How to set the same VLANs between the switch and PfSense
-
@jt40 pfSense is not for everyone.

-
@bob-dig said in How to set the same VLANs between the switch and PfSense:
@jt40 pfSense is not for everyone.

Thanks for the feedback, but looking at the last message, tell me if I could have made some mistake.
That message was written before my test today, prepare yourself, you are gonna laugh hardly.All looks good today, the firewall was re-enabled automatically overnight, which I don't mind if there is the auto-enable after some time, I still need to figure out where is such setting though.
The box has been working without reboot, magic happens during night :D .Basically, alI I tried yesterday, today works well, firewall rules work as expected, IP to IP, network to IP, or network to network (not in every case though, but that could be my negligence)...
This is what I did today, mostly successful
 :
:-
WebGUI connection always successful
-
Firewall rules behaved as expected for the WebGUI, even changing IP to network etc.
-
Firewall rules behaved as expected to reach the WAN from another interface
 , I couldn't believe it :D .
, I couldn't believe it :D .
The only thing is that I specified the modem/router from my ISP as a gateway, I think there is no other way to do it.
Considering that I have 4 interfaces to use at the moment, I'll specify the same gateway in each interfaces, I hope it's safe enough in terms of security. -
Firefox behaved bad today, I've got a HTTP 200 GET --> NS_BINDING_ABORTED
This can happen for many reasons, I didn't investigate too much...
Chrome works though, so today I can't blame the firewall in front of this case. I need to specify that yesterday Chrome didn't work, I had to disable every time the firewall to login.
Yesterday I also rebooted the laptop and did a fresh test when the firewall was enabled, nothing changed.
What to say, today was productive again :) .
I'll check again tomorrow, just in case something changes overnight :D -
-
@jt40 said in How to set the same VLANs between the switch and PfSense:
I'll specify the same gateway in each interfaces
Normally only the interface that connects to the network would have a gateway.
Aside from that, each interface would need a gateway in its subnet, so it can communicate with said gateway.
Glad it's working for you today. Make a backup of the config. :)
-
@steveits said in How to set the same VLANs between the switch and PfSense:
@jt40 said in How to set the same VLANs between the switch and PfSense:
I'll specify the same gateway in each interfaces
Normally only the interface that connects to the network would have a gateway.
Aside from that, each interface would need a gateway in its subnet, so it can communicate with said gateway.
In my case I think that I simply need firewall rules then, and that's what I did in the end, I made a mistake before, sorry.
I've set the firewall rules for a basic network is in this way:
- LAN5 (send everything from LAN5 network to WAN address)
- WAN (accept everything that comes from LAN5 network and send it to Single Host or Alias (Gateway IP)) (I have a modem/router in front of)
The WAN is set to use the gateway and that's how it knows where to route the packets.
In this way I was able to get to internet, but does it look safe?
Forget about protocols and ports for now we could argue a lot abotu strategies here :D , moreover I mean if the routing is correct, I don't think there is something else that could work.Glad it's working for you today. Make a backup of the config. :)
On man, the BACKUPP!!! At this point, more I do everything from scratch, more I learn, I won't try to rollback unless I'm actively using the network when making a change :D .
-
@jt40 Firewall rules don't sent traffic anywhere. They just allow it or block it. pfSense will know where to route traffic on its own interfaces, or send the rest to its gateway to get to the Internet. Are you thinking of NAT rules?
The default rule on LAN allows from LAN to any, meaning any other network. There are no default rules on any other interface, meaning all traffic is blocked. Rules apply to packets arriving on that interface.
-
@steveits said in How to set the same VLANs between the switch and PfSense:
@jt40 Firewall rules don't sent traffic anywhere. They just allow it or block it. pfSense will know where to route traffic on its own interfaces, or send the rest to its gateway to get to the Internet. Are you thinking of NAT rules?
I think it does auto NAT then, like simple routers out there.
The default rule on LAN allows from LAN to any, meaning any other network. There are no default rules on any other interface, meaning all traffic is blocked. Rules apply to packets arriving on that interface.
I don't have default rules when I create the interface, I think I disabled that function, it should be a good idea :) .
I've just set the rule in outbound for now, "any to WAN" to keep it easy for the initial testing.Regarding NAT, I'll need to think on how to do it...
