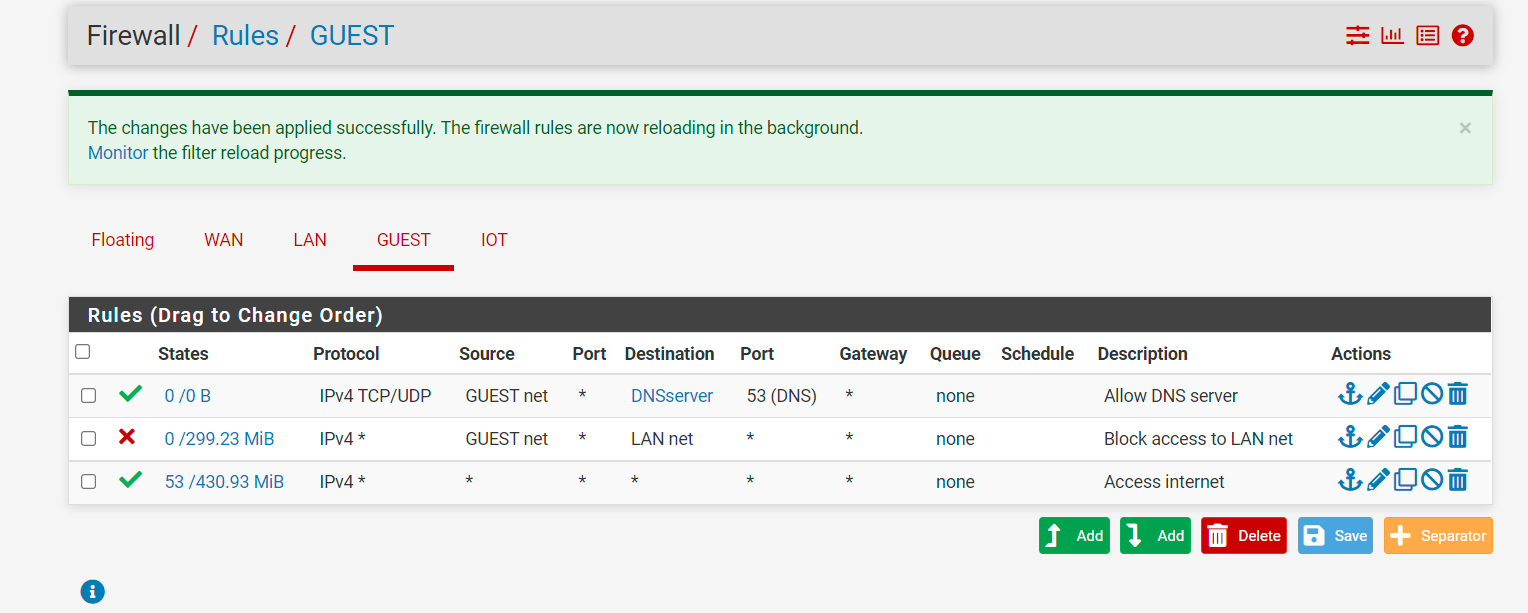
No internet access to VLAN when isolating it with LAN net
-
@johnpoz I randomly selected 120.168.10 for my VLAN. It is inside my network so thought it would not be a problem. May be I can change later if that creates issue.
Regarding the DNS, yes I have adguard running in 192.168.10.9:53. I initially guessed so and created allow from GUEST net to that specific IP and port, but that also didn't help. this is what I was doing.
