UPnP Fix for multiple clients/consoles playing the same game
-
Okay, so here are the logs from when Playstation boots up (10.0.0.18) - (x'd out Public IP):
Feb 18 12:53:51 Firewall miniupnpd[94330]: SSDP M-SEARCH from 10.0.0.18:51183 ST: urn:schemas-upnp-org:device:InternetGatewayDevice:1
Feb 18 12:53:51 Firewall miniupnpd[94330]: Single search found
Feb 18 12:53:51 Firewall miniupnpd[94330]: SendSSDPResponse(): 0 bytes to 10.0.0.18:51183 ST: HTTP/1.1 200 OK^M CACHE-CONTROL: max-age=120^M ST: urn:schemas-upnp-org:device:InternetGatewayDevice:1^M USN: uuid:2fdeeab1-42c9-19cc-8e38-93771b9fc28::urn:schemas-upnp-org:device:InternetGatewayDevice:1^M EXT:^M SERVER: FreeBSD/12.3-STABLE UPnP/1.1 MiniUPnPd/2.2.1^M LOCATION: http://10.0.0.254:2189/rootDesc.xml^M OPT: "http://schemas.upnp.org/upnp/1/0/"; ns=01^M 01-NLS: 1645206819^M BOOTID.UPNP.ORG: 1645206819^M CONFIGID.UPNP.ORG: 1337^M ^M
Feb 18 12:53:51 Firewall miniupnpd[94330]: HTTP REQUEST from 10.0.0.18:62124 : GET /rootDesc.xml (HTTP/1.1)
Feb 18 12:53:51 Firewall miniupnpd[94330]: Host: 10.0.0.254:2189
Feb 18 12:53:51 Firewall miniupnpd[94330]: HTTP REQUEST from 10.0.0.18:62125 : POST /ctl/IPConn (HTTP/1.1)
Feb 18 12:53:51 Firewall miniupnpd[94330]: Host: 10.0.0.254:2189
Feb 18 12:53:51 Firewall miniupnpd[94330]: SOAPAction: urn:schemas-upnp-org:service:WANIPConnection:1#GetExternalIPAddress
Feb 18 12:53:51 Firewall miniupnpd[94330]: HTTP REQUEST from 10.0.0.18:62126 : POST /ctl/IPConn (HTTP/1.1)
Feb 18 12:53:51 Firewall miniupnpd[94330]: Host: 10.0.0.254:2189
Feb 18 12:53:51 Firewall miniupnpd[94330]: SOAPAction: urn:schemas-upnp-org:service:WANIPConnection:1#AddPortMapping
Feb 18 12:53:51 Firewall miniupnpd[94330]: AddPortMapping: ext port 9308 to 10.0.0.18:9308 protocol UDP for: 10.0.0.18:9308 to 9308 (UDP) leaseduration=0 rhost=
Feb 18 12:53:51 Firewall miniupnpd[94330]: UPnP permission rule 0 matched : port mapping accepted
Feb 18 12:53:51 Firewall miniupnpd[94330]: Check protocol udp for port 9308 on ext_if em0 x.x.x.x , 859168D0
Feb 18 12:53:51 Firewall miniupnpd[94330]: fe00000a:28982 00000000:0 <=> 9308 859168d0:9308
Feb 18 12:53:51 Firewall miniupnpd[94330]: 00000000:1900 00000000:0 <=> 9308 859168d0:9308
Feb 18 12:53:51 Firewall miniupnpd[94330]: 00000000:514 00000000:0 <=> 9308 859168d0:9308
Feb 18 12:53:51 Firewall miniupnpd[94330]: 00000000:67 00000000:0 <=> 9308 859168d0:9308
Feb 18 12:53:51 Firewall miniupnpd[94330]: 0200080a:123 00000000:0 <=> 9308 859168d0:9308
Feb 18 12:53:51 Firewall miniupnpd[94330]: 0b02080a:123 00000000:0 <=> 9308 859168d0:9308
Feb 18 12:53:51 Firewall miniupnpd[94330]: 0502080a:123 00000000:0 <=> 9308 859168d0:9308
Feb 18 12:53:51 Firewall miniupnpd[94330]: 01e6fa0a:123 00000000:0 <=> 9308 859168d0:9308
Feb 18 12:53:51 Firewall miniupnpd[94330]: fe14000a:123 00000000:0 <=> 9308 859168d0:9308
Feb 18 12:53:51 Firewall miniupnpd[94330]: fe0a000a:123 00000000:0 <=> 9308 859168d0:9308
Feb 18 12:53:51 Firewall miniupnpd[94330]: 0100007f:123 00000000:0 <=> 9308 859168d0:9308
Feb 18 12:53:51 Firewall miniupnpd[94330]: fe00000a:123 00000000:0 <=> 9308 859168d0:9308
Feb 18 12:53:51 Firewall miniupnpd[94330]: 859168d0:123 00000000:0 <=> 9308 859168d0:9308
Feb 18 12:53:51 Firewall miniupnpd[94330]: 00000000:123 00000000:0 <=> 9308 859168d0:9308
Feb 18 12:53:51 Firewall miniupnpd[94330]: 859168d0:11462 00000000:0 <=> 9308 859168d0:9308
Feb 18 12:53:51 Firewall miniupnpd[94330]: 859168d0:56449 00000000:0 <=> 9308 859168d0:9308
Feb 18 12:53:51 Firewall miniupnpd[94330]: 859168d0:37906 00000000:0 <=> 9308 859168d0:9308
Feb 18 12:53:51 Firewall miniupnpd[94330]: 859168d0:44561 00000000:0 <=> 9308 859168d0:9308
Feb 18 12:53:51 Firewall miniupnpd[94330]: 0100007f:53 00000000:0 <=> 9308 859168d0:9308
Feb 18 12:53:51 Firewall miniupnpd[94330]: fe00000a:53 00000000:0 <=> 9308 859168d0:9308
Feb 18 12:53:51 Firewall miniupnpd[94330]: 859168d0:1194 00000000:0 <=> 9308 859168d0:9308
Feb 18 12:53:51 Firewall miniupnpd[94330]: 00000000:0 00000000:0 <=> 9308 859168d0:9308
Feb 18 12:53:51 Firewall miniupnpd[94330]: redirecting port 9308 to 10.0.0.18:9308 protocol UDP for: 10.0.0.18:9308 to 9308 (UDP)
Feb 18 12:53:51 Firewall miniupnpd[94330]: use external ip xxx.xxx.xxx.xxx
Feb 18 12:53:52 Firewall miniupnpd[94330]: level=0 type=20
Feb 18 12:53:52 Firewall miniupnpd[94330]: sdl_index = 2 em1:0.c1.a2.20.12.31
Feb 18 12:53:52 Firewall miniupnpd[94330]: ST: urn:schemas-upnp-org:device:InternetGatewayDevice:1 (ver=1)
