How to set the same VLANs between the switch and PfSense
-
@johnpoz said in How to set the same VLANs between the switch and PfSense:
@jt40 your still using shit /16 mask.. WHY???
The error message says: the IP is out of range, that's it.
What says that?? If you set an IP of 192.168.140/24 and try and point it to a gateway of 192.168.0.1 then yeah that is out of range because its not in the 192.168.140 network.
Dude change the mask on your router to 255.255.255.0 - there is no possible way have 65k some clients needed on this network.. Why would you think in any way that a /16 makes any sense??
If you want to use 192.168.140/24 as pfsense - then set your router to 192.168.140.1 and pfsense to 192.168.140.2 both with /24 or 255.255.255.0 masks.
No, it fails when I simply try to reserve the address, I need to reserve it because I can't have DHCP for the Pfsense Uplink.
I don't understand why it's wrong, CIDR looks correct to me.I could change the mask to 255.255.255.0, but then I would not be able to change the range in this way 192.168.x.x, am I wrong?
Or you are telling me that for the uplink is not necessary to be outside of that range? Basically 192.168.0.5 would be just fine for you?Just a note, the rest of the PfSense interfaces can't be on that range, so can I set them to 10.x.x.x like the switch?
-
@jt40 said in How to set the same VLANs between the switch and PfSense:
No, it fails when I simply try to reserve the address
Show us..
-
@jt40 I am still a bit confused but it sounds like you're unclear on how subnet masks work. In the simplest explanation, "255" means "this part of the address must match." So 192.168.0.0 with 255.255.0.0 (a /16) means "any address that starts with '192.168' is on this interface."
You can use 192.168.0.0/16 on one interface but then can't use any 192.168.x.x addresses on any other interfaces. Or, you can use 192.168.1.x with a 255.255.255.0 (/24) mask on one, 192.168.2.x on another, etc.
If you expect less than 254 devices on a network then it's fine to use 255.255.255.0 on that interface/network. You can use a larger subnet, but it's not necessary.
-
@steveits Im also a bit confused on "where" he is trying to set what.. Is he trying to set it on the isp device?
If he trying to set it on wan, then yeah 192.168.140/16 is going to overlap if he has any 192.168 on pfsense other interfaces.
And it could even overlap with 192.168.140/24 on wan if he has some /16 on other pfsense interface. He has some management interface he set to something in 192.168
edit: But pfsense shouldn't say out of range - it would say overlap and should show you what is overlapping. Here I just tried to change one of my test interfaces to a /16 mask
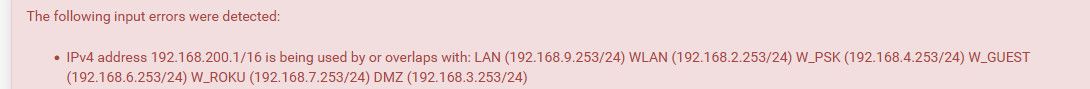
-
@johnpoz said in How to set the same VLANs between the switch and PfSense:
@jt40 said in How to set the same VLANs between the switch and PfSense:
No, it fails when I simply try to reserve the address
Show us..
What do I need to show?
I mean, I'm not idiot till that point :D , this is what I receive from that UI...I discovered something though, look at this example:
192.168.80.5 (out of range)
192.168.80.1 (ok)I think that the address I assigned to the Pfsense management interface interfers with the rest of the modem/router config. (192.168.200.1)
I unplagged it from the modem/router, same result though, I was expecting a difference here but since the address is reserved in the modem/router, I think it's the same for this reason...Changing the mask to 255.255.255.0 on the modem/router and removing the previous assignments, my previous connection running on 192.168.5.1 still works.
This was my doubt, I was pretty sure that the subnet mask mentioned by you would have cut off that connection, but it didn't happen.Look at the fun again:
Mask: 255.255.255.0
192.168.0.220 (ok)
192.168.1.50 (out of range)
192.168.50.50 (out of range)Based on what I get here, the connection on 192.168.5.1 should have been stopped, but it didn't.
Coming back to the dumb approach, I can assign ~192.168.0.200 in the modem/router, + to the PfSense uplink interface (same IP).
