site to site connection not working
-
I have recently moved but I want to still be able to access my homes network resources and my family at my home mine. so I have set up a pfsense server in my place and at home, I have an ubuntu server running OpenVPN.
my LAN network is 192.168.1.0/24 and my homes network is 192.168.0.0/24
I connected to my OpenVPN server at home with this tunnel settings
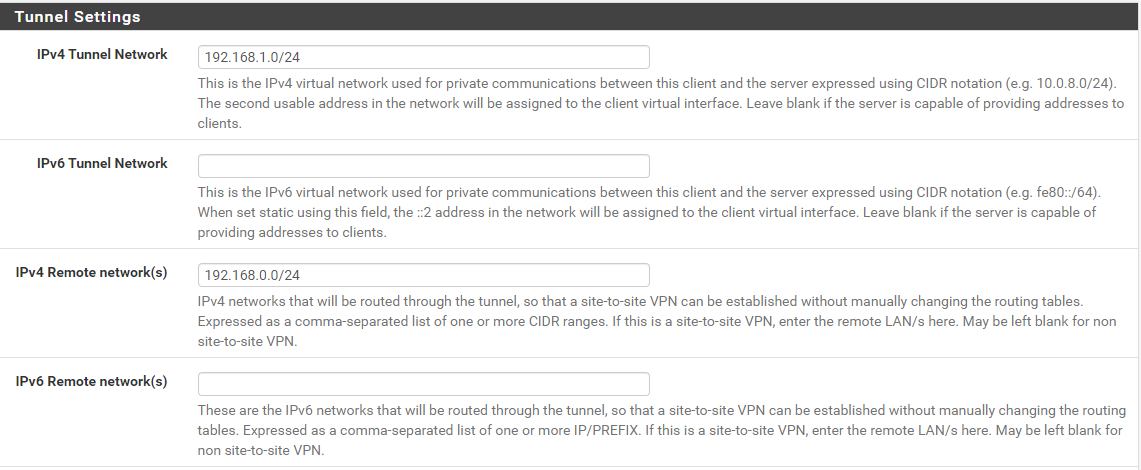
and as you can see I can the ovpn interface goes up fine
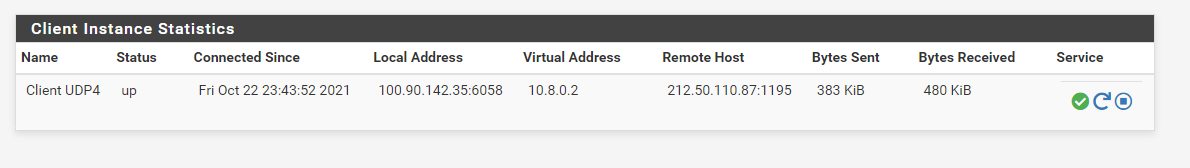
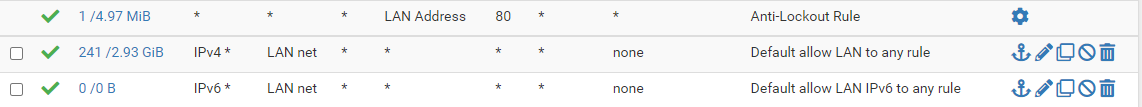
then I made a rule on my interface to allow traffic
LAN should be fine since I have the default allow any rule
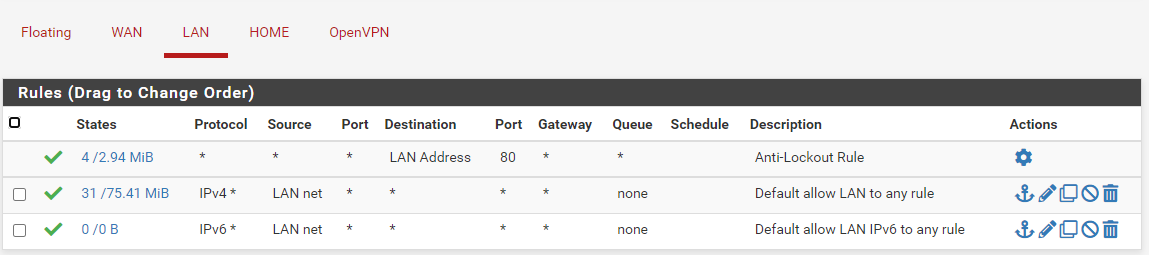
my default gateway is my wan port on pfsense and didn't add a static route since in ovpn IPv4 Remote network(s) option it states
"IPv4 networks that will be routed through the tunnel, so that a site-to-site VPN can be established without manually changing the routing tables."But I can't get access to my home network. and as a bonus my internet connection stops working which i don't understand since my default gateway is my wan port. my internet connection goes back to normal when i stop ovpn service
-
@elliopitas said in site to site connection not working:
my LAN network is 192.168.1.0/24 and my homes network is 192.168.0.0/24
I connected to my OpenVPN server at home with this tunnel settingsLeave the Tunnel Network box blank. This is given by the server.
then I made a rule on my interface to allow traffic
The rule on HOME might be useless with LAN net as source.