Feb 18 12:53:52 Firewall miniupnpd[94330]: SSDP M-SEARCH from 10.0.0.18:53977 ST: urn:schemas-upnp-org:device:InternetGatewayDevice:1
Feb 18 12:53:52 Firewall miniupnpd[94330]: Single search found
Feb 18 12:53:52 Firewall miniupnpd[94330]: SendSSDPResponse(): 0 bytes to 10.0.0.18:53977 ST: HTTP/1.1 200 OK^M CACHE-CONTROL: max-age=120^M ST: urn:schemas-upnp-org:device:InternetGatewayDevice:1^M USN: uuid:2fdeeab1-42c9-19cc-8e38-93771b9fc28::urn:schemas-upnp-org:device:InternetGatewayDevice:1^M EXT:^M SERVER: FreeBSD/12.3-STABLE UPnP/1.1 MiniUPnPd/2.2.1^M LOCATION: http://10.0.0.254:2189/rootDesc.xml^M OPT: "http://schemas.upnp.org/upnp/1/0/"; ns=01^M 01-NLS: 1645206819^M BOOTID.UPNP.ORG: 1645206819^M CONFIGID.UPNP.ORG: 1337^M ^M
Feb 18 12:53:52 Firewall miniupnpd[94330]: HTTP REQUEST from 10.0.0.18:62130 : GET /rootDesc.xml (HTTP/1.1)
Feb 18 12:53:52 Firewall miniupnpd[94330]: Host: 10.0.0.254:2189
Feb 18 12:53:52 Firewall miniupnpd[94330]: HTTP REQUEST from 10.0.0.18:62131 : POST /ctl/IPConn (HTTP/1.1)
Feb 18 12:53:52 Firewall miniupnpd[94330]: Host: 10.0.0.254:2189
Feb 18 12:53:52 Firewall miniupnpd[94330]: SOAPAction: urn:schemas-upnp-org:service:WANIPConnection:1#GetExternalIPAddress
Feb 18 12:53:52 Firewall miniupnpd[94330]: HTTP REQUEST from 10.0.0.18:62132 : POST /ctl/IPConn (HTTP/1.1)
Feb 18 12:53:52 Firewall miniupnpd[94330]: Host: 10.0.0.254:2189
Feb 18 12:53:52 Firewall miniupnpd[94330]: SOAPAction: urn:schemas-upnp-org:service:WANIPConnection:1#AddPortMapping
Feb 18 12:53:52 Firewall miniupnpd[94330]: AddPortMapping: ext port 9308 to 10.0.0.18:9308 protocol UDP for: 10.0.0.18:9308 to 9308 (UDP) leaseduration=0 rhost=
Feb 18 12:53:52 Firewall miniupnpd[94330]: UPnP permission rule 0 matched : port mapping accepted
Feb 18 12:53:52 Firewall miniupnpd[94330]: updating existing port mapping 9308 UDP (rhost '') => 10.0.0.18:9308Here is the 2nd Playstation (10.0.0.19) attempting to map port 9308:
Feb 18 12:54:03 Firewall miniupnpd[94330]: SSDP M-SEARCH from 10.0.0.19:56592 ST: urn:schemas-upnp-org:device:InternetGatewayDevice:1
Feb 18 12:54:03 Firewall miniupnpd[94330]: Single search found
Feb 18 12:54:03 Firewall miniupnpd[94330]: SendSSDPResponse(): 0 bytes to 10.0.0.19:56592 ST: HTTP/1.1 200 OK^M CACHE-CONTROL: max-age=120^M ST: urn:schemas-upnp-org:device:InternetGatewayDevice:1^M USN: uuid:2fdeeab1-42c9-19cc-8e38-93771b9fc28::urn:schemas-upnp-org:device:InternetGatewayDevice:1^M EXT:^M SERVER: FreeBSD/12.3-STABLE UPnP/1.1 MiniUPnPd/2.2.1^M LOCATION: http://10.0.0.254:2189/rootDesc.xml^M OPT: "http://schemas.upnp.org/upnp/1/0/"; ns=01^M 01-NLS: 1645206819^M BOOTID.UPNP.ORG: 1645206819^M CONFIGID.UPNP.ORG: 1337^M ^M
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6180 2 14
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6100 2 13
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6080 2 12
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6000 2 11
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6180 2 14 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6100 2 13 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6080 2 12 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6000 2 11 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6180 2 14
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6100 2 13
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6080 2 12
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6000 2 11
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6180 2 14 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6100 2 13 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6080 2 12 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6000 2 11 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6180 2 14
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6100 2 13
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6080 2 12
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6000 2 11
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6180 2 14 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6100 2 13 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6080 2 12 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6000 2 11 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6180 2 14
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6100 2 13
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6080 2 12
