pfSense 2.5.2 OpenVPN Server - problems getting DNS working
-
Hi,
I'm new to the forum so please bear with me.
I created an OpenVPN Server successfully and get this to connect to pfsense.
For initial test purposes , I'm using my android handset to test connectivity.
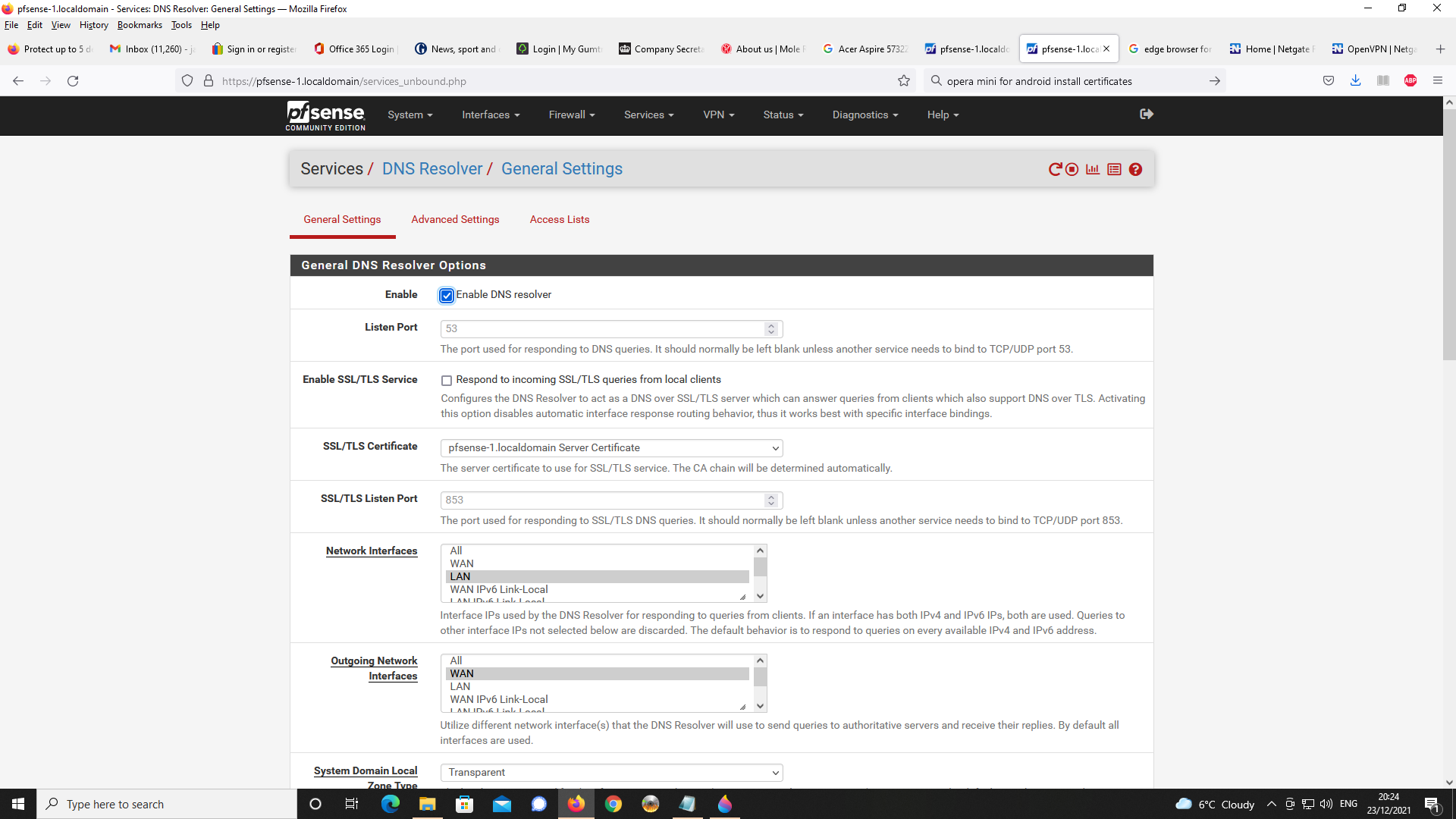
On pfSense, I have set up DNS Resolver as a forwarder to cloudfare servers and have configured DNS over TLS to work for all DNS requests to the cloudflare servers. For all local DNS traffic this goes to DNS resolver as port 53 traffic. This all appears to work ok and
I have used packet capture to confirm DNS over TLS is functioning as expected.For checking local name resolution on port 53, I tested name resolution on my LAN
Windows 10 client. I used nslookup to test resolution of hostnames and these all work
as expected.In order to prohibit port 53 traffic out of pfsense (as this is handled solely by DNS over
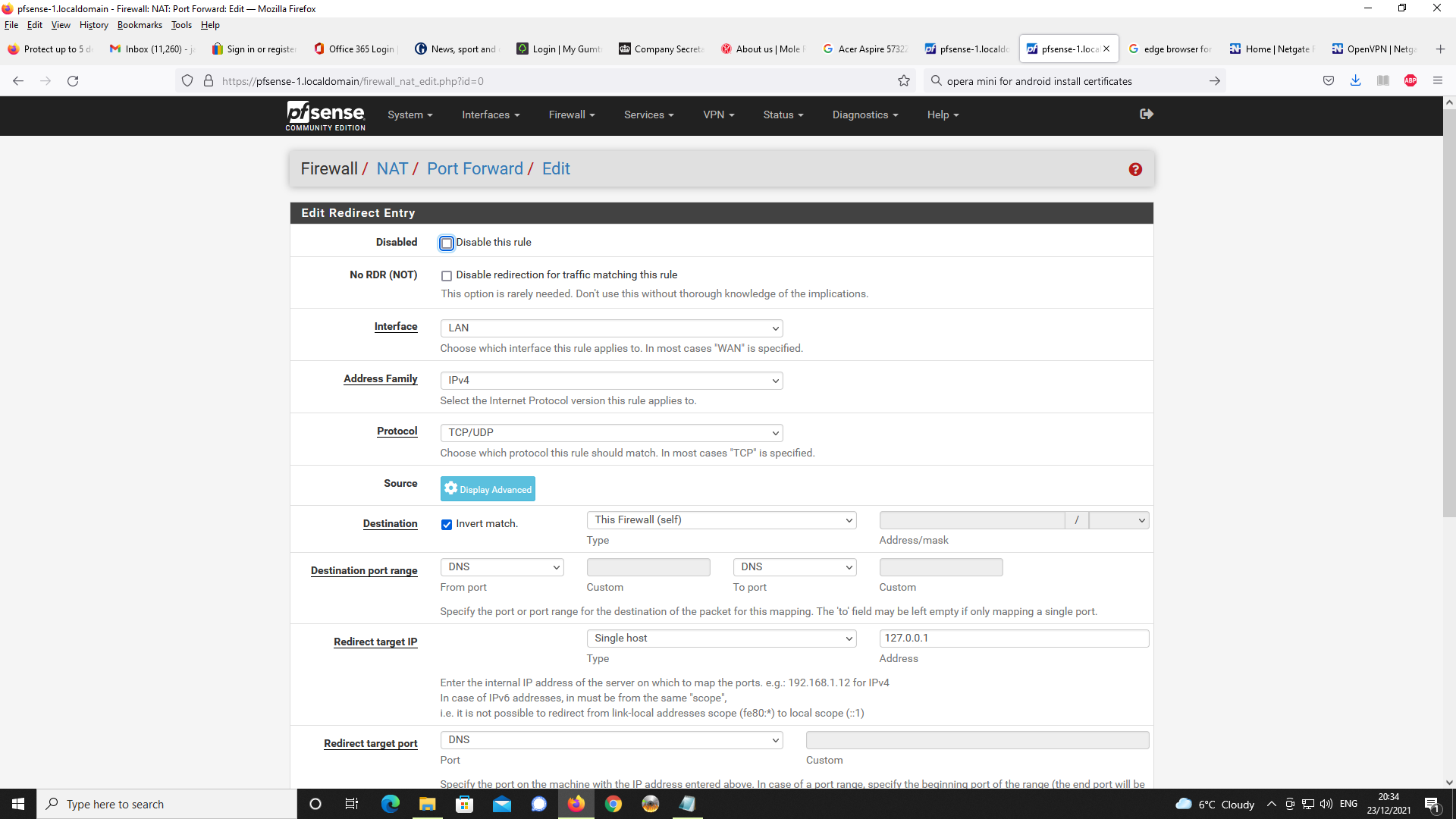
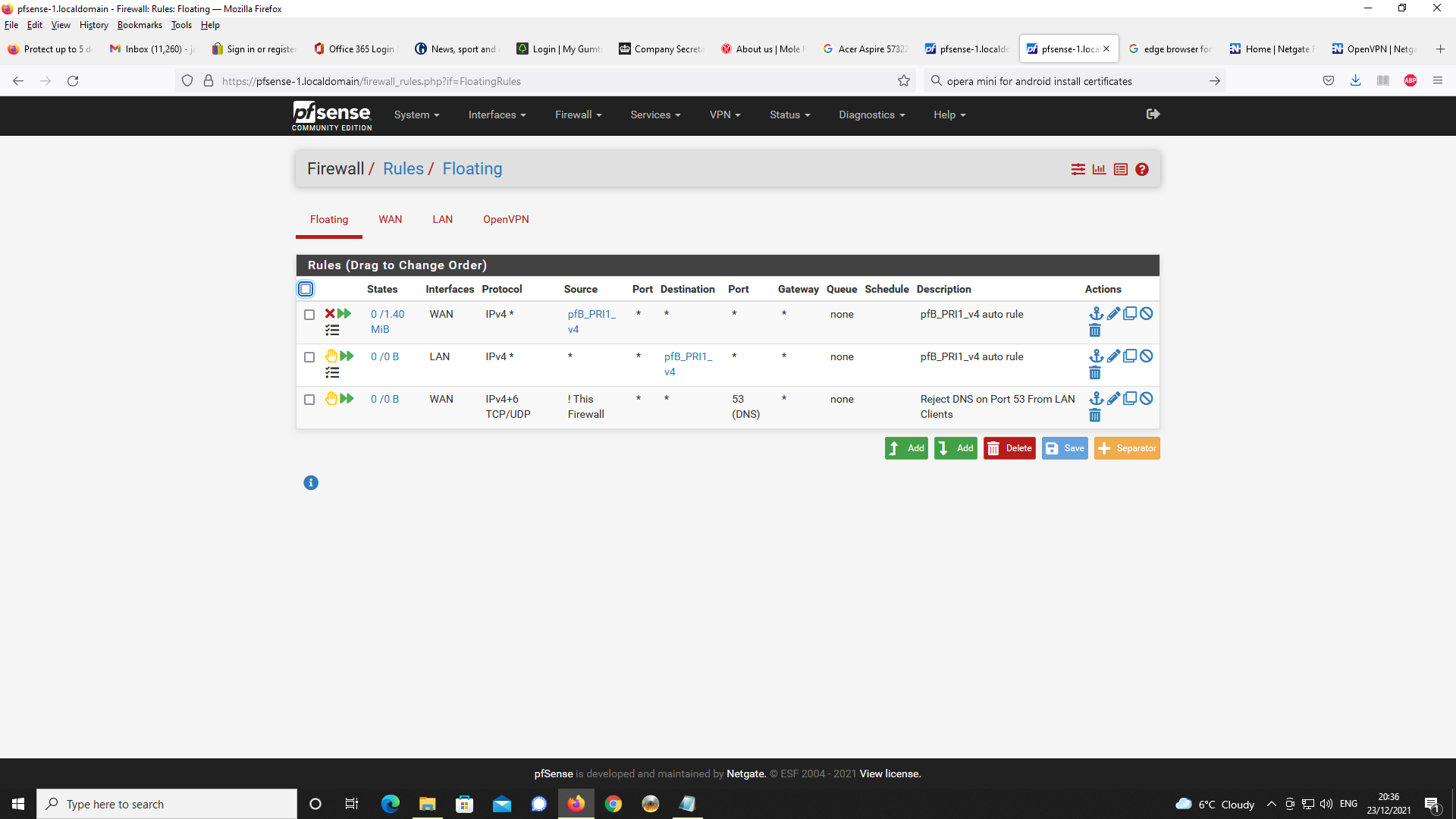
TLS), I first created a floating rule to prohibit port 53 LAN traffic going to the WAN interface.
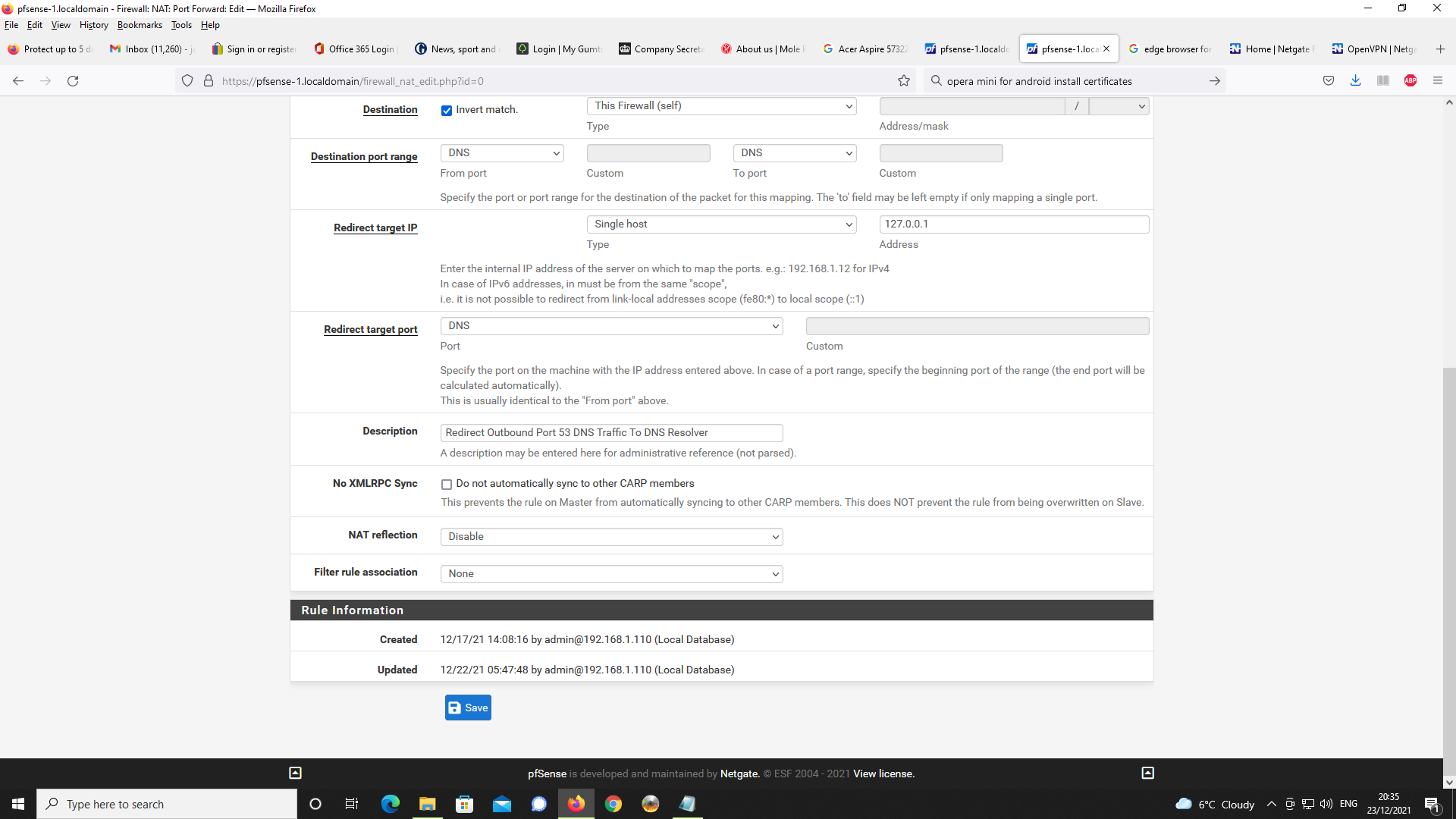
I also created a port forwarding rule that makes all port 53 traffic go to the DNS resolver.The problem I am having is that with Chrome on Android, whenever I use a FQDN to connect
to pfSense via the OpenVPN Connect client, the browser reverts to using Google servers
and comes up with a web page for the FQDN.
