Block printing in remote printer
-
@silence The Facebook_Block is a testing rule, rest there with no impact (i suppose).
I didn't know that the sorting of the rules affect their operation order!
So my printer's ip is 192.168.3.100 and i am trying to print from 10.168.10.198.
Pfsense ip is 10.168.10.115. -
You have a fundamental misunderstanding of how the firewall rules work in pfsense. Immediately delete this rule on the WAN:

It is allowing anything on the internet to access anything on your internal networks!I can help you straighten this out but it's going to take some work. Definitely read this: https://docs.netgate.com/pfsense/en/latest/firewall/index.html
I didn't know that the sorting of the rules affect their operation order!
Rules are evaluated from the top down. The first rule that gets triggered is it....no other rules below it are evaluated.
Rules on an interface are interpreted in the inbound direction as allowing/blocking clients on that interface to pass into the firewall to be routed. Client--->firewall rule on the interface ----->routed through firewall.
-
The WAN has a default BLOCK rule that prohibits anything from passing through the WAN and into the firewall.
-
The LAN interface has a default ALLOW rule that permits clients on the LAN so send traffic into the firewall.
The printer rule you have on the WAN is wrong. The way that rule is written it is saying that any IPv4 traffic coming from the WAN (ie anything from the internet) is allowed to pass through the WAN and into the router and be sent to the device at IP 192.168.3.0. That rule needs to be on the LAN (10.168.10.xxx) interface and not on the WAN. And the gateway for that rule needs to be your IPsec interface. In that way you will be policy routing (allowing) traffic initiated on the LAN destined for the printer's IP address to be directed to be sent out the IPsec tunnel.
I'll look at the rules in more detail tomorrow and will give you more feed back.
-
-
-
@silence Thanks a lot!
-
@dma_pf Very appreciated for your detailed instructions! May i have to explain you further my network infrastructure
-
@nikpony said in Block printing in remote printer:
Very appreciated for your detailed instructions! May i have to explain you further my network infrastructure
You are very welcome, and I'm glad to help. I do need some more info on your infrastructure. In your earlier post you mentioned the Huawei Router.
-
Is that router still being used or has pfsense replaced it?
-
If it is still being used is it acting as a gateway to the ISP?
-
If so, is it in bridge mode now that you have pfsense behind it?
Does anything on the remote network need to reach back to your local LAN to access any resources on the LAN?
What is the purpose of the OpenVPN on pfsense?
-
-
So, the router is still in use, of course, and this is our gateway.
I have not set it in a bridge mode, should i do it?Right now, remote network get into our lan through ipsec and they have access to our domain.
OpenVPN is used just for access in our sources, like ERP, mail etc. -
@dma_pf Also i have to inform you that it runs in a Hyper-V
-
@nikpony Is the router serving any other purpose other than just providing a gateway to pfsense?
All IPsec is being handled by pfsense (no IPsec configured on router)?
Is the domain all Microsoft? Is everything on the LAN part of the domain?
How do you have pfsense set to resolve DNS?
So if I understand correctly, OpenVPN is used to allow outside sources to access local resources on the LAN? Are any of those sources mobile, or are the accessing resources from fixed locations?
-
Router has all the management of IPSec.
The domain is Microsoft only, all devices are parts of my domain.
