Interface range setup
-
@jt40 said in Interface range setup:
VLAN ID 20 TAGGED on port 2
UPLINK on port 15, no TAGS.I have no idea what your doing... What is port 15? Is that the port connected to pfsense lan.. What is port 2, and why are you tagging it
I have no experience with that specific switch... I have not read its manual, I have no idea what other settings you have made on it..
setting link aggregation
What are you doing with link aggregation?
Lets see these pages from your switch.
-
@johnpoz said in Interface range setup:
@jt40 said in Interface range setup:
VLAN ID 20 TAGGED on port 2
UPLINK on port 15, no TAGS.I have no idea what your doing... What is port 15? Is that the port connected to pfsense lan.. What is port 2, and why are you tagging it
Port 15 is the uplink port.
Port 2 is where I connected the laptop for testing.I can't create a VLAN untagged on that port, the UI doesn't allow me... It allows me only NOT MEMBER or UNTAGGED.
Same for the other ports...It may be because by default, all the ports are UNTAGGED with VLAN ID 1...
I have no experience with that specific switch... I have not read its manual, I have no idea what other settings you have made on it..
setting link aggregation
What are you doing with link aggregation?
It's one way to set up port truncate, there is LINK AGGREGATION and STATIC, both provide the same message.
I just linked you a short guide, the UI is simple: https://eu.dlink.com/uk/en/support/faq/switches/layer-2-gigabit/dgs-series/uk_dgs_1210_configure_link_aggregation_lacpThere is no other page where I can set up port truncate, without it, the VLANs will never work.
Then, there is another page where I can create the VLANs, that's even simpler.
You just posted the screenshots, yes, they are the same as in my switch, same config.
-
@jt40 said in Interface range setup:
Port 2 is where I connected the laptop for testing.
Then why and the hell would you tag it?? How many times do I have to state you do NOT tag traffic if there is one device connected to the port.
port truncate
Where did you get the idea that you need that?? I searched in the manual, this term isn't even the manual
dgs_1210_configure_link_aggregation_lacp
Why are you trying to setup LACP??? JFC!!! dude baby freaking steps!!
they are the same as in my switch, same config.
How and the F is that - thought you said you created vlan 20, that image only shows vlan 1.. Sorry but really at the that point that your just trolling.. Just at a loss to how someone could be this dense, and just fail to follow the most basic instructions..
I want nothing more to help you, and get to the point where you can set it up how you want it.. .But if you can not even get a basic vlan working.. Just at a loss to how you think your going to get to more advanced functions.
-
@johnpoz said in Interface range setup:
@jt40 said in Interface range setup:
Port 2 is where I connected the laptop for testing.
Then why and the hell would you tag it?? How many times do I have to state you do NOT tag traffic if there is one device connected to the port.
The UI doesn't allow me... I can only tag it, I don't know how to come out from that, I need to ask on their forum.
I understood the point :Dport truncate
Where did you get the idea that you need that?? I searched in the manual, this term isn't even the manual
Port trunk is necessary, or it doesn't allow the traffic on the UPLINK port...
I think this is the best explanation of what it does (at page 44 onwards), but I need to review the entire chapter, the manual is for another slightly different series, but the menu is exactly the same: https://www.use-ip.co.uk/datasheets/d-linkDGS-1210-52P_User_Manual.pdfdgs_1210_configure_link_aggregation_lacp
Why are you trying to setup LACP??? JFC!!! dude baby freaking steps!!
they are the same as in my switch, same config.
How and the F is that - thought you said you created vlan 20, that image only shows vlan 1.. Sorry but really at the that point that your just trolling.. Just at a loss to how someone could be this dense, and just fail to follow the most basic instructions..
I meant that that's the correct UI, and by default the VLAN ID 1 is UNTAGGED on each port.
Then, by myself, I've created a TAGGED VLAN with ID 20 on port 5 (example), I keep reminding you that I can't select UNTAGGED :D ... I will need to check this with their support...I want nothing more to help you, and get to the point where you can set it up how you want it.. .But if you can not even get a basic vlan working.. Just at a loss to how you think your going to get to more advanced functions.