I checked online and read that in fact, Chrome on Android uses its own DNS Resolver with
the bowser and/or OS and this may explain the behaviour I am seeing.
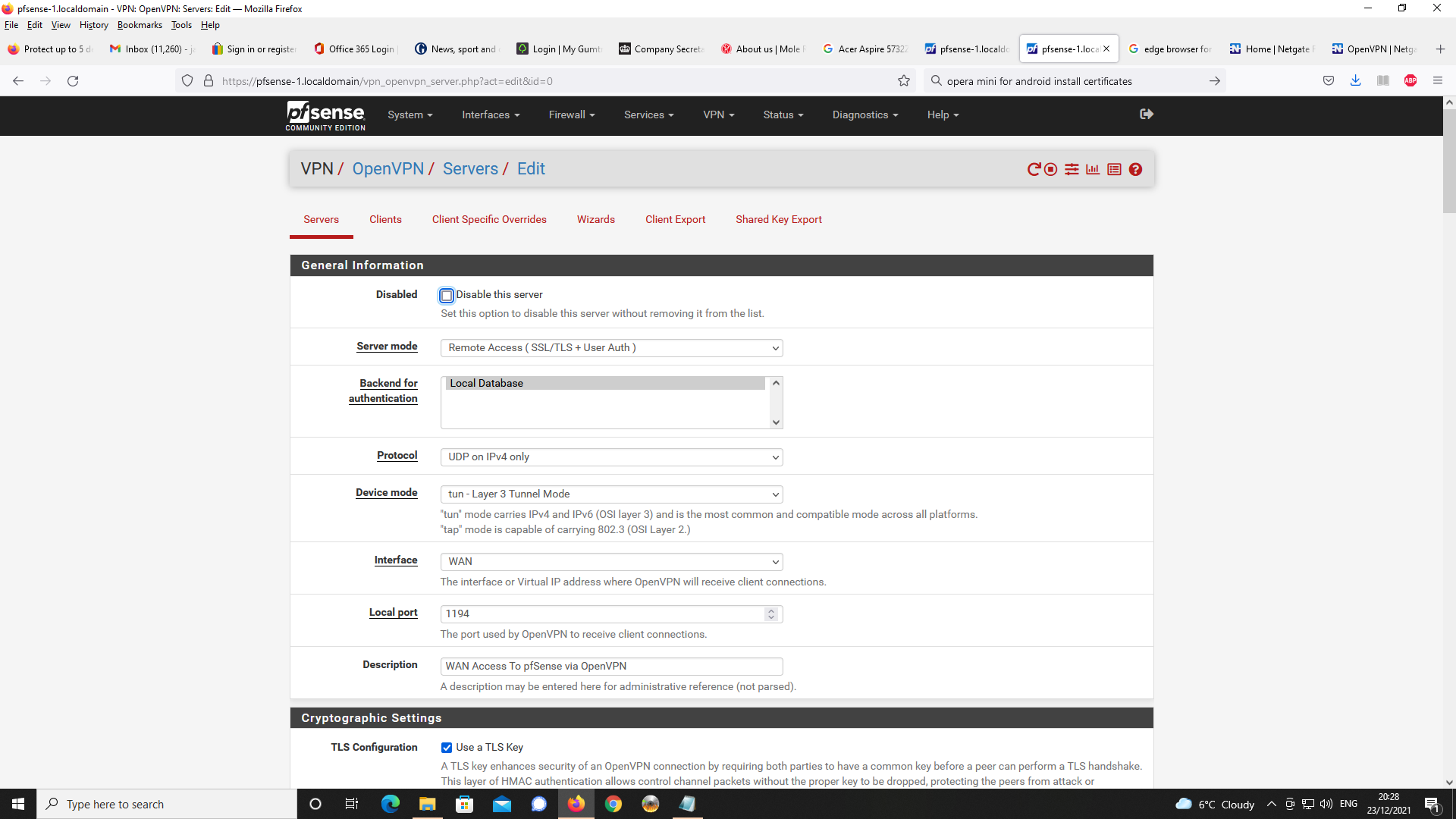
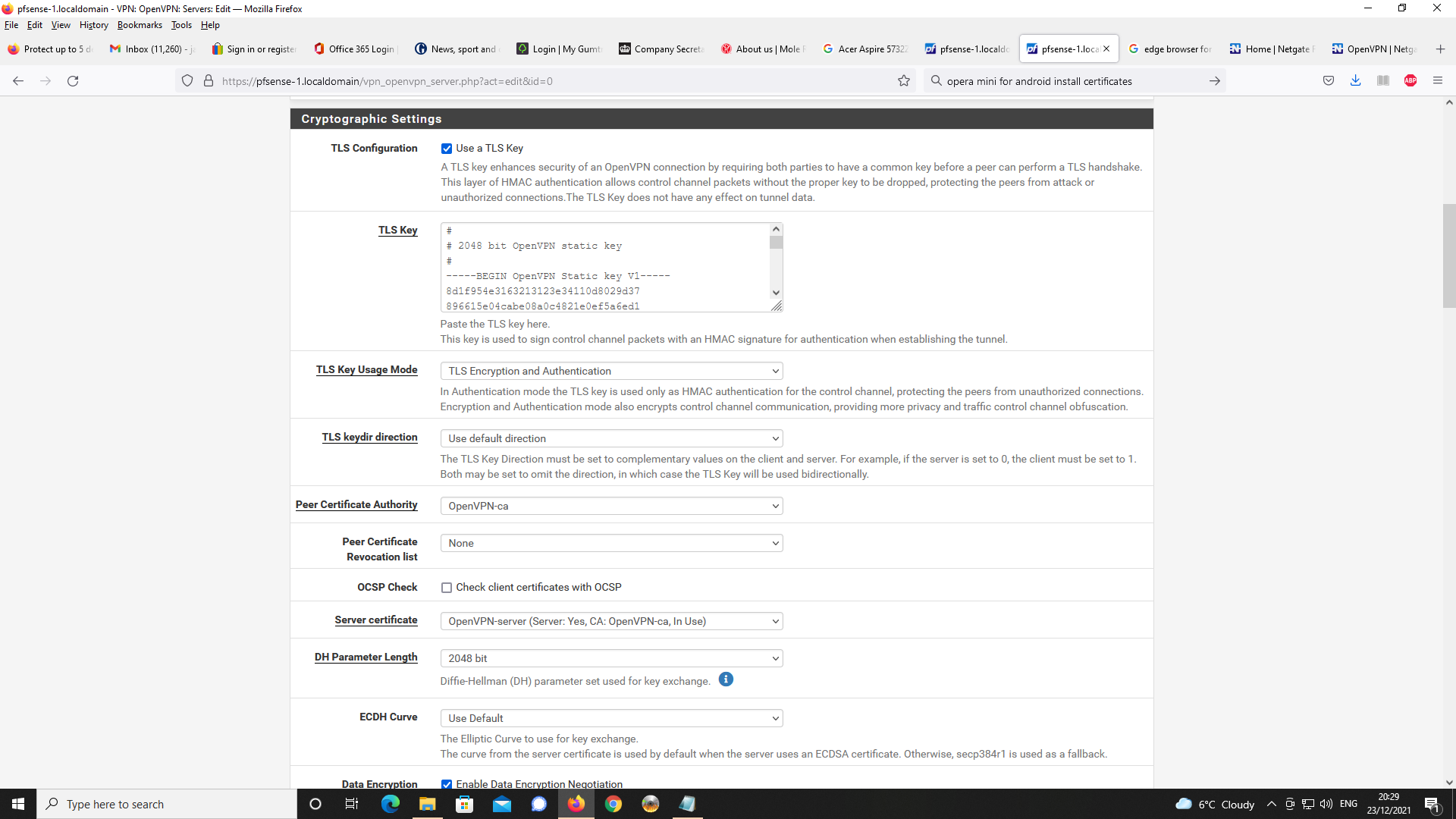
Even though the DNS domain name and IP address of 192.168.1.1 i.e. DNS resolover are specified in the OpenVPN server configuration, it is never making the request to unbound.
Can forum members confirm this is the case?I can connect via IP address and https to the WebGUI on pfsense and this works correctly.