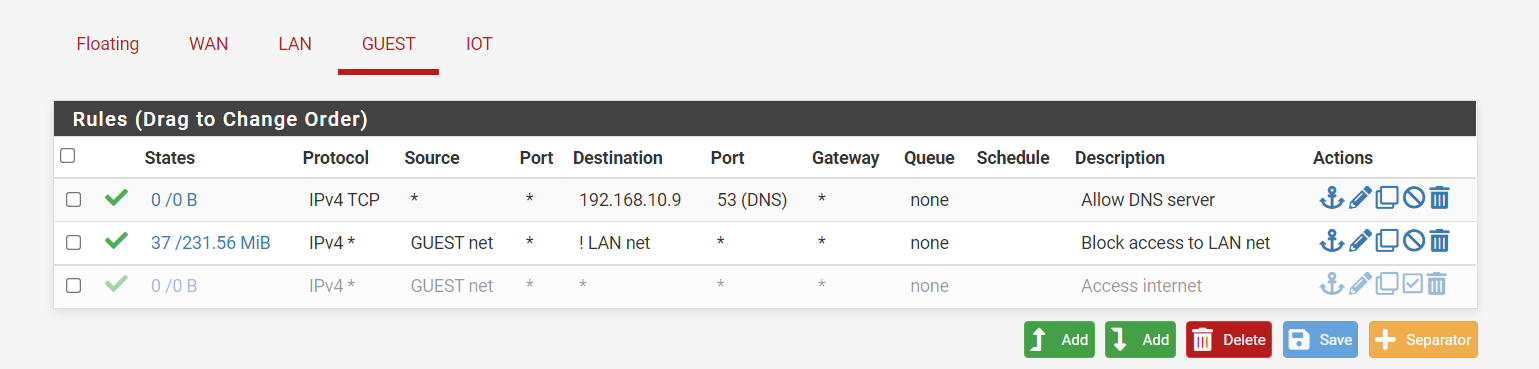
I am testing different ways to create firewall rules. The invert should be same as before (I guess), and added DNS as first rule so that I have access to DNS server.
I also tried IP address of google directly (142.250.114.102) in the computer with guest network and that also did not work.
May be I am not correctly creating rules? or can it be because of the IP I am assigning? -
@062bel313 said in No internet access to VLAN when isolating it with LAN net:
May be I can change later if that creates issue.
It is really bad practice to just use public space internally - while technically it can work.. If you ever wanted to actually go to a public site hosted off that public network you would not be able to get there.
You should use the more than adequate amount of space specifically assigned for use on local network, ie rfc1918..
If your dns is on 192.168.10.9 - maybe it doesn't allow access from what it feels is public IP space..
I would not use ! rules, unless there is some specific reason for it. Rules are evaluated top down, first rule to trigger wins, no other rules are evaluated.
Your first set of rule were fine - depending on where your client on your guest was pointing to for dns..
I would correct your guest network to be rfc1918, and then can work on whatever problem your having. But I can tell you right now anyone looking to helping you and seeing your use of public space internally that is not actually assigned for you to use is going to point it out as problematic.. There is ZERO reason to just use random public IP space internally..
