VLAN won't communicate with LAN
-
@djjoakim please upload images to the forum so other users do not need to go to other sites and can see the images in context.
-
And exactly as I stated your policy routing - forcing traffic out a gateway - so why would you think you would be able to get to your other networks.
https://docs.netgate.com/pfsense/en/latest/multiwan/policy-route.html#bypassing-policy-routing
-
@johnpoz Well like i said in the beginning, i am new to this - and i don't really understand what policy routing means, but i see now what you mean. The only problem is, the devices connected to that vlan must go trough the vpn client, i can't let the ip slip into the other wan, so i must force it.
Anyway, that's another problem - the thing is, like i said in the first thread, i have tried 1000 different options but nothing works, i have also tried to not force the gateway.Can you explain why these 2 networks can't communicate?
LAN is 192.168.1.1 and WIFI is 10.0.0.1 - not forcing anything.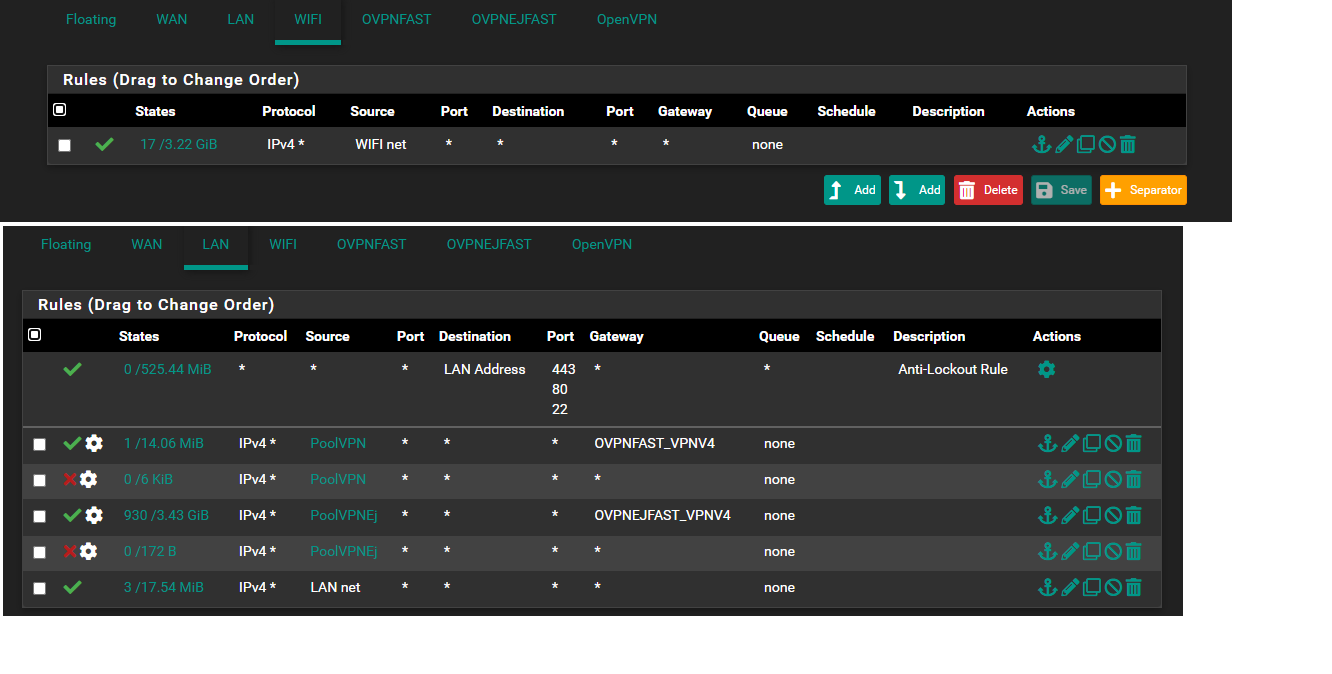
-
I have done exacly like that link you sent me, and still - they won't communicate... What am i doing wrong?
-
I'll just ask some questions, sometimes answering , forces one to rethink a solution.