It seems that I got all set for a simple setup, now the rest of the story is on the switch after PfSense...
I think I'll need to do the following:- Create the VLANs on the switch (done)
- Create the simple rules (if possible) on the switch
- Create the same VLANs on PfSense on the same interface (truncate port)
- Create firewall rules
- The IP range will be a problem, the switch has 10.x.x.x by default, so I'll need to change it.
I've read somewhere that 192.x.x.x at home could give some trouble with VPNs (or similar issue), most probably I'll need to change every IP to 10.x.x.x...
I need also to check why the mask is also 255.255.255.0 for 10.x.x.x, I think that the mask is the same for the meaning of the mask itself, but it's a different network than 192.x.x.x , therefore I'd need a virtual gateway, NAT or some other way that I don't know.
I think I'll open a new thread, this is going too wild :D .
Thanks a lot to everyone :) , you have been fundamental in this journey to get internet on one port at least, LOL :D -
@jt40 said in How to set the same VLANs between the switch and PfSense:
I don't have any other rule on that interface,
The default settings are
- WAN: Common functional default setting for a WAN
- LAN: Common functional default setting for a LAN including an anti-lockout rule
- OPT1... or VLAN: No rules other the default deny all rule.
So if you add a VLAN or use OPT as an extra LAN you need rules similar to the default LAN rules. Similarly if you use OPT as an extra WAN you need rules similar to the default WAN rules.
-
@steveits said in How to set the same VLANs between the switch and PfSense:
Firewall rules don't sent traffic anywhere.
Unless your policy routing ;)
@jt40 said in How to set the same VLANs between the switch and PfSense:
LAN5 (send everything from LAN5 network to WAN address)
What does that even mean? That isn't going to get to the internet..
WAN (accept everything that comes from LAN5 network
How would the WAN ever see any traffic from LAN5?
Rules are evaluated as traffic enters an interface from the network it is attached too... WAN could never see Lan5 traffic as source..
Please post up these rules you created..
-
@patch said in How to set the same VLANs between the switch and PfSense:
@jt40 said in How to set the same VLANs between the switch and PfSense:
I don't have any other rule on that interface,
The default settings are
- WAN: Common functional default setting for a WAN
- LAN: Common functional default setting for a LAN including an anti-lockout rule
- OPT1... or VLAN: No rules other the default deny all rule.
So if you add a VLAN or use OPT as an extra LAN you need rules similar to the default LAN rules. Similarly if you use OPT as an extra WAN you need rules similar to the default WAN rules.
I removed all the default rules, plus when I create a new interface there is no rule at all.
Is the "DENY ALL in INBOUND" rule implicit for each interface? If so, where I can see it?@johnpoz said in How to set the same VLANs between the switch and PfSense:
@steveits said in How to set the same VLANs between the switch and PfSense:
Firewall rules don't sent traffic anywhere.
Unless your policy routing ;)
@jt40 said in How to set the same VLANs between the switch and PfSense:
LAN5 (send everything from LAN5 network to WAN address)
What does that even mean? That isn't going to get to the internet..
In my head, that means that every address of the network in the LAN5 interface can reach the WAN address, which is directly connected to a gateway. I don't know if I see it correctly, but this is how it makes sense for me :D .
WAN (accept everything that comes from LAN5 network
How would the WAN ever see any traffic from LAN5?
I probably didn't mention it in this way, but due to the ISP router in front of, that WAN is actually a LAN.
I'd be curious to know if it would have been different with a real WAN.Rules are evaluated as traffic enters an interface from the network it is attached too... WAN could never see Lan5 traffic as source..
Strange, so how the routing would work?
Where and how should I specify the rule to allow traffic from one LAN to internet?Please post up these rules you created..
The rules are in the previous message, I didn't omit details or rules, I could give a screenshot but it's really what I described.
-
@jt40 said in How to set the same VLANs between the switch and PfSense:
Where and how should I specify the rule to allow traffic from one LAN to internet?
On interface LAN5 the default should be no rules. The implicit deny rule is not explicit, therefore not listed. Add a rule to allow from LAN5 Net to any. If you also want to block LAN5 from getting to LAN, add a rule above that rule, to deny from LAN5 Net to LAN Net.
