Anyone know openvpn obfuscate technology?
-
FYI, I can map network drive using TUN.
Thanks. So can I now, too. pfSense makes it easy. I came from a DD-WRT background and was happy just to get it working in that case. I was originally under the impression that tun was for private browsing and tap was for network browsing.
Now I have 3 servers:
1 tun for safe remote browsing - easy to sign on to.
1 tun for network access: difficult to sign on to and uses different certs and sign on requirements. Also allows safe browsing
1 tap just because I had it and it worked fine. Wouldn't do it again, though, now that I know how to make tun 'bridging' work.Still looking for openVPN obfuscate insights. I put the new server on port 4664 tcp (google docs) but don't expect it to hide and better than the other servers.
-
"now that I know how to make tun 'bridging' work."
HUH??? You sure and the hell do not need to bridge to access file shares..
-
"now that I know how to make tun 'bridging' work."
HUH??? You sure and the hell do not need to bridge to access file shares..
Chill. It's a figure of speech. That's why it put it in quotes. I don't live and breath routers like you do. Mentally replace 'bridge' with 'network access just as if it were bridged'. If that's wrong terminology, try well ….
Anyway, back to the original question about obfuscation .....
-
Bridge would not be the term.. But to your obfuscation question, already answered. The only way to hide that its openvpn ssl traffic would be to put the tunnel inside a different tunnel, be that normal SSL tunnel or SSH tunnel, etc.
-
Bridge would not be the term.. But to your obfuscation question, already answered. The only way to hide that its openvpn ssl traffic would be to put the tunnel inside a different tunnel, be that normal SSL tunnel or SSH tunnel, etc.
Thanks. I expected to still do a lot of look up work after some pointers, but this is still too vague. Just say "I don't know but this is probably what the ones with programming staff who CAN hide it do" next time. MY paid VPN providers must make it look like normal traffic. That's why they can get though and my port switch-a-roos don't work.
I guess if it were easy, everyone would be doing it and I wouldn't be asking here.
Thanks, anyway. At least I got tun 'bridging' to work.
-
not freaking 'bridging" dude..
What part do you not understand about putting your vpn inside a ssl?? Hot spots for internet traffic sure and the hell are not doing deep packet inspection saying oh shit that is a vpn, block that. They are just blocking non standard ports like UDP 1194.. Run your openvpn connection over tcp 443 so it looks like normal https traffic. Only doing a DPI would where your at be able to know its not normal ssl..
-
@johnpoz JohnPoz, I understand we can use port TCP 443 for OpenVPN. Is there any way to use it without port forwarding the port i.e. not visible to port scanners? If not, how dangerous is it to leave open port TCP 443 to the internet? Shieds-Up always gives me a warning flag that TCP 443 is open and very dangerous to leave open. Thoughts?
-
@frankzappa said in Anyone know openvpn obfuscate technology?:
Shieds-Up always gives me a warning flag that TCP 443 is open and very dangerous to leave open.
It gives you a warning about ANY Port ;) Opening services to the public is always a risk.. But to access even to attempt to access your vpn has to pass signature on the packet.. Or its just dropped..
example.
Oct 7 18:08:43 openvpn 68875 Incoming Control Channel Encryption: Using 256 bit message hash 'SHA256' for HMAC authenticationLookup how the tls key auth works.
Is there any way to use it without port forwarding the port i.e. not visible to port scanners?
No - how would that work.. The only way to do what would be able to limit the source IP on who can talk to the service. Sure if you know what IPs would be talking to you, you could prevent them from talking to your service, and the firewall would just drop the traffic because the source IP is not on the allow list..
You can with say pfblocker create an alias that only allows say IPs from the company your phone uses for cell connections. Or could limit to specific country your in.. To lower the exposure.
If you know your only going to be accessing the vpn from your work location - then you could limit access to only the public IP from your work site, etc.
-
@johnpoz Thanks. The part that makes no sense to me is how OpenVPN can listen all day on UDP1194 and be stealthy, but we have to "open" a port to listen on TCP443, even if OpenVPN lets you share port 443. I guess I don't understand why we don't need to open other ports e.g. 80, 25, or 8080, and yet they work fine and don't show up on a port scan as open., Sorry, I'm rambling. I'll get off my soapbox now.
-
@frankzappa said in Anyone know openvpn obfuscate technology?:
all day on UDP1194 and be stealthy
No its not stealthy at all.. That grc scanner is only looking for tcp.. If the port is open its open and you could connect to it.. If it answers..
Are you running services on 80, 25 or 8080?? Then no you don't need to open them.. If you want people to connect to your "service" on 443 - then you have to have it open.. If its open, then people can see it via a scan.. Just like if you were running services on 25 (smtp) or 80 http.. or 8080 normally used as proxy or just http if 80 is blocked inbound, etc.
-
@johnpoz Ok, got it. Thanks. I was thinking, for example, that SMTP needs port TCP25 open... but, as you mentioned, not on my machine as it's open on the google servers for my email. Makes sense now. You're right...I'm not running any services on my network ergo, nothing is open. So, if I do open port TCP443 for OpenVPN, is it possible for someone to hack that port if they don't have proper OpenVPN certs or user authentication, and is it possible to attack that port (and get in) using something other than OpenVPN service e.g. some kind of hacking tool? I get that anything is possible, but is it likely?Thanks
-
@frankzappa openvpn is pretty freaking secure.. As I mentioned if setup with current recommended settings. TLS auth and encryption
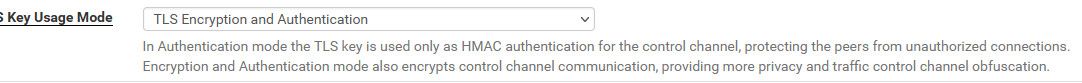
They would have to pass that first before openvpn would even start to process any data.. They would then need to be able to pass your authentication, they would need the CERT that you issued, they might also need the password you set and the cert, etc.
Now if you were running openvpn with just simple password, and no use of tls or certs in anyway - then yeah sure someone might be able to guess auth to get in..
But to get into a vpn server that is setup correctly would require pretty high level hack - and I have heard of no such possible issues. Something like that would be HUGE freaking news if there was some known exploit to openvpn..
-
@johnpoz Many Thanks.