1:
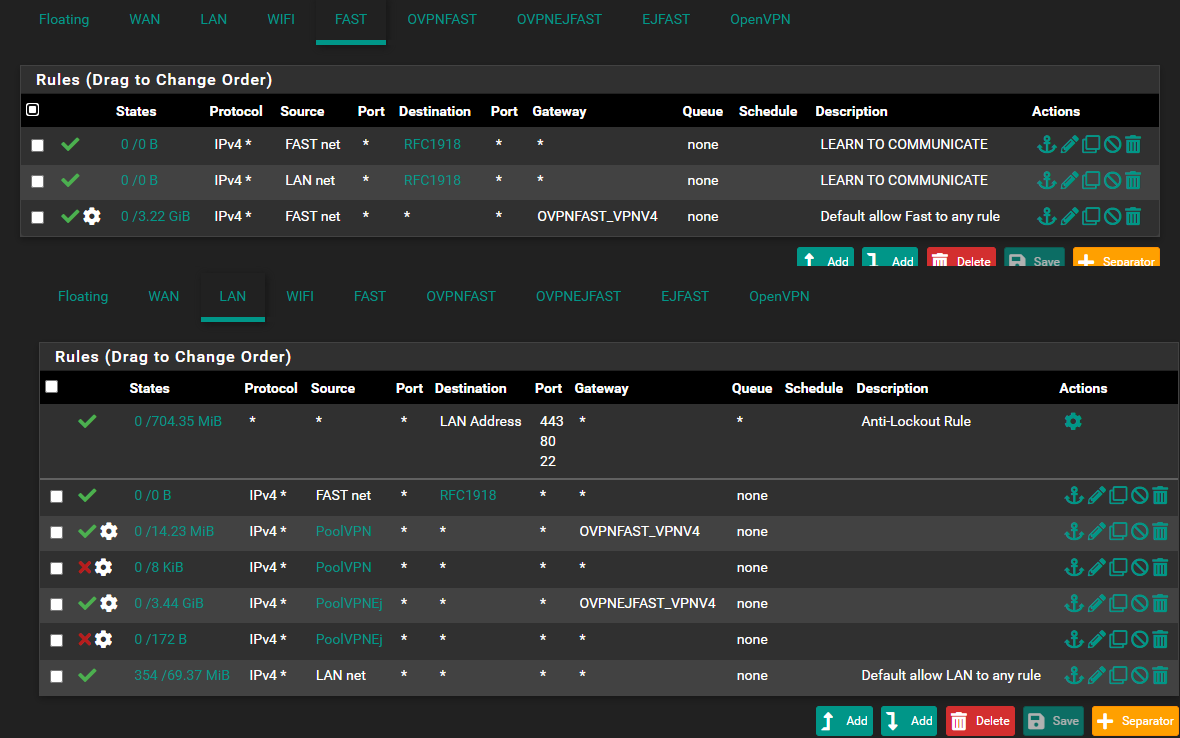
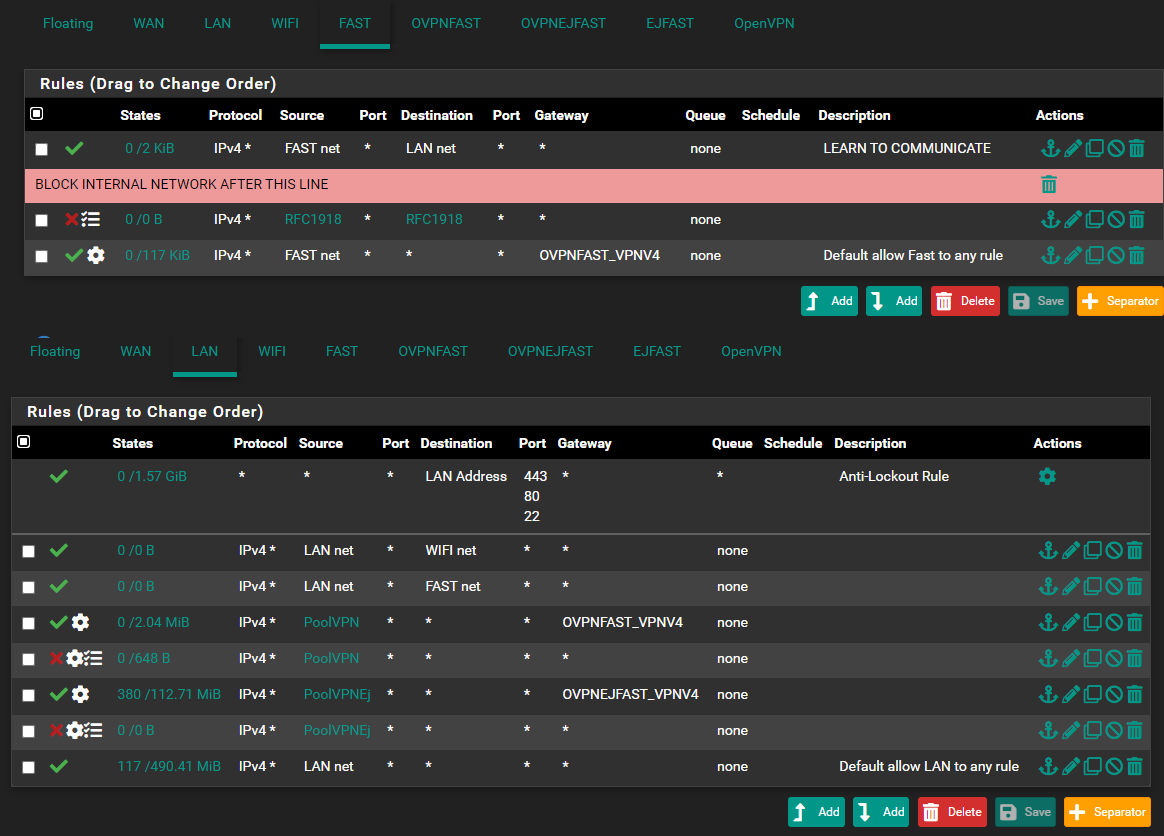
On FastLan - Why do you have a rule with source Lan net ?