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6000 2 11
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6180 2 14 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6100 2 13 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6080 2 12 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6000 2 11 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: HTTP REQUEST from 10.0.0.19:65238 : GET /rootDesc.xml (HTTP/1.1)
Feb 18 12:54:03 Firewall miniupnpd[94330]: Host: 10.0.0.254:2189
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6180 2 14
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6100 2 13
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6080 2 12
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6000 2 11
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6180 2 14 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6100 2 13 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6080 2 12 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6000 2 11 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6180 2 14
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6100 2 13
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6080 2 12
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6000 2 11
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6180 2 14 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6100 2 13 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6080 2 12 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6000 2 11 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: HTTP REQUEST from 10.0.0.19:65239 : POST /ctl/IPConn (HTTP/1.1)
Feb 18 12:54:03 Firewall miniupnpd[94330]: Host: 10.0.0.254:2189
Feb 18 12:54:03 Firewall miniupnpd[94330]: SOAPAction: urn:schemas-upnp-org:service:WANIPConnection:1#GetExternalIPAddress
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6180 2 14
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6100 2 13
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6080 2 12
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6000 2 11
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6180 2 14 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6100 2 13 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6080 2 12 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6000 2 11 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6180 2 14
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6100 2 13
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6080 2 12
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6000 2 11
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6180 2 14 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6100 2 13 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6080 2 12 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6000 2 11 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: HTTP REQUEST from 10.0.0.19:65240 : POST /ctl/IPConn (HTTP/1.1)
Feb 18 12:54:03 Firewall miniupnpd[94330]: Host: 10.0.0.254:2189
Feb 18 12:54:03 Firewall miniupnpd[94330]: SOAPAction: urn:schemas-upnp-org:service:WANIPConnection:1#AddPortMapping
Feb 18 12:54:03 Firewall miniupnpd[94330]: AddPortMapping: ext port 9308 to 10.0.0.19:9308 protocol UDP for: 10.0.0.19:9308 to 9308 (UDP) leaseduration=0 rhost=
Feb 18 12:54:03 Firewall miniupnpd[94330]: UPnP permission rule 1 matched : port mapping accepted
Feb 18 12:54:03 Firewall miniupnpd[94330]: port 9308 UDP (rhost '') already redirected to 10.0.0.18:9308
Feb 18 12:54:03 Firewall miniupnpd[94330]: Returning UPnPError 718: ConflictInMappingEntry
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6180 2 14
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6100 2 13
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6080 2 12
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6000 2 11
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6180 2 14 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6100 2 13 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6080 2 12 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6000 2 11 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: level=0 type=20
Feb 18 12:54:03 Firewall miniupnpd[94330]: sdl_index = 2 em1:0.c1.a2.20.12.31
Feb 18 12:54:03 Firewall miniupnpd[94330]: ST: urn:schemas-upnp-org:device:InternetGatewayDevice:1 (ver=1)
Feb 18 12:54:03 Firewall miniupnpd[94330]: SSDP M-SEARCH from 10.0.0.19:52932 ST: urn:schemas-upnp-org:device:InternetGatewayDevice:1