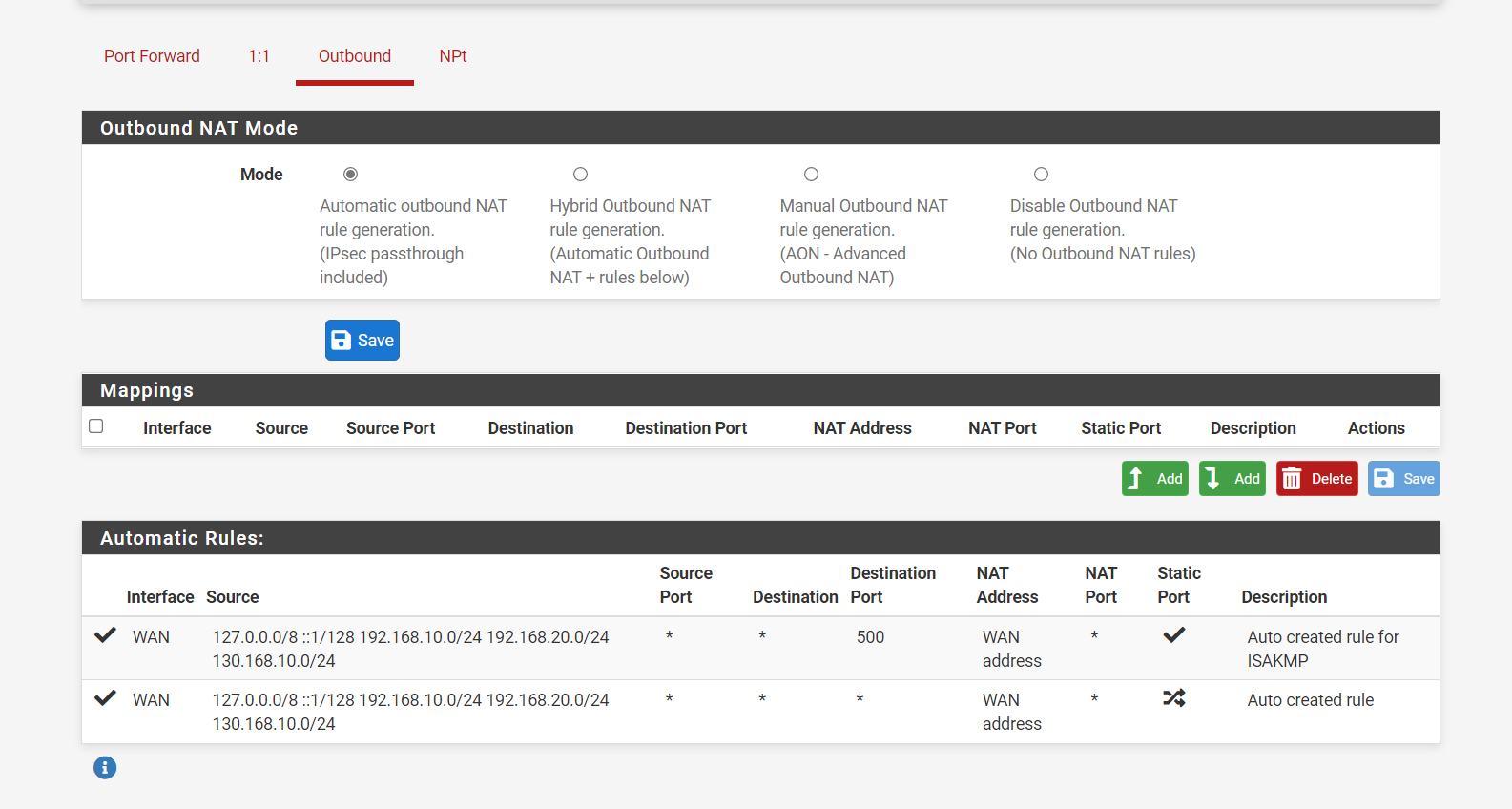
did you mess with the default outbound automatic setup? Out of the box pfsense will auto nat any new local networks you create vlan or native to your wan IP. If you changed this from auto, you would have to manually create the outbound nat rules?
Do you have any floating rules that could be blocking this guest network from going out your wan?
-
@johnpoz Got it,
my taks:
I will change the IP address of my VLAN to 192.168.20.0/24
Then use 1.1.1.1 as DNS server
Will revert back the firewall rule as before and update the thread (if it works, and if it doesn't work)
I will also create guest network as rfc1918 (no idea how to do that, but google should help on it :-)) -
@062bel313 said in No internet access to VLAN when isolating it with LAN net:
I will also create guest network as rfc1918
Just pick some address space out of that VAST amount of space, 192.168.20/24 for example - anything in rfc1918 space will work just fine, as long as it doesn't overlap with your existing lan or other networks, etc.
-
Just for easy reading I use a 10. addresses for things outside my LAN.
-
did you mess with the default outbound automatic setup? Out of the box pfsense will auto nat any new local networks you create vlan or native to your wan IP. If you changed this from auto, you would have to manually create the outbound nat rules?
I have not changed anything on NAT side. This is what I see after I changed my guest network to 192.168.20.0/24:
Do you have any floating rules that could be blocking this guest network from going out your wan?
My floating rules are blank.