Seems strange to me2:
On Lan - Why do you have a rule with source Fast net ?
Seems strange to me3:
The deny's on Lan (small arrows) , why do they have the "Gear wheel" , that's usualy just shown if you do some "trickery's" as setting "Gateway"
What have you set ? , show the config .
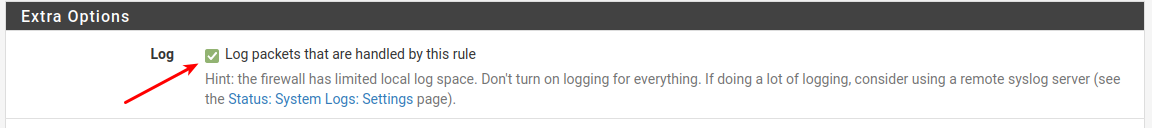
It is always adviceable (at least when debugging) to enable logging on all deny's including these.4: Please show the definition of those POOLVPN and POOLVPNEJ
/Bingo
-
@bingo600 Hey!
Thanks for you'r questions and for taking the time to help me.
First and all, i am very new to this - so everything dosen't make sense for now, and i have a friend that is trying to help me, so he has done some of the rules.-
I am just trying every possible way to make it work, so even if it seems strange, i open up to every possible way for the networks to communicate.
-
Same here as the above, i am trying to open up every possible senario to make the networks communicate.
-
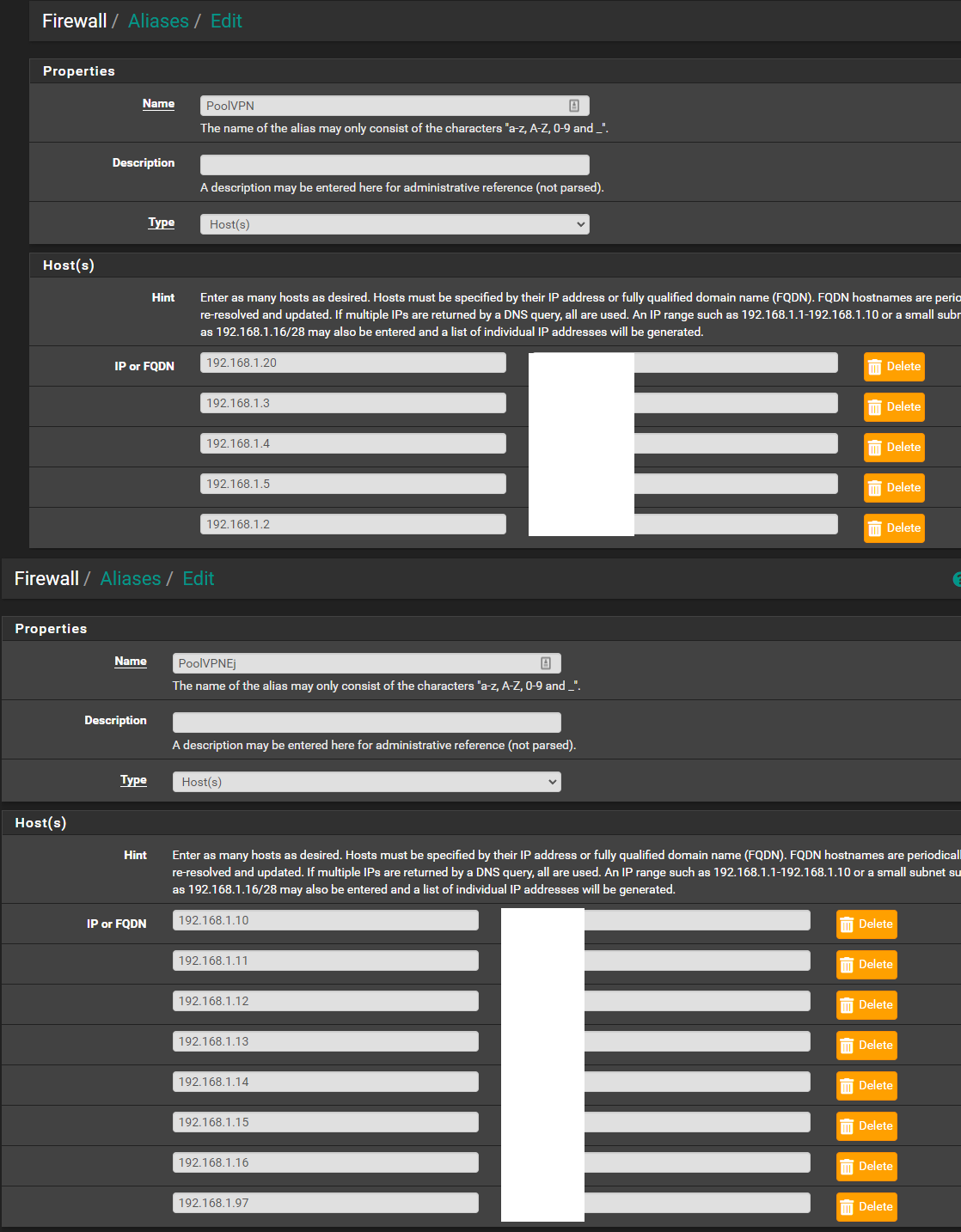
The PoolVPN is something my friend helped me set up, as for now - the VLAN don't work since they cant communicate, so everything on my network runs on LAN (192.168.1.x) and to make those devices not access internet except they go through the vpn client, he did that PoolVPN thing. The reason it's a gear wheel is becouse he added some tag, to make the network block if the devices somehow don't go through vpn client, here is the settings for PoolVPN and the meaing of that "gear wheel"
How can i enable logging?
