Backdoor into Home network through company laptop
-
I just discovered my work laptop is being used as a backdoor into my home network.
I had the device on the guest network, with it bypassing my VPN (as work has its own pulseVPN).Nevertheless, when the work PC is not connected to their VPN, I had a few ports open e.g. web browsing.
It seems they have been probing my network from the inside (most likely when the PulseVPN has been down) as they contacted my managed about having the 3rd party vpn installed on my laptop (which it is not - the vpn is a client connection on my pfsense).
Can someone advise how best to ensure they have no access to any other internal part of the network inc the firewall and only the PulseVPN will be passed through. It is of course no surprise the company is from a country that is renowned for do as I say, not as I do.
-
@gwaitsi
I don't know where you are, but in many places that would be illegal.
Regardless, if that computer is connected to your local network, there's not much pfsense can do, beyond blocking whatever they're connecting to.
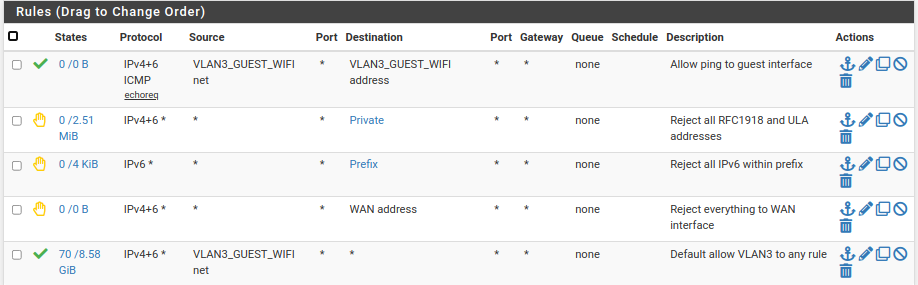
Perhaps you should only connect to your guest network and have your rules set up to not allow anything to the main network. That's what I do here. I have my work computer connected to my guest WiFi and my rules do not allow any access to my main network or even pfsense, other than ping the interface.
Here are my guest WiFi rules:
-
@jknott it's unbelievable. It is a criminal offence with jail time in my country, but that has never stopped my employer's country from creating their own set of rules for themselves ;-)
I have created a vlan with a single ip and blocked everything on the lan side excep 443 access to the vpn servers and dhcp/dns on the pfsense.
I will give them conditional approval to do testing. Try to get some free penetration testing results
why do you have the block ipv4+6 at the top? I have;
- allow IP4 work_laptop port 443 to work_vpn * gw_wan
- reject IP4/6 * * * *
do i have the order wrong?
-
@gwaitsi Order of the rules as shown in the GUI is "first match wins" so if a packet matches your IPV4 from work_laptop port 443 to work_vpn rule, the reject IPV4/6 is never evaluated.
-
@gwaitsi
I use block IPv4 & IPv6 because I have both on my network and am just covering all bases.
As for your connection, a guest LAN, such as mine, should be all you need and you could still have other guests on it. As I mentioned, my work computer is on my guest VLAN, so they could probe all they want and won't find anything. I have OpenVPN on my main network.
BTW, I was just looking at some stuff from my work computer. I'm currently doing training for Avaya IP Office unified communications and so was using Packet Capture to see what it was doing. Likewise, you could use it to see what snooping is going on.
-
@gwaitsi said in Backdoor into Home network through company laptop:
why do you have the block ipv4+6 at the top? I have;
allow IP4 work_laptop port 443 to work_vpn * gw_wan
reject IP4/6 * * * *do i have the order wrong?
As mentioned above, rules are run in order until first match. So, I first allowed ping to the interface. I then blocked the specific IPv4 and IPv6 addresses and finally allowed access out to the Internet.
-
@jknott yeh, so my order is correct right.
only allow out the specific vpn for the specific device. block everything else to lan or wan. -
@jknott said in Backdoor into Home network through company laptop:
my work computer is on my guest VLAN, so they could probe all they want and won't find anything.
Problem is, I had both my work laptop and my wife's laptop on the same guest network. So my work penetration testing, could have potentially hit my wife's work. Then the question comes, who is legally liable - punishable by 2yrs here. Now it will put them both on separate isolated vlans so no chance of this happening again
-
@gwaitsi
Why is your wife's computer on the guest LAN? Don't you trust her?

My guest WiFi is used for guests, work computer and TV. The only reason the TV is on it is because it can't handle the 63 character password I use on my main SSID.
-
@jknott said in Backdoor into Home network through company laptop:
Why is your wife's computer on the guest LAN? Don't you trust her?
of course i meant her work laptop. i didn't think anything of it, because they both require company vpns, but in hindsight, probably should have isolated them from day 1
-
@gwaitsi said in Backdoor into Home network through company laptop:
I had the device on the guest network, with it bypassing my VPN (as work has its own pulseVPN).
It might be an application on the laptop itself talking back to the office, I quite often see snort throw up a warning about the Zscaler application on my work laptop about http being run over port 443 regardless if I'm connected via pulse or not.
If you're that worried about it place the laptop in a protected port on your switch if you can, so the only l2 device it can talk to is the gateway.
-
Give the DHCP lease a static IP and make rules for the mentioned IP.
Block everything for the IP except access to the internet.
First rule basis.... put it on top.
-
@gwaitsi said in Backdoor into Home network through company laptop:
Problem is, I had both my work laptop and my wife's laptop on the same guest network. So my work penetration testing, could have potentially hit my wife's work.
I assume, your guest network is a Wifi. Most wireless access points have the capability to block communication between stations connected to it within the same SSID.
It's a good advise to activate this option on a guest network as there should be no need to access any other device.