One tunnel for remote access
-
@thebabufrik yeah I tried both split and full tunnel :( and I followed the same thing. I have no idea where I could have gone wrong. I just upgraded wireguard on it and now that interface with the handshake is no longer there.
-
@korr2221 said in One tunnel for remote access:
@thebabufrik yeah I tried both split and full tunnel :( and I followed the same thing. I have no idea where I could have gone wrong. I just upgraded wireguard on it and now that interface with the handshake is no longer there.
double check the keys in pfsense and in the client.. maybe regenerate them and reapply ?
-
@mcury I did. I mean it's green and the handshake is successful for a reason I think? Going to retry but I think it's something with the firewall or routing. Do I need to create static routing so I can see my LAN on the other subnet for me to see it?
-
@korr2221 said in One tunnel for remote access:
@mcury I did. I mean it's green and the handshake is successful for a reason I think? Going to retry but I think it's something with the firewall or routing. Do I need to create static routing so I can see my LAN on the other subnet for me to see it?
No, no static route required.
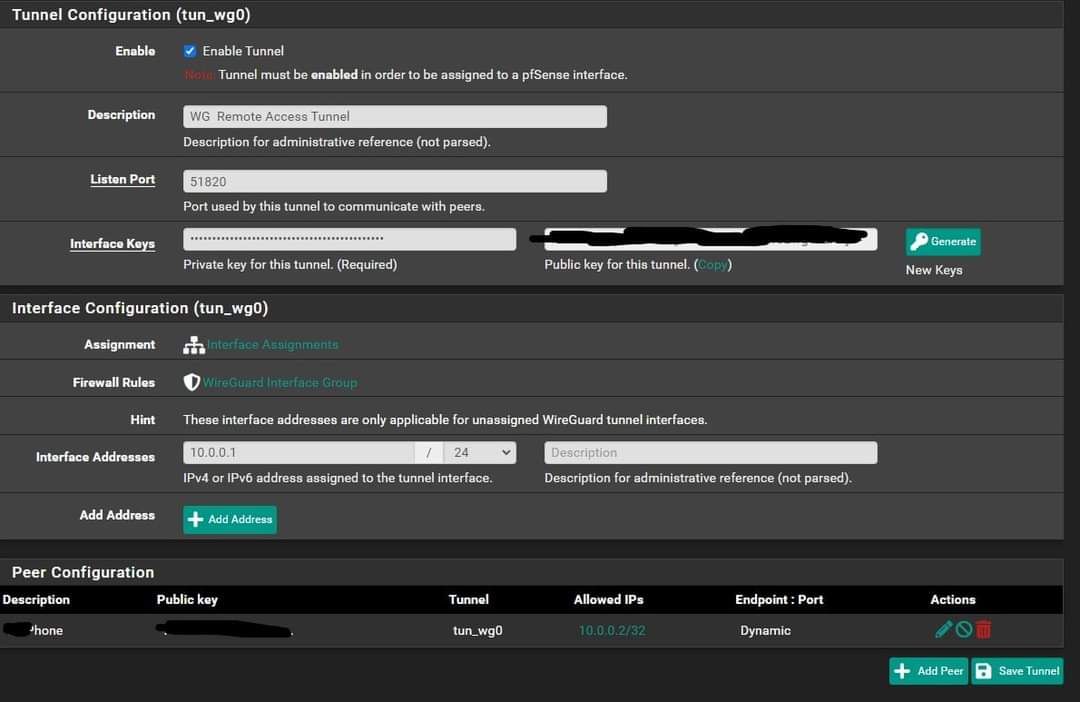
