OpenVPN - Remote Access User Auth still broken in 2.5.2?
-
if "User Auth" was broken, then all devices using current CE and Plus couldn't be used to "home work", or just simple remote access.
That alone would trigger an emergency update - or at least a patch.
Btw : what about skipping "User Auth", go for TLS only.
I know that works, as I'm using it right now.@andyhi said in OpenVPN - Remote Access User Auth still broken in 2.5.2?:
I ran across it a day or so after upgrading a BYOD box to v2.5.0 and had to use the same fix
2.5.0 is old, was a huge milestone and had some issues.
2.5.2 is what you need - you don't want to test drive old bugs ;). -
@gertjan said in OpenVPN - Remote Access User Auth still broken in 2.5.2?:
if "User Auth" was broken, then all devices using current CE and Plus couldn't be used to "home work", or just simple remote access.
That alone would trigger an emergency update - or at least a patch.
Wrong - Many people appear to be using TLS based auth only instead of TLS + User Auth (TLS + User Password).
Btw : what about skipping "User Auth", go for TLS only.
I know that works, as I'm using it right now.Yeah, that's what I stated in my original post... TLS based auth works. TLS + "User Auth" (TLS + password) and "User Auth" (password only) does not... at least on my SG-1100 and one of my BYOD builds. The "User Auth" (password) option quit working on both after a prior version upgrade and started working again with no changes on my end for the SG-1100 after a recent v2.5.2 upgrade... but is still broken on the BYOD device which is also on v2.5.2.
As for TLS only vs TLS + user password - TLS + User Auth is more secure. (Technically it's 2FA - Something you have and something you know.) The TLS cert / private key are sitting on the client in the file system (assuming smart card / HSM isn't being used) and subject to be stolen while at rest at any point. This could potentially be by malware or if you lose physical control of the asset. Assuming you key the password in at every login and don't check the store password option - The user password portion is only subject to be stolen if the password or it's hash is stolen from memory by the threat actor... so exploitation opportunity is still there but significantly reduced by using the TLS plus User password option and not saving the password to the file system on the client.
@andyhi said in OpenVPN - Remote Access User Auth still broken in 2.5.2?:
I ran across it a day or so after upgrading a BYOD box to v2.5.0 and had to use the same fix
2.5.0 is old, was a huge milestone and had some issues.
2.5.2 is what you need - you don't want to test drive old bugs ;).Perhaps the timing of up upgrades wasn't clear. I upgraded to 2.5.0 early in the year - Late Feb / Early March a week or two after release. Given the issues with v2.5 for CE and Plus - I was slower to upgrade to the 2.5.1 and 2.5.2 code bases.
At this point I do suspect at least some people have TLS + User Auth (password) working as that's the default config for new setups and noone appears to be reporting similar issues. When I get some free time after the holidays I'll spin up some pFsesnse VMs from scratch to see what's going on... perhaps import a back up of the broken BYOD device and try a fresh OOB install with 1st time CA, certs, + open vpn config.
-
@andyhi said in OpenVPN - Remote Access User Auth still broken in 2.5.2?:
Wrong - Many people appear to be using TLS based auth only instead of TLS + User Auth (TLS + User Password).
What's wrong ?
If "User Auth" was broken, then we would / should would see posts on the forum about it. OpenVPN server usage became last year a extremely important feature, we all know why.
.I presume that "User Auth" (or "User Auth" combined with TLS) is very often used.Myself, I'm not using "User Auth", only TLS, as I'm using the pfSense OpenVPN server access just for maintenance reasons and some minor administration tasks.
edit :
I've set up a "user auth" OpenVPN server on my WAN interface, port 1195 UDPv4.
