VLAN an Firewall rule not matching
-
@johnpoz Yes maybe I m lost.
The main network is 192.168.1.0/24, the VLAN 10.40.23.99/24
The Client (mobile phone) is connected with a Access Point, the SSID is tagged with 4000, the switch have a configuration as hybrid port, and the tags 1000,2000,3000,4000,1 is configured. Than the switch connect to pfsense with the same config.
As I can see the allow of the connection from the 10.40.23/24 network to 192.168.1.0/24 in the pfsense log I guess, that the routing must be happening here and not before.
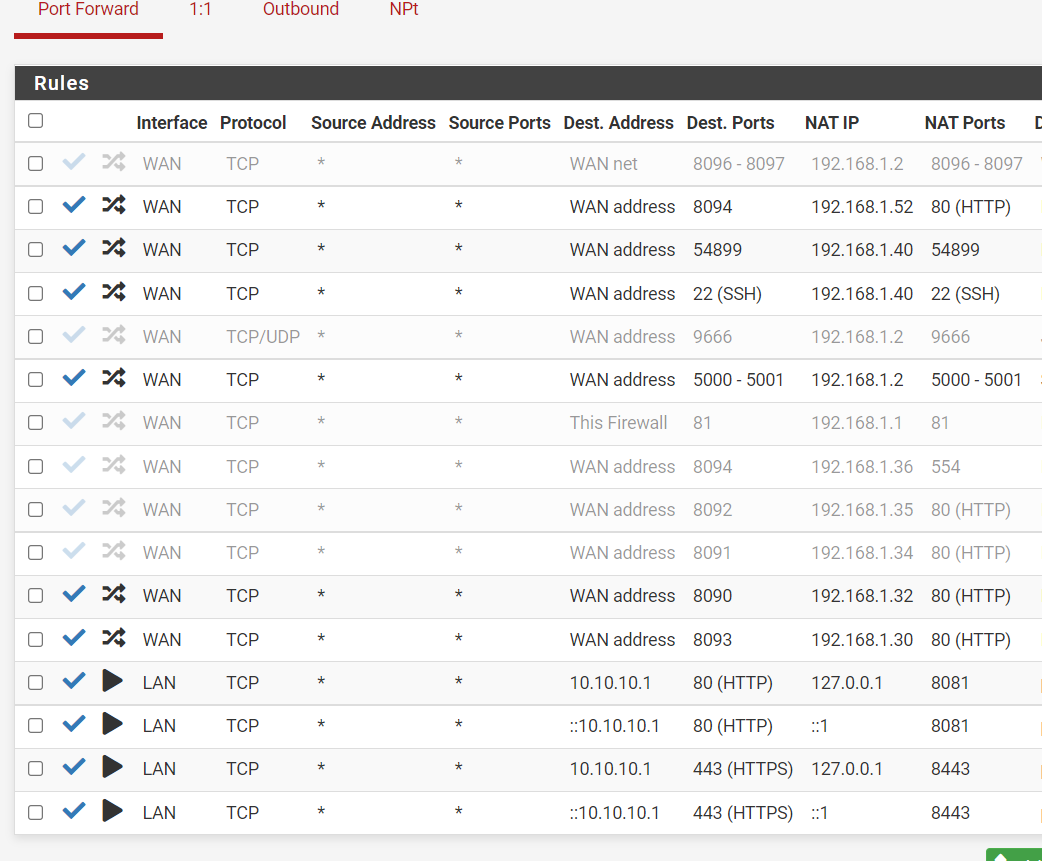
Here a post again of my port forwardings, that also does not contain any network that is in question here:
-
@interessierter said in VLAN an Firewall rule not matching:
As I can see the allow of the connection from the 10.40.23/24 network to 192.168.1.0/24 in the pfsense log I guess
where?
Here?
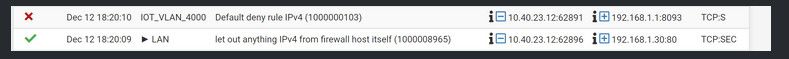
The allowed there is because the traffic was generated by pfsense.. There are rules that let the firewall go where it wants..
[21.05.2-RELEASE][admin@sg4860.local.lan]/root: pfctl -sr | grep "let out" pass out inet all flags S/SA keep state allow-opts label "let out anything IPv4 from firewall host itself" pass out inet6 all flags S/SA keep state allow-opts label "let out anything IPv6 from firewall host itself" -
@johnpoz Yes but to be honest I don t know what rule that should be? How does such a rule look like?