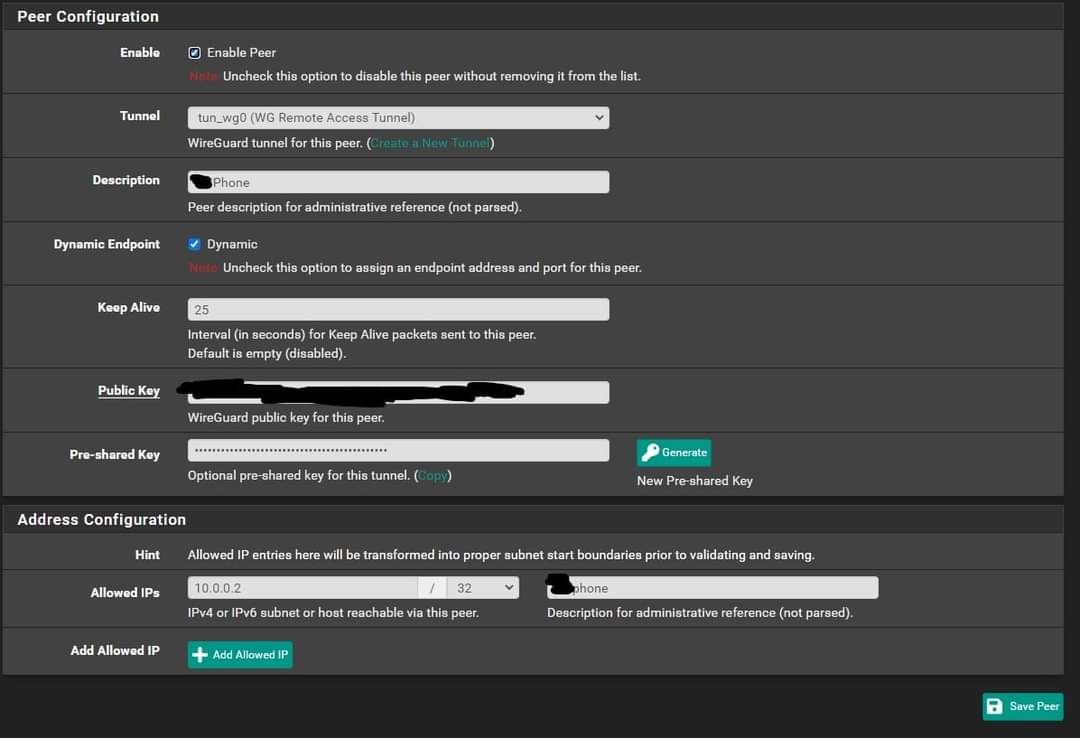
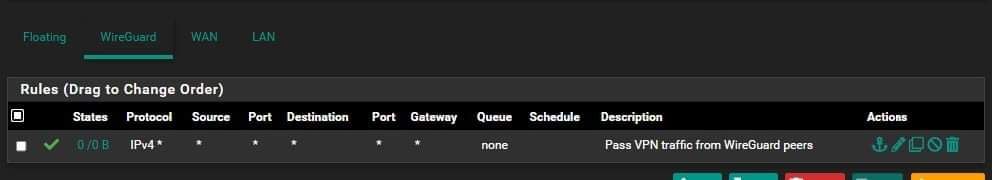
Follows my configuration:
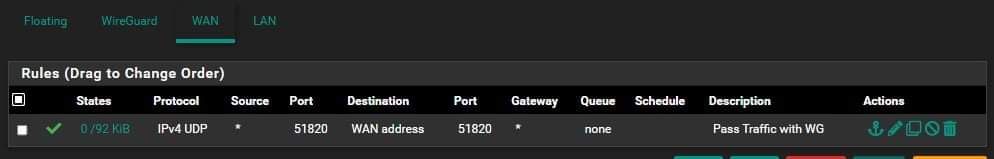
Firewall WAN rule:
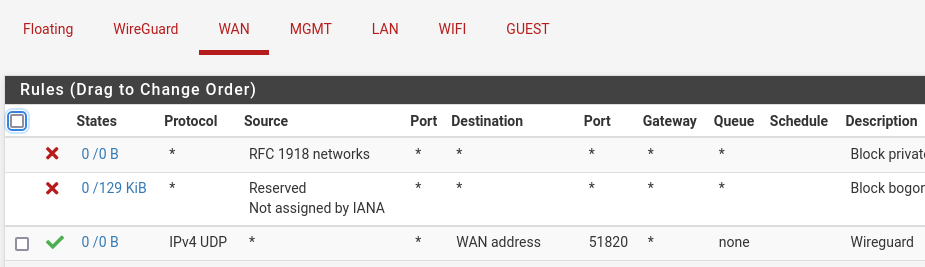
Wireguard allow rule:
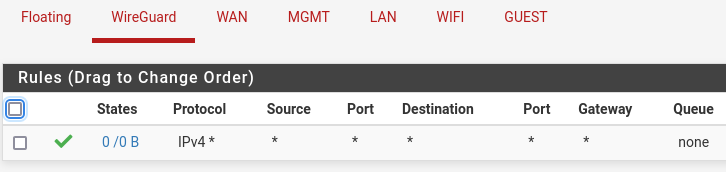
Tunnel setup:
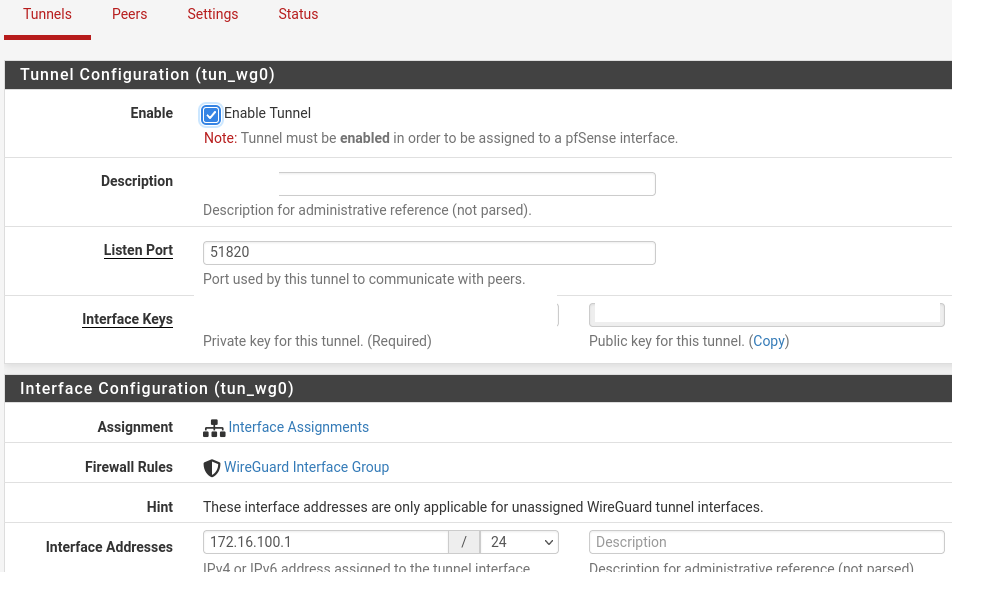
Peer setup:
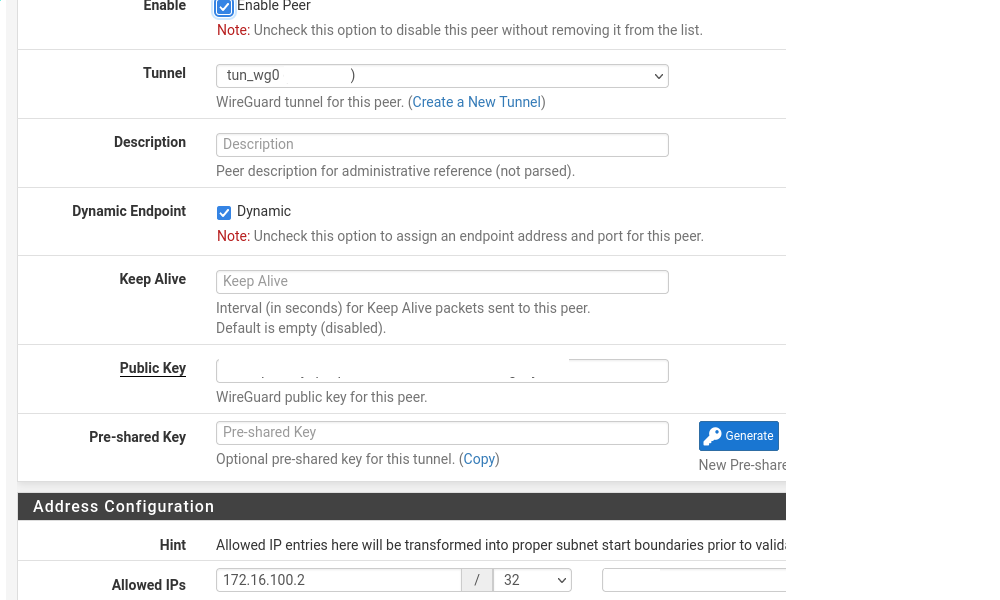
Wireguard app in my phone:
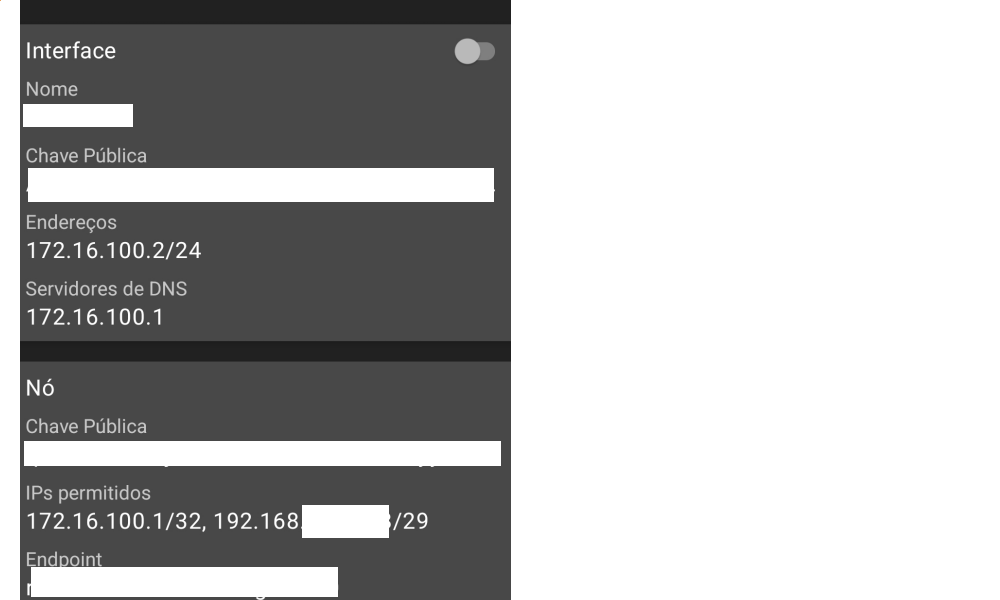
-
@korr2221 the weirdest thing ever. So I reinstalled WG twice, and all i did was change the order of the allowed IPs. Where I would put 0.0.0.0/0 in the middle. Suddenly it works now.