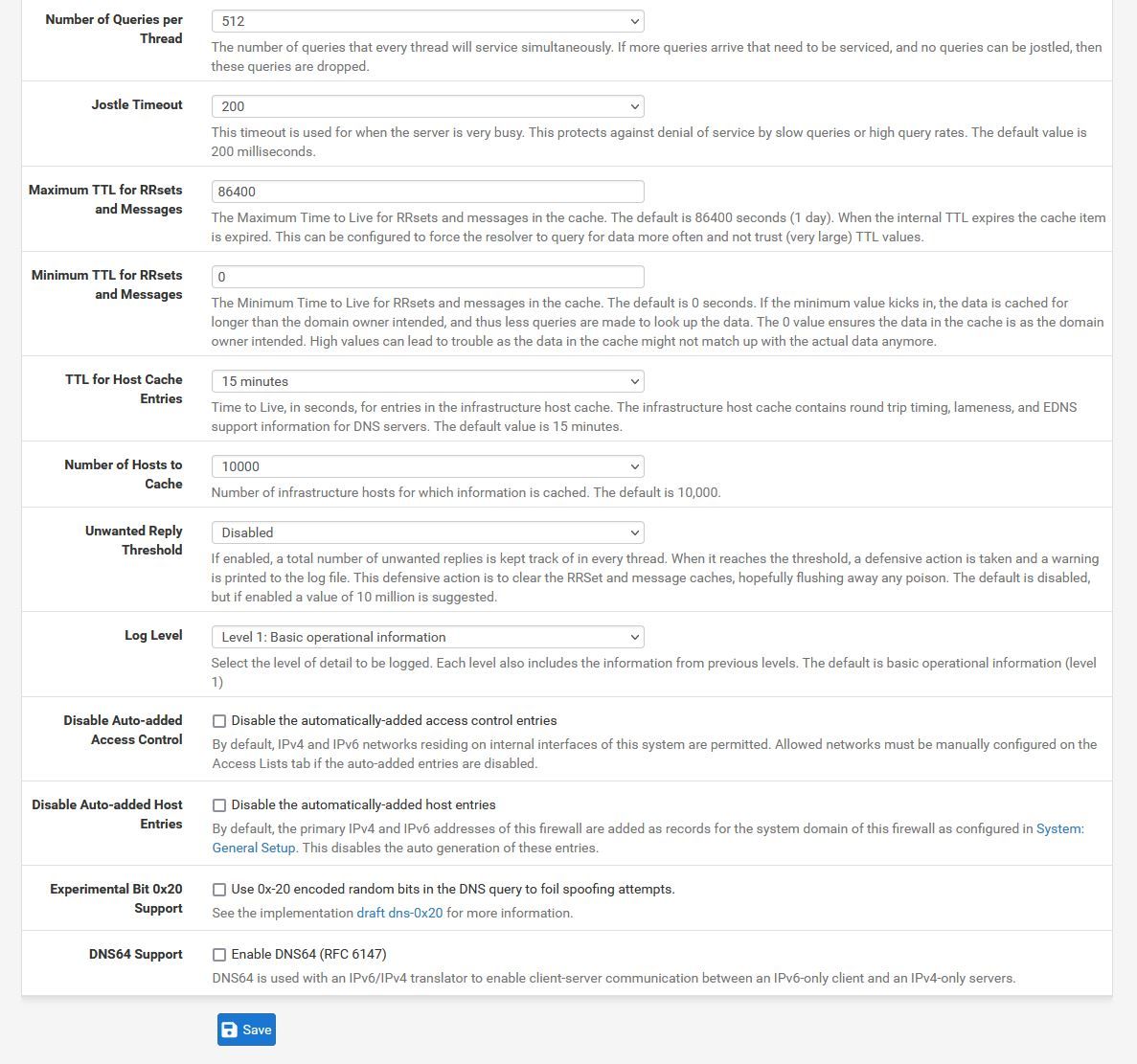
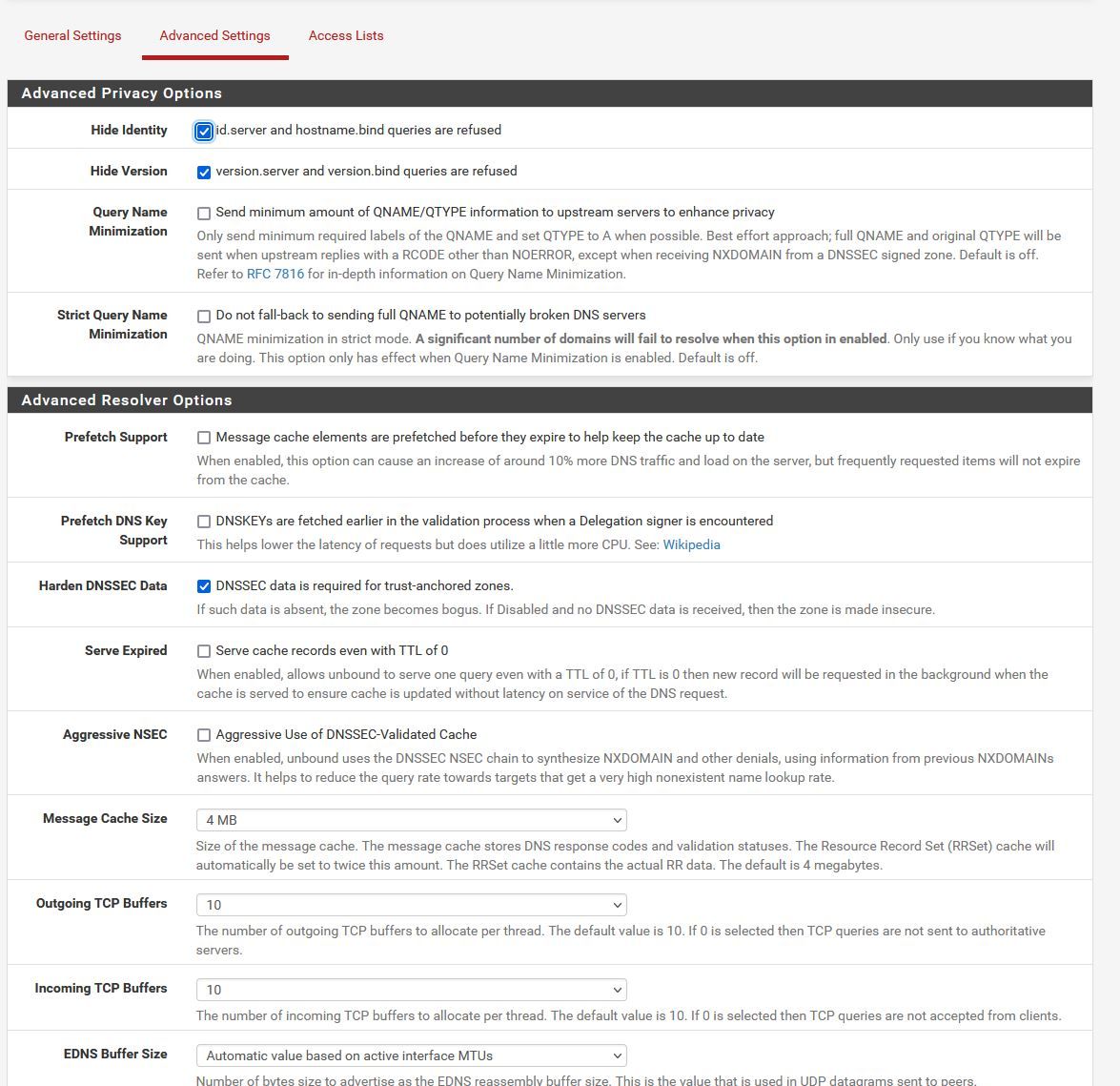
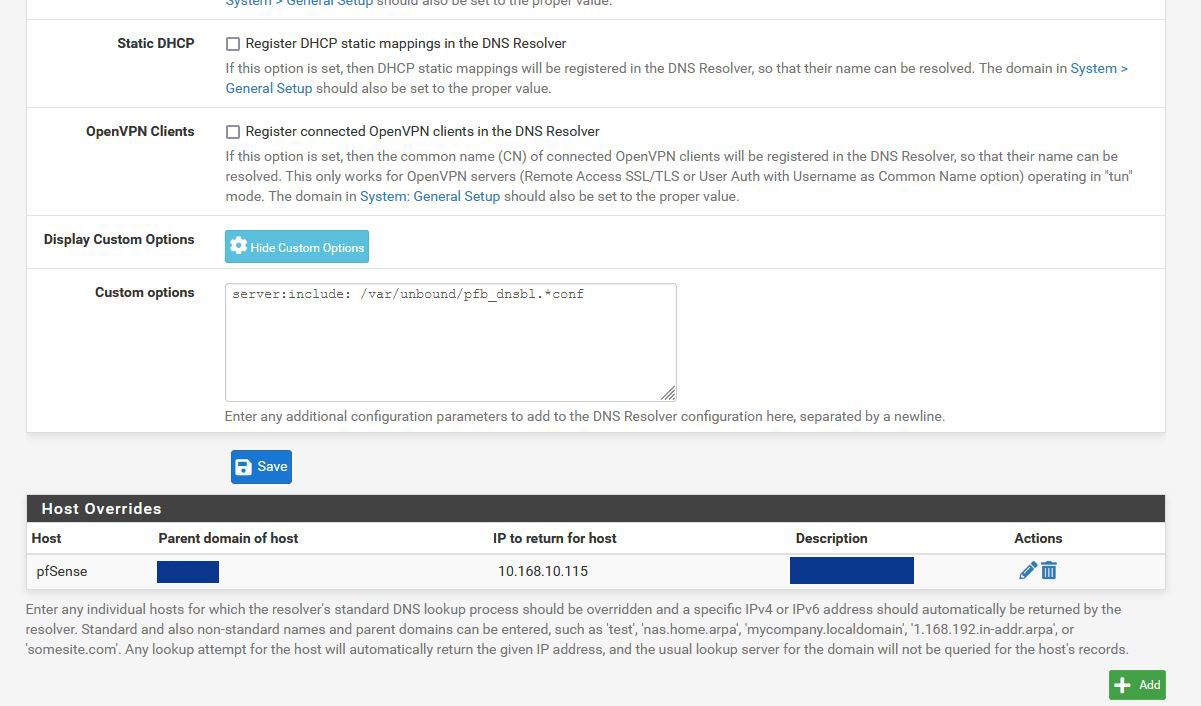
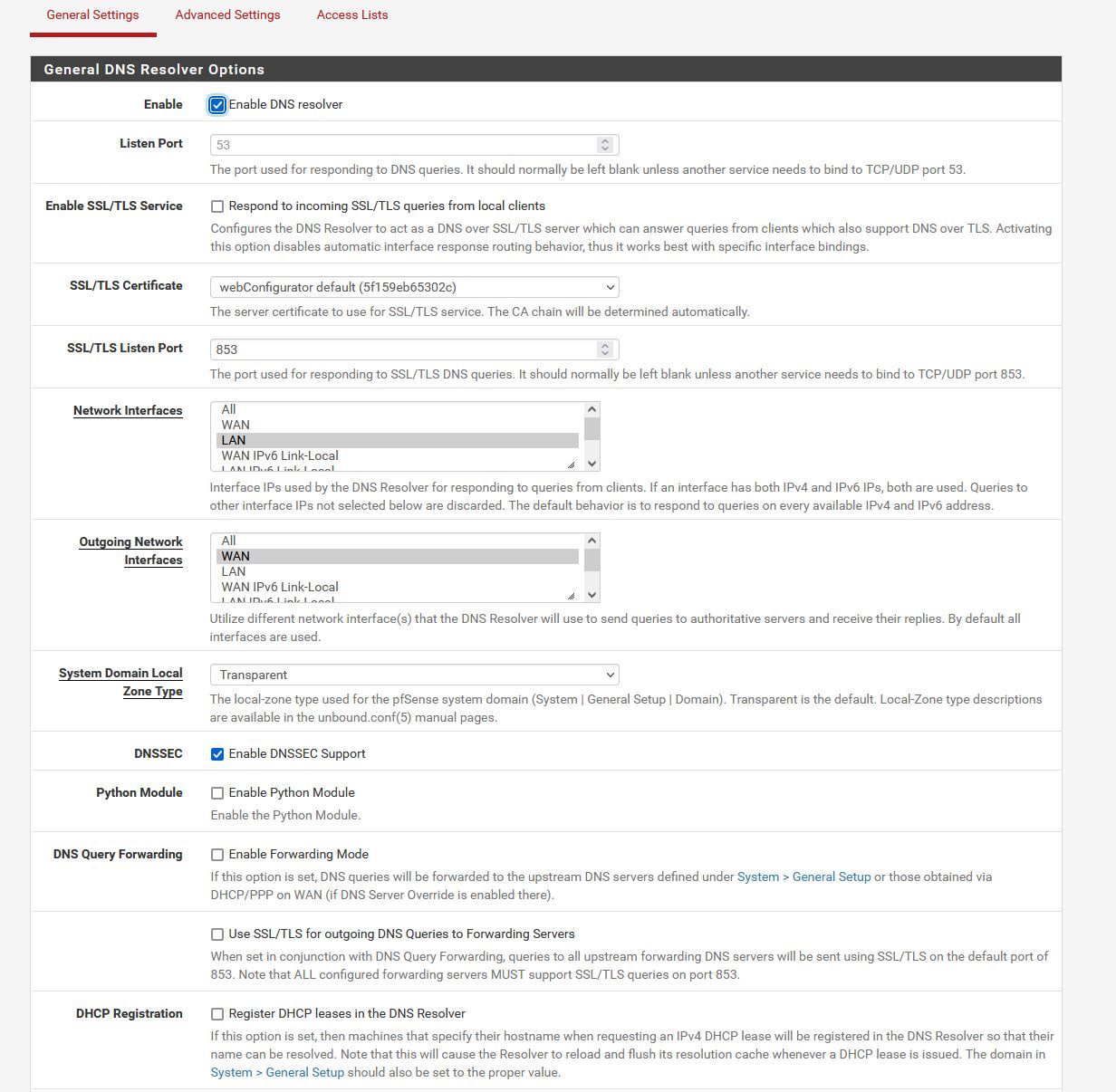
Attached photo of my DNS resolve settings.
Regarding the OpenVPN, you are right. There are no fixed locations, if you mean such as static ip's that using the OpenVPN.
-
