Allow any not working
-
Hello pfsense Community,
i m trying to create a "allow all" rule for my PC in the firewall, but is is not working...
I created the rule on the top:
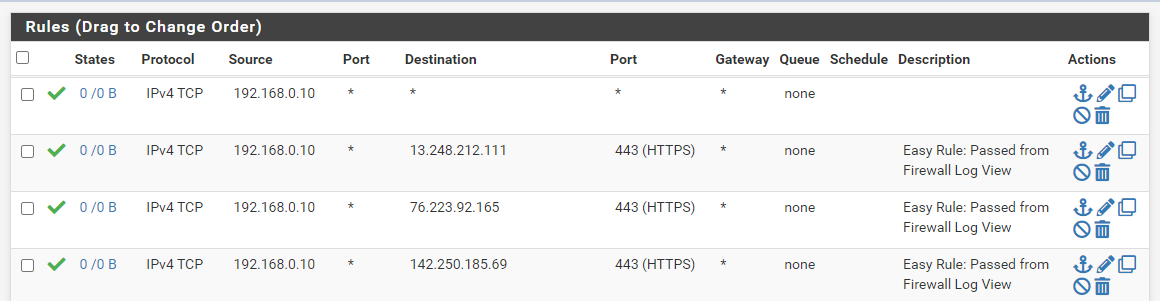
My setup:
LAN ==== Subnet: 192.168.0.XX PC: 192.168.0.10 pfsense: 192.168.0.37 Gateway: 192.168.0.1 (hardware router + modem)VLAN ==== Subnet: 192.168.11.XX pfsense: 192.168.0.37 Gateway: 192.168.1.11 (pfsense)When my PC is in LAN with Gateway 192.168.0.1, there is no access to VLAN => ok
When i switch Gateway of PC oto 192.168.0.37 he has acces to LAN an VLAN (if firewall rules allow access) => ok
But my PC has no complete access to the internet, pfsense firewall is still blocking requests.
I tried to create an "allow all access" rule
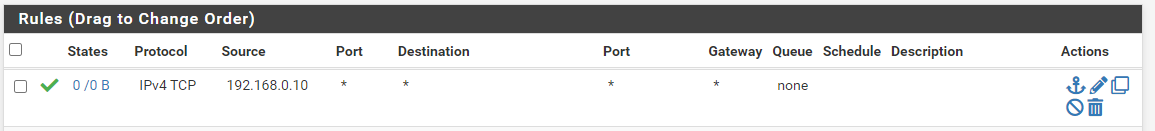
but it is not working, still have to allow each IP address seperatly (like rules 2-4).
Any idea why?
Kind Regards
Darth -
@darth-0 said in Allow any not working:
PC: 192.168.0.10
pfsense: 192.168.0.37
Gateway: 192.168.0.1 (hardware router + modem)How would that work?? If the vlan is off of pfsense, then you would have to use pfsense as your gateway to get to that vlan. Or you would have to have a route on your PC that says when you want to get to the pfsense.
This also makes no sense
Subnet: 192.168.11.XX pfsense: 192.168.0.37 Gateway: 192.168.1.11 (pfsense)What mask are you using? /24 /16 something else..
None of those rules you created show any evaluations even see the 0/0 in the states column.. So not sure what they are allowing or not allowing - because from what you posted they are never being triggered..
-
@johnpoz
of course youe are right, there are no 192.168.0.XX IPS in the VLAN...
And alls Subnets are /24.here the corret ones:
VLAN ==== Subnet: 192.168.11.XX pfsense: 192.168.11.1 Gateway: pfsense DHCP: pfsensepfSense has in LAN 192.168.0.37 and in VLAN 192.168.11.1.
Now i am searching for a way to get access to both subnets (i want to move servers to VLAN) and clients in LAN should still be able to consume services from them.
Your hint with a route is working fine on my PC
 .
.But is there another way none PCs like Tablets or Cellphones?
Best regards
Darth -
@darth-0 so what is the end goal here.. If you have some setup like this..
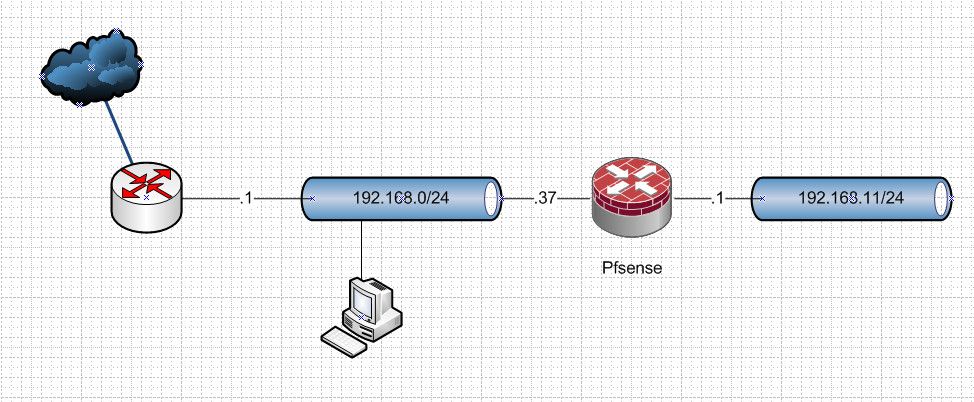
And you have devices on the 192.168.0 network and you want to get to devices on that vlan 192.168.11 network and you can not create routes on the devices.