And here is what's behind "PoolVPN"
Thanks
-
-
-
@bingo600 Thank you, will do.
-
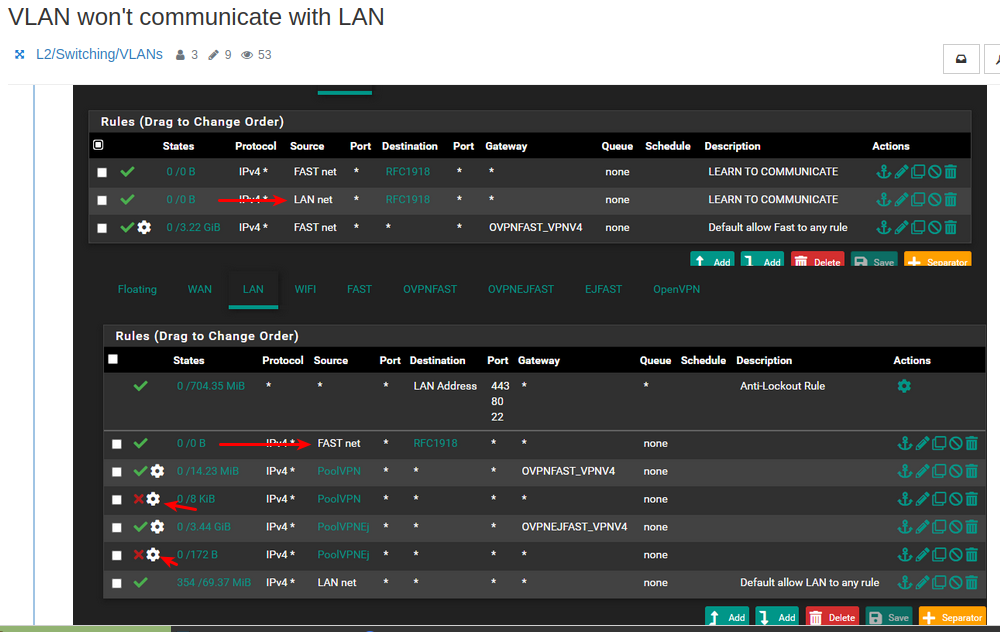
Let's take LAN
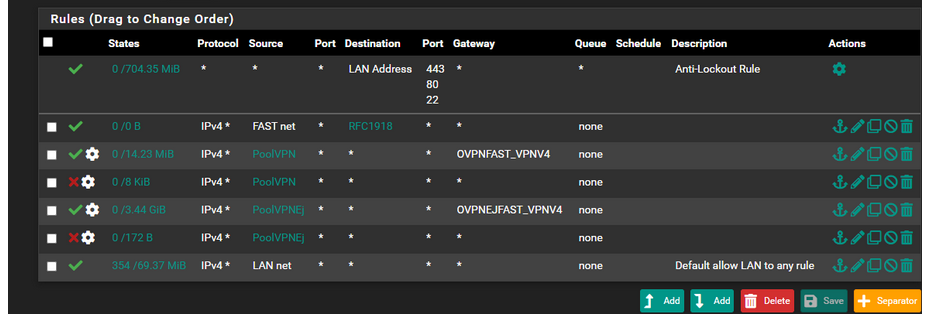
Disable the Top rule by clicking the "No parking icon" , it wont delete the rule just disable it.
You can enable it again by clicking the "ok" icon that will be shown instead of the "no parking".
