Can't route between 2 vlans
-
@faktorqm what interfaces are those rules on?
And so on your lan side of pfsense this 214 vlan but where does pfsense see this 184 network/vlanAll I see is this vlan 6 untagged to get to the internet? I take it this is a public IP.. Where exactly is this admin IP on the loco sit?
I see that trunked in the igb4 to port 15 connection. But where is it where is the actual device your trying to talk too? Is it that loco? IP
-
The first image, is corresponding to the igb4.184 interface. The second image corresponds to igb4.214 interface.
pfsense see vlans 214, 184 and in the future 174 on igb4.
vlan 6 untagged is the internet interface. (It's a pppoe connection) and yes, you are right, the IP address on that is public.
The ufiber loco has the untagged traffic for the web admin page. If I connect a laptop directly I got access to the admin web interface. Tagged traffic are vlan 3 and 6.
If I set the vlan 6 on the laptop, and put a pppoe client, then I will have the public address.In the ARP table, I see the MAC Addresses and the IP addresses so I discarded a switch configuration problem. Also I tested to set the vlan 184 under port access mode to try the switch and I can access.
Also, I have ping from pfsense to ufiber loco (I can ping to 192.168.184.2) so I assume that pfsense "see it".
I know it's a difficult design to share in a forum post, so thanks for your time. Regards!
-
@faktorqm I see 214 and 184 on but I don't see 184 in the second image at all..
I only see vlan 6 untagged. Is that were your tagging 184?
-
@johnpoz excuse me, I'm talking about the rules images.
Interface igb4.214:
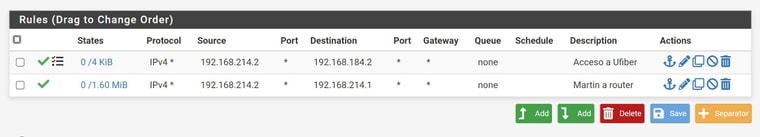
Interface igb4.184:
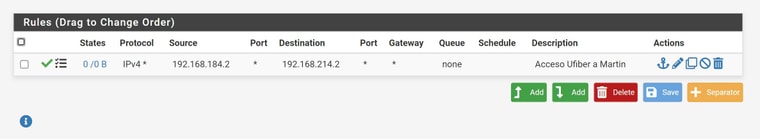
Vlan 184 untagged is entering from port 2 of the switch. Between the ufiber loco and port 2 on the switch, on the switch side, I got 184 untagged, 3 and 6 tagged. Then that VLAN is tagged on port 15 inside the switch.
Vlan 184: Untagged on port 2, tagged on port 15. port 2 is connected to the ufiber, 15 is connected to pfsense.
vlan 214: Untagged on port 16, tagged on port 15. Admin computer connected to port 16, pfsense is on 15.
vlan 174: This is not implemented yet, but will have same configuration. Untagged on port 6, tagged on port 15.
Vlan 14: this is the user network and has internet working and a dhcp server for the clients
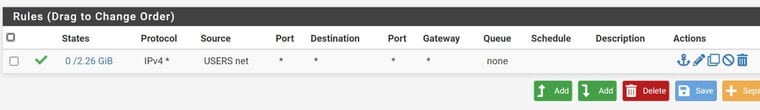
thanks
-
@faktorqm so I would sniff and make sure the traffic to the loco actually leave the interface on pfsense it should go to..
But most likely the problem is that the loco doesn't know how to get back to 192.168.184.2, so if you can not add a route to this on the loco, you would need need to nat on pfsense so local thinks your coming from 192.168.214.1 (pfsense IP in that network)
I might of flipped those around.. but you get what I mean?
-
@johnpoz mmm I think so. so I should setup, 192.168.214.1:8080 (that ip address correspond to the pfsense side of admin network) pointing to 192.168.184.2 (ip of the ufiber loco) in order to access from 192.168.214.2 (admin computer). In that way, the ufiber loco will "see" that the request are sent from 192.168.184.1 (ip address correspond to the pfsense side of ufiber loco network)
Another question, this is a secure network design? In the past I was thinking in a single subnet having the switch web admin, ufiber admin, and so on, but I switched to make one vlan per device in order to increase security in case of attack. I know that this is my home and there is no need to be maniac, but I would like to know which is the "industry standard" if any, or the commonly used solution for this use case. Thanks!
-
@faktorqm I would just nat to the interface IP.. I am still not seeing where this vlan the loco is on is connected to pfsense.. Its not on the drawing.
So its tagged to your switch on port 2 from the loco, its a different interface to the dlink?
All you need to do is outbound nat to the loco so it sees any traffic coming from pfsense networks as the IP of pfsense in that 184 network..
As to secure design? Can not tell from the looking at these drawings, especially with only seeing some rules on a couple of interfaces. And no idea on what vlans you have going where with your switches.
Seems you have what is the same switch in multiple drawings - I wouldn't draw it way, that can always be confusing.. I would put everything on 1 drawing.
-
@johnpoz ok John, I'm going for the "design is my passion" cup now...
I had to put the image in imgur because the forum told me that the image dimensions are too big.
https://imgur.com/a/icIOGOf
I hope this drawing can help you to understand my setup. Thanks!
-
Ok - so sniff on your 184 interface when you send traffic from 214 to your loco.. Do you see the traffic go out?
You mentioned that pfsense sees the arp for the loco IP.
So if your not seeing a reply that leads to believe that there is no gateway for the 184 address on the loco to know how to get back to 214.. So source nat the traffic, so when you talk to loco from your admin pc. It thinks that came from pfsense 184 address.
-
@johnpoz ok I got it working!!! you were right, I need source NAT to work with the device. I had to read the docs and some forums posts about that because I did not know how to do that.
The solution for those who wants to do the same config
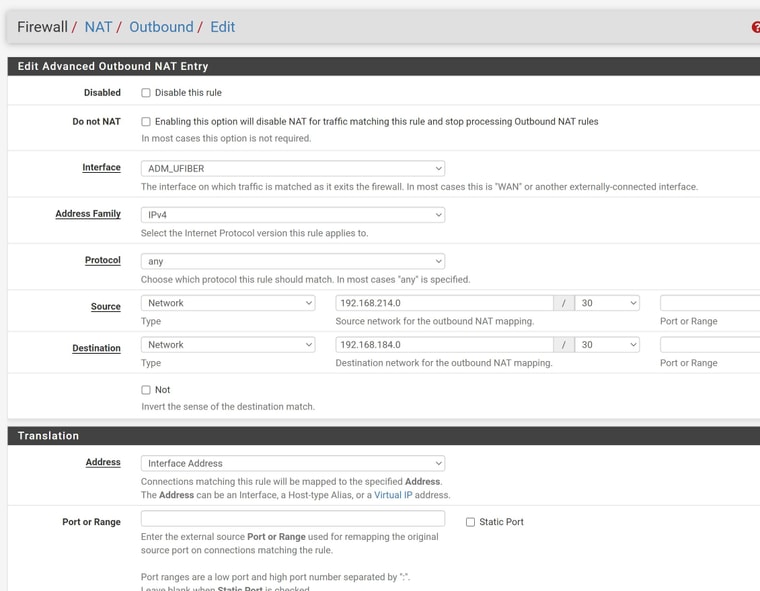
REMEMBER to change before that sccreen, to "Hybrid Outbound NAT rule generation.
(Automatic Outbound NAT + rules below)" mode. If you create the rule without changing the mode, it will show greyed out and of course, it will not work.John, thanks a lot for your patience and for guide me to the solution. Regards!