Then I assign something like 192.168.0.199 to the management interface of PfSense (instead of 192.168.200.1), or from now on I should only use 10.10.x.x on the other PfSense interfaces?
-
@jt40 where are you setting that?? On the isp device?
I want to see the actual error from the page your setting on it - so I have a clue to if your doing it on pfsense or your isp device, etc.
Is it telling you your dhcp is out of range for the network your setting..
192.168.1.50 255.255.255.0 is not out of range - out of range of what? The dhcp server that is set to 192.168.0.x -- y?
my previous connection running on 192.168.5.1 still works.
Works to where? Have no idea where this is set, or if its a wan or lan on a router?
Then I assign something like 192.168.0.199
With what mask? Where are you setting that on pfsense, some other device.. Show us all of the interfaces you have set on pfsense.
here are mine.. all /24 other than the ipv6 address which are /64 and the public IP space is dhcp from my isp and has a /21 on it.. And my vpn 172 also has a /21 on it.. 255.255.248.0
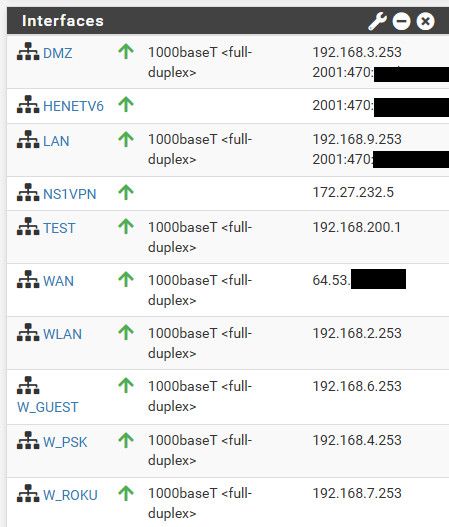
-
I thought that this was clear, but ok it happens, sorry.
In the last ~10 messages I've been talking about the modem/router only, the ISP device in other terms.
In correspondence to the IPs I mentioned previously, it says that the IP is not in range, that's the exact message I get, not the DHCP or any other component.
my previous connection running on 192.168.5.1 still works.It's currently set on another router after the modem/router, but it's not reserved in the modem/router, I think that it's supposed to work even if not reserved, maybe it's just that :D .
Previously with a mask of 255.255.0.0, now is 255.255.255.0 it works fine but in the same time I'm not able to reserve a similar address, which makes it suspicious.Forget about the PfSense interfaces for now, I still need to get sorted one of them as uplink, until now without success. I mean, I've set it up and PfSense was able to ping Google, but I wasn't able to join the network with a laptop for example, even the gateway was unreachable... Which seems to be the most stupid issue but that's how it is.
The next question would be how to set the other interfaces and get at least one VLAN working with a single device using it (laptop), excluding the switch in the end, that will be the last step.
Anyway, thanks for the immense help so far.
-
@jt40 said in How to set the same VLANs between the switch and PfSense:
It's currently set on another router after the modem/router, but it's not reserved in the modem/router
what the F dude.. How many freaking routers/modems do you have
This isp device that was set to 192.168.0.1 - what is on its WAN??
From your drawing 192.168.140 is LAN of some router.. And its wan is 192.168.0.1 that isn't going to work because they would overlap if using /16
The device upstream of pfsense has what for its WAN IP and its LAN IP?? What are the masks of these interfaces?
This device
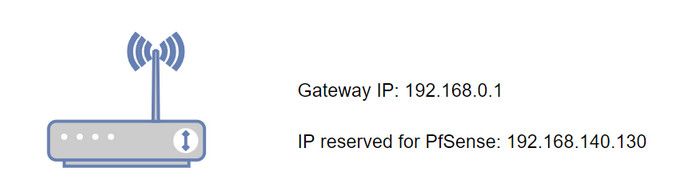
What is it - make and model.. Is this the sky box? WHAT do you have set on its wan - that makes no sense at all that its wan would be 192.168.0.1 - its wan would be what connects you to the internet if the gateway device from your ISP.
Or was it using 192.168/16 and your were trying to get pfsense to talk to 192.168.0.1 from 192.168.140 using a /16?
On this device it has 2 interface - public or internet facing - upstream connection. And downstream or lan where you connect pfsense. What are the 2 networks on this device, is its wan public?? Or cgnat 100.64/10 - what is it? Is it also in the 192.168 range - if so what mask?
