Block answer on ping from Vlan
-
@silence
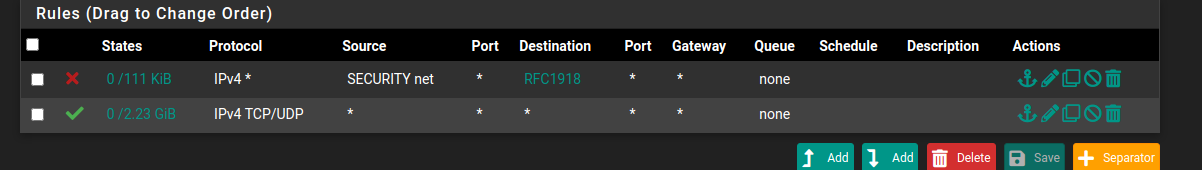
-
@19taurus79 rules are evaluated on interface where traffic enters pfsense..
Return traffic is allowed by the state that is created when traffic is allowed.
If you don't want vlan B to be able to answer ping, then you need to block that traffic from pinging from vlan A..
Since if you allowed A to ping B, then the answer would be allowed by the state you allowed to be created when you allowed A to ping B.
-
@johnpoz ok I see, if i dont want vlan 50 to answer on ping to any other vlans. I have to block icmp in the other vlans to vlan 50... Because i want my main adm vlan10 to ping every other vlans. I dont know how important this is for me, but it is more to try and learn:) since this is my security vlan with cameras i thought it could be a good set-up to block icmp.
-
@19taurus79, you can duplicate the first rule but now swap source and destination.
and just above create a rule to allow ping from your vlan 10
-
@silence Yes, thanks for help. Learning something new every day.. I am new with pfsense rules a little different ffrom edgerouter to setup..
-
@19taurus79 while you might want to stop your cameras from pinging or talking to your other vlans. Not sure why it would be an issues from your other vlans to ping devices in vlan 50.
But you do you - but with a stateful firewall, return traffic allowed by the state. If you don't want anything to be able to ping stuff in vlan 50, block them from doing so where their traffic would enter pfsense. This could be done on the interfaces directly, it could be done with a floating rule.
-
@johnpoz as i said, this is more for learning what happens and how to do it...
-
@19taurus79 Which is great! Just telling you how it works ;)
-
@johnpoz I used the Floating rules and setup with all my Vlans and VPN interfaces to block ICMP to Vlan50. Than i made a new rule for Vlan 10 to one host IPadress that allows ICMP to vlan 50.. It worked, now a beer:)
-
@19taurus79 said in Block answer on ping from Vlan:
now a beer:)
hehee - which is always to the correct response ;)