Out of frustration, I tested Microsoft Edge browser for Android to see if I could get a better result for DNS resolution but as much as I can connect via IP address and https to the WebGUI via the OpenVPN Connect client, again, DNS resolution reverts to the Bing Search engine.
It seems I apparently, have the same problem as with Chrome on Android.I have provided details of the relevant settings on my pfsense box as below.
Any insight as to where there may be issues to address, I welcome in anticipation.
Thanks in advance for your consideration.First, in general setup
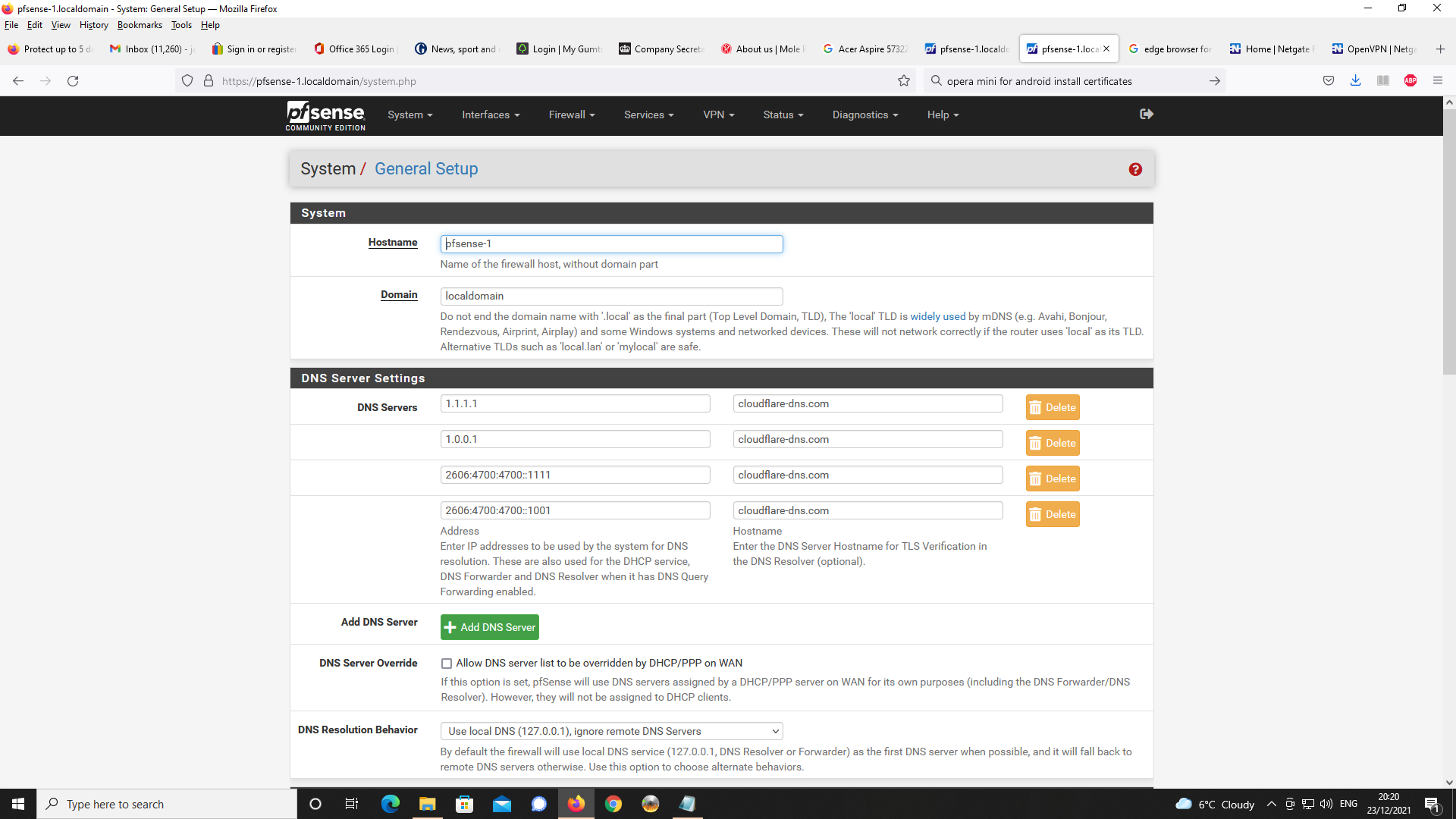
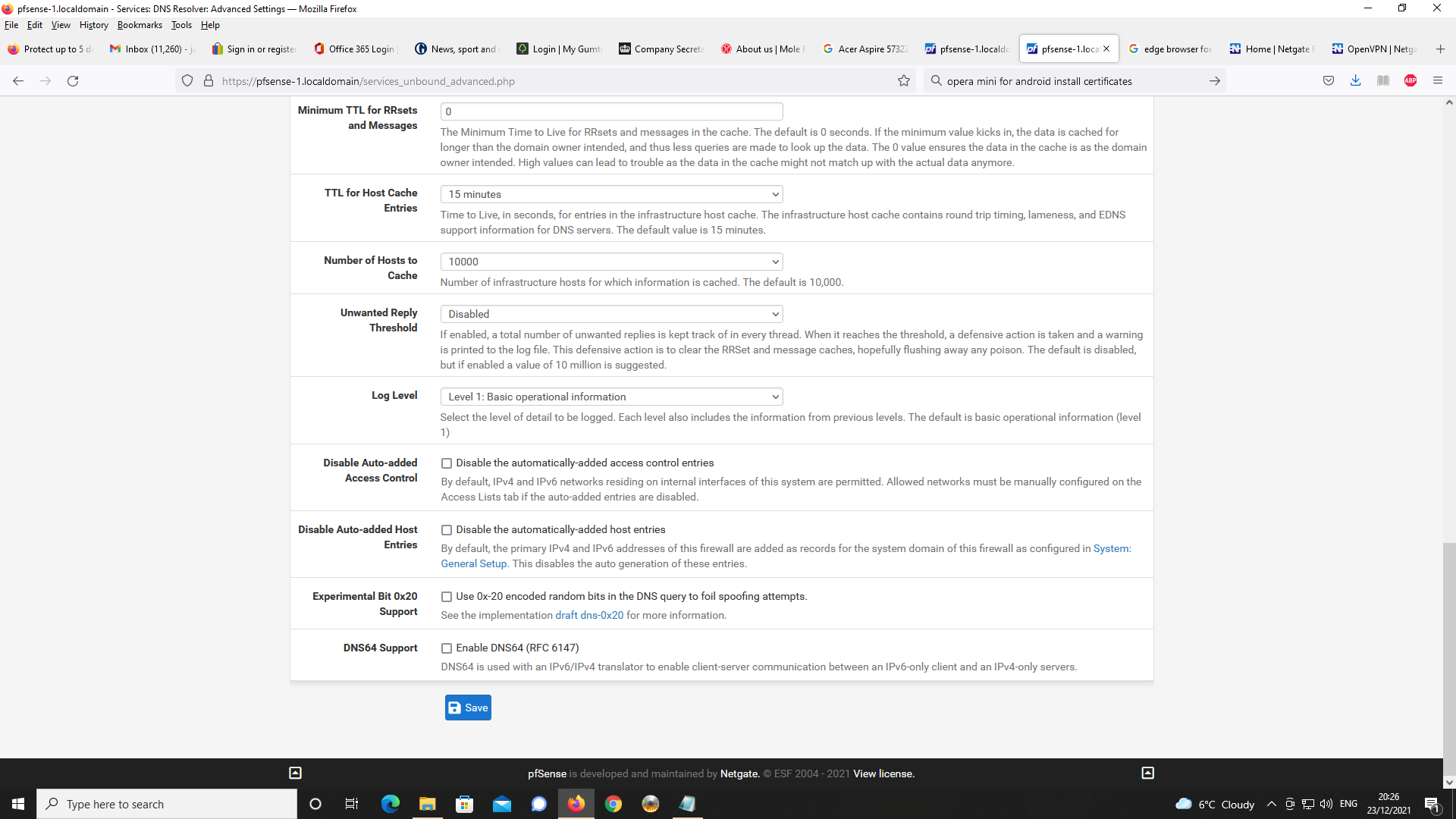
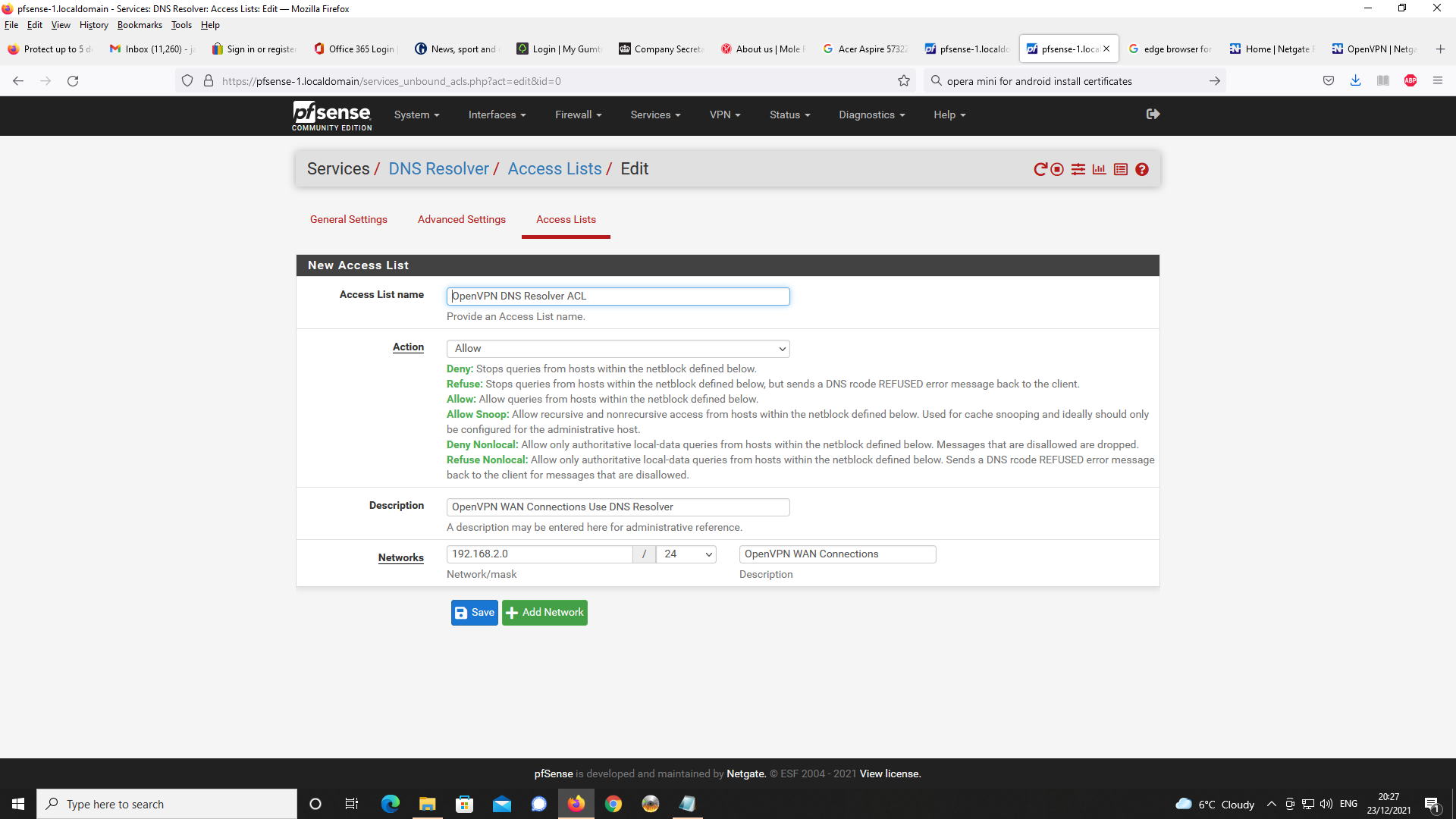
Next, DNS Resolver Setup
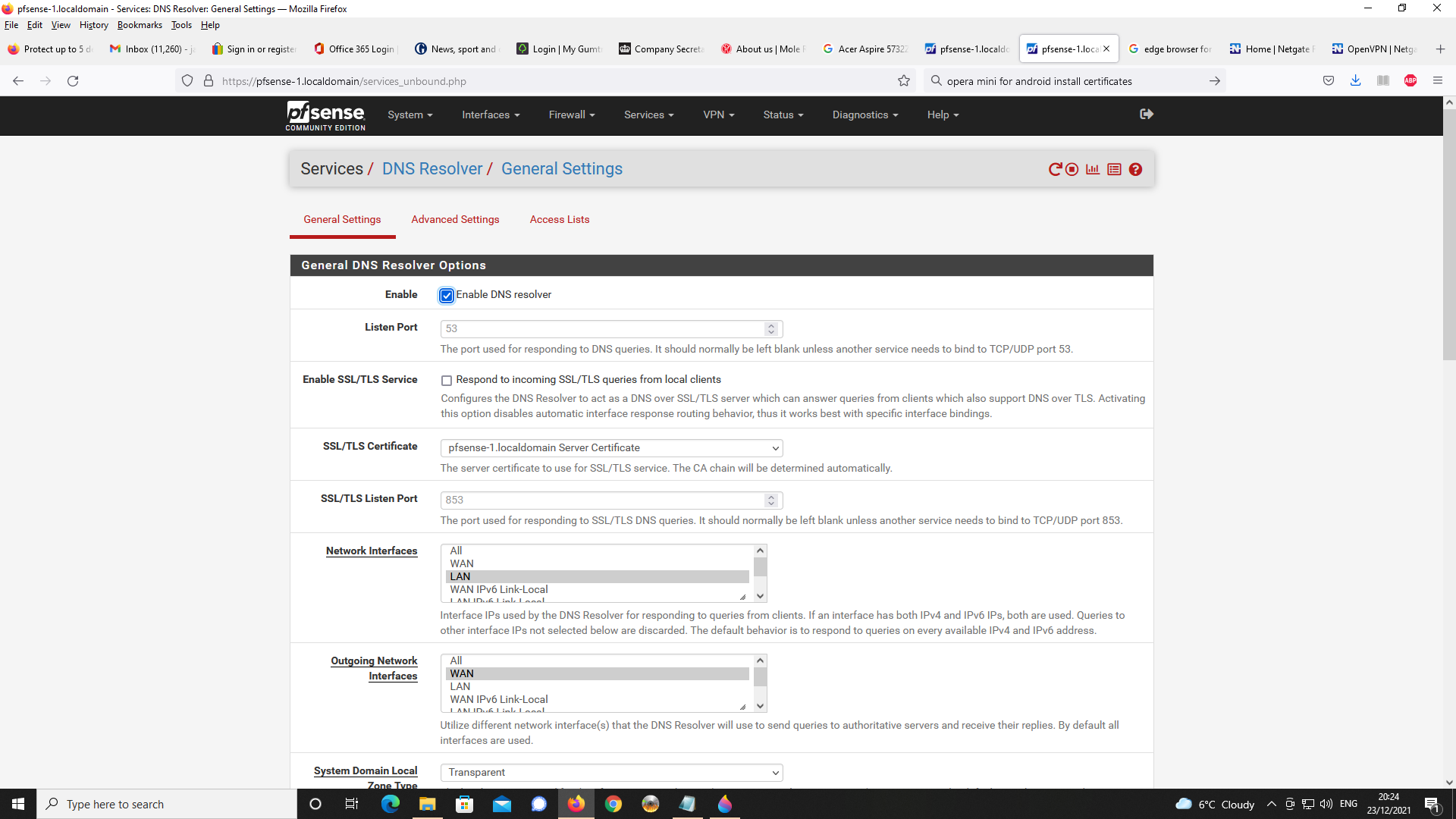
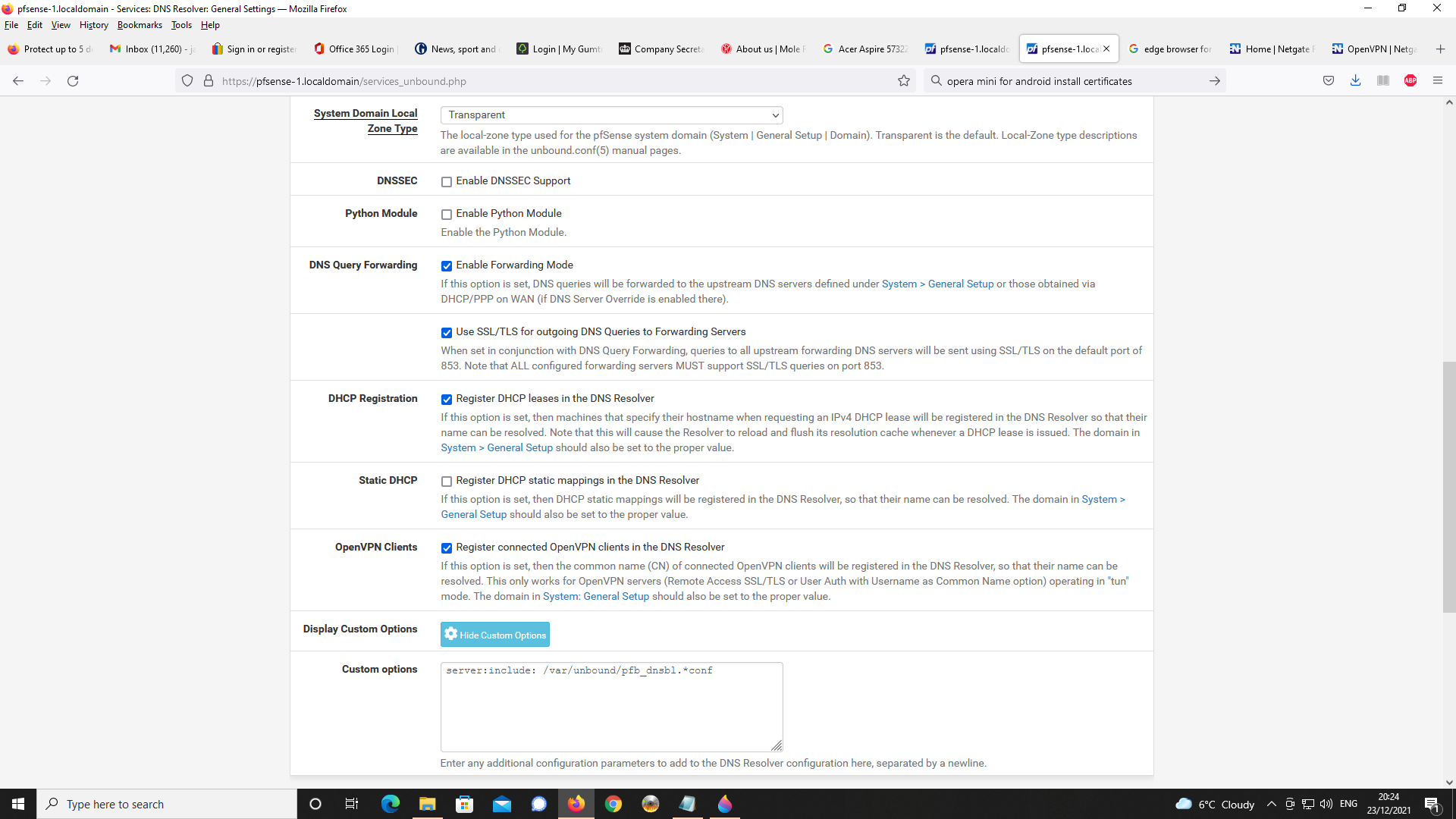
Next up, OpenVPN Server Setup
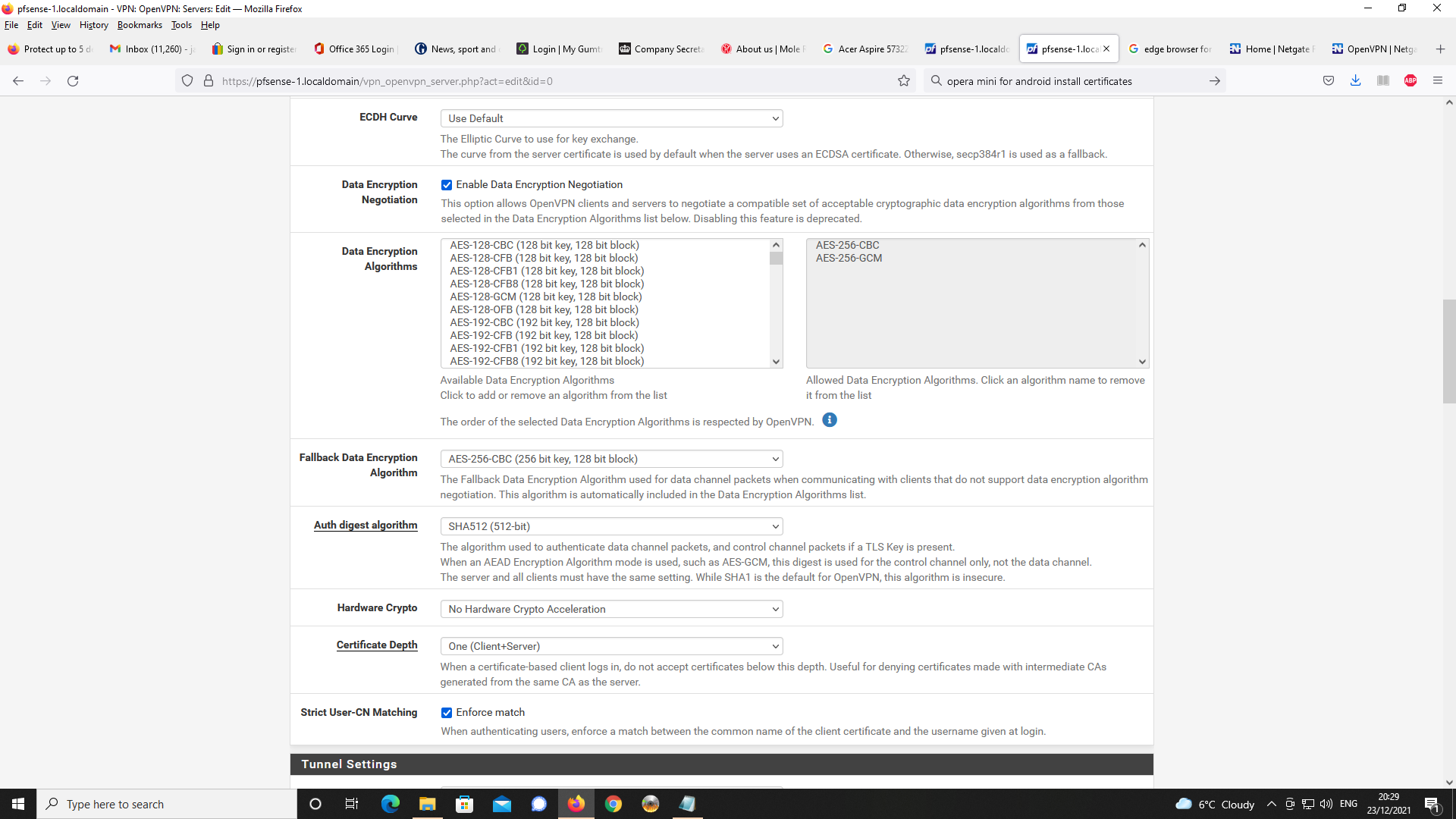
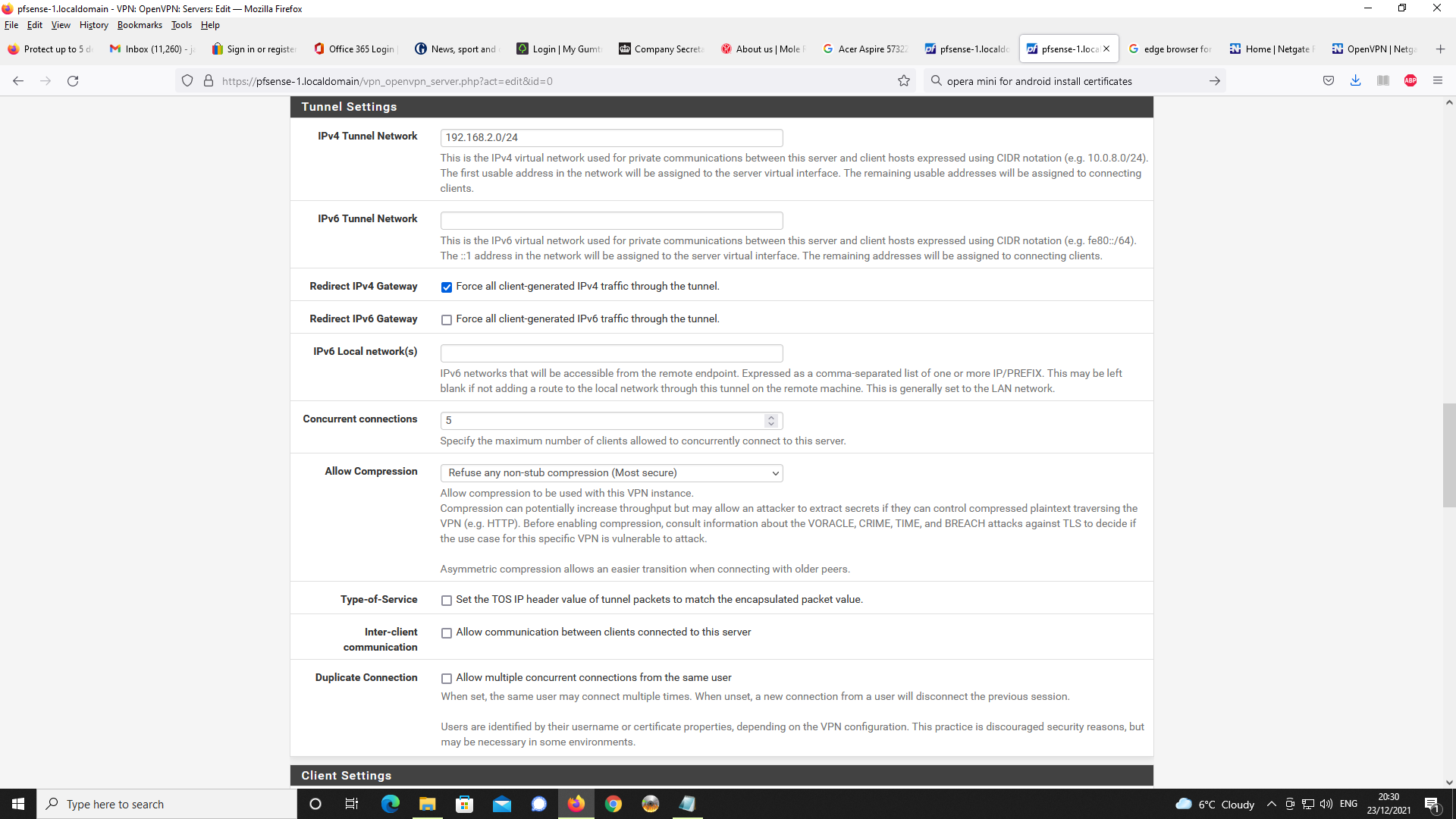
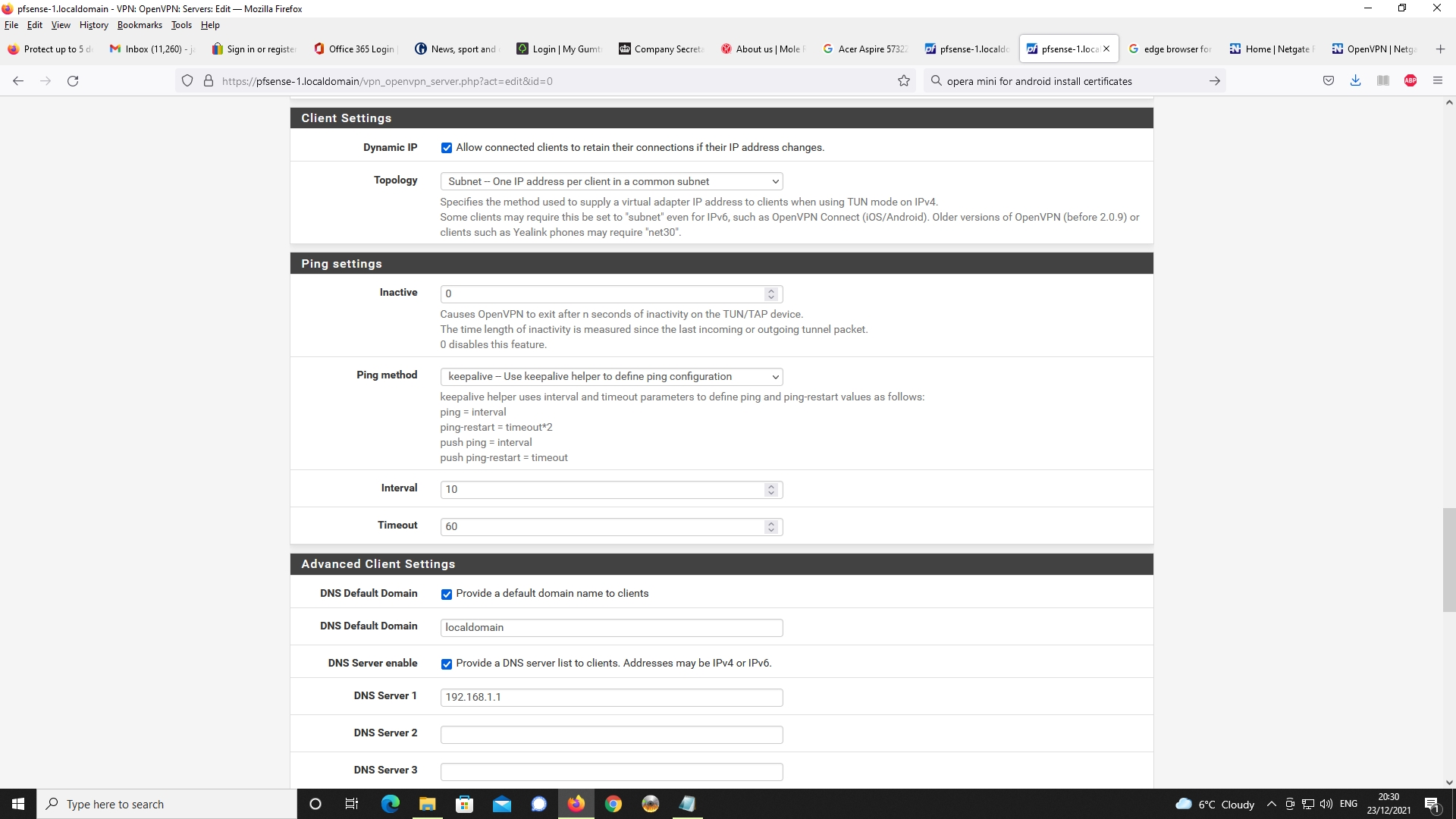
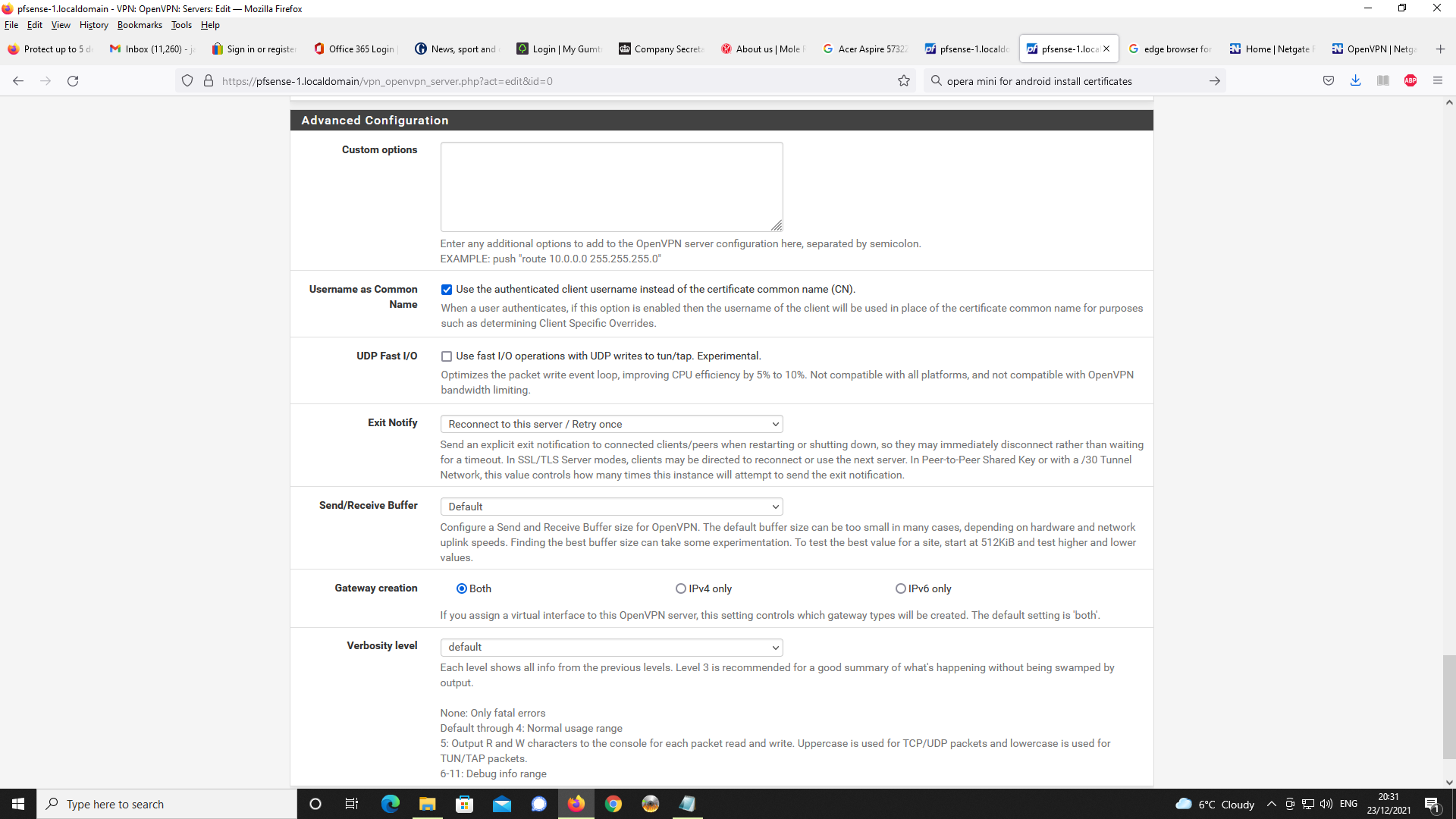
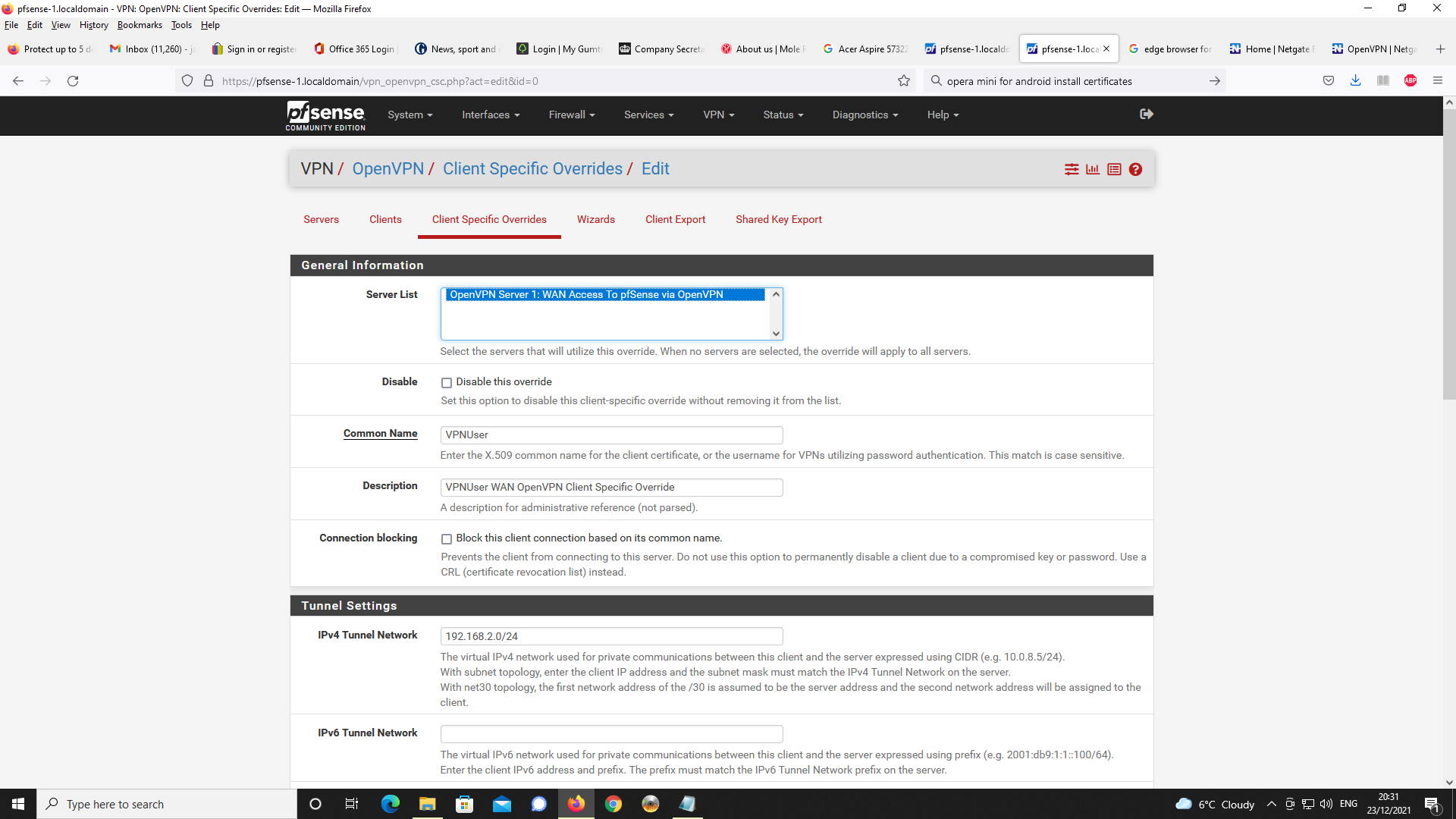
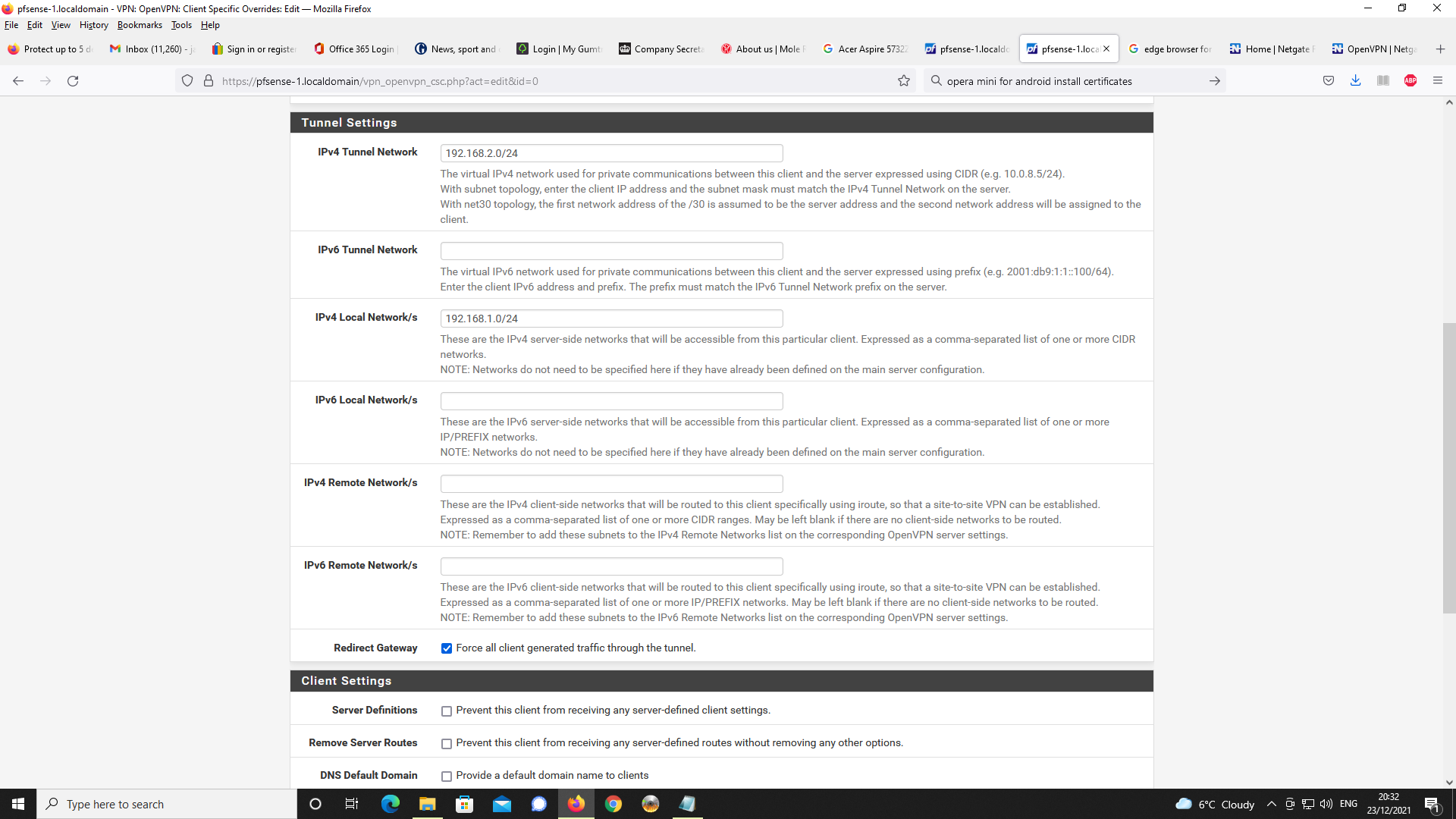
Next, Firewall rules, first NAT and port forwading
Next Floating Rule