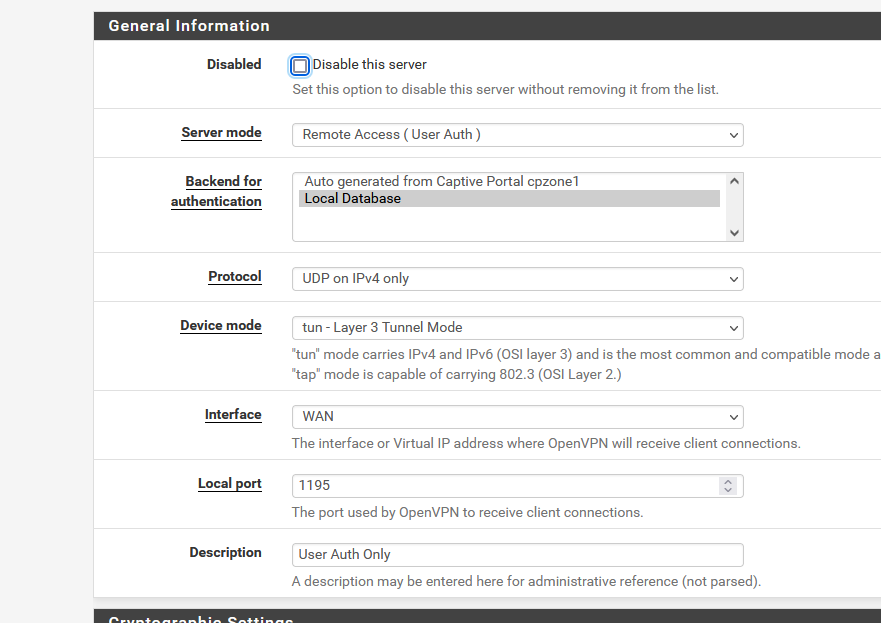
Assigned a not-yet-used IPv4 network 192.168.4.0/24
edit2 :
That is, I instantiated the 'virtual' interface created by my second '1195' OpenVPN as an interface and called it OPENVPNAUTH :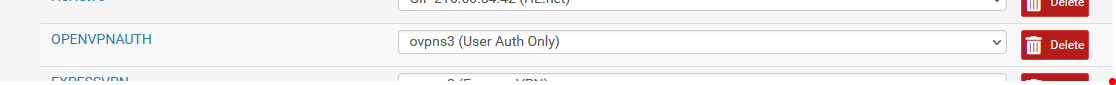
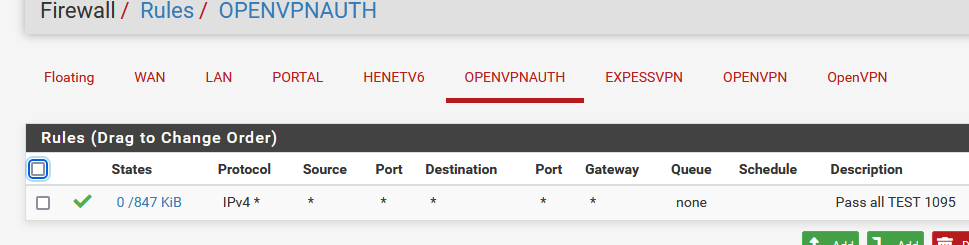
Created a main pass rule firewall rule on this OPENVPNAUTH :
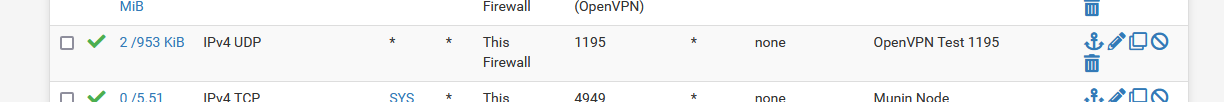
Created a firewall rule on WAN so UDP port 1195 traffic can come in :
Created a Nat/firewall in my ISP router ("port 1195 UDP4 to IP WAN pfSense" )
Created a OpenVPN user :
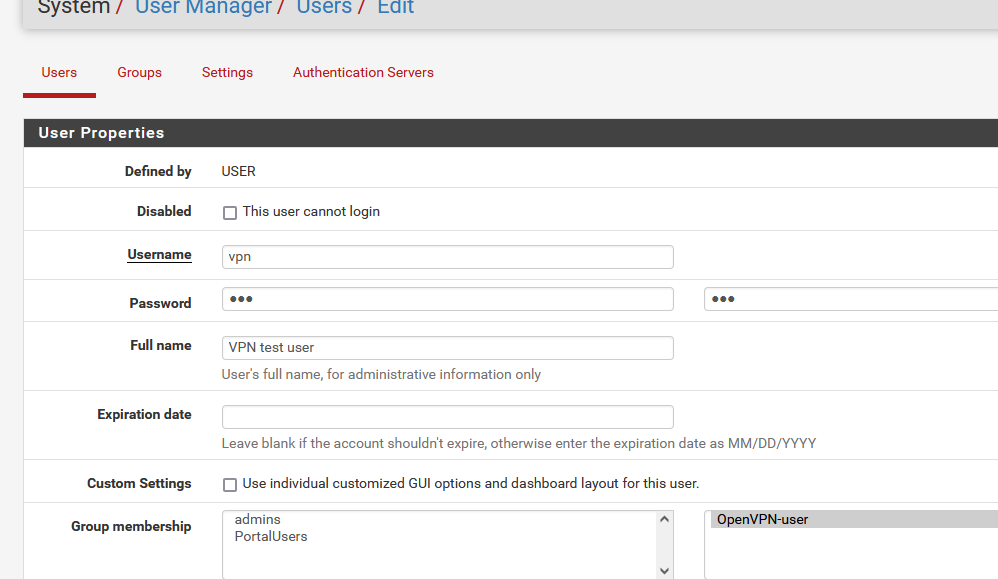
Exported the user config file( I had to select the "1195" openvpn server instance ) :
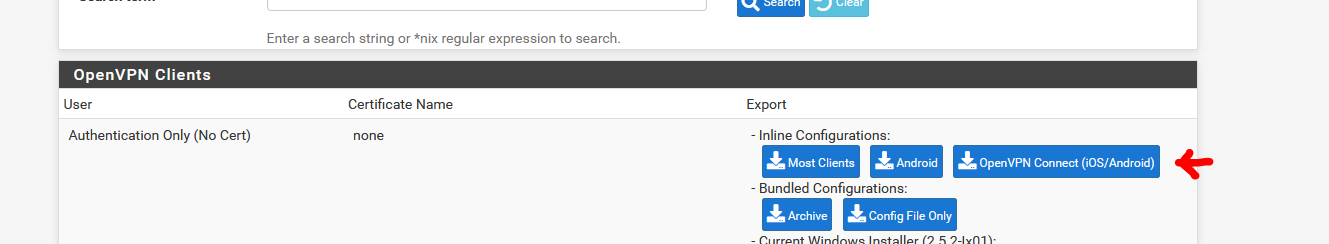
Imported the file in my iPhone.
While doing so, added a user name "vpn" and password "***".I could connect just fine, using "User Auth" only.
-
I'm using TLS + User Auth for my "Roadwarroirs"
AKA .. 4096bit Certs + UID/PWDIt would be a major disaster if it does not work , when i upgrade my Central pfSense to 2.5.2.
So i'm quite interested in this thread
/Bingo
-
@bingo600 said in OpenVPN - Remote Access User Auth still broken in 2.5.2?:
So i'm quite interested in this thread
Same here - I spend way to much time here ;) And I would of thought I would of noticed this thread where jimp confirmed an issue, but no bug report? I can not seem to find anything in redmine related to this.
And also agree, that if something like this broke - I would think there would be many a post about it.. Its a common sort of setup, etc.
-
@johnpoz said in OpenVPN - Remote Access User Auth still broken in 2.5.2?:
