DMZ 1 firewall vs DMZ 2 cascaded firewalls
-
Hello Everyone,
I'm thinking how to implement DMZ (exposed) network + Private LAN on same firewall, or with 2 different firewalls. (we are talking hardware pfsense).
DMZ usage will be some app servers, ftp servers, web servers, and some site to site vpn tunnels.I'm aware that in theory we can set rules on DMZ interface and LAN interface to have appropriate security and isolation, but i wanted to ask if there is any difference on implementation when 2 cascaded firewalls are used.
Does pfSense treat all interfaces the same ? What's the technical difference between WAN and LAN interfaces? WAN has all blocked by default, LAN has anti-lockout rule and allow all rule on LAN by default. It seems to me that some operations are not the same between WAN and LAN, so i'm wondering if there is any benefit of having the 2nd configuration setup.
Please see diagram below. All comments and suggestions appreciated.
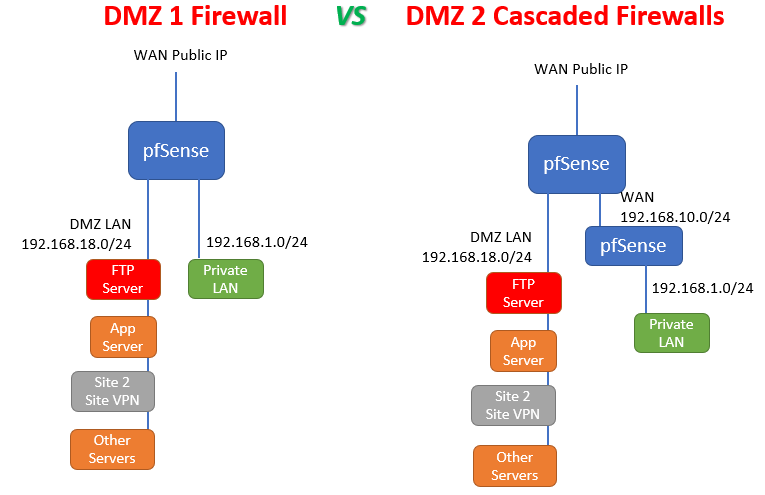
-
Hi there,
sorry for my poor language skills...I am not a Pro-user of pfsense, just doing it in my little home lab, so be advised.
IMHO what you would get by your cascading scenario is quite a bit more struggle with the configuration, extra costs (hardware, energy, time) and no real advantage.
Since your two networks (dnz / lan) are on two different interfaces, traffic is securely seperated afaik. You would need to implement rules to allow inter-network traffic (which you dont want, if i get you correctly).
So stick with the left szenario is what I would suggest. -
No needs to cascade firewalls. A proper isolation is obtained by rules. That's what firewalls are used and designed for.
-
thanks @psp @the-other
i expect a 6 port device to arrive for configuration.