-
@interessierter I just showed you what the rule looks like ;)
Its a hidden rule.
You can view all the rules via
https://docs.netgate.com/pfsense/en/latest/firewall/pf-ruleset.htmlThere are a few hidden rules, mostly to keep users from shooting themselves in the foot ;) Common example of these is when you enable dhcp server on an interface, rules are created (hidden) that make sure dhcp will work.
notice those rules are pass "out" rules, which is why you see the little black triangle on the firewall entry.
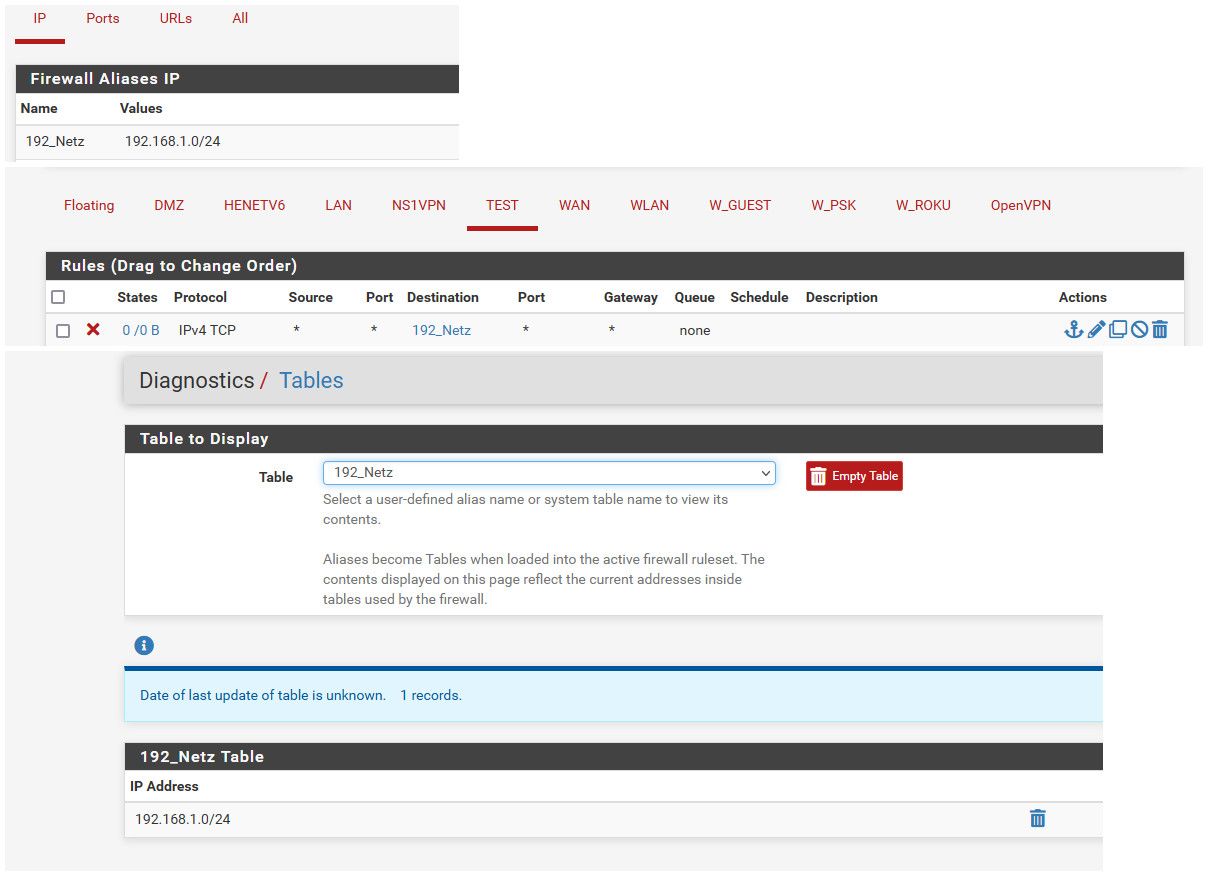
What I would look into is why your rule is not triggering? Do you still show 0/0 for the states on your block 192_netz rule? You could look in your tables under the diagnotic menu to make sure that table is showing your 192.168.1/24 network.
Possible your rules have not be loaded?
-
-
@interessierter that is not the 192_netz table..
Also why are you natting a 172.168.1.0? that is a typo? without a mask?