The network was working without the default VLAN, I could check it simply with the IP range assigned to my devices.
Btw I'll remove the VLAN with ID 1 on PfSense.I'll review your messages but I think I followed every step...
-
@jt40 said in Interface range setup:
I'll review your messages but I think I followed every step...
Please post screen shots of your settings. Relying on your interpretation of what is set up, limited by what you know, is making fixing your system much harder than it needs to be. In essence knowing what you don't know is the hardest problem to solve.
Btw I am not intending to discredit your ability, but simply observe if this was something in your core skill set, then there would be no need to post questions on a forum. I would also like to optimize the chance you get your system working.
So specifically please post all of these screen shots
- Switch showing VLAN setting pages
- pfsense -> Interfaces -> Interface assignments
- pfsense -> Interfaces -> VLANs
- Pfsense -> Firewall -> Rules -> Floating, WAN, all LAN, all VLAN
-
@jt40 said in Interface range setup:
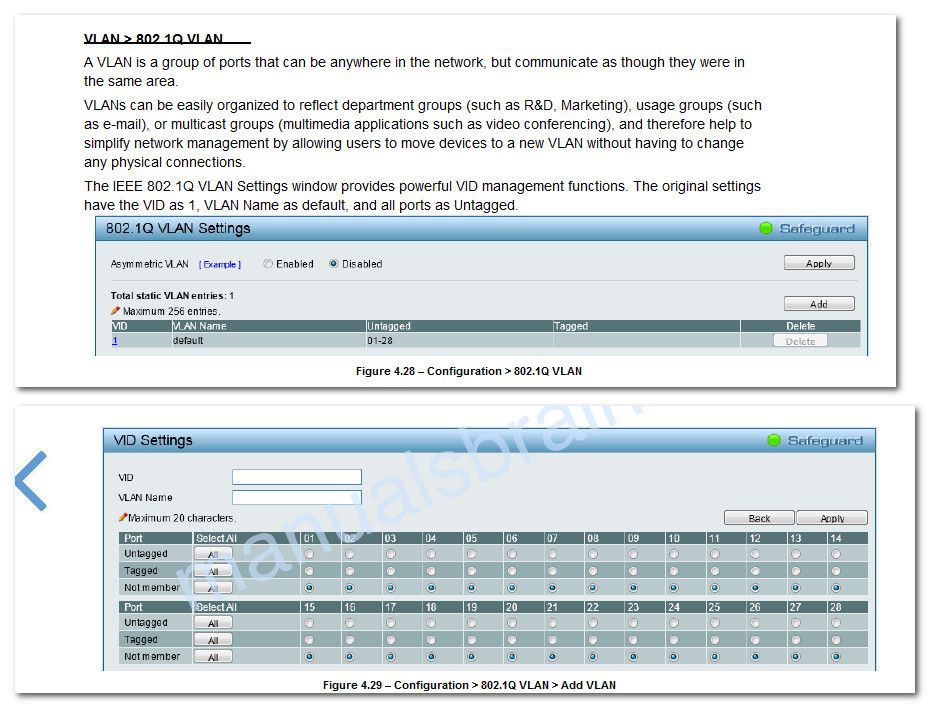
I meant that that's the correct UI, and by default the VLAN ID 1 is UNTAGGED on each port.
Then, by myself, I've created a TAGGED VLAN with ID 20 on port 5 (example), I keep reminding you that I can't select UNTAGGED :D ... I will need to check this with their support...Goto the switch web menu , in 802.1Q vlan
Select Vlan 1 , and set all ports not needing Vlan1 as untagged to:
NOT MemberVoila .. No more default Vlan1 untagged on those ports.
-
@patch said in Interface range setup:
Relying on your interpretation of what is set up, limited by what you know, is making fixing your system much harder than it needs to be. In essence, knowing what you don't know is the hardest problem to solve.