@nikpony said in Block printing in remote printer:
Router has all the management of IPSec.
Is this true even for the pfsense LAN to the remote network? Why is there an IPsec interface on pfsense if all IPsec is being handled by the router?
-
@dma_pf I just enable it, a few months ago, for testing. There is not any tunnel enable. Are my settings in DNS Resolver correct?
-
@nikpony said in Block printing in remote printer:
Are my settings in DNS Resolver correct?
Generally they look fine to me. I would enable the following in the Advance Settings: Query Name Minimization, Prefetch Support, Prefetch DNS Key Support, Serve Expired and Static DHCP.
Some feedback on the OpenVPN firewall rules you posted. Rule 1 being the top most rule and then working down:
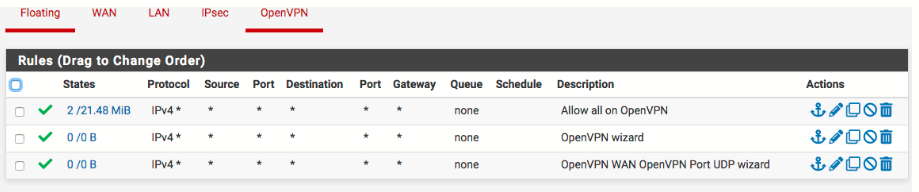
I am assuming that theses are the OpenVpn rules even though Floating is highlighted as well. Rule 1 is the only rule you need here. The other 2 rules below it are exactly the same rule and accomplish nothing.