-
Oh ok, I think I was a bit drunk, if there is no rule then is DENY ALL, so all the INBOUND traffic is DENY currently because I have no rule as such, I think it works in this way as any other router :D , I tested it in the LAN just in case.
-
This Askimet spam filter is against me, I didn't post any link and I still can't write the message I need :D
-
@jt40 said in How to set the same VLANs between the switch and PfSense:
I could give a screenshot but it's really what I described.
What you described doesn't make any sense - lan5 could not or would or could ever be source of traffic into the wan interface..
-
In response to Steve -->
Is it not already disabled by default? Please look my message above.If you talk about the same LAN instead (for example LAN2 to LAN2), I don't want the communication between the devices on the same LAN, but I also don't want the communication between different LANs for now.
At the moment, due to no rule in place I think it's DENY ALL between LANs, I need to check between the devices of the same LAN.In any case, I'll configure such things in VLAN, where below that VLAN there will be a switch, which by itself will have the client isolation rule enabled.
I need to check what I need to do on the PfSense firewall about it... -
@jt40 said in How to set the same VLANs between the switch and PfSense:
I don't want the communication between the devices on the same LAN
pfsense has nothing to do with communication between devices on the network (lan) Pfsense is a router, it routes and firewall traffic between networks. It is not involved in devices talking to each other on the same network, only for traffic wanting to leave a network.
If you don't want devices talking to each other on the same network you would need to do that at your switch - lookup up a private vlan. Or via wireless this is often called AP or Client isolation.
https://en.wikipedia.org/wiki/Private_VLAN
https://support.denon.com/app/answers/detail/a_id/3746/~/wireless%2C-ap-or-client-isolation
-
@jt40 If you allow LAN2 to Any, that will allow to LAN5 as well. LAN5 is "any."
You can't do much about devices on the same network communicating. That normally is handled by a switch and those packets don't even get to the router.
-
@jt40 said in How to set the same VLANs between the switch and PfSense:
if there is no rule then is DENY ALL, so all the INBOUND traffic is DENY currently because I have no rule as such
- Rules are evaluated from the top down.
- The first rule which matches is used and no further rules are evaluated.
- If no entered rules match the the packet is dropped / blocked.
So if no rules are entered every packet falls off the bottom of the rule list and is blocked.
I find it simplest to order my rules as
- Allowed local traffic
- Reject other local traffic
- Allowed Internet traffic
- Block other Internet traffic
An example of which for LAN2 is:
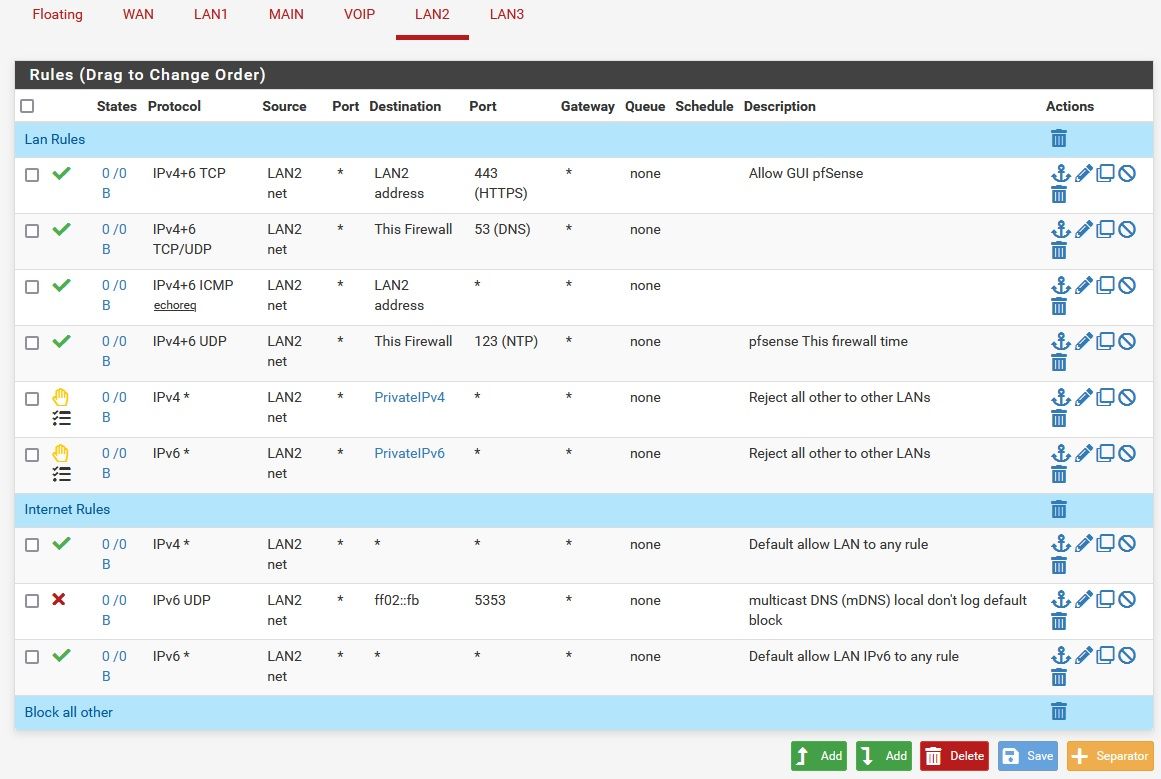
-
@jt40 said in How to set the same VLANs between the switch and PfSense:
This Askimet spam filter is against me, I didn't post any link and I still can't write the message I need :D
I am with Akismet on this one.

-
