Successful logins YubiKey (smartcard) & AD creds with OpenVPN
-
I could not find any successful and documented configs for using YubiKey or smartcards with OpenVPN on a Windows computer and did not use a on-prem or cloud subscription solution.... so here we go:
The OpenVPN Client (tested with version 2.5.2) prompts for username and password, then prompts for the PIN of the smartcard. I followed these guides:
- https://support.yubico.com/hc/en-us/articles/360013707820-YubiKey-Smart-Card-Deployment-Guide
- https://mujadin.se/suse/openvpn/
- https://github.com/OpenSC/OpenSC/wiki
It works with everything of Active Directory and did not need to use any pfSense generated certs (besides the TLS key) as with my previous implementation. I copied OpenSC's opensc-pkcs11.dll to '\Program Files\OpenVPN\bin' directory.
Only the AD CA (or sub-CA) public cert and a signed cert from that for pfSense would need to be uploaded to pfSense as it is needed for the user authentication along with the LDAP type in the Authentication Servers tab of User Management.
I still need to do some additional testing for revoke certs, and a few other items but I was able to login with a successful PIN and not with an incorrect PIN or smartcard. This was already validating against the AD group and using pfSense generated user certs before adding YubiKey / smartcard.
The config will need to be modified if a different yubikey is used or if the cert / serial ID is renewed on it…. minor for now. Maybe a script can parse that out and put in a separate 'config filename' OpenVPN parameter.
Here is my .opvn config:
dev tun persist-tun persist-key data-ciphers AES-128-GCM:AES-128-CBC data-ciphers-fallback AES-128-GCM auth SHA256 tls-client client #resolv-retry infinite remote 10.10.1.1 1194 udp4 #IP address or FQDN lport 0 verify-x509-name "Your 'Server certificate' name from OpenVPN settings" auth-user-pass remote-cert-tls server comp-lzo adaptive #compress passtos connect-retry 5 300 connect-retry-max 1 resolv-retry 15 connect-timeout 10 reneg-sec 36000 # this may need to be set to zero (0) or it may fail trying to ask for smartcard PIN on regen pkcs11-providers ..\\bin\\opensc-pkcs11.dll # this is from the OpenSC installer and is the only file needed pkcs11-id 'piv_II/PKCS\x2315\x20emulated/YourSerialIDHere/Your\x20Token\x20ID\x20Here/01' <ca> -----BEGIN CERTIFICATE----- Your AD CA or whichever CA public key here defined in 'Peer Certificate Authority' from OpenVPN settings -----END CERTIFICATE----- </ca> key-direction 1 <tls-auth> # # 2048 bit OpenVPN static key # -----BEGIN OpenVPN Static key V1----- Your key here -----END OpenVPN Static key V1----- </tls-auth>
-
@dimnovotny Finally, thank you. Will try on macos now.
How did you find the pkcs11-id?openvpn --show-pkcs11-ids /usr/lib/pkcs11/opensc-pkcs11.soBut I still get this error
[Jan 28, 2022, 10:45:15] EVENT: EPKI_ERROR External Certificate Signing Failed [Jan 28, 2022, 10:45:15] Client exception in transport_recv_excode: OpenSSLContext::SSL::read_cleartext: BIO_read failed, cap=2576 status=-1: error:141F0006:SSL routines:tls_construct_cert_verify:EVP lib -
@sha512 I currently do not have a Mac to test. Over this past summer, I needed to install Tunnelblick instead of Viscosity (from pfSense) on one of our employee's personal Macbook for OpenVPN to login with pfSense generated CA, server, and user certs.
In my OP, I was doing this on a domain-joined computer. It may be working for me because my test computer also have the root CA cert(s) installed via GPOs/domain and with the almost current OpenVPN client (2.5.2) from https://openvpn.net/community-downloads/.
You may also need to install the root CA cert(s) on the YubiKey. This site is for performing the operation on a Windows computer, not sure offhand the commands for a Mac - https://support.yubico.com/hc/en-us/articles/360015654500-Setting-up-Windows-Server-for-YubiKey-PIV-Authentication#Working-with-Enterprise-Root-Certificates
-
@dimnovotny Will follow that guide tomorrow and try on one of our domain joined Windows laptops. At the moment, CA on pfsense is not a subordinate to ADCS, but will create one too.
In which slot did you install the certificates?
What I tried today was to export CA, user certificate and key from pfsense and import to slot 82 and 83 as described here on Yubikey 5C. Then followed your
.opvnconfig recipe and installed opensc. Imported the profile to OpenVPN Connect, assigning certificate etc.. connection failedEVENT: EPKI_ERROR External Certificate Signing Failed.A tutorial for using YK4 for OpenVPN here
-
@sha512 To not mess with the production VPN connection on pfSense, I cloned my production OpenVPN server profile to a test profile and use a different port (e.g. udp:1195), then I can select our AD certs without messing with the current remote users connection.
pfSense's CA does not need to be signed CA, but it depends on each individuals corporate policies. My pfSense is using a server cert signed by our AD CA for the web GUI and a separate server cert signed by AD CA for the OpenVPN server connection settings:
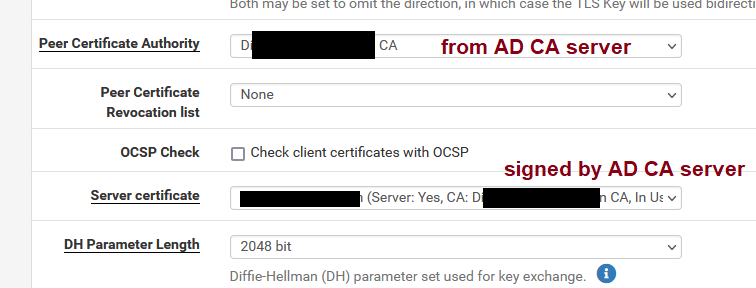
My YubiKey 5 series sticks were factory defaults and I followed Yubico guides linked in my op. Then you can have the YubiKey autoenroll or do the enroll on behalf of user from a Windows machine. Everything was saved to the 9a slot which is the default location. This is still R&D for us but the YubiKey main purpose is for Windows local and remote OpenVPN logins instead of going with some subscription on-prem or cloud subscription.
Best of luck!
-
thank you for your howto. Did you find a way to detect id-changes and automate the configuration generation für pkcs11-id?