Regarding the LAN rules:
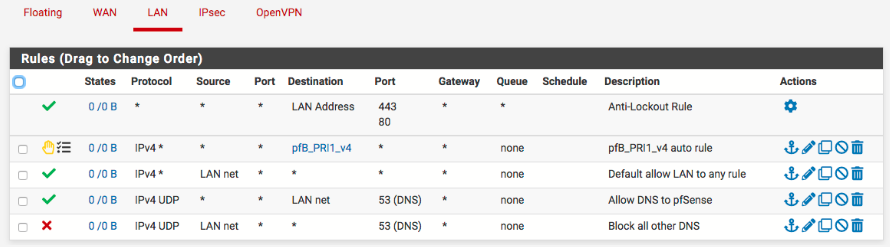
Move rule 3 to the bottom of the rules.I don't know why all of those rules are are showing no states and traffic (0/0). Could you please post a screenshot of your NAT rules. Also, enable logging on them for now. If you do look at the firewall logs filtered by the Interface as LAN what do you see?
I'm still trying to get my head around how the router is routing traffic to it's various IPsec tunnels. What ip address is the router providing to pfsense?
Regarding the WAN Rules:
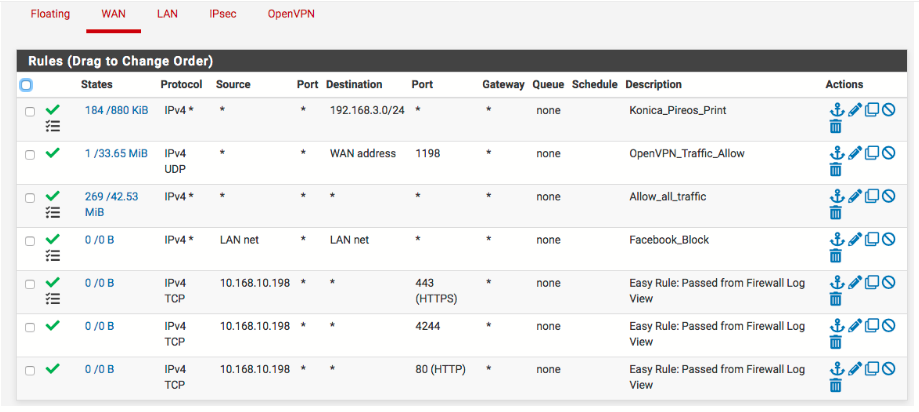
In Rule 1 I do not understand why traffic is coming from the router and trying to access your remote network (192.168.3.0/24). Nonetheless, it is happening and the firewall is letting that traffic through the WAN (184/880 KiB). Can you look at the firewall logs and filter it with a Destination of 192.168.3. and Interface of WAN?
Rule 2 looks fine. I see that you are using pfblocker. You may want to consider creating an GeoIP "Alias Permit" rule in Firewall/pfBlockerNG/IP/GeoIP then use that alias (Firewall/Aliases) in Rule 2 as the Source. That will only allow traffic from those specific selected countries to access port 1198.
Rule 3 I discussed in depth yesterday. I do see that there are packets that have hit that rule. Are there other networks on the other side of the tunnels that would initiate traffic into pfsense (other than through OpenVPN)? If so I would create a manual alias (Firewall/Aliases) with the networks, and/or specific IP's, that need to access through the WAN and use the alias in this rule as Source.
Rule 4 is not needed.
Rules 5-7 I see that those 3 rules have never had any packets hit them (0/0). I get the sense that you set them up to try to get the printer working. Is there any reason why the printer on the remote network would be initiating traffic to anything on pfsense on those ports? If not then those rules are not needed.
Just for now I would set all of the rules to log.
-
This post is deleted! -
@dma_pf Finally, i resolve it, after changing the NIC in Hyper-V. As i have, two physical NIC, i use the first one for WAN, and the second one for LAN.
So, stop using any virtual card, all features working properly, and i can print directly to any remote printer.
Then, just tried to switch my local NIC of my PC, to look at the WAN of pfSense, and once again i was not able to print.Anyway, the problem has just resolved, and i would like to thank you once again dear @dma_pf