Anyway a pass rule here is only for allowing access from the remote site to you.
Also check the rules on the OpenVPN tab. These will also by applied if they are matching.But I can't get access to my home network.
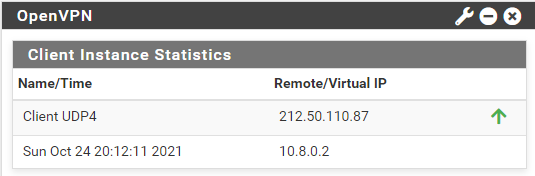
Are you able to access the OpenVPN server by its virtual IP? This requires that there is a network service running on of course.
The Ubuntu server doesn't pass traffic to the devices behind by default. This need some extra settings.
Additionally you will have to do masquerading on the servers LAN interface, otherwise the devices will send responses to their default gateway.and as a bonus my internet connection stops working
Presumably the server pushes the default route to the client. If you want to keep this setting on the server for other purposes you can avoid that the OpenVPN client sets the default route by checking "Don't pull routes".
-
Leave the Tunnel Network box blank. This is given by the server.
done
The rule on HOME might be useless with LAN net as source.
Anyway a pass rule here is only for allowing access from the remote site to you.
Also check the rules on the OpenVPN tab. These will also by applied if they are matching.changed
LAN
HOME

OPENVPN

Are you able to access the OpenVPN server by its virtual IP? This requires that there is a network service running on of course.
yeaThe Ubuntu server doesn't pass traffic to the devices behind by default. This need some extra settings.
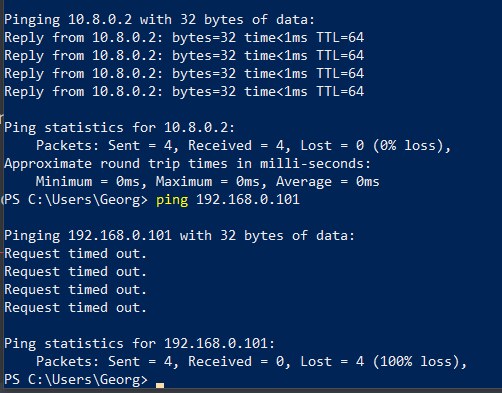
i added push "route 192.168.0.0 255.255.255.0" in ovpn server config still no dice
btw if I VPN from ovpn client on my device withroute-nopull route 192.168.0.0 255.255.255.0I can access my home resources just fine and it forwards just my networks packets thru vpn
Additionally you will have to do masquerading on the servers LAN interface, otherwise the devices will send responses to their default gateway.
and as a bonus my internet connection stops working
Presumably the server pushes the default route to the client. If you want to keep this setting on the server for other purposes you can avoid that the OpenVPN client sets the default route by checking "Don't pull routes".
ok this fixed that
-
@elliopitas said in site to site connection not working:
i added push "route 192.168.0.0 255.255.255.0" in ovpn server config still no dice
btw if I VPN from ovpn client on my device with
route-nopull
route 192.168.0.0 255.255.255.0I can access my home resources just fine and it forwards just my networks packets thru vpn
So I guess, you're able to access the home devices from pfSense as well. Try a ping from pfSense.
-
@viragomann said in site to site connection not working:
@elliopitas said in site to site connection not working:
i added push "route 192.168.0.0 255.255.255.0" in ovpn server config still no dice
btw if I VPN from ovpn client on my device with
route-nopull
route 192.168.0.0 255.255.255.0I can access my home resources just fine and it forwards just my networks packets thru vpn
So I guess, you're able to access the home devices from pfSense as well. Try a ping from pfSense.
