ?
Thanks, Marcello.
The big change between pfSense-2.4.5 and 2.5.x is the move to FreeBSD 12.2-STABLE. That meant many NIC drivers were migrated over to use the new iflib wrapper API. Netmap operation is now bundled into the wrapper API, and that relieves NIC driver developers from having to directly support that mode of operation. There were a number of bugs in the earlier NIC drivers when it came to netmap operation.
And with the recent inclusion of version 14 of the NETMAP_API in FreeBSD 12.2-STABLE, netmap picked up a new feature -- the ability to support multiple host stack rings. I've worked with the upstream Suricata team to integrate this new functionality (netmap API v14 and multiple host stack rings) into the Suricata package. It is slated to be released upstream when version 7.0rc1 of Suricata comes out. However, I've already backported the changes into the Suricata binary used with pfSense. So the latest Suricata package has the new API code in it.
Snort on pfSense also has multiple host rings support. But because Snort 2.9.x is itself single-threaded, there is not much benefit when using multiple rings. They all still get serviced by only a single thread, and thus run on a single CPU core. Suricata's multithreaded nature means all CPU cores can be used and traffic spread across them when using the new netmap code.
If you want to try inline IPS mode again in the current Snort package, enable it and see how it performs. You can easily switch back with just two mouse clicks and a restart of Snort.
If you want to try multithreading with the new multiple host stack rings, consider giving Suricata a test drive. It works very much like Snort in terms of the configuration. Just be aware that if you are using VLANs, you might want to wait until the 6.0.3_3 update for Suricata is posted.
-
@bmeeks now I'm using suricata, and i have vlans on this ix0 NIC
So I'll wait the _3 version for trying the inline mode with suricata :)
Anyway my problems starts when I disabled the checksum offload (1 year ago with 2.4.5-p1), not when enabling the inline mode.
So now it's "safe" try to disable it again on 2.5.2?Dumb question: i cannot run inline mode without all the offloads disabled?
-
@xm4rcell0x said in Snort-3 release:
@bmeeks now I'm using suricata, and i have vlans on this ix0 NIC
So I'll wait the _3 version for trying the inline mode with suricata :)
Anyway my problems starts when I disabled the checksum offload (1 year ago with 2.4.5-p1), not when enabling the inline mode.
So now it's "safe" try to disable it again on 2.5.2?Dumb question: i cannot run inline mode without all the offloads disabled?
Without disabling all of the NIC-based processing such as LRO, checksumming, etc., you will likely see various "bad packet" errors. So yes, you need to disable all of the offloading options for your NIC. That includes the hardware VLAN tagging options. You want to let the kernel do it all.
Back in pfSense-2.4.5 (which was based on FreeBSD 11.x), some NICs had driver bugs. This was especially true with netmap operation because netmap support had to be purposefully coded into the driver. That is no longer the case in FreeBSD 12.x where iflib is used. Most of the NIC drivers in FreeBSD 12 have been ported over to iflib. So hopefully that means things that formerly gave you issues may be cleared up in FreeBSD 12.x (and thus in pfSense-2.5.2). One bug I do remember was an Intel NIC that did not actually disable hardware VLAN tagging even when the option was properly passed to it.
There are system tunables available for some NICs as well. There is a Sticky Post at the top of this forum with some examples of system tunables for a few Intel NICs.
I run Snort using Inline IPS Mode on a Netgate SG-5100 without issue. That box has ix and igb NICs in it.
And in terms of your problem with the earlier pfSense-2.4.5 install, even if the NIC driver crashes and burns when starting up, you should be able to access the console. And there on the console you can edit the
config.xmlfile and remove any customized system tunable values you entered (I assume you entered these options using the GUI). Or if you did it on the pfSense Advanced Networking tab, those options are also stored as text strings inconfig.xml. -
@bmeeks another dumb question (sorry that's only an hobby....and i have to thanks you and this forum for all I know )
You say hardware VLAN tagging... But I don't think I have enabled it.
I only have vlans configured into pfSense's interfaces tab...that's only a "software VLAN tagging" right? -
@xm4rcell0x said in Snort-3 release:
@bmeeks another dumb question (sorry that's only an hobby....and i have to thanks you and this forum for all I know )
You say hardware VLAN tagging... But I don't think I have enabled it.
I only have vlans configured into pfSense's interfaces tab...that's only a "software VLAN tagging" right?Some NICs have the feature and enable it by default. Here is a link to some pfSense documentation about that: https://docs.netgate.com/pfsense/en/latest/vlan/index.html. And here is a post from the forum discussing how to disable it on igb cards: https://forum.netgate.com/topic/158898/disable-hardware-level-vlan-filtering-on-igb-network-card.
One thing to be aware of, though, is that the NIC driver name in FreeBSD is sort of generic in that the driver may cover a number of slightly different variations of the same basic hardware. Not all igb cards are absolutely identical.
-
M mcury referenced this topic on