-
@korr2221 said in One tunnel for remote access:
@korr2221 the weirdest thing ever. So I reinstalled WG twice, and all i did was change the order of the allowed IPs. Where I would put 0.0.0.0/0 in the middle. Suddenly it works now.
Weird indeed.. full tunnel is that you want? If so, you need an outbound NAT as well.
Only 0.0.0.0/0 won't work. -
@mcury i didn't really need full tunnel, but for whatever reason that made it work adding the 0.0.0.0/0 scope. Can someone explain? LOL.
I know I needed to adjust the NAT if I want full tunnel. But at this point it works and I am happy.
Just checked my NAT settings, ZERO NAT rules. No idea what's going on.
-
@korr2221 said in One tunnel for remote access:
@mcury i didn't really need full tunnel, but for whatever reason that made it work adding the 0.0.0.0/0 scope. Can someone explain? LOL
0.0.0.0/0 will route everything that is connected to wireguard through the tunnel, including internet access, but you would also need an outbound NAT created.
Split tunnel (0.0.0.0/0 not included in allowed-ips) you will only gain access to the networks included in allowed-ips.
Full tunnel (0.0.0.0/0 included in allowed-ips), wireguard connections will be routed to the internet as well. -
@mcury just realized my LAN works but can't access public sites. It works without the 0.0.0.0/0 I'm guessing adding it in the middle did something and now it works like it's supposed to. But still having trouble with public sites. Odd...
-
@korr2221 nevermind. Changed my DNS from comcast to 1.1.1.1 now all is working normally. WHAT? :3
-
@korr2221 said in One tunnel for remote access:
@mcury just realized my LAN works but can't access public sites. It works without the 0.0.0.0/0 I'm guessing adding it in the middle did something and now it works like it's supposed to. But still having trouble with public sites. Odd...
Do you want to use the Internet from pfsense while connected to wireguard?
Or the phone Internet? -
@mcury it doesn't matter. I know if I want to use the internet from pfsense it is full tunnel and if I want from my phone it's split tunnel. But after changing my dns my split tunnel works correctly now. Odd!
-
@korr2221 It doesn't matter? Really? Ok then.
-
@mcury well i mean for some people it would. but for me, I just wanted to have remote access. haha.
-
@korr2221 said in One tunnel for remote access:
@mcury well i mean for some people it would. but for me, I just wanted to have remote access. haha.
So, you just want to access local resources? That's all?
Remove 0.0.0.0/0 from the allowed ips configuration file, and leave the configuration in pfsense exactly as I posted above. -
@mcury I have. I think you missed the one post above. I know the 0.0.0.0/0 doesn't belong. I was in the midst of trying full tunnel settings and somehow it kicked it in. Then worked after I removed it.
I'm okay now. I think maybe reinstalling WG package did something.
-
@korr2221 said in One tunnel for remote access:
@mcury I have. I think you missed the one post above. I know the 0.0.0.0/0 doesn't belong. I was in the midst of trying full tunnel settings and somehow it kicked it in. Then worked after I removed it.
Its kind of hard to understand what you are trying to do over there, you are not being clear about your objective.
If you remove 0.0.0.0/0, the Internet will work, but its not going to be a full tunnel, which means that websites on the internet will be accessed through your local internet, and not through pfsense internet.
If you put the 0.0.0.0/0, and configure the outbound NAT, its going to be a full tunnel, which means that websites on the internet will be accessed using the pfsense Internet, thus going through the tunnel.
You said that removing 0.0.0.0/0 is working, so you have a split tunnel, which is used only to access local resources in allowed-ips field. Web sites on the internet are actually been accessed using the Internet from wherever you are connecting from.
-
@mcury since that post I have removed the 0.0.0.0/0 and am currently using split tunnel fine now. After changing my DNS all is working. I understand. All is well, it works!
-
@korr2221 said in One tunnel for remote access:
@mcury since that post I have removed the 0.0.0.0/0 and am currently using split tunnel fine now. After changing my DNS all is working. I understand. All is well, it works!
Oh, great then =) One less thing to worry about now
-
@mcury Thank you for your patience and understanding. :)