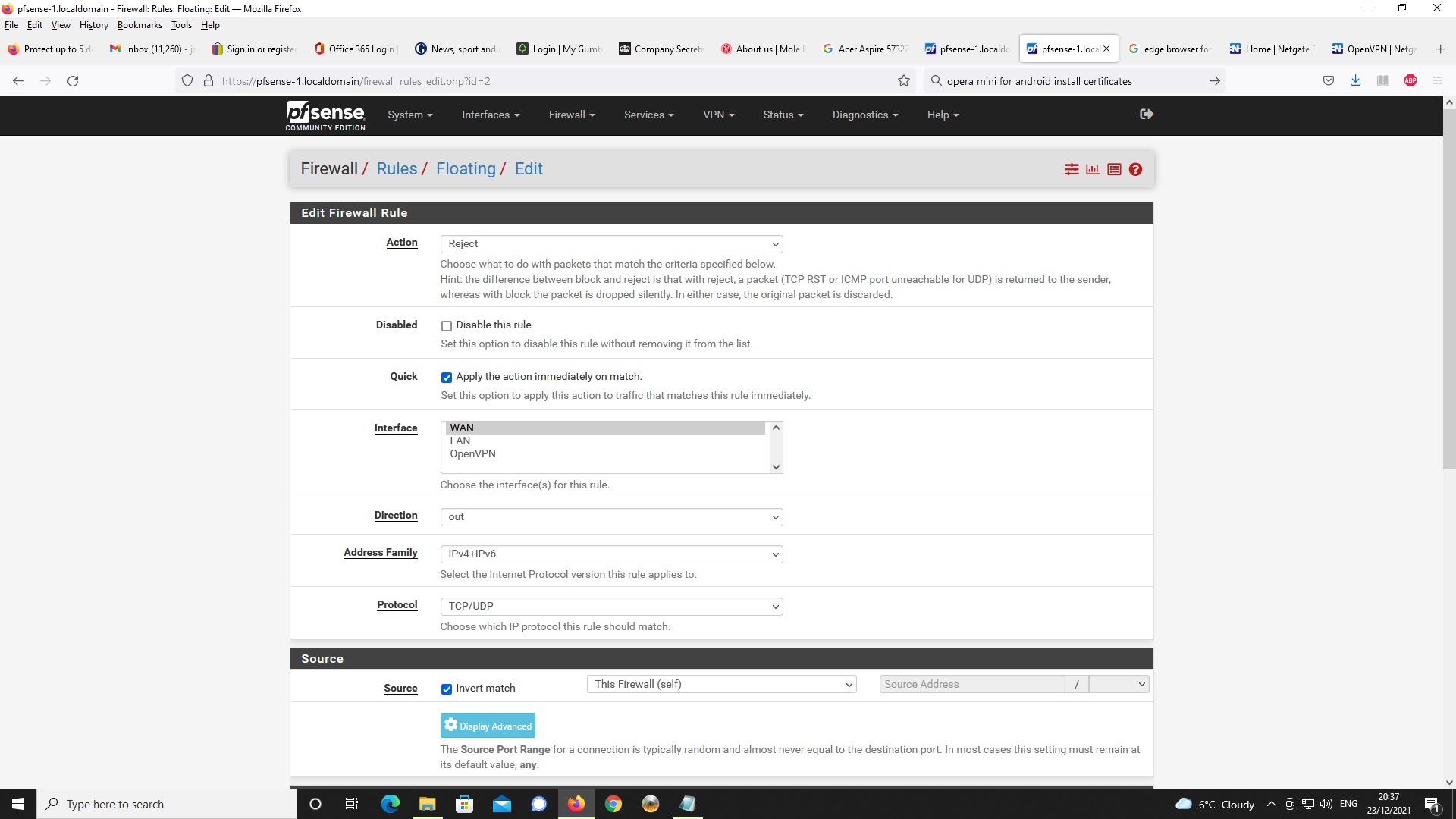
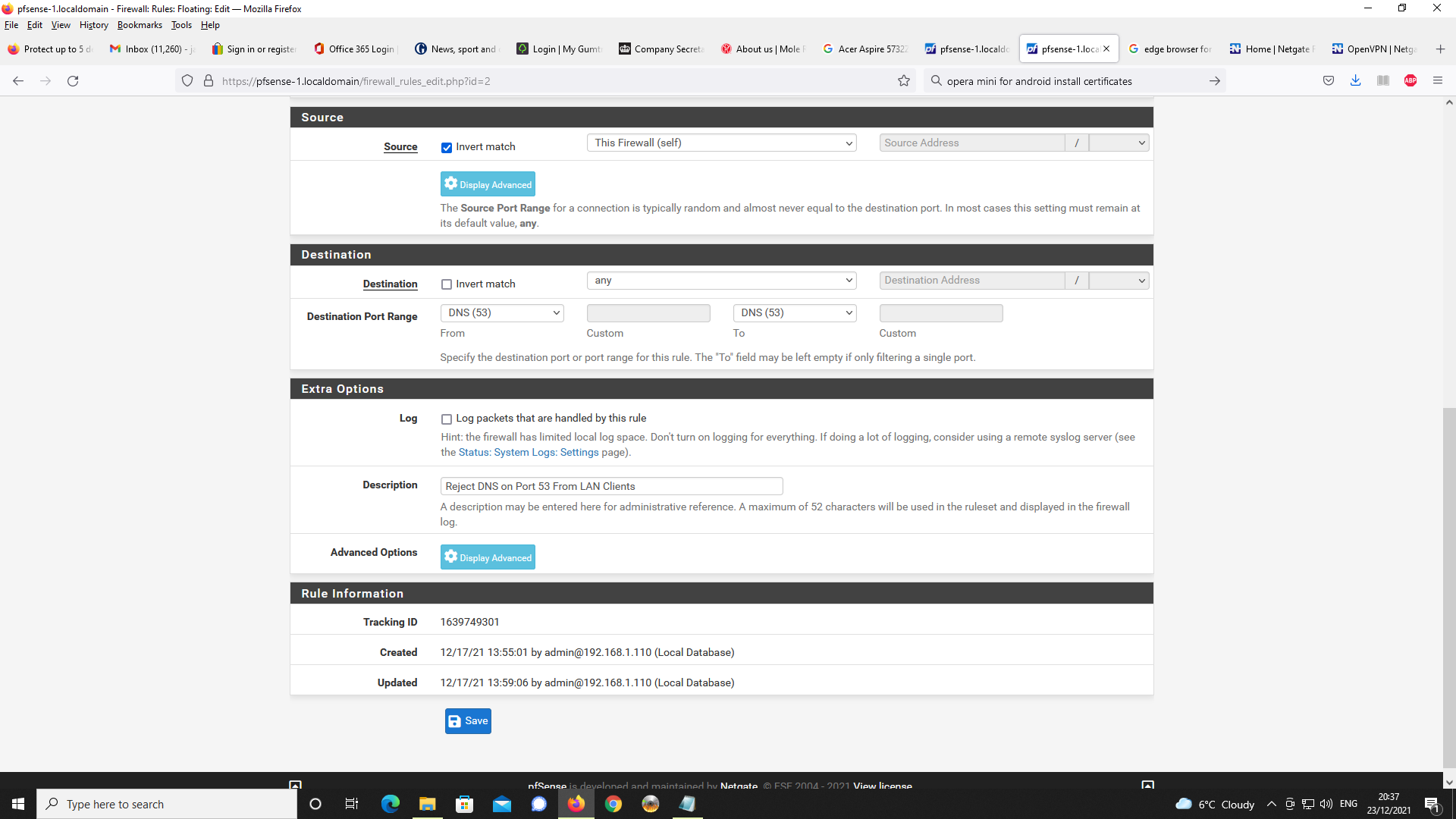
Like stated, I have used packet capture and can confirm the use of Google
servers with Chrome for Android. This is not what I configured.Can forum members, advise as to a browser which will work with Android
in order I can test to see if DNS resolver on pfsense is reachable and resolve
host names?I presently do not have a external client such as a laptop with linux, free-bsd or
windows to see if this behaviour is replicated with browsers on these platforms.Any help or insight appreciated.