-
@johnpoz said in How to set the same VLANs between the switch and PfSense:
what is on its WAN??
192.168.0.1 is the sky modem/router connected to the WAN, what it could be otherwise? :D
Or was it using 192.168/16 and your were trying to get pfsense to talk to 192.168.0.1 from 192.168.140 using a /16?Exactly, that's what I was trying...
Having said that, instead of explaining what I did before, let's go ahead with the setup.
Now it's the turn of PfSense, from where do I start?I watched interesting videos, like this one, I think that if I stick to addresses like 192.168.0.8 it won't create any problem for the uplink, but what about the rest of the interfaces on PfSense?
What about the switch in the end? (after PFSense)
They should have same VLAN, but I'm a bit confused about the IP range here.The whole point of messing around with different IP ranges is because I want every interface on different networks for security reasons...
Beyond that I would have one VLAN for each purpose, that was my crazy idea :D -
@jt40 said in How to set the same VLANs between the switch and PfSense:
192.168.0.1 is the sky modem/router connected to the WAN, what it could be otherwise? :D
OMG dude.. any router has to have at least 2 interfaces - or it can not route.. If that is the LAN IP of this device then change it.. But it could be giving you an error depending on what IP is on its WAN..
Exactly, that's what I was trying...
Not going to work if 192.168.0.1 is not on the same network is 192.168.140 - so it would work with a /16 but not with something like /24
I gave you a drawing with 192.168.0 being on pfsense WAN - connected to your device with lan of 192.168.0.1
And then use something else on pfsense lan 192.168.2/24 for example.
For your switch and other vlans - use whatever ranges you want, as long as they do not overlap with what is on pfsense
-
@johnpoz said in How to set the same VLANs between the switch and PfSense:
@jt40 said in How to set the same VLANs between the switch and PfSense:
192.168.0.1 is the sky modem/router connected to the WAN, what it could be otherwise? :D
OMG dude.. any router has to have at least 2 interfaces - or it can not route.. If that is the LAN IP of this device then change it.. But it could be giving you an error depending on what IP is on its WAN..
Exactly, that's what I was trying...
Not going to work if 192.168.0.1 is not on the same network is 192.168.140 - so it would work with a /16 but not with something like /24
I gave you a drawing with 192.168.0 being on pfsense WAN - connected to your device with lan of 192.168.0.1
And then use something else on pfsense lan 192.168.2/24 for example.
For your switch and other vlans - use whatever ranges you want, as long as they do not overlap with what is on pfsense
Of course the modem has the public IP assigned to its WAN (not sure if I can say it in this way), and then 192.168.0.1 on the private LAN, did I miss anything?
Yes, 2 different interfaces, 2 different IPs, same device.Regarding PfSense and the rest of the network, do you mean this draw?
https://forum.netgate.com/assets/uploads/files/1638718805697-doublenat.jpg
192.168.0.1 & 192.168.1.1 are 2 different networks if I'm not wrong... They would require a gateway for my knowledge, that's why since the beginning I was trying to create gateways.
Anyway, at least now I'm sure that between the modem/router and PfSense there should not be any gateway (just because PfSense prompts it :D ), but I don't know if it's a PfSense thing, or networking thing :D -
@jt40 said in How to set the same VLANs between the switch and PfSense:
192.168.0.1 & 192.168.1.1 are 2 different networks if I'm not wrong...
They are the same network if using a 255.255.0.0 mask. Different if 255.255.255.0.
-
Or also the same network if using /23 or 255.255.254.0
Going to again suggest you do a bit of research on what a mask actual is and how it works.
-
@steveits said in How to set the same VLANs between the switch and PfSense:
@jt40 said in How to set the same VLANs between the switch and PfSense:
192.168.0.1 & 192.168.1.1 are 2 different networks if I'm not wrong...
They are the same network if using a 255.255.0.0 mask. Different if 255.255.255.0.
I think I've been reasoning in the opposite way until now, I thought that if the mask was restricting that range, I was not able to use an IP outside of that range...
Basically, what you are saying is that with a mask of 255.255.255.0 I can still set up 192.168.5.1 and 192.168.9.1 networks?