@JT40 -
Take a deep breath and read what knowledgeable members are suggesting and/or recommending. Pick up a book or an online resource on basic networking and get familiar with the terminology, concepts, etc. You seem to be lost in a maze of pre-conceived ideas of how networking - you think - should work, only to make it more difficult to fix your problem. As a non-expert myself, I can't help but notice how you're blindly running circles around every bit of advice you have been given in your threads.
Post screenshots as @Patch is asking!

-
Thanks everyone.
I was able to setup all, including the AP, just before the end of the year
I think that the main problem here was the different terminology of these devices, plus some lack of knowledge :D
In the end, to resolve, it, I understood the following things:
-
I really need DHCP on the switch, that's the first step prior thinking to go ahead with any other step
-
Defined the VLANs taking care of the following principles:
- Remove the VLAN 1 UNTAGGED almost everywhere, leave at least 2 ports with VLAN 1 UNTAGGED, it will be necessary for the initial maintenance
- If I have only one device on that port, the VLAN has to be untagged
- The AP started to work when I also set the VLAN 1 UNTAGGED on the respective port, if you only add the TAGGED VLANs, the traffic won't pass, so it seems that whenever there is a devices after the switch that is able to aggregate multiple devices, it needs to have VLAN 1 UNTAGGED as minimum, then the rest of the TAGGED VLANs.
I assume that the UNTAGGED VLAN ID on my Unifi 6 lite is also "1", I need to double check for curiosity, it doesn't appear on the menu. - Make sure to TAG all the VLANs on the UPLINK port, that may be obvious but I just note it here, plus you need to have the UNTAGGED VLAN 1 there as well.
-
I still have the VLAN 1 defined in PfSense and assigned to the DOWNLINK port for the switch, I'm not sure if it's necessary, I'll test the removal later, ops, I mean next year :D .
-
The Private VLANs have been automatically created by my switch, but the traffic is allowed anyway, most probably for the basic firewall rules that I have now (LOCAL_NETWORK to ANY), which makes sense, I just have to prove it, again, next year :D
-
In the AP I defined the VLANs with DHCP, as well as the internal default network + the way the AP gets its IP, without it, everyone would have an hard time to set it up or restore the config, same principle of DHCP on a switch...
-
It's important to notice that the AP needed to be disconnected after I've set up the VLANs, so whatever you change to the network there, it needs a reboot, that is unplug/plug the power cable :D
Plus this will be necessary also for your interface management of the Unifi 6 lite, it may not pair after these changes unless you reboot, just give it some time to apply the change, once it blinks with the blue light it means that is waiting for pairing, at that point you can reboot.
(It seems more an issue with the interface management software rather than the AP itself, but here the solution is)- I'll consider a wise advised given to me by someone here to reserve the IP addresses once the devices joined the network.
Regarding firewall questions, I'll open another thread, if I didn't already.
I hope that this message may help someone in the future.
I wish you all a nice end of the year!!! Your help guys has been critical!!!!!!!!
(BACKUP ALL!
 )
) -
-
@jt40 said in Interface range setup:
I really need DHCP on the switch, that's the first step prior thinking to go ahead with any other step
NO! Unless your taking about the switches IP because you don't know how to set one.
whenever there is a devices after the switch that is able to aggregate multiple devices, it needs to have VLAN 1 UNTAGGED as minimum, then the rest of the TAGGED VLANs.
Nope Again - vlan 1 only needs to be include if something downstream is going to be on that vlan. Be it say the a switch or AP that management IP is in your default vlan which is untagged. But that does not actually mean it would be vlan 1, it might be a different vlan there is no "requirement" that untagged vlan be it 1 or some other be included.
I still have the VLAN 1 defined in PfSense and assigned to the DOWNLINK port for the switch
Again NO!