-
change your dns server from 192.168.1.1 to 192.168.2.1
-
@silence
Hi, thanks for responding.
I made the change as suggested and with the FQDN pfsense-1.localdomain now Android for Chrome states it cannot find the IP for Google Servers and can't reach the site.
The webpage reports ERR_NAME_NOT_RESOLVEDDoes this mean that DNS Resolver could not resolve the FQDN or something else?
Thanks for the input.
-
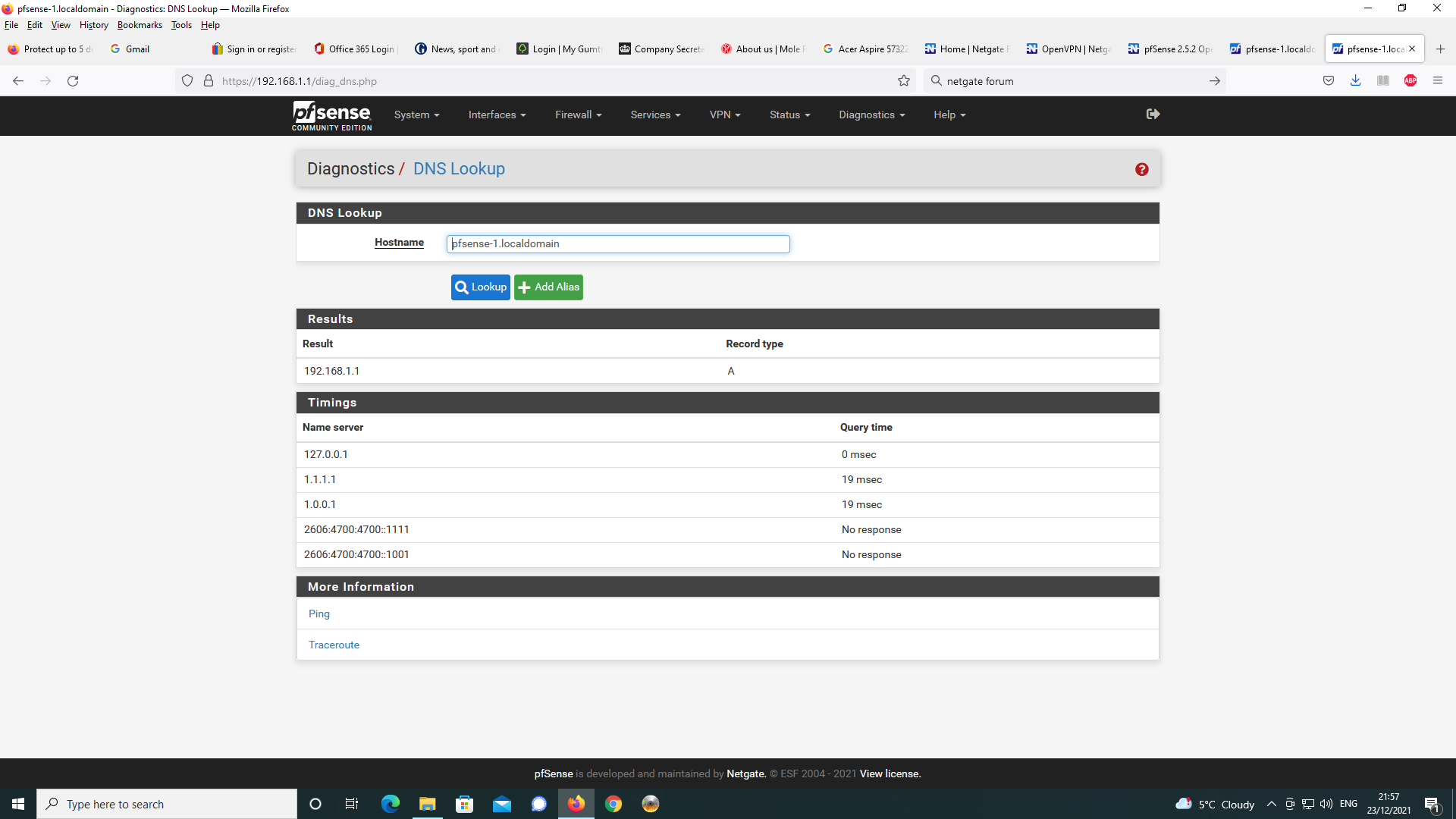
@jewilson Diagnostics> DNS Lookup
and look for pfsense-1.localdomain
-
Because this only points to the WAN interfaces. Sorry, your configuration is very confusing. If you could simply explain to me what you want to achieve, I will help you with pleasure.
-
@silence
Diags - DNS Lookup of pfsense-1.localdomain
-
-
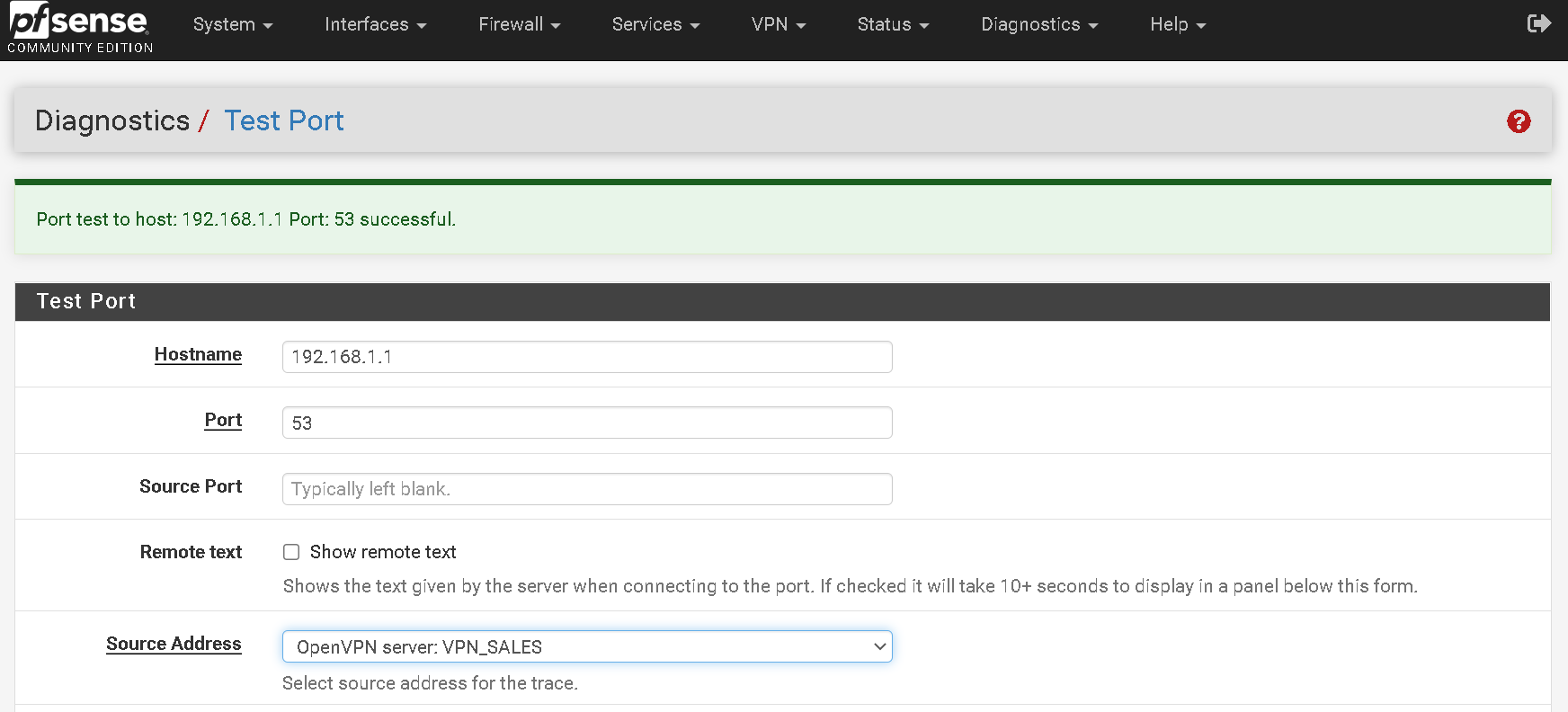
@silence
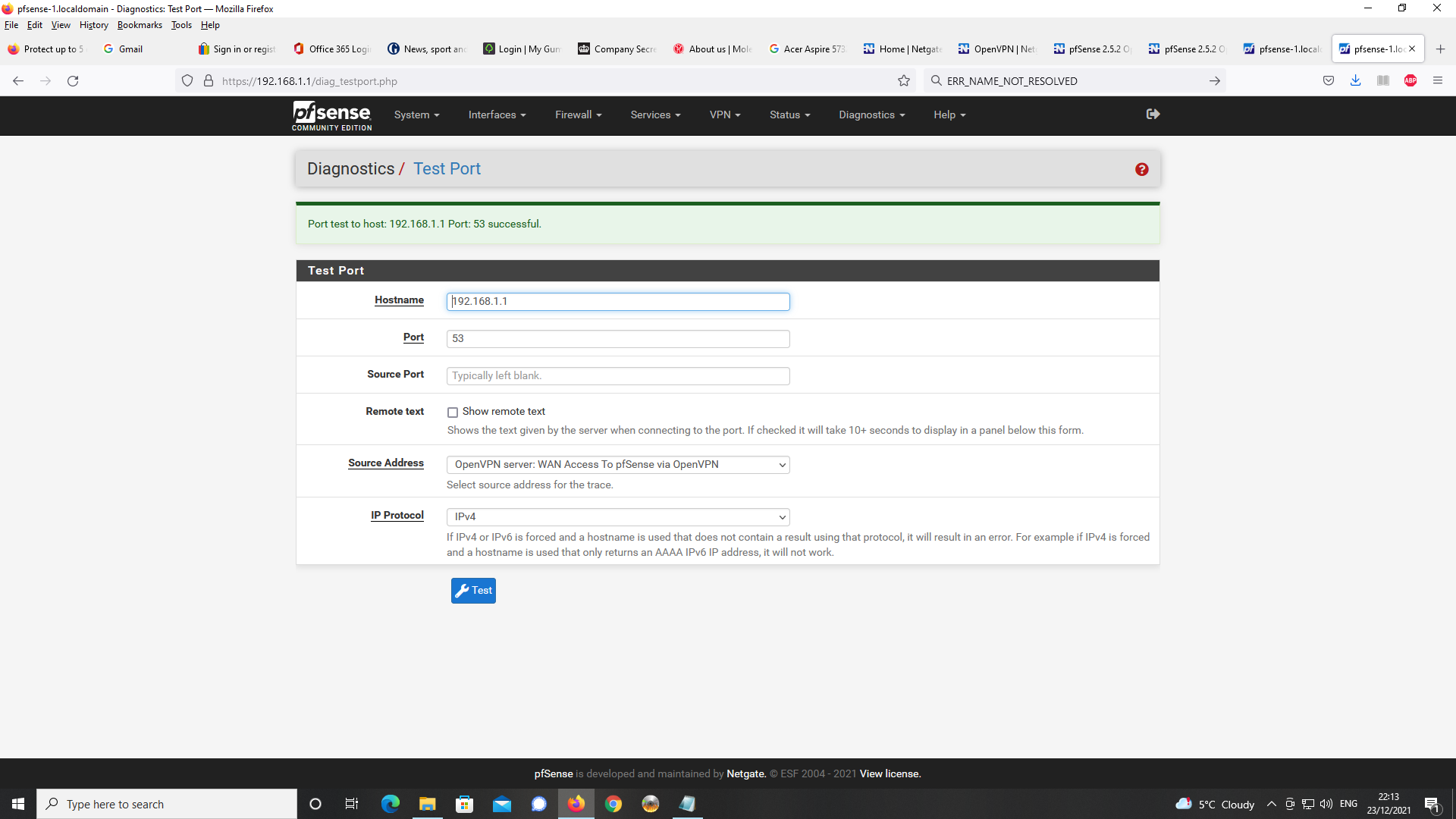
Test Port results
-
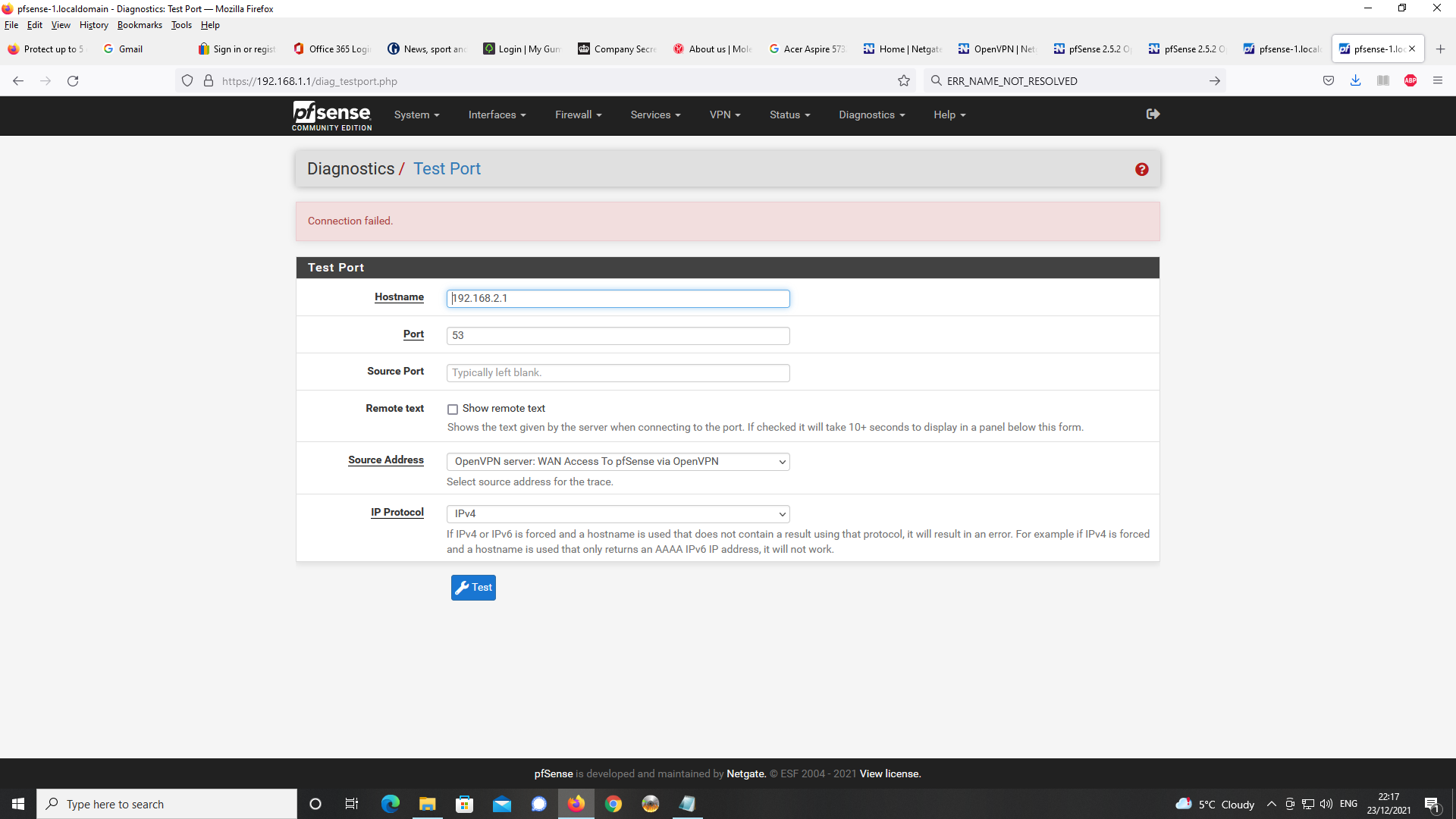
Results for test port for the DNS Server address 192.168.2.1 in OpenVPN Server config
-
here is the problem in my case if it answers
-
@jewilson said in pfSense 2.5.2 OpenVPN Server - problems getting DNS working:
On pfSense, I have set up DNS Resolver as a forwarder to cloudfare servers and have configured DNS over TLS to work for all DNS requests to the cloudflare servers. For all local DNS traffic this goes to DNS resolver as port 53 traffic. This all appears to work ok and
and you also specified that you changed the resolvers setting :
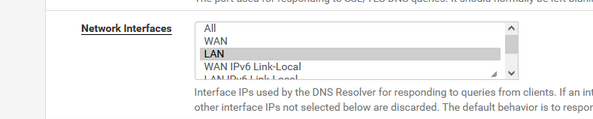
which means : only listen to LAN.