If I use 1.1.1.1 as DNS server, GUEST network has internet access, but if I changed it to 192.168.10.9, I do not have access to internet. So I guess the problem is with my DNS server running on the LAN net. I set up my firewall rule as this, is it correct?
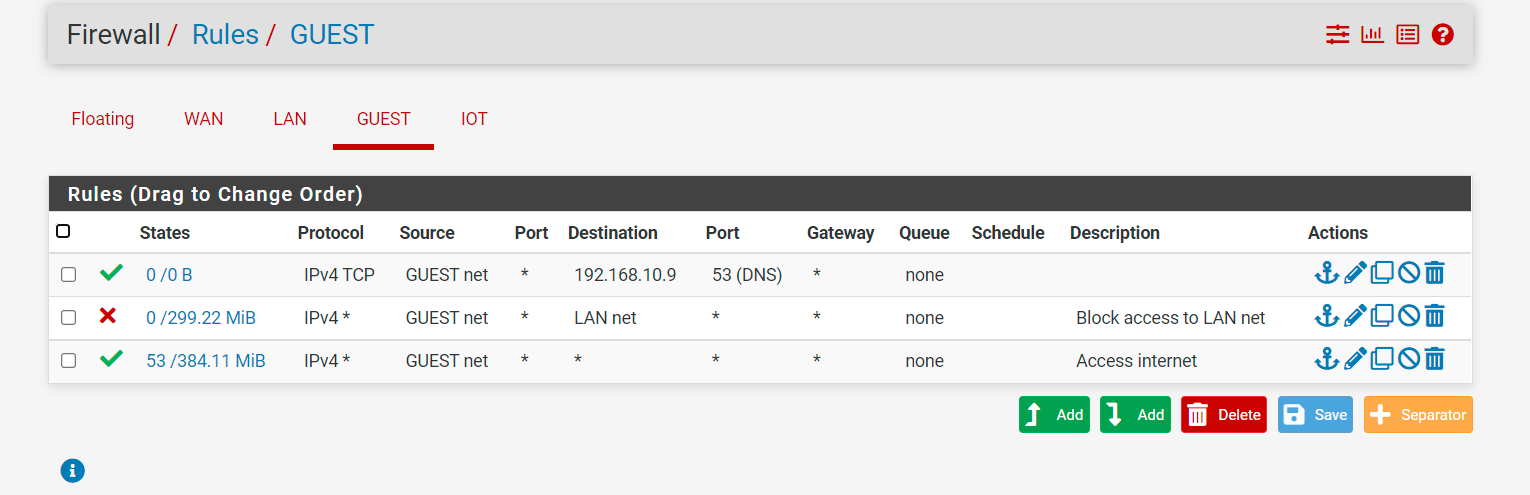
-
-
@062bel313 and what are you running on your 10.9 for dns - its firewall rules might not allow your vlan network? Or like unbound with ACLs, or Bind also has ACLs, etc. which need to be set to allow for queries, etc.
Also you should prob fix up that 130.168 network while your fixing stuff..
NetRange: 130.168.0.0 - 130.168.255.255 CIDR: 130.168.0.0/16 Organization: Agilent Technologies (AGILEN-2)I didn't catch the tcp only rule - because focus was on your NON rfc1918 network ;) hehehe
-
@johnpoz Agree: I have to change that 130. 168 VLAN. I have changed it. Now every thing is working as expected. I am using Adguard as DNS server, not sure about your questions on ACLs, no idea hehehe.
Thank you all.
-
@062bel313 said in No internet access to VLAN when isolating it with LAN net:
not sure about your questions on ACLs, no idea hehehe.
What are you running for dns on 10.9? Different dns software has a feature of Access Control Lists which determine what IPs or IP ranges can do different types of queries..
Unbound and Bind both support this feature for example. Unbound running on pfsense out of the box will auto create ACL entries for locally attached networks, etc.
Here is bind package for example
So depending on what dns you running on 10.9 - it would be possible that you would have to edit whatever ACLs to allow for queries from your other network/vlans