See here is my rfc1918 alias table I created entries
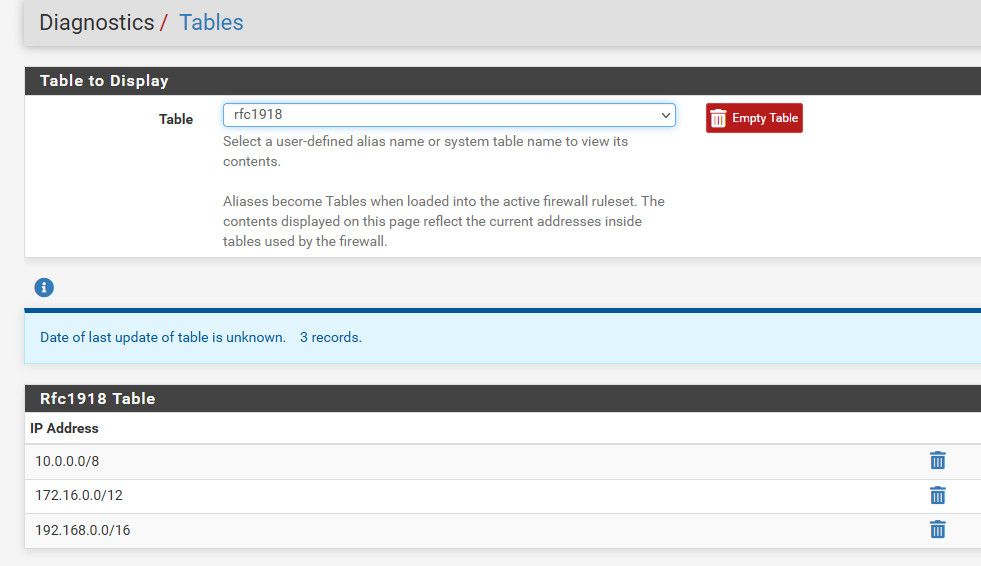
-
@johnpoz I dont know but I guess it will not solve the issue right?
I have for my main network right now 192.168.1.0/24
vlan 10.10.23.99/24
vlan2 10.20.23.99/24
vlan3 10.30.23.99/24
vlan4 10.40.23.99/24
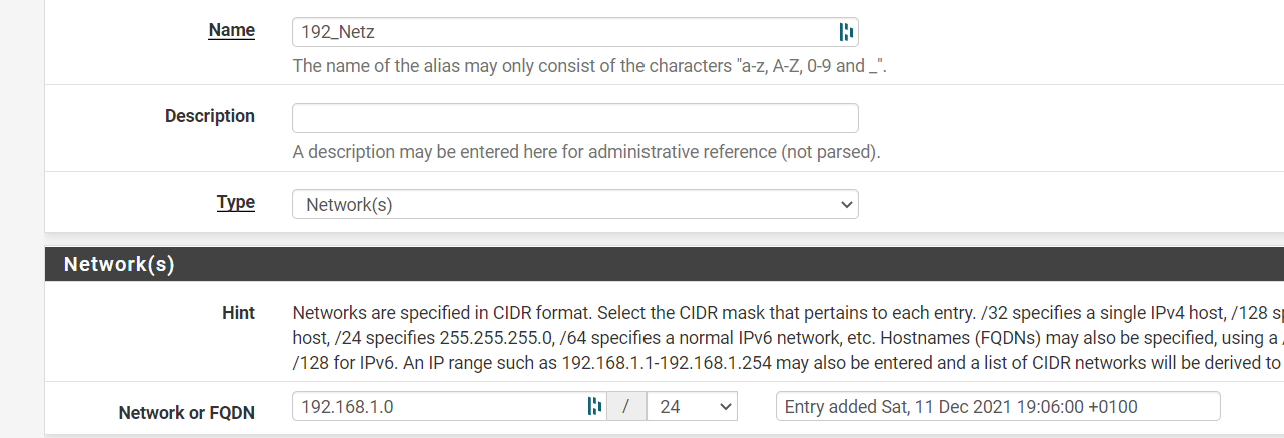
vlan5 10.45.23.99/24My 192 Netz only contains 192.168.1.0/24, because I want to block requests to this network
-
@interessierter I get that.. But your not showing that the table actually loaded.
And your rule is not triggering from the 0/0 in the states column.. Why its not is the question.. Maybe the table didn't load? Maybe your client isn't going through pfsense?