What happens here after first rule is disabled....
Is that ANY ip in either of the VPNxx lists will be "Policy routed" aka "Forced out of" the gateway the rule points to. The "Deny rule below" is tagging the packet , prob. so that : If the VPN Gateway (above) goes down , the tagged package is not allowed to exit via normal wan.If the IP is NOT in those VPN lists the package is allowed to go "anywere" including to wifi or exit via wan.
This means that ANY IP in those lists will not be able to go to wifi , as they match the "Exit via VPN policy" before they hit the bottom allow lan to anywhere rule.
Do you (from a wifi unit) test or ping a device on Lan that is not on the POOL lists ??
Else you will never get an ansver.If what you wanted was to allow anything on lan to be able to talk to units on wifi (all local RFC1918 IP's) , and still have those in the pool exit via vpn's.
You should reenable the top rule , but change it's source to Lan net .
You will hopefully never see a source ip of Fast Lan , on your Lan.
So that rule won't do much good on lan ... aka never match./Bingo
-
@bingo600 Thank you for taking the time, the thing is - the PoolVPN only exist for now since my VLAN don't work as they should. And yes, the devices are now on LAN network, 192.168.1.x, so just like you said, all those that are in the PoolVPN is allowed except they don't go though the wrong wan exit, and then they are banned - that works fine, but that's not what i am after.
The devices that now are in PoolVPN and PoolVPNEJ is going to the Vlan. The devices in PoolVPN is going to VLAN30 = 172.18.0.1 (FAST) and the devices on PoolVPNEJ is going to VLAN40 = 172.19.0.1 (EJFAST)So they should not be botherd by the PoolVPN rule since they don't belong in that Aliases. So the question still remains, why does the devices on FAST access internet but i can't access them from my LAN network..
Thanks
-
@djjoakim said in VLAN won't communicate with LAN:
in that Aliases. So the question still remains, why does the devices on FAST access internet but i can't access them from my LAN network..Now you are changing the goal ....