Feb 18 12:54:03 Firewall miniupnpd[94330]: Single search found
Feb 18 12:54:03 Firewall miniupnpd[94330]: SendSSDPResponse(): 0 bytes to 10.0.0.19:52932 ST: HTTP/1.1 200 OK^M CACHE-CONTROL: max-age=120^M ST: urn:schemas-upnp-org:device:InternetGatewayDevice:1^M USN: uuid:2fdeeab1-42c9-19cc-8e38-93771b9fc28::urn:schemas-upnp-org:device:InternetGatewayDevice:1^M EXT:^M SERVER: FreeBSD/12.3-STABLE UPnP/1.1 MiniUPnPd/2.2.1^M LOCATION: http://10.0.0.254:2189/rootDesc.xml^M OPT: "http://schemas.upnp.org/upnp/1/0/"; ns=01^M 01-NLS: 1645206819^M BOOTID.UPNP.ORG: 1645206819^M CONFIGID.UPNP.ORG: 1337^M ^M
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6180 2 14
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6100 2 13
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6080 2 12
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6000 2 11
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6180 2 14 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6100 2 13 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6080 2 12 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6000 2 11 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6180 2 14
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6100 2 13
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6080 2 12
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6000 2 11
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6180 2 14 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6100 2 13 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6080 2 12 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6000 2 11 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6180 2 14
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6100 2 13
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6080 2 12
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6000 2 11
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6180 2 14 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6100 2 13 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6080 2 12 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6000 2 11 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6180 2 14
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6100 2 13
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6080 2 12
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6000 2 11
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6180 2 14 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6100 2 13 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6080 2 12 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6000 2 11 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: HTTP REQUEST from 10.0.0.19:65250 : GET /rootDesc.xml (HTTP/1.1)
Feb 18 12:54:03 Firewall miniupnpd[94330]: Host: 10.0.0.254:2189
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6180 2 14
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6100 2 13
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6080 2 12
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6000 2 11
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6180 2 14 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6100 2 13 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6080 2 12 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6000 2 11 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6180 2 14
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6100 2 13
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6080 2 12
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6000 2 11
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6180 2 14 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6100 2 13 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6080 2 12 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6000 2 11 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: HTTP REQUEST from 10.0.0.19:65251 : POST /ctl/IPConn (HTTP/1.1)
Feb 18 12:54:03 Firewall miniupnpd[94330]: Host: 10.0.0.254:2189
Feb 18 12:54:03 Firewall miniupnpd[94330]: SOAPAction: urn:schemas-upnp-org:service:WANIPConnection:1#GetExternalIPAddress
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6180 2 14
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6100 2 13
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6080 2 12
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6000 2 11