The Private VLANs have been automatically created by my switch, but the traffic is allowed anyway
NO.. There is no freaking switch on the planet that would "auto create" private vlans out of the box. Traffic allowed between devices on the same network wouldn't be blocked unless you had actually setup private vlans - which would require you to define which ports can talk to each other. Devices between vlans talking to each other would be controlled by pfsense firewall rules on those interfaces.
in the AP I defined the VLANs with DHCP
No idea what your talking about makes no sense.
It's important to notice that the AP needed to be disconnected after I've set up the VLANs, so whatever you change to the network there, it needs a reboot, that is unplug/plug the power cable
More nonsense
-
@johnpoz said in Interface range setup:
@jt40 said in Interface range setup:
I really need DHCP on the switch, that's the first step prior thinking to go ahead with any other step
NO! Unless your taking about the switches IP because you don't know how to set one.
Yes, I mean the switch IP.
I'm using DHCP from PfSense, not from the switch.
It's much easier for backup restore plus some other situation that I can't remember right now.whenever there is a devices after the switch that is able to aggregate multiple devices, it needs to have VLAN 1 UNTAGGED as minimum, then the rest of the TAGGED VLANs.
Nope Again
That's how my AP works then, I tested it multiple times.
I still have the VLAN 1 defined in PfSense and assigned to the DOWNLINK port for the switch
Again NO!
In this case I need to test if this is necessary or not, in any case the setup is working for now, I just take it for good but I still didn't verify if it's correct.
Withotu VLAN with ID 1, I think it's gonna refuse whatever traffic comes with that ID, which in my case it doesn't make much sense, but in some other yes.
In my case I only have devices under UNTAGGED/TAGGED VLANs with ID != 1The Private VLANs have been automatically created by my switch, but the traffic is allowed anyway
NO.. There is no freaking switch on the planet that would "auto create" private vlans out of the box.
The VLAN IDs appear in the VLAN Private ID page, I can test it when I'll have the correct firewall rules, but not today :D
in the AP I defined the VLANs with DHCP
No idea what your talking about makes no sense.
This means that the VLANs in the AP don't have a static IP, but it takes the IP range defined in PfSense, even though there is a switch in the middle, which makes sense, I only have one DHCP server that runs on PfSense.
It's important to notice that the AP needed to be disconnected after I've set up the VLANs, so whatever you change to the network there, it needs a reboot, that is unplug/plug the power cable
More nonsense
That's what I've seen :)
-
@johnpoz said in Interface range setup:
@jt40 said in Interface range setup:
I still have the VLAN 1 defined in PfSense and assigned to the DOWNLINK port for the switch
Again NO!
I think this is useful if you need to administer the AP management interface from one of those VLANs, specifically when the routing is entirely managed by PfSense (which is my case).
I agree that is not necessary in general. -
@jt40 said in Interface range setup:
This means that the VLANs in the AP don't have a static IP,
Vlans don't have IPs assigned to them on devices - if your thinking about a an IP for a SVI (switch virtual interface), where a switch would be doing routing, or have an IP on that vlan you could use to connect to the switch to manage. An AP would never have this in all of its vlans, it would only ever have an IP to manage it. What vlan that is in, be it untagged or tagged would depend on the AP. But an AP wouldn't have an IP in each vlan that it might provide via SSIDs, etc.
I think this is useful if you need to administer the AP management interface from one of those VLANs
Mr isolated admin interface on pfsense, and private vlans where nothing can talk and you think its a good idea to put IPs your AP to be managed via a wireless network?
You only need 1 management IP.. You would route this through your router if you wanted to manage it from another vlan. And normally filter this traffic so you can only manage it via your management vlan and only from your admin machine(s) IPs.. And no you wouldn't normally allow management of AP from any wireless network.
-
@JT40 is there a reason you are unwilling to post the following information?
@patch said in Interface range setup:
So specifically please post all of these screen shots
Switch showing VLAN setting pages
pfsense -> Interfaces -> Interface assignments
pfsense -> Interfaces -> VLANs
Pfsense -> Firewall -> Rules -> Floating, WAN, all LAN, all VLANPerhaps if we better understood that we could better help you.