( I can't check if you checked other interface )Then :
The problem I am having is that with Chrome on Android, whenever I use a FQDN to connect
to pfSense via the OpenVPN Connect client, the browser reverts to using Google serversbecause there is no DNS server available at the OpenVPN server port.
The client can't try out "something else", and will default to known DNS servers. No surprise that a chrome or Android device goes to "8.8.8.8".This test confirms it :
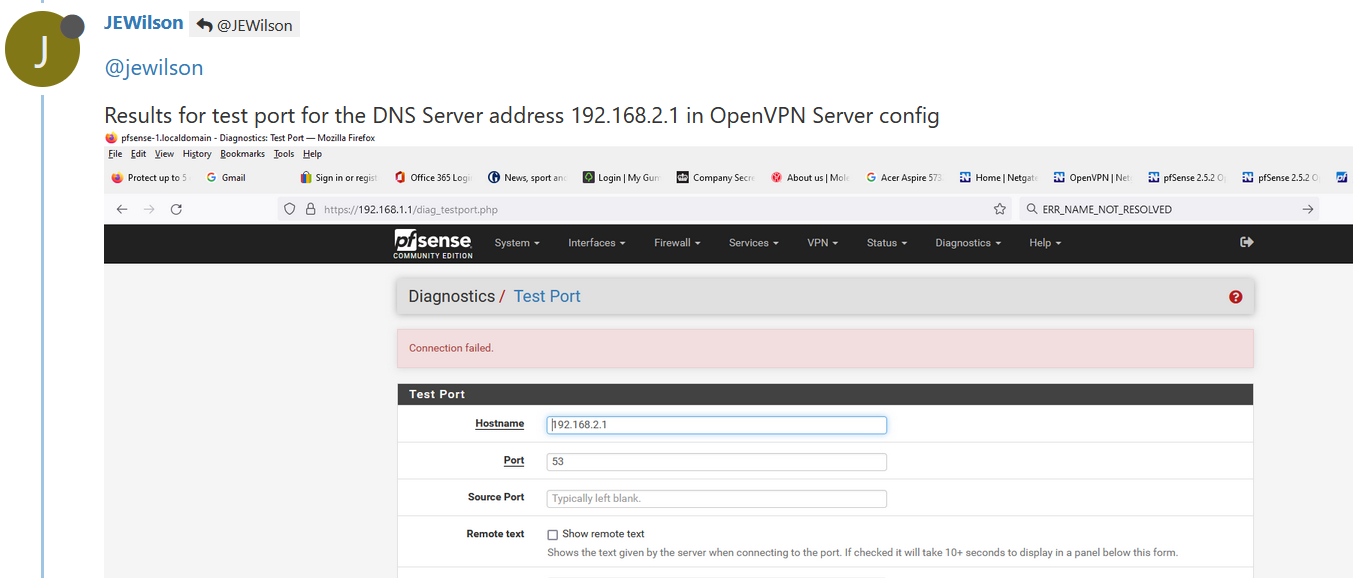
an OpenVPN can't connect to "192.168.2.1" (the base OpenVPN network) as the unbound, the resolver, isn't listing on that interface / address.
I propose the default value :
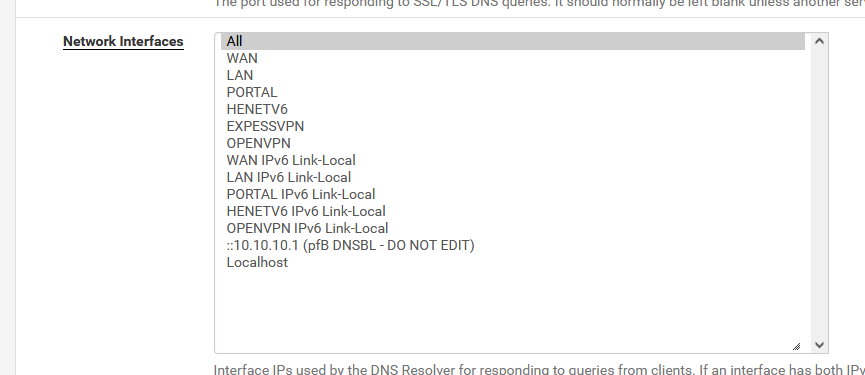
as it works soooooooooo good.
or, at least, include the local networks :(my case ) :

and now you can remove the "DNS is here 192.168.1.1" in the OpenVPN server settings page.
Firewall :
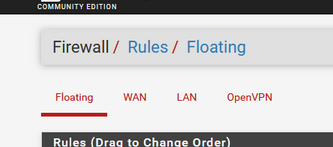
LAN traffic enter the firewall on the LAN interface using LAN firewall rules.
Right ? Right !WAN traffic enter the firewall on the WAN interface using WAN firewall rules.
Right of course. Normally, none or very few rules are present on the WAN interface. You have probably a OpenVPN rule there. It permits openvpn clients from the 'outside' to connect to the OpenVPN server.And there is a OpenVPN interface :
OpenVPN (server) traffic enter the firewall on the OpenVPN (server) interface using OpenVPN (server) firewall rules.
You checked ? Is there a firewall rule ? Normally, there is as the OpenVPN wizard creates one.
It should pass, amongst others, UDP traffic., so DNS traffic can come in. -
Thanks for responding.
Y, there is a WAN rule for OpenVPN and there is a rule under the setting for OpenVPN.I have set the DNS server to 192.168.2.1 as advised in VPN server settings.
When I try to connect with Chrome for Android with the FQDN pfsense-1.localdomain,
the webpage reports the site cannot be reached and is unable to resolve.As shown below, I did a packet capture as per the supplied settings and then did an
analysis with Wireshark.
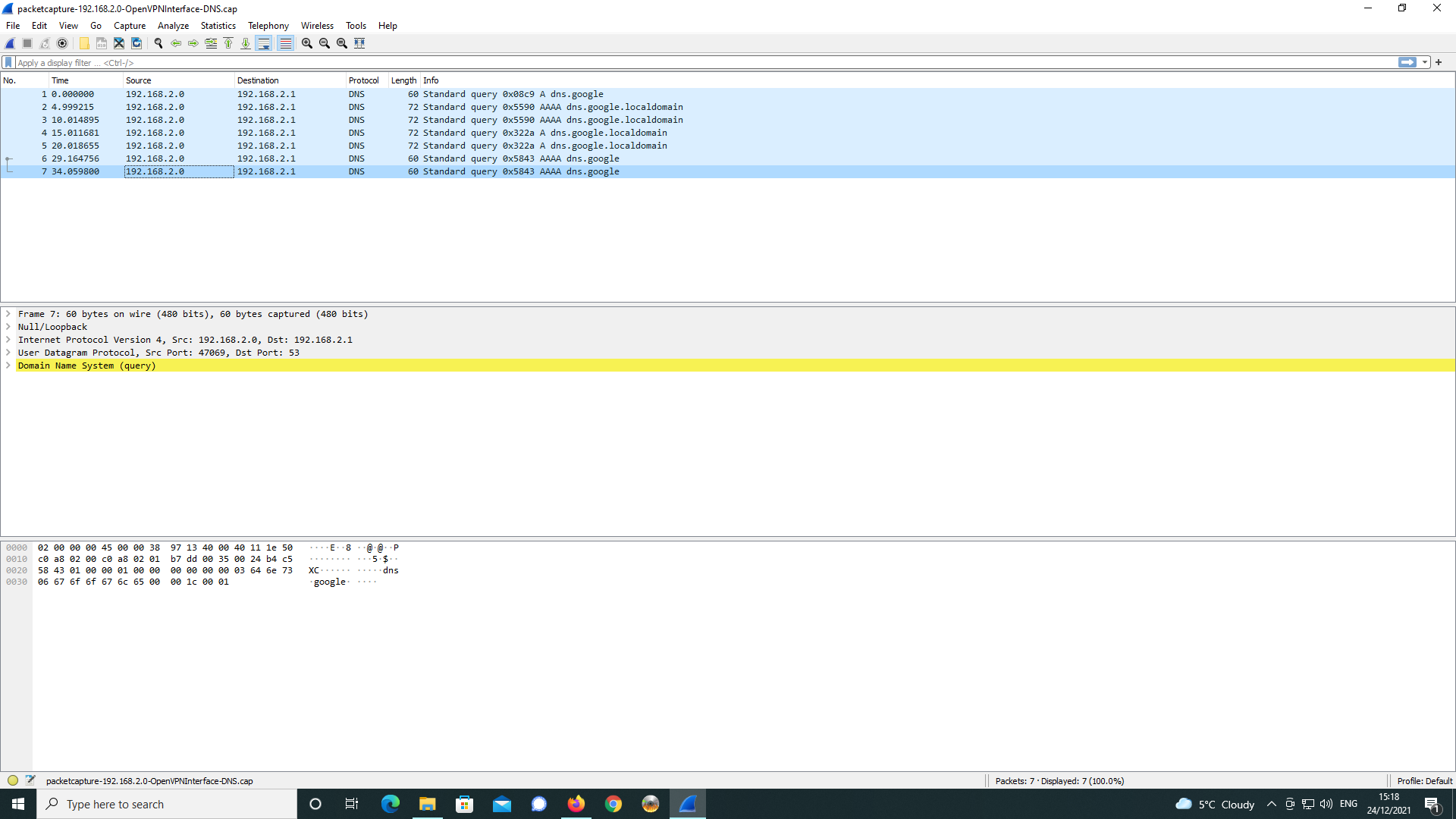
As can be seen, google is trying to resolve the DNS request despite the DNS
server setting being sent to 192.168.2.1 in the OpenVPN server config.
This is something that I think Chrome for Android is doing and it is not
the settings specified for the OpenVPN Connect client on Android that I
am using.I tried setting off Secure DNS in Chrome for Android as well as disabling
the server dns.google which uses DNS over TLS.