@bob-dig said in How to set the same VLANs between the switch and PfSense:
@jt40 said in How to set the same VLANs between the switch and PfSense:
This Askimet spam filter is against me, I didn't post any link and I still can't write the message I need :D
I am with Akismet on this one.


@patch said in How to set the same VLANs between the switch and PfSense:
@jt40 said in How to set the same VLANs between the switch and PfSense:
if there is no rule then is DENY ALL, so all the INBOUND traffic is DENY currently because I have no rule as such
- Rules are evaluated from the top down.
- The first rule which matches is used and no further rules are evaluated.
- If no entered rules match the the packet is dropped / blocked.
So if no rules are entered every packet falls off the bottom of the rule list and is blocked.
I find it simplest to order my rules as
- Allowed local traffic
- Block other local traffic
- Allowed Internet traffic
- Block other Internet traffic
An example of which for LAN2 is:

Thank you.
I see that you have set also the REJECT rules, but my point is, is it not by default?
Precisely, I would expect DROP as by default, not REJECT.Look at the simplest case, if I have a rule do to something, I expect that rule to be evaluated.
If the device asks for something else and the rule is not present, I expect the packets to be dropped automatically...
This is also the easiest way a firewall can work to make my life easier :D -
@jt40 the default is drop, ie just block..
But internally it is sometime better to reject vs just drop. I want to let my internal client you can not go there right away - via a reject. Vs letting it bang its head with retrans trying to figure out why he is not getting an answer.
Externally no you would almost never want to send a reject to something out on the internet.. But internally - if your going to on purpose prevent something like vlan x from talking to vlan y.. its better to just let them know - hey stop trying to go there ;)
If the device asks for something else and the rule is not present, I expect the packets to be dropped automatically...
That is how it works.. If there is not allowed, then traffic dropped gone over this how many times already.. But yet to see a picture of your rules.. You have been told multiple times that pfsense will not route traffic unless there is an allow rule.
If the spam system is preventing you from uploading a picture - then link to it somewhere else, use something like my picture is here somewhere . domain . tld / whatever even if you have to but. But what I can tell you yet again yes default is deny. No rule to allow, traffic is dropped.
If you want to actually see it - then look at the full rule set. Since this default deny is not shown in the gui..
[21.05.2-RELEASE][admin@sg4860.local.lan]/root: pfctl -sr | grep "Default deny rule" block drop in inet all label "Default deny rule IPv4" block drop out inet all label "Default deny rule IPv4" block drop in inet6 all label "Default deny rule IPv6" block drop out inet6 all label "Default deny rule IPv6" [21.05.2-RELEASE][admin@sg4860.local.lan]/root: -
P Patch referenced this topic on
-
P Patch referenced this topic on