The are not anymore different hosts as for example 192.168.9.3 vs 192.168.9.2 (random values), but they are officially different networks because the mask for the hosts is defined at a lower range, so called Class C.If all above is correct, then I can simply use a mask of 255.255.255.0 and set all the networks that I want on the range of 192.168.x.x, is it correct??
Or better, 10.10.x.x range.
This confuses me though: https://www.qsc.com/resource-files/productresources/dn/switch_configuration_examples/audio_video/d-link/q_dn_qsys_d-link_dgs_1210_1500_series_sce.pdf
(The network switch’s default IP address is 10.90.90.90 and subnet is 255.0.0.0. Make sure your computer’s NIC uses an IP address that
is within that subnet domain)How comes...
That IP works right as soon as I set something like 10.90.90.91 to access it, gateway 10.90.90.90 if I recall well.
I'm talking about direct access, no other node in the network before that.I was reading this: https://avinetworks.com/glossary/subnet-mask/ , but I can't get my head around the class 10 then... The way it appears, it seems to be a public IP range due to the mask (or the mask doesn't define the network private/public type??), whenever I'm pretty sure that is a private IP range, I use it a lot at work between machines on the same network, obviously attached to a gateway.
-
@jt40 said in How to set the same VLANs between the switch and PfSense:
https://avinetworks.com/glossary/subnet-mask/
from that
"The “255” address is always assigned to a broadcast address, and the “0” address is always assigned to a network address"Wow!! that is just plain wrong!
If I had a network 192.168.0.0/23 192.168.0.255/23 would be just a host address, and 192.168.1.0/23 would also just be a host address.
Why do they bring up Classes - network classes haven't been a thing since early 1990s..
If I used a mask of say /25 on 192.168.0.0 the broadcast would be 192.168.0.127 not .255, with that same mask the next network 192.168.0.128/25 would be the network..
Such a statement would only be valid for for specific mask that use up the whole octet, like /8 or /16 or /24 - again back to the class days, which hasn't been a thing for going on 30 years.
or the mask doesn't define the network private/public type?
The mask has nothing to do with the network being public or private. What makes it public or private is the address range used..
rfc1918 or private space is spelled out here
https://datatracker.ietf.org/doc/html/rfc191810.anything is a private space 10.0.0.0/8 which is the range 10.0.0.0 - 10.255.255.255, where yes .0 is the network or wire and 10.255.255.255 would be the broadcast. but say 10.90.90.0/8 would be just a host, and 10.0.0.255/8 also just a host..
This would prob be a better place to start
https://docs.netgate.com/pfsense/en/latest/network/addresses.html -
@jt40 said in How to set the same VLANs between the switch and PfSense:
with a mask of 255.255.255.0 I can still set up 192.168.5.1 and 192.168.9.1 networks
255.255.255.0 means "the first three numbers must match." So:
192.168.0.1 / 255.255.255.0
is in a different network than
192.168.1.1 / 255.255.255.0but
192.168.0.1 / 255.255.0.0
is in the same network as
192.168.1.1 / 255.255.0.0So the mask matters but they matter together.
So if you tell pfSense WAN to use 192.168.0.1 / 255.255.0.0 then it knows all those addresses are WAN. You can't also set up LAN as 192.168.5.1 / 255.255.255.0 unless you change the mask on WAN.
-
@johnpoz said in How to set the same VLANs between the switch and PfSense:
@jt40 said in How to set the same VLANs between the switch and PfSense:
https://avinetworks.com/glossary/subnet-mask/
from that
"The “255” address is always assigned to a broadcast address, and the “0” address is always assigned to a network address"Wow!! that is just plain wrong!
If I had a network 192.168.0.0/23 192.168.0.255/23 would be just a host address, and 192.168.1.0/23 would also just be a host address.
Why do they bring up Classes - network classes haven't been a thing since early 1990s..
If I used a mask of say /25 on 192.168.0.0 the broadcast would be 192.168.0.127 not .255, with that same mask the next network 192.168.0.128/25 would be the network..
Such a statement would only be valid for for specific mask that use up the whole octet, like /8 or /16 or /24 - again back to the class days, which hasn't been a thing for going on 30 years.
or the mask doesn't define the network private/public type?