I don't see any other rules above it that would allow the traffic..
-
@johnpoz What table you want to see?
-
The table alias you created the 192_netz table.
What version of pfsense are you running exactly? There was some issues in the dev versions the other day where state tables not counting.. and all showing 0/0
Alias tables normally do not populate until used in a rule.. But lets make sure the alias you created actually created the table and put in the 192.168.1.0/24 network.
-
-
@interessierter dude that is not the actual TABLE that is created from the alias..
Go to the diagnostic menu, pick tables then select your 192_netz table.. Does it list this network, do you see the table in the table drop down?
See my above example showing my rfc1918 table created from my rfc1918 alias.
What I am trying to verify is this
-
@johnpoz said in VLAN an Firewall rule not matching:
@interessierter dude that is not the actual TABLE that is created from the alias..
Go to the diagnostic menu, pick tables then select your 192_netz table.. Does it list this network, do you see the table in the table drop down?
See my above example showing my rfc1918 table created from my rfc1918 alias.
What I am trying to verify is this

Sorry do you mean here? If yes, the 192_Netz is not here:
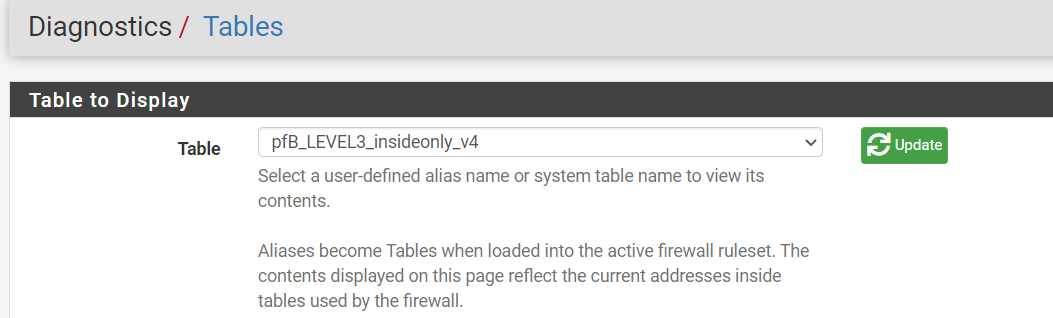
-
@interessierter well if you do not see your table populated, then that would explain why that rule is not working.
As I highlighted, tables that you create with an alias are not populated until they are put into a rule, and the rule is loaded.
If your not seeing the table listed under diagnostics. Then no it wouldn't work..
-
@johnpoz said in VLAN an Firewall rule not matching:
@interessierter well if you do not see your table populated, then that would explain why that rule is not working.
As I highlighted, tables that you create with an alias are not populated until they are put into a rule, and the rule is loaded.
If your not seeing the table listed under diagnostics. Then no it wouldn't work..
But what did I wrong? I have saved and applied the rule after creating, and I m sure that the firewall was also rebooted in the time between (what should be anyway not required).
-
@interessierter You sure your not seeing a error about memory? You sure look to have a lot of aliases..
And none of your rules show any hits at all - they all show 0/0 for states.
When you have lots entries in your tables - it can cause a memory issue.
There are many a thread related to this about. Here for example
Have you increased your table entries?
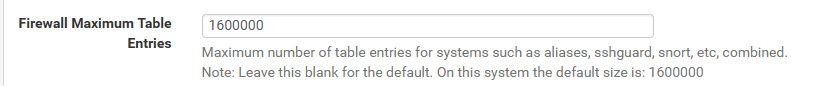
This setting is system / advanced / firewall & nat
-
This post is deleted! -
@bob-dig said in VLAN an Firewall rule not matching:
It looks like an alias can't start with a number
Looks to be working here..
-
@johnpoz You are right, I had no rule using it. Working here too.
-
@bob-dig no problem - it was a good check to be sure.
if I had to "GUESS" from how many aliases he has setup, and I see some there labeled IPv6, etc..
He needs to adjust his max table entries.. Maybe his not seeing the error that should show up when rules don't load because of allocation of memory.. I would assume that TOP_v6 rule would be quite large..
I also don't like that none of his rules showing any hits at all 0/0 there for states..
His any any IPv4 rule he shows for sure should show something vs 0/0.. That is if anything is hitting that interface at all for traffic. But tables in rules don't actually have to trigger to populate - they just need to be used in a rule. And the rules reloaded, which would happen when you hit apply.