Block access to LAN from any other network
-
Hello everyone,
Can anyone explain why this rule is not blocking ?
I even disable the anti-lockout rule to remove source(any) for 80 and 443.This is LAN16 (192.168.16.0/24) and my goal is to allow only access from physical LAN port.
I have added a rule to block everything that is not from LAN16.I can still access the pfsense and LAN16 through a tunnel VPN network 172.16.92.0/24.
Any comments appreciated.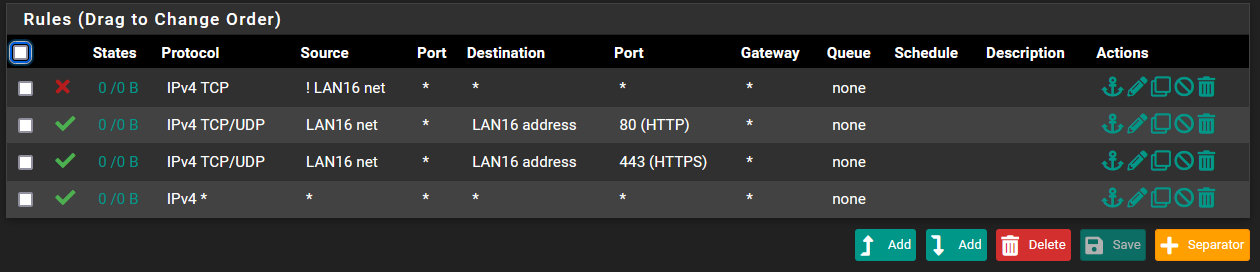
-
First I will use * (any) not TCP for the block rule to block all.
But to block the VPN network, I think I would block it on the VPN interface and tell Block any, source VPN net, destination LAN16 netBut i think the block rule do not apply as if this is the lan16 interface, then VPN traffic will not be ever the source on the interface? or am I wrong here?
-
The firewall rules apply to traffic coming inbound through the interface from the external network towards the pfsense. You cannot block traffic coming from other interfaces. To block vpn you would make a rule on that VPN interface blocking traffic destination to VLAN16.
-
@brians Thank you, is this a pfsense implementation or is general for all firewalls ?
I mean what is the correct thinking here?
If need to restrict, restrict on all other interfaces.
If allow, don't restrict on other interfaces (? ? ?) -
@mikki-10 to my understanding, the source will be the tunnel network of VPN. sometimes i don't get this concept.
But you are right, for some reason is not working. Maybe this is why they have the source and destination "this firewall" ? -
@bambos said in Block access to LAN from any other network:
I mean what is the correct thinking here?
Like brians said: Filtering is done where traffic enters the firewall.
So you have to watch your rules on your "vpn".You have to learn the basics...
-
@bob-dig thanks for your feedback. i'm learning the basics now, you are right. So to make things simple, considering only LAN16 setup:
For restricting incoming to LAN16, i have to restrict on all other interfaces.
For allowing outgoing from LAN16, i have to work on the LAN16 interface.Is this correct ?
-
@bambos said in Block access to LAN from any other network:
@bob-dig thanks for your feedback. i'm learning the basics now, you are right. So to make things simple, considering only LAN16 setup:
Is this correct ?
Yes.
And by default everything is blocked so technically you don't have to restrict on all the other interfaces but selectively allow on those interfaces, you want to have connectivity to your LAN.
If you not have don this already, make a rfc1918-alias for all private addresses. This inverted is good for routing all the internet traffic and not touching your "local rules".
-
@bob-dig thank you Mr.Bob,
as a newbie i was trying to get the OpenVPN working, following a tutorial, so on the VPN interface i have the allow any rule now. So i will tear that apart and start adding allow rules selectively. Thanks for help.
-
@bambos said in Block access to LAN from any other network:
what is the correct thinking here?
What makes the most sense to you? You can create a "floating" rule that applies to traffic going out of an interface
firewall -> rules
floatingWhen you add a rule there's a drop down menu for Direction where you can specify "out"