The mask has nothing to do with the network being public or private. What makes it public or private is the address range used..
rfc1918 or private space is spelled out here
https://datatracker.ietf.org/doc/html/rfc191810.anything is a private space 10.0.0.0/8 which is the range 10.0.0.0 - 10.255.255.255, where yes .0 is the network or wire and 10.255.255.255 would be the broadcast. but say 10.90.90.0/8 would be just a host, and 10.0.0.255/8 also just a host..
This would prob be a better place to start
https://docs.netgate.com/pfsense/en/latest/network/addresses.htmlI remembered the classes as the new cool thing :D , you make me feel old now ahaahah.
I didn't understand this, was it a typo in the end?
How both can be hosts?? Is it an exception of that address range defined in some RFC?10.anything is a private space 10.0.0.0/8 which is the range 10.0.0.0 - 10.255.255.255, where yes .0 is the network or wire and 10.255.255.255 would be the broadcast. but say 10.90.90.0/8 would be just a host, and 10.0.0.255/8 also just a host..
Thank you again :)
-
@steveits said in How to set the same VLANs between the switch and PfSense:
@jt40 said in How to set the same VLANs between the switch and PfSense:
with a mask of 255.255.255.0 I can still set up 192.168.5.1 and 192.168.9.1 networks
255.255.255.0 means "the first three numbers must match." So:
192.168.0.1 / 255.255.255.0
is in a different network than
192.168.1.1 / 255.255.255.0but
192.168.0.1 / 255.255.0.0
is in the same network as
192.168.1.1 / 255.255.0.0So the mask matters but they matter together.
So if you tell pfSense WAN to use 192.168.0.1 / 255.255.0.0 then it knows all those addresses are WAN. You can't also set up LAN as 192.168.5.1 / 255.255.255.0 unless you change the mask on WAN.
Thank you.
So this means that every interface on PfSense needs to be on the same address range and configured with the same mask, right?
Regardless of uplink or other LANs.At that point, how do I route packets from/to 192.168.0.1 to 10.90.90.130 for example?
Shall I create a gateway? That would be a virtual gateway in PfSense.What would be its IP then?? I ask because the interface asks me for an IP address, but I don't want to create only 192.168.0.x networks/interfaces, I actually need to route down the switch on a network with range 10.90.90.x (I think I can even change that, but let's make it work as by default for now, just to keep things easy)
-
@jt40 said in How to set the same VLANs between the switch and PfSense:
So this means that every interface on PfSense needs to be on the same address range and configured with the same mask, right?
No. They just can’t overlap.
At that point, how do I route packets from/to 192.168.0.1 to 10.90.90.130 for example?
PfSense will know where it’s own interfaces/networks are. You just need to create firewall rules to allow traffic. Only LAN has an allow to any rule.
Re:.0/.255 …networks can have masks like 255.255.255.128 or other masks.
-
@steveits said in How to set the same VLANs between the switch and PfSense:
@jt40 said in How to set the same VLANs between the switch and PfSense:
So this means that every interface on PfSense needs to be on the same address range and configured with the same mask, right?
No. They just can’t overlap.
At that point, how do I route packets from/to 192.168.0.1 to 10.90.90.130 for example?
PfSense will know where it’s own interfaces/networks are. You just need to create firewall rules to allow traffic. Only LAN has an allow to any rule.
Re:.0/.255 …networks can have masks like 255.255.255.128 or other masks.
No. They just can’t overlap.
Do you mean they can't overlap by IP address?
PfSense will know where it’s own interfaces/networks are. You just need to create firewall rules to allow traffic. Only LAN has an allow to any rule.
So you mean that nothing will stop the traffic by default between LANs on the same PfSense device? And no virtual gateway is needed?
So If I assign the following IPs to different interfaces like:
- INET 1 190.168.0.4 ( Web GUI management interface, even though I'd like that IP on another range if possible)
- INET 2 192.168.0.5 (random usage)
- INET 3 UPLINK 192.168.0.6 (how does it know that it's UPLINK?)
- INET 4 DOWNLINK to the switch 10.90.90.120 (the default IP of my switch is 10.90.90.90, but that should be reserved to the Web GUI)
Is this supposed to work?
I'll try this evening.