You mentioned Lan to WiFi ... Does that work.I think you need to describe what it is you want to end up with , not strange "quirks" you have made because , you couldn't get it to work.
Edit: And what does go to 172.18.0.1 mean ???
Should they get policy routed to 172.18.0.1 ?
Should they "just" be allowed to communicate with 172.18.0.1 or ??Back in my IBM Mainframe days IBM's APAR Team would the pressed the (in)Famous - More Documentation is required ... button , in a situation like this
-
@bingo600 No, i am not changing the goal - this is exacly what i was trying to explain in my main post, i only used the WIFI example for johnpoz response, since the wifi wasn't forced out of any gateway. (Since he said the problem was becouse of that on FAST interface)
Anyway, i am sorry for the confusion - not having english as my first language sometimes makes everything 10x harder aswell. I will try and explain exacly what's my plan is:
(Ignore all that PoolVPN for now, since that's "quirks")I have 3 VLAN networks.
VLAN30 (FAST) 172.18.0.1
VLAN40 (EJFAST) 172.19.0.1
VLAN60 (WIFI) 10.0.0.1And then there is my LAN network 192.168.1.1
So all devices placed under VLAN30 and VLAN40 must be forced through different VPN Clients, they can not leak into my orignal WAN.
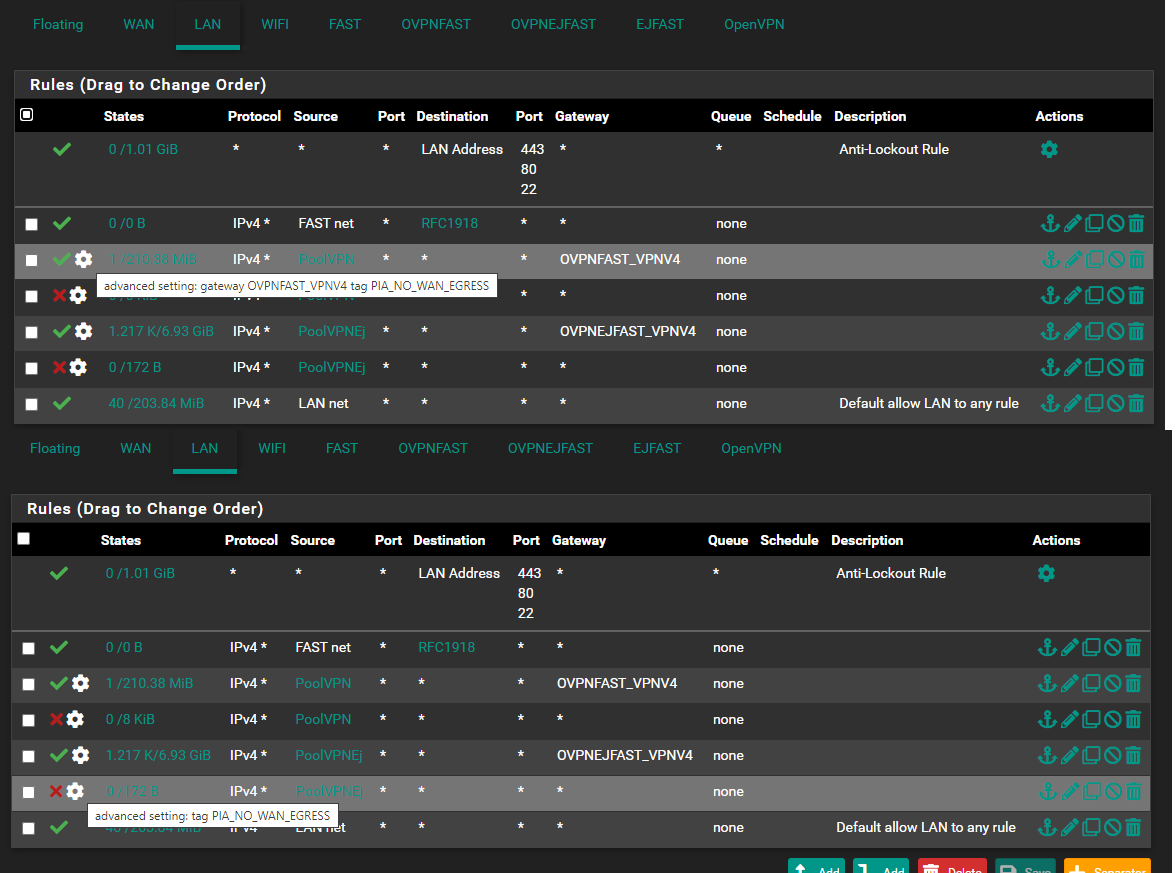
Everything so far seems to work, all devices i place under VLAN30 can access internet fine, but i can't access them thought my PC that's placed in LAN.
(Some devices that will be in VLAN30 have webui witch i need to access from my PC, that's why i need to access some of the IP adresses)Now, when i have changed some of the settings (see pic below) i can ping my PC (192.168.1.103) from one device on FAST (172.18.0.124), but i can't ping 172.18.0.124 from my pc (192.168.1.103).
So somehow, i managed to get it working one way, but not the other way back.. And i can't figure out what i have done wrong.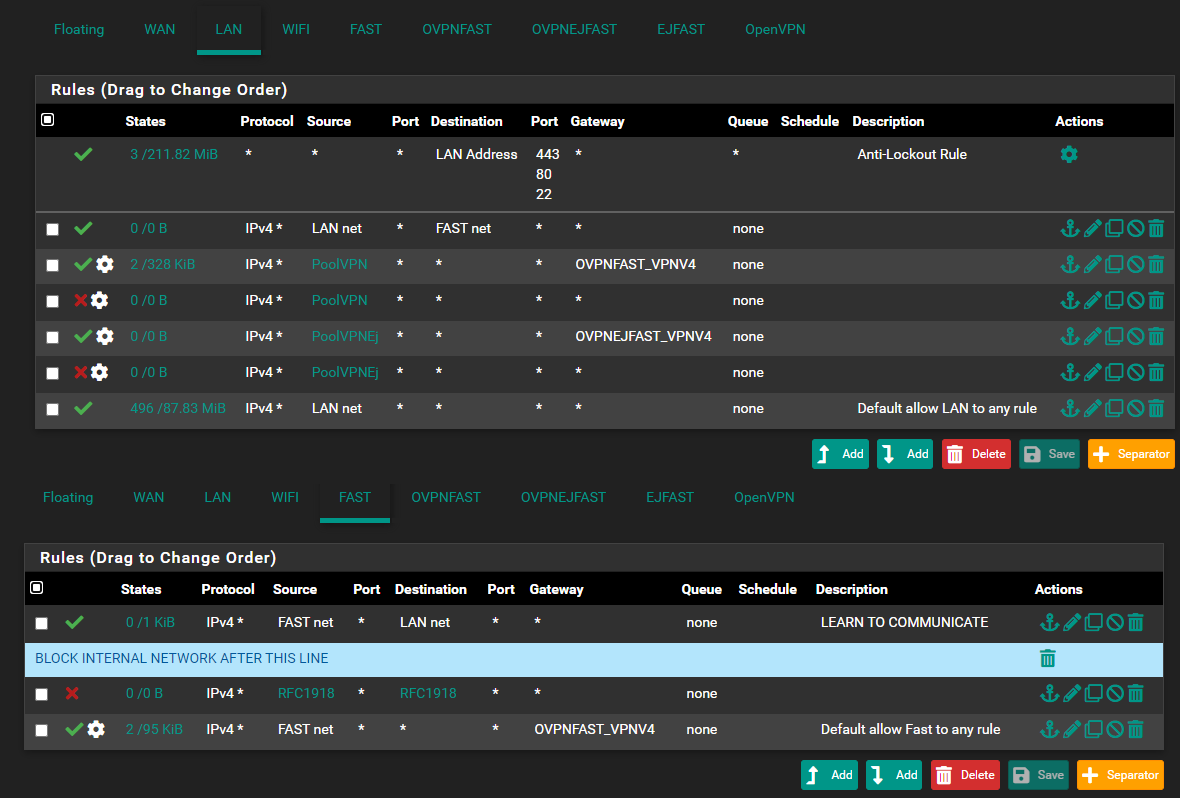
Thanks
-
The config you showed above , ought to work for LAN <--> FAST.
