New OpenVPN server, can connect but can't get to LAN subnet.
-
@fatman032 said in New OpenVPN server, can connect but can't get to LAN subnet.:
The part that I don't get is why I'm not seeing any blocks now form this network to my LAN network.
Possibly because pfSense doesn't block any.
Maybe the remote device blocks the access by its own firewall. Since you said, this was already working before, this shouldn't be the case, but possibly you had set up a workaround with masquerading.To investigate on pfSense you can take a packet capture on LAN, while you try to access from the remote client to see if the device is responding properly.
-
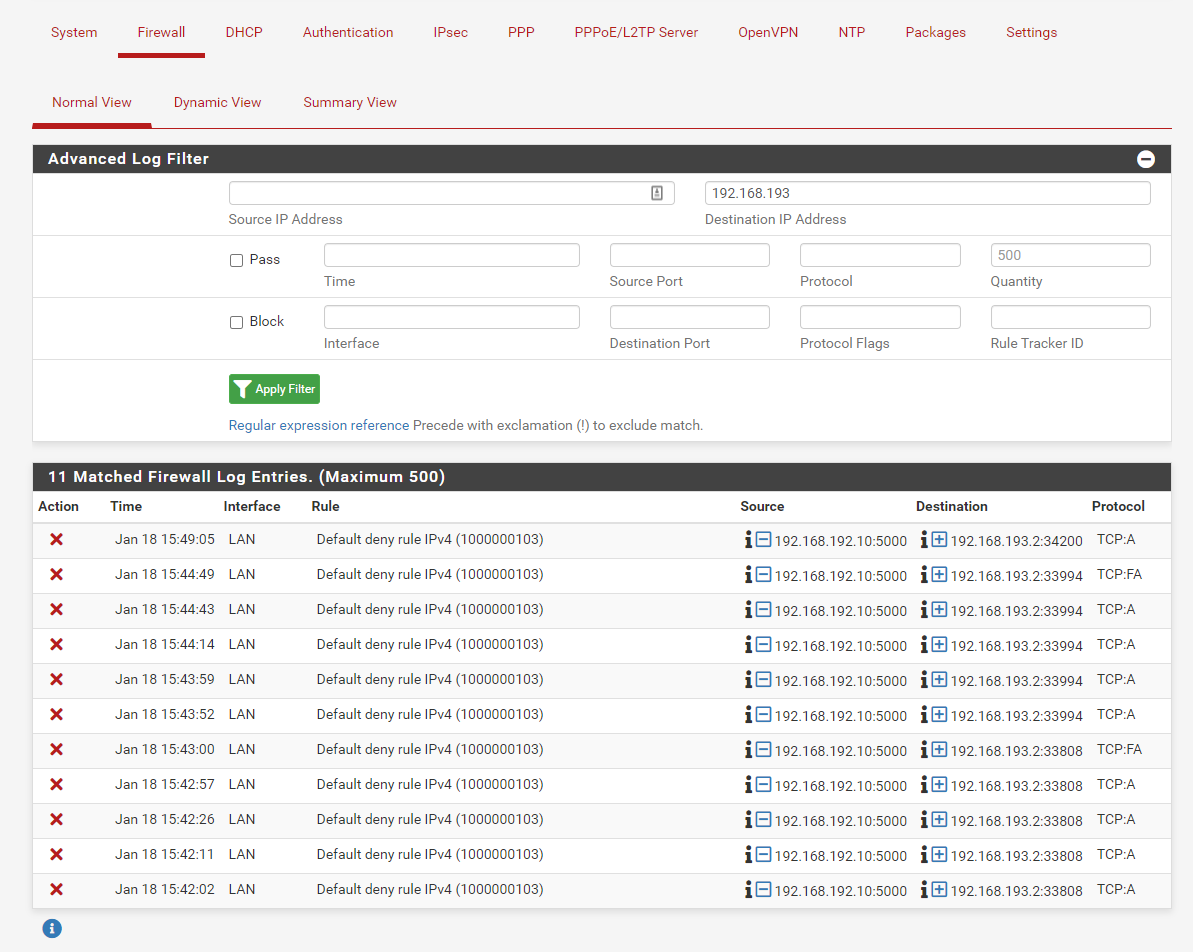
@viragomann I think I found part of the problem. I added the OpenVPN rule back in. I can now see blocks from 192.168.193.2
-
@viragomann said in New OpenVPN server, can connect but can't get to LAN subnet.:
@chpalmer
No, it's a private one out of 192.168.0.0/16.I see that now.. I was an octet off.