from pfsense shell its fine
from my laptop that is on the LAN it doesn't work
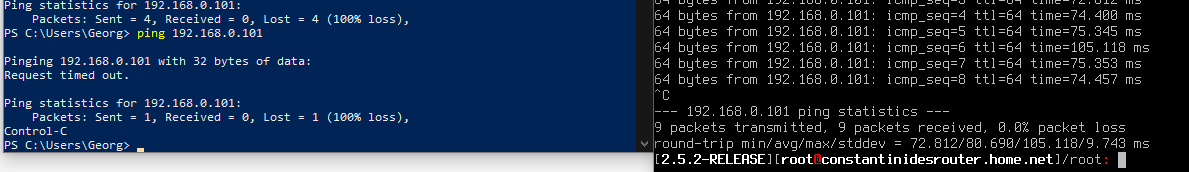
so I guess my static route works

is it something with the firewall? -
@elliopitas
Your rules allow anything anyway yet.It might be a routing issue. But you can also solve it with masqerading as I already mentioned above. I'm assuming that the Ubuntu server is not the default gateway in the home LAN and the devices do not have a route for the tunnel network to the server.
So since you're able to access the remote devices from pfSense the Ubuntu server might have a masquerading rule in iptables for the packets from VPN clients (subnet 10.8.0.0/24) on its LAN interface.
Now you need also such a rule for your LAN 192.168.1.0/24.Alternatively you can add an outbound NAT rule on the Home interface on pfSense and hence do double NAT.
BTW:
The firewall rule on HOME with the source HOME net only allows access from the VPN tunnel (= HOME net) to anywhere on your site. Don't know if this is really that what you want.
For accessing the remote site you need only a proper rule on LAN. -
@viragomann said in site to site connection not working:
@elliopitas
Your rules allow anything anyway yet.It might be a routing issue. But you can also solve it with masqerading as I already mentioned above. I'm assuming that the Ubuntu server is not the default gateway in the home LAN and the devices do not have a route for the tunnel network to the server.
So since you're able to access the remote devices from pfSense the Ubuntu server might have a masquerading rule in iptables for the packets from VPN clients (subnet 10.8.0.0/24) on its LAN interface.
Now you need also such a rule for your LAN 192.168.1.0/24.Alternatively you can add an outbound NAT rule on the Home interface on pfSense and hence do double NAT.
BTW:
The firewall rule on HOME with the source HOME net only allows access from the VPN tunnel (= HOME net) to anywhere on your site. Don't know if this is really that what you want.
For accessing the remote site you need only a proper rule on LAN.yes you are right the ubuntu server is not the default gateway