This made no difference with the same packet capture settings as prior to and
an analysis in Wireshark as below.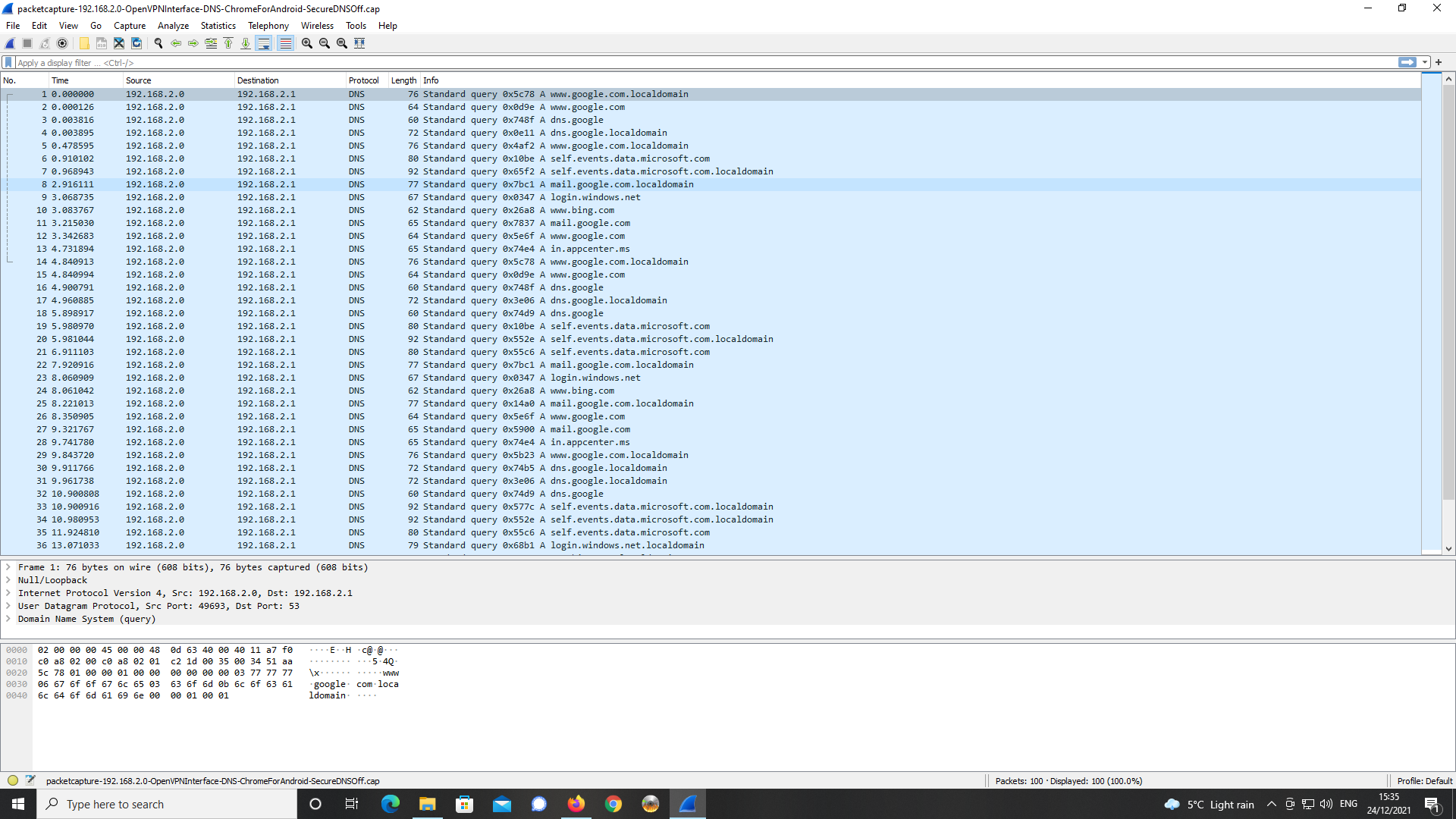
Again, a number of external DNS servers are being queried in order to resolve
the FQDN.The DNS server specified at 192.168.2.1 is not listening on port 53 but it is listening
on port 80 and port 443. -
Changed the DNS Server in the OpenVPN Server config back to 192.168.1.1.
Having checked with Diags -> Test Port on pfSense, I know this address is listening on
port 53, port 80 and port 443.Downloaded Opera For Android and browsed to https://pfsense-1.localdomain as FQDN.
Unlike with Chrome For Android and other chromium based browsers such as Microsoft
Edge, Opera will, it appears resolve the FQDN but warns, the connection is untrusted.
That would be correct as I have not installed the SSL/TLS certificate for the https connection to
the pfsense WebGUI into Opera for Android.Having checked settings for Opera, there does not appear to be a means to install the
relevant certificate into the bowser.
The CA chain is installed in the Android Certificate Store and whereas, chromium based
browsers look to this certficate store on Android, Opera for Android does not appear to.Will try next with Firefox with the DNS server set to 192.168.1.1.
-
Firefox for Android will not resolve the FQDN even over http on port 80 with the DNS Server
setting for the OpenVPN Server config set to 192.168.1.1.
Reports cannot find the site.Appears this problem may be browser related issues on Android and how DNS is resolved.
-
Further investigation with Opera for Android, finds that as above the FQDN will
resolve to port 80 only with the Android OS settings for Private DNS set to off.
I'm using Android 9.
Appears Opera for Android does not have the means to install certificates but
that the desktop version for Linux or Windows does.As part of further testing, will dl OpenVPN Connect for Windows 7 on my notebook
and test with Chrome and Firefox. I will set up my Android mobile as a hotspot and
connect via WiFi on my notebook to see what results I get with DNS. -
As below, I did a packet capture on the DNS resolution of the FQDN in the Opera for
Android browser and analysed with Wireshark.
The query and response are highlighted in the Wireshark screen capture.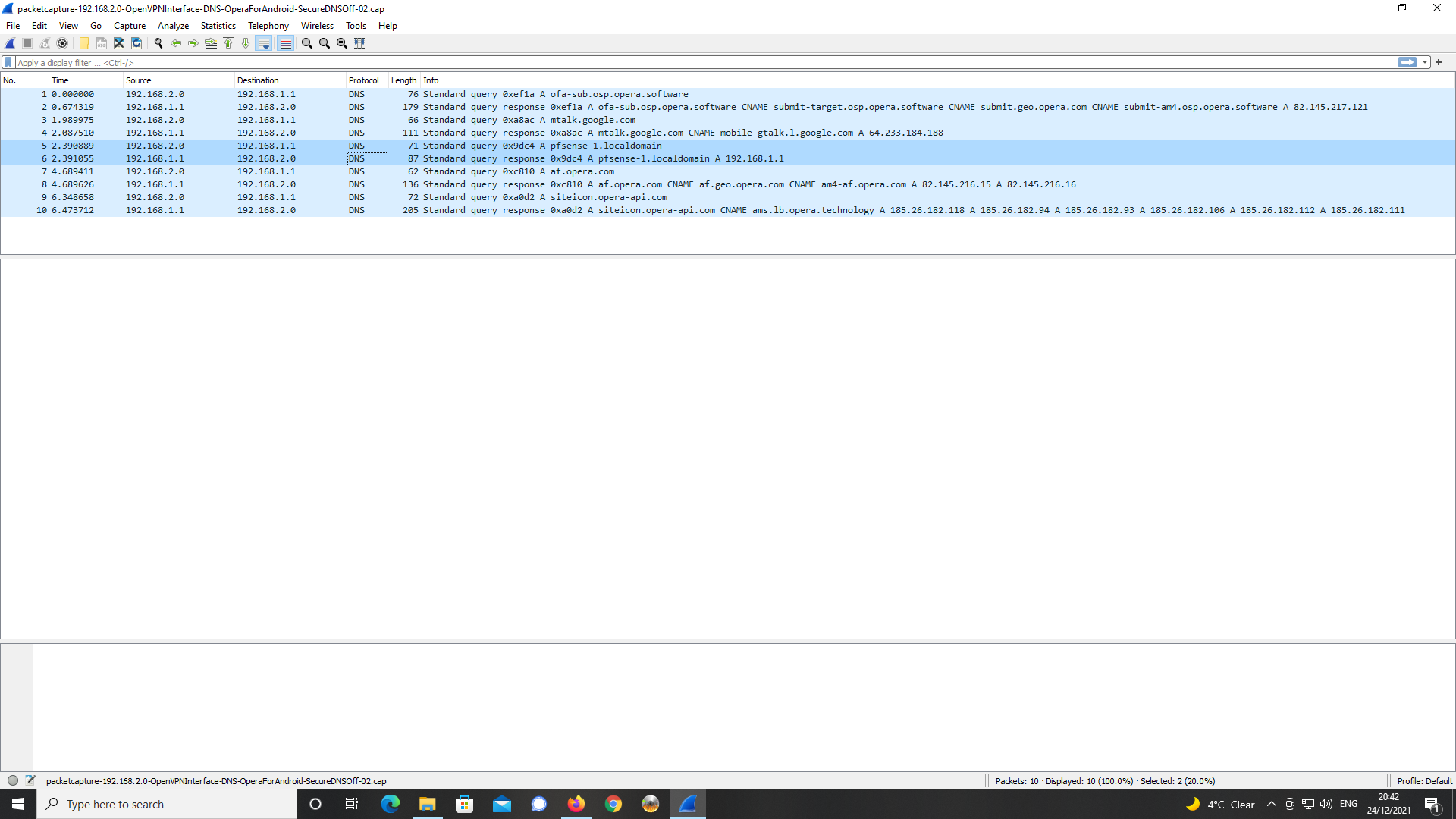
-
Did some further testing with a IBM Thinkpad T60 notebook running Windows
7 Pro SP1.Note, my DNS server in the pfsense OpenVPN server config is set to 192.168.1.1.
I updated Chrome for Windows, dl'd the relevant OpenVPN connect client for the OS.
Exported the certificate chain from the Windows 10 desktop certficate store and
imported these into the certificate store on Win7 Pro SP1.
Exported the OpenVPN profile from OpenVPN Server for Windows 7.
Installed OpenVPN Connect on the laptop and imported the profile.
Configured my Android 9 mobile handset as a WiFi hotspot and connected
the WiFi on my notepad to this for the purposes of making an inbound VPN
connection to my pfSense appliance via mobile 4G broadband.This all worked ok and the OpenVPN Connect client connected ok.
I used Chrome browser for Windows to load https://pfsense-1.localdomain
and the name was resolved and the SSL/TLS certificate supported the
https port 443 connection to the pfSense webGUI.It would appear given this finding with the chrome desktop browser version
for Windows, being it works with DNS as expected with no apparent issues,
the problems I was experiencing with Android and a number of Android
browsers were/are the root cause of my issues.Hopefully, forum members can use these findings as a basis for their own
work and testing on mobile VPN clients as is relevant to the manner of the OpenVPN
server config I have set up. -
Like you, I launched a packet capture on the OpenVPN server interface :
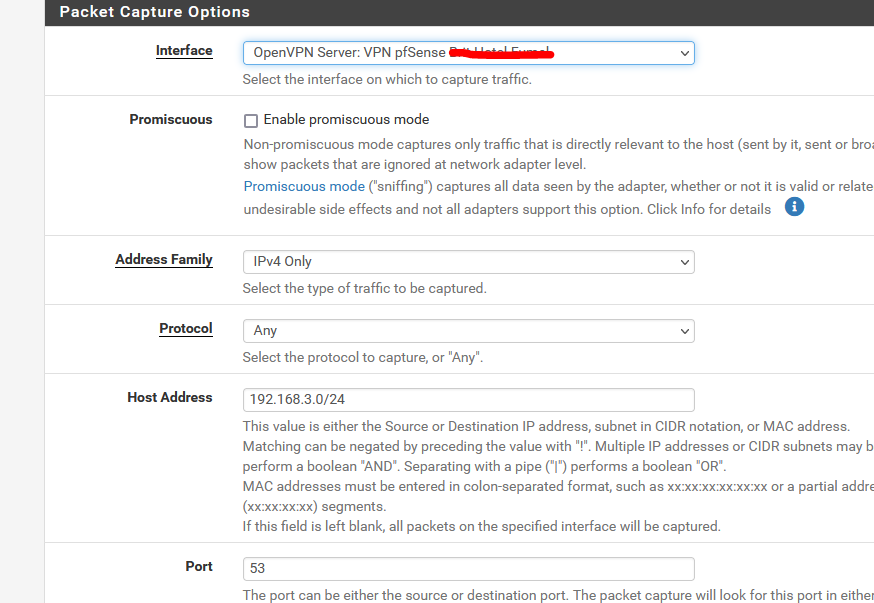
Important settings :
My OpenVPN network : 192.168.3.0/24 and the port : 53.
I should see mostly DNS traffic.And I did :
08:19:42.573451 IP 192.168.3.2.56732 > 192.168.3.1.53: UDP, length 37 08:19:42.573506 IP 192.168.3.2.50036 > 192.168.3.1.53: UDP, length 37 08:19:42.573550 IP 192.168.3.2.57791 > 192.168.3.1.53: UDP, length 53 08:19:42.573577 IP 192.168.3.2.54751 > 192.168.3.1.53: UDP, length 53 08:19:42.573602 IP 192.168.3.2.55796 > 192.168.3.1.53: UDP, length 27 08:19:42.573626 IP 192.168.3.2.59088 > 192.168.3.1.53: UDP, length 27 08:19:42.575260 IP 192.168.3.1.53 > 192.168.3.2.55796: UDP, length 27 08:19:42.601370 IP 192.168.3.1.53 > 192.168.3.2.59088: UDP, length 43 08:19:42.603502 IP 192.168.3.1.53 > 192.168.3.2.54751: UDP, length 128 08:19:42.629427 IP 192.168.3.1.53 > 192.168.3.2.57791: UDP, length 128 08:19:42.660713 IP 192.168.3.1.53 > 192.168.3.2.50036: UDP, length 133 08:19:42.687205 IP 192.168.3.1.53 > 192.168.3.2.56732: UDP, length 149Only 2 IP's are listed :
192.168.3.1 = The OpenVPN interface - unbound is instructed to listen on port 53.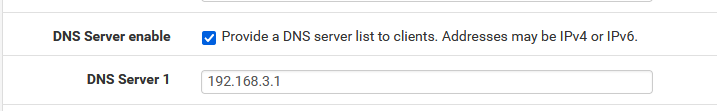
192.168.3.2 = my device, an iPhone.
You can clearly see that there are only 2 IP's implicated in the DNS traffic.For some reason, your logs show 192.168.2.0 as a source or destination IP.
That's impossible. "dot zero" can't be a source or destination, except when broadcasting.The device you use as an OpenVPN client really obtains 192.168.2.0 as an IP ?
-
Hi,
Thnaks for responding.
Y, you are right on the matter of 192.168.2.0. This is the broadcast network number used for, e.g. with a DHCP allocated scope such as mine where my VPN network is 192.168.2.0/24.
OpenVPN connect does in fact in use 192.168.2.0 for the client as this is what it gives me!
The VPN gateway is 192.168.2.1.
I think this is what OpenVPN does do albeit it seems at heads with using IP address routing
and network practice - very odd.You appear to be using Apple iOS, my problems came from Android and using Android browsers.
-
@jewilson said in pfSense 2.5.2 OpenVPN Server - problems getting DNS working:
OpenVPN connect does in fact in use 192.168.2.0 for the client as this is what it gives me!
The VPN gateway is 192.168.2.1.Exact.
I use 192.168.3.1 as the VPN gateway. (192.168.3.0/24 is the network setting)
When I connect my VPN client device, it receives the first one available : 192.168.3.2Does your device receive 192.168.2.0 ?
@jewilson said in pfSense 2.5.2 OpenVPN Server - problems getting DNS working:
Apple iOS, my problems came from Android and using Android browser
We all use the OpenVppN Connect app, right ?
The OS doesn't matter.
192.168.2.0 is not a usable IP DHCP server or the OpenVPN server can hand out to a device - IMHO.