-
@fatman032
These blocks are out of state packets. That is no traffic which should be allowed at all.
However, I've no idea, why you see this only, when you allow traffic on the OpenVPN interface.Is the port 5000 this one you tried to access from the remote client?
-
@viragomann Nope I can try any LAN IP device and I get the same thing. At this point I'm about restore my entire firewall and start over. The other strange part is when I try to reset the states it basically is crashing the browser. I read this might be because it is running into some sort of error and can't rebuilt the states.
-
@fatman032
Do you have a Synology which you tried to access from the client? -
@viragomann yes and a raspberry pi is hosting a web server that I play with. I block all traffic on it so it can't get out to the internet. This is part of the reason I want to setup the VPN.
-
@fatman032
So maybe on the vpn client runs any software, which is accessing it. But the Synology may send responses to another destination than pfSense, because it uses another default gateway. -
Okay so I factory reset my pfSense. I have nothing plugged into my network but one computer and my raspberry pi at 192.168.192.12.
My LAN network is 192.168.192.0/24I setup the VPN using these setups instructions.
I have no other VLans no other VPNs. I have two any to any rules on every interface. One for IPV4 and one for IPV6.
I'm still getting a default deny rule. I have no idea what is going on.
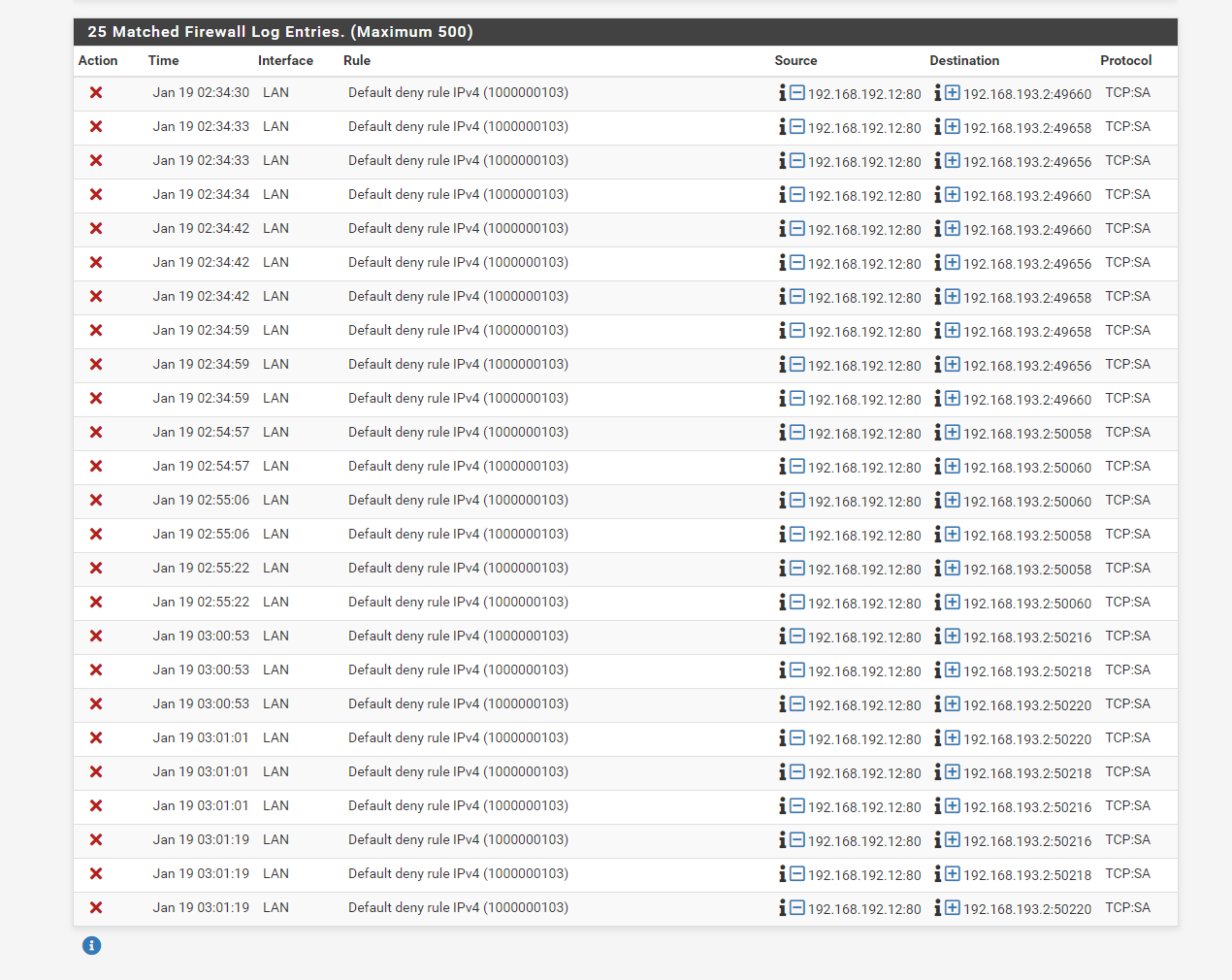
I know this is not the ideal setup. I just want to get everything out of the way that could be causing this problem. I have no idea how this can be blocked. I don't remember my other netgate being this big of a pain to setup. Is there something different with this new SG-2100?