Have you tried to reboot the firewall , or "Clear the states" ?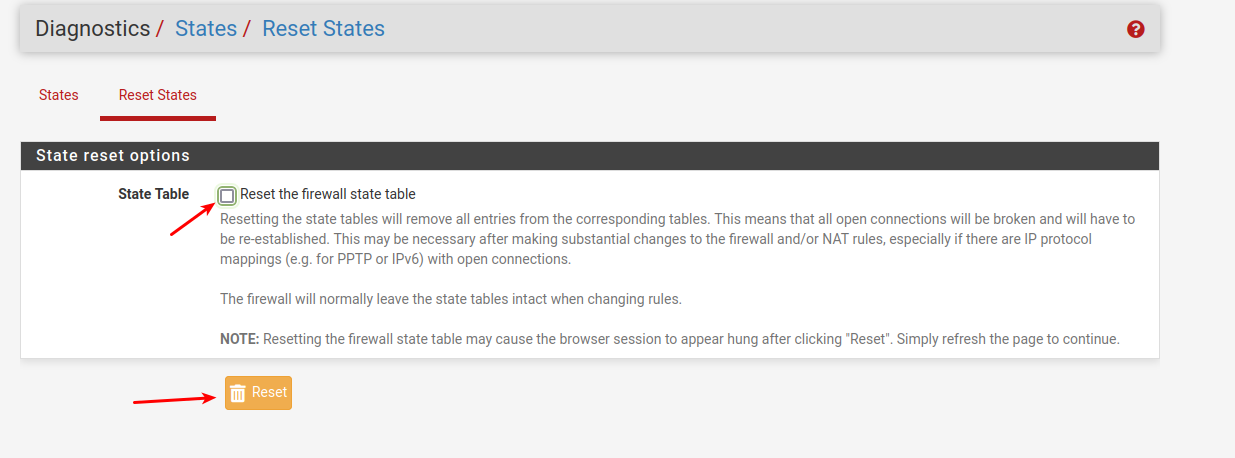
And it seems you haven't enabled loggong on all the "deny" lines , that can be super helpfull during debugging an issue like this.
-
@bingo600 Yes i just did that, and still dosen't work..
I have also tried to make the same rules for WIFI, just to be sure there was nothing wrong with the device on FAST that i tried to ping, but the problem remains - i can ping LAN but i can't ping the VLAN..
Edit: Hmmm.. Now i can access FAST from WIFI (VLAN60), but i can't reach WIFI from FAST, So, in this equation the problem is on the other way.
LAN - FAST Can't ping
FAST - LAN Can ping
FAST - WIFI Can't ping
WIFI - FAST Can pingSorry, i have now enabled the logging for those.