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6180 2 14 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6100 2 13 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6080 2 12 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6000 2 11 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6180 2 14
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6100 2 13
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6080 2 12
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6000 2 11
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6180 2 14 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6100 2 13 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6080 2 12 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6000 2 11 0 0
Feb 18 12:54:03 Firewall miniupnpd[94330]: HTTP REQUEST from 10.0.0.19:65252 : POST /ctl/IPConn (HTTP/1.1)
Feb 18 12:54:03 Firewall miniupnpd[94330]: Host: 10.0.0.254:2189
Feb 18 12:54:03 Firewall miniupnpd[94330]: SOAPAction: urn:schemas-upnp-org:service:WANIPConnection:1#AddPortMapping
Feb 18 12:54:03 Firewall miniupnpd[94330]: AddPortMapping: ext port 9308 to 10.0.0.19:9308 protocol UDP for: 10.0.0.19:9308 to 9308 (UDP) leaseduration=0 rhost=
Feb 18 12:54:03 Firewall miniupnpd[94330]: UPnP permission rule 1 matched : port mapping accepted
Feb 18 12:54:03 Firewall miniupnpd[94330]: port 9308 UDP (rhost '') already redirected to 10.0.0.18:9308
Feb 18 12:54:03 Firewall miniupnpd[94330]: Returning UPnPError 718: ConflictInMappingEntry
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6180 2 14
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6100 2 13
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6080 2 12
Feb 18 12:54:03 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6000 2 11
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6180 2 14 0 0
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6100 2 13 0 0
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6080 2 12 0 0
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6000 2 11 0 0
Feb 18 12:54:04 Firewall miniupnpd[94330]: level=0 type=20
Feb 18 12:54:04 Firewall miniupnpd[94330]: sdl_index = 2 em1:0.c1.a2.20.12.31
Feb 18 12:54:04 Firewall miniupnpd[94330]: ST: urn:schemas-upnp-org:device:InternetGatewayDevice:1 (ver=1)
Feb 18 12:54:04 Firewall miniupnpd[94330]: SSDP M-SEARCH from 10.0.0.19:56976 ST: urn:schemas-upnp-org:device:InternetGatewayDevice:1
Feb 18 12:54:04 Firewall miniupnpd[94330]: Single search found
Feb 18 12:54:04 Firewall miniupnpd[94330]: SendSSDPResponse(): 0 bytes to 10.0.0.19:56976 ST: HTTP/1.1 200 OK^M CACHE-CONTROL: max-age=120^M ST: urn:schemas-upnp-org:device:InternetGatewayDevice:1^M USN: uuid:2fdeeab1-42c9-19cc-8e38-93771b9fc28::urn:schemas-upnp-org:device:InternetGatewayDevice:1^M EXT:^M SERVER: FreeBSD/12.3-STABLE UPnP/1.1 MiniUPnPd/2.2.1^M LOCATION: http://10.0.0.254:2189/rootDesc.xml^M OPT: "http://schemas.upnp.org/upnp/1/0/"; ns=01^M 01-NLS: 1645206819^M BOOTID.UPNP.ORG: 1645206819^M CONFIGID.UPNP.ORG: 1337^M ^M
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6180 2 14
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6100 2 13
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6080 2 12
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6000 2 11
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6180 2 14 0 0
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6100 2 13 0 0
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6080 2 12 0 0
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6000 2 11 0 0
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6180 2 14
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6100 2 13
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6080 2 12
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6000 2 11
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6180 2 14 0 0
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6100 2 13 0 0
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6080 2 12 0 0
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6000 2 11 0 0
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6180 2 14
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6100 2 13
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6080 2 12
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6000 2 11
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6180 2 14 0 0
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6100 2 13 0 0