I added the outbound rule and now i can have access to my home lan from my lan
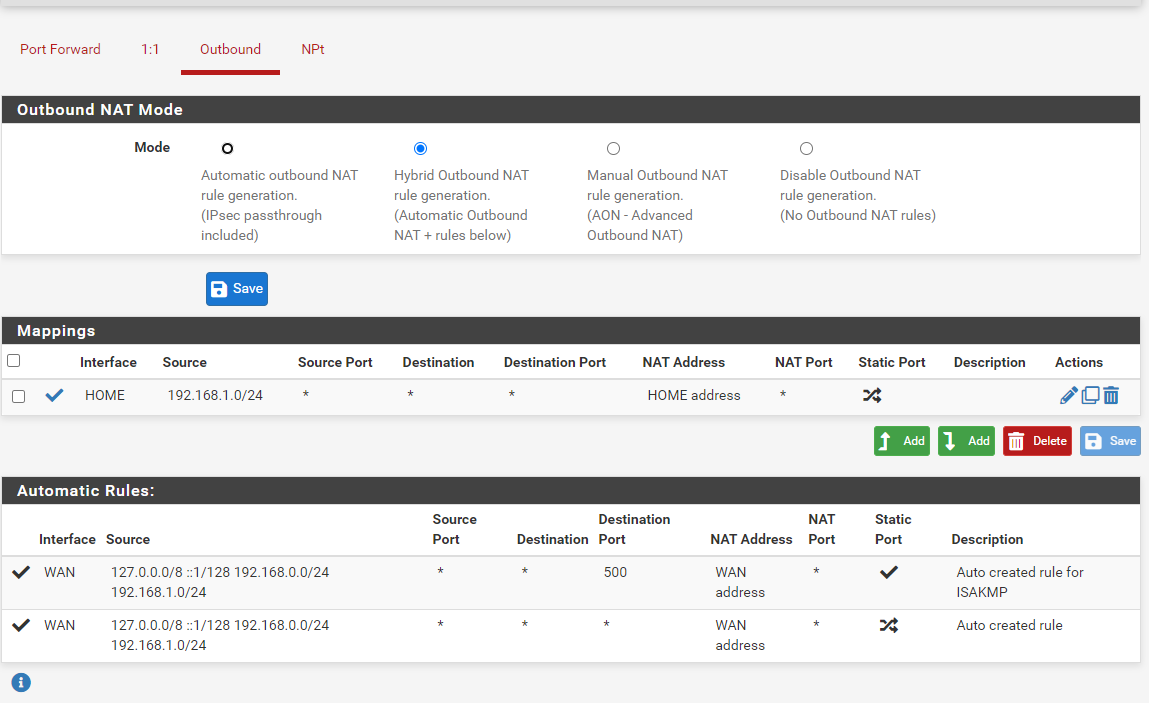
from my laptop on my lan pinging the ubuntu server and my default gateway (isp router)
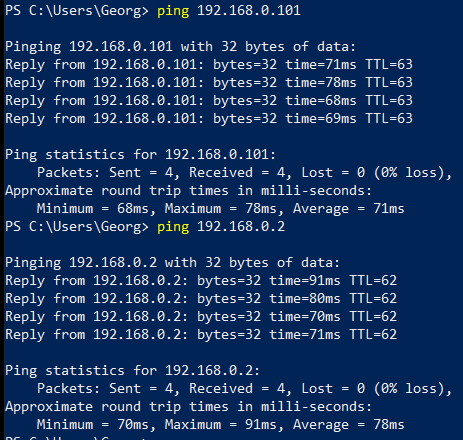
but my home lan still doesn't have access to my local lan
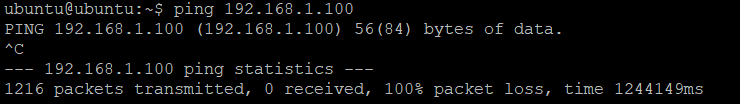
I guess I have access because when I sent a packet and the device on my home lan replies it replies to the ubuntu ovpn server and the server sends the packet thru the tunnel but when a device from my lan tries to communicate it sends the packet to the default gateway and the default gateway my isp router doesn't know what to do with it. correct?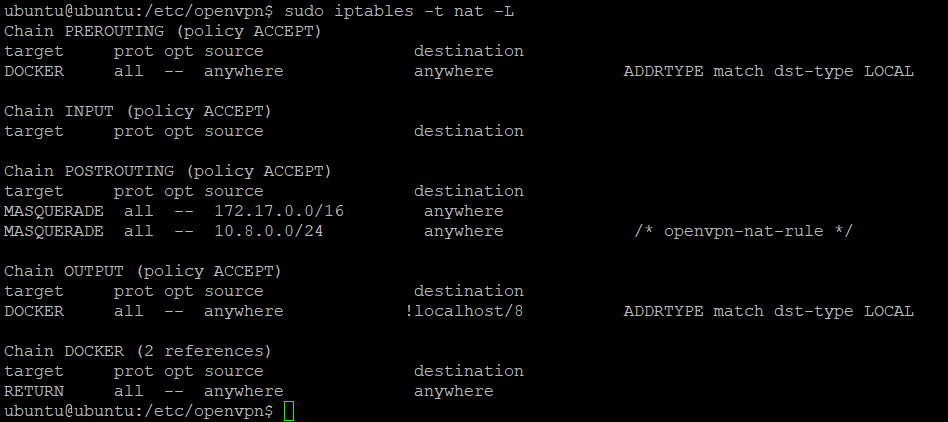
found the masquerading rule on the ubuntu server. do I have to add another one with source 192.168.0.0/24 and dest 192.168.1.0/24 to work?btw I appreciate all your help thus far. i am starting to understand how this works now.
-
@elliopitas
As I mentioned with the additional outbound NAT rule you do NAT (masquerading) twice on packets from your LAN to home LAN. Once on your pfSense when packets are going into the VPN interface (packets get 10.8.0.2 as source) and a second time on the Ubuntu when packets are going out to the home LAN (packets get the home LAN IP of Ubuntu).but my home lan still doesn't have access to my local lan
You didn't mention before that this is also desired, even if I asked for it.
This is more complicated, since the VPN endpoint is not the default gateway in the home LAN.
I assume the home LAN router is not capable to manage multiple network segments. If that's true you will need a static route for your LAN pointing to the Ubuntu server on each device which you want to have access to your LAN. -
This post is deleted! -
I'm going to make the assumption that HOME is an interface that you assigned to the VPN client. In pfSense, traffic applies to the interface where the traffic arrives. So in this case, on HOME you need to allow traffic from source 192.168.0.0/24, but instead you have source as LAN net. LAN net will never be the source for traffic arriving at that interface.