Thanks
-
What can you ping from Lan (your 192.168.1.103)
Can you ping 192.168.1.1
Can you ping 10.0.0.1
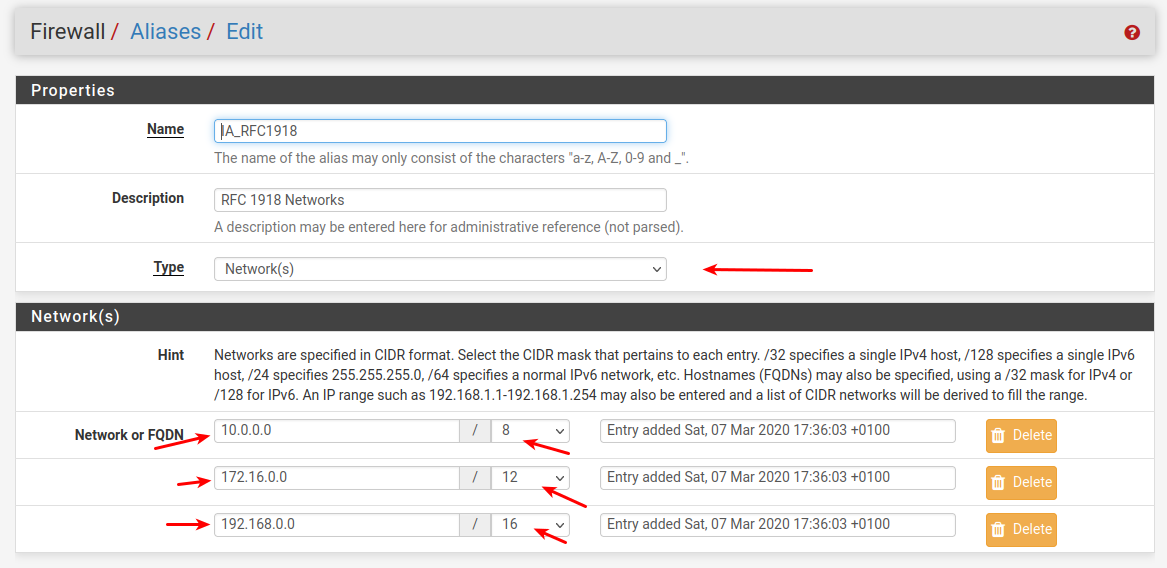
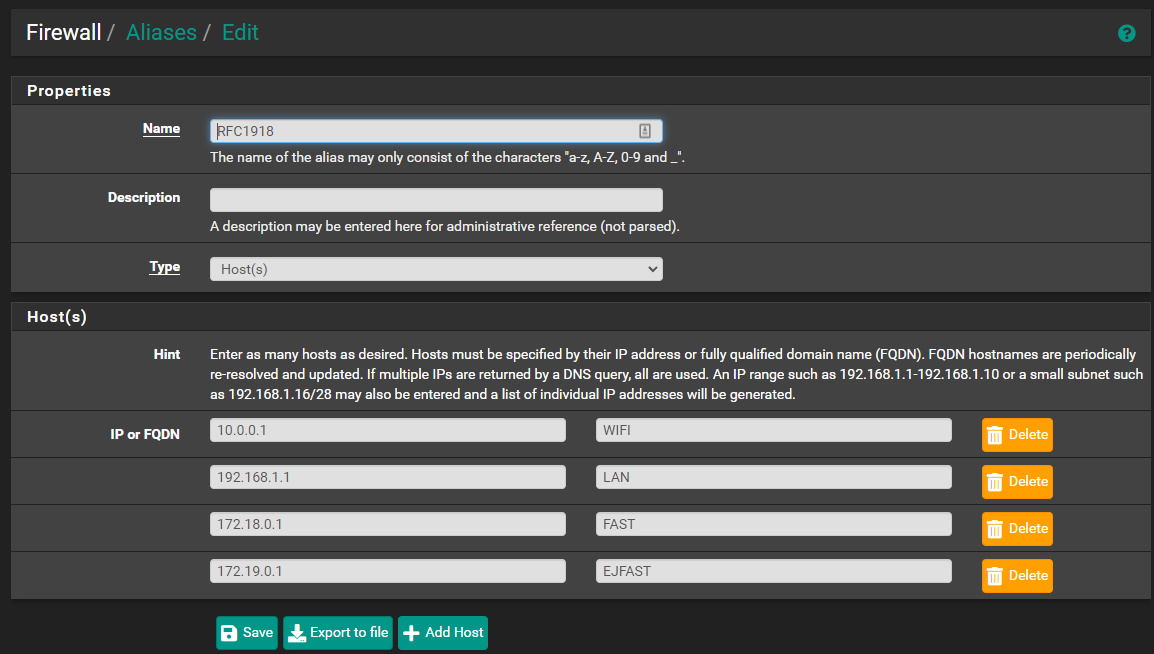
Can you ping 172.18.0.1How does your RFC1918 definition look
/Bingo
-
@bingo600 Hmm, strange.
I did an edit on my last post, i tried to "reduce" the issue so i tried the same thing on my other vlan, WIFI. And when i did that, the problem is on the other way. From WIFI i can reach FAST, but from FAST i can't reach WIFI, something is really strange here.To answer you'r question, from my PC (LAN) i can only ping 192.168.1.1, it dosen't respond on anything else. (While on my WIFI, i can ping 172.18.0.1, 172.19.0.1, 192.168.1.1, and the same on FAST)
Sorry, i am not trying to confuse the situation by starting to talk about the WIFI vlan, i just think it's strange that the problem is on the other way around there.Anyways, here is my RFC1918
-
Hmm okey, well - forget about that WIFI connection, i used my brain and figured out that it probably had something with windows firewall to do, said and done - when i turn off the firewall on that WIFI device, i can reach it from FAST - so clearly it was something wrong at that side.
So, since everything works with the firewall settings in that VLAN, it seems like there is something really wrong with my LAN, and maybe not PFsense fault... -
-
@bingo600 I followed this "guide" https://docs.netgate.com/pfsense/en/latest/multiwan/policy-route.html#bypassing-policy-routing
Isn't it how i should do it?
-
@bingo600 Ooops.. Well, fixed now