You would have to setup port forwards and and nats so that say you want to access 192.168.11.X you really access 192.168.0.37 on port xyz, and pfsense forwards that traffic to 192.168.11.X
I take it this is just some temp thing while you setup some new overall network layout..
-
Greate assumption and 100 points to you


That is my current situation.Hmm, bad network setup?
Would this be a better approach:
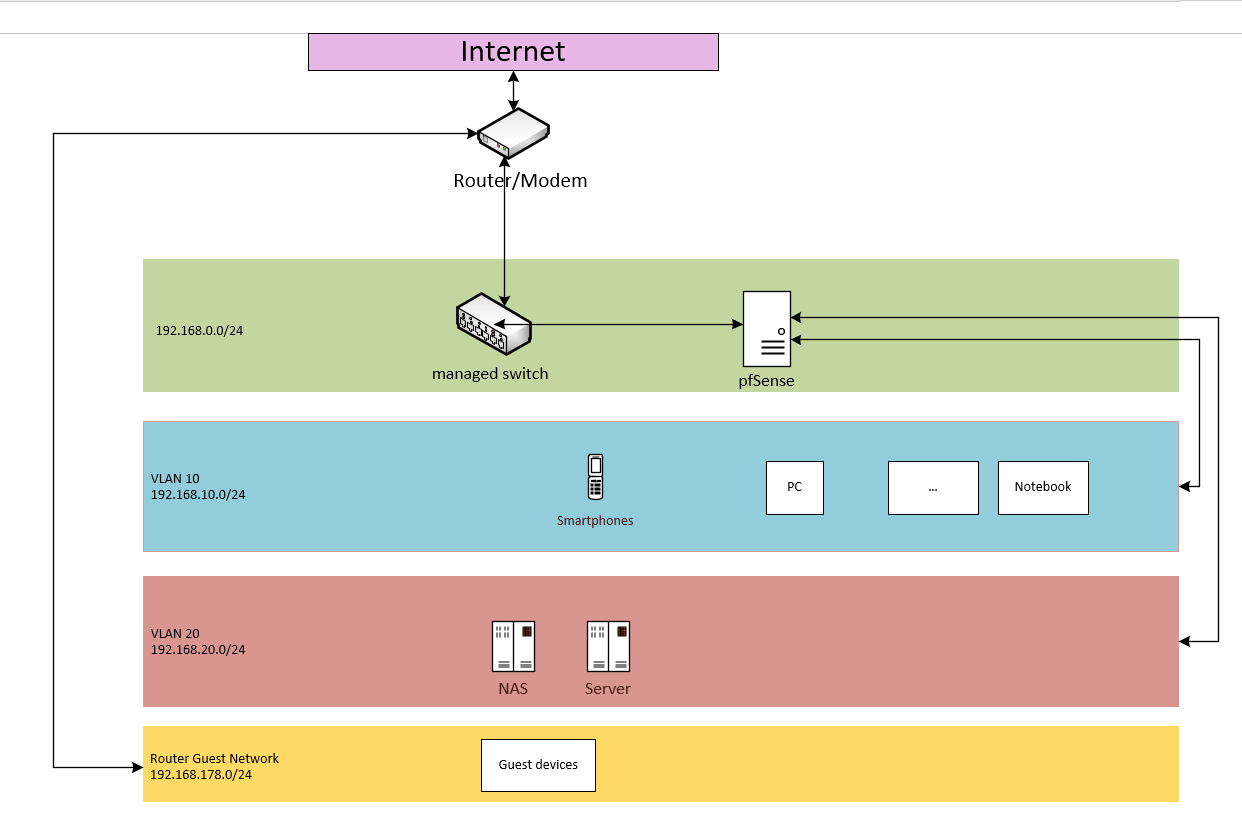
Each device in 192.168.10.XX/24 and 192.168.20.XX/24 uses pfsense dhcp and gateway in their VLANs.
(Pfsense has access to all VLANs and 192.168.0.XX/24)A big thanks for your help so fare!!
-
Morning,
it might make even more sense, when you would put your managed switch behind your pfsense device:Router---------pfsense-------switch------vlans with devices (you might want to put your guest network behind pfsense as another VLAN with strict ruleset, so guests cannot get into other vlans and just reach the i-net...
Then every subnet (vlan) will get dhcp, dns, ad-blocking/ipblocking (pfblockerng_dev) etc from your centralized pfsense, you could install rules for every vlan dependent on your needs...
:) -
@the-other
Yeah this is even better