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6080 2 12 0 0
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6000 2 11 0 0
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6180 2 14
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6100 2 13
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6080 2 12
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6000 2 11
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6180 2 14 0 0
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6100 2 13 0 0
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6080 2 12 0 0
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6000 2 11 0 0
Feb 18 12:54:04 Firewall miniupnpd[94330]: HTTP REQUEST from 10.0.0.19:65264 : GET /rootDesc.xml (HTTP/1.1)
Feb 18 12:54:04 Firewall miniupnpd[94330]: Host: 10.0.0.254:2189
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6180 2 14
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6100 2 13
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6080 2 12
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6000 2 11
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6180 2 14 0 0
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6100 2 13 0 0
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6080 2 12 0 0
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6000 2 11 0 0
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6180 2 14
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6100 2 13
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6080 2 12
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6000 2 11
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6180 2 14 0 0
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6100 2 13 0 0
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6080 2 12 0 0
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6000 2 11 0 0
Feb 18 12:54:04 Firewall miniupnpd[94330]: HTTP REQUEST from 10.0.0.19:65265 : POST /ctl/IPConn (HTTP/1.1)
Feb 18 12:54:04 Firewall miniupnpd[94330]: Host: 10.0.0.254:2189
Feb 18 12:54:04 Firewall miniupnpd[94330]: SOAPAction: urn:schemas-upnp-org:service:WANIPConnection:1#GetExternalIPAddress
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6180 2 14
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6100 2 13
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6080 2 12
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6000 2 11
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6180 2 14 0 0
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6100 2 13 0 0
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6080 2 12 0 0
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6000 2 11 0 0
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6180 2 14
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6100 2 13
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6080 2 12
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_selectfds: 0x800ab6000 2 11
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6180 2 14 0 0
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6100 2 13 0 0
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6080 2 12 0 0
Feb 18 12:54:04 Firewall miniupnpd[94330]: upnpevents_processfds: 0x800ab6000 2 11 0 0
Feb 18 12:54:04 Firewall miniupnpd[94330]: HTTP REQUEST from 10.0.0.19:65266 : POST /ctl/IPConn (HTTP/1.1)
Feb 18 12:54:04 Firewall miniupnpd[94330]: Host: 10.0.0.254:2189
Feb 18 12:54:04 Firewall miniupnpd[94330]: SOAPAction: urn:schemas-upnp-org:service:WANIPConnection:1#AddPortMapping
Feb 18 12:54:04 Firewall miniupnpd[94330]: AddPortMapping: ext port 9308 to 10.0.0.19:9308 protocol UDP for: 10.0.0.19:9308 to 9308 (UDP) leaseduration=0 rhost=
Feb 18 12:54:04 Firewall miniupnpd[94330]: UPnP permission rule 1 matched : port mapping accepted
Feb 18 12:54:04 Firewall miniupnpd[94330]: port 9308 UDP (rhost '') already redirected to 10.0.0.18:9308
Feb 18 12:54:04 Firewall miniupnpd[94330]: Returning UPnPError 718: ConflictInMappingEntry -
@saber
You can see that it isn't trying new ports, so its stuck in a death spiral that it will never escape. Sad that Sony implemented that way. Maybe it doesn't like the 718 error, and other UPnP servers handle that differently? Dunno.So you may not ever get your PS itself show the right NAT type, but I am curious as to what the games show.
-
@encrypt1d said in UPnP Fix for multiple clients/consoles playing the same game:
@saber
You can see