Its a common sort of setup, etc.
"Common" means you know what to do. And the thing is, that's not 'common'.
Setting up a bare minimum 'OpenVPN server' supporting 'user auth', implies several steps.
I even had to 'punch' a hole into my upstream ISP router, something I completely forgot during several minutes, but then the palm of my hand went straight to the front of my head etc. -
@gertjan said in OpenVPN - Remote Access User Auth still broken in 2.5.2?:
'OpenVPN server' supporting 'user auth', implies several steps.
Concur there are more steps than just tls auth, but tls+auth is default using the wizard, to why I stated common.
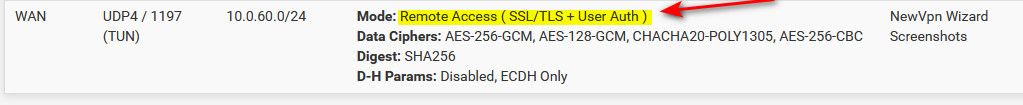
The wizard didn't even ask the question..
-
I learned something : there is a wizard !
-
@gertjan said in OpenVPN - Remote Access User Auth still broken in 2.5.2?:
there is a wizard
hahaah ;)
-
@johnpoz said in OpenVPN - Remote Access User Auth still broken in 2.5.2?:
@gertjan said in OpenVPN - Remote Access User Auth still broken in 2.5.2?:
there is a wizard
hahaah ;)
I've never used a wizard for making VPN's.
I'd like to be in control.Or ... Did I just miss you being procounced : The Gandalf of pfSense ??
/Bingo
-
@bingo600 said in OpenVPN - Remote Access User Auth still broken in 2.5.2?:
The Gandalf of pfSense ??
hahah - no unless I missed the ceremony myself? ;)
The wizard is just a easy way to get a basic remote access vpn up in running in a few clicks. You can always edit the settings how you see fit after. It will even walk you through creating the CA and certs, etc.. Its a great little tool for someone new to setting up a vpn.. Will create the firewall rule for you, etc.