-
@fatman032
Again, it look like that the raspberry is sending response not to pfSense, but to another device.So go to the Pi and check out his routing table to get any further, please.
-
@viragomann Sorry had a bad night just wanting to get this working.
Here is the routing table for the pi.
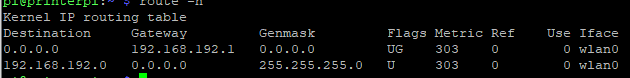
-
@fatman032
And what's the LAN IP of pfSense? Does it match? -
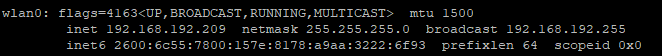
@viragomann Yes they Match. The LAN is 192.168.192.0/24
Here you go. It has new IP since it no longer has a reservation.
-
@fatman032 said in New OpenVPN server, can connect but can't get to LAN subnet.:
Yes they Match. The LAN is 192.168.192.0/24
That's not a proper Interface IP, that's a network address.
-
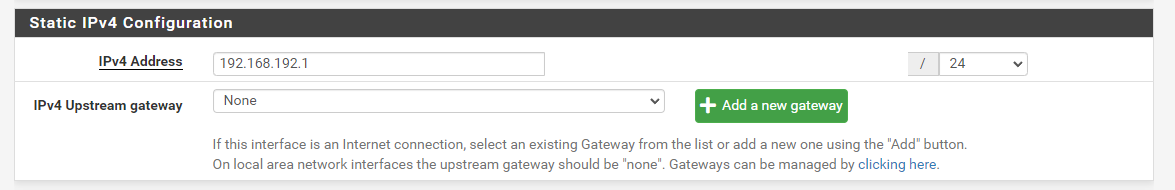
@viragomann Here you go.
-
@fatman032
All right. So I cannot tell you, why you run into these out-of-state blocks on LAN:

Since the source port is 80 and the flag is SA, these are definitely respond packets SYN packets. And presumably pfSense did never see the respective SYN packets.
Okay, do you connect your VPN clients from inside your LAN?
-
@viragomann no I have been using my cell as a hotspot.
-
@fatman032 said in New OpenVPN server, can connect but can't get to LAN subnet.:
no I have been using my cell as a hotspot.
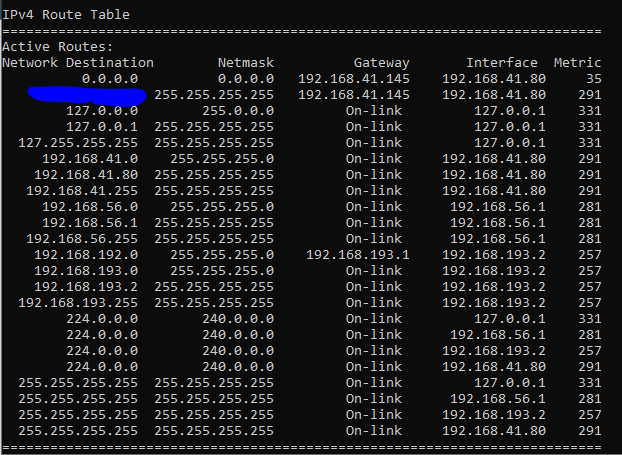
Also cut all internal connections?
Need to see the clients routing table to get closer.
-
Also cut all internal connections?
Yes, I turn off the Wi-Fi.
Need to see the clients routing table to get closer.
-
@fatman032
Looks well.Ensure that also your cell phone has no internal connection at the time you test the VPN via the hotspot.
I'm sure, there must be something wrong in your setup. You have obviously an asymmetric routing issue on the VPN.
For further investigation I can only suggest to sniff the traffic on all involved interface while you try to access the LAN from the VPN client.
I guess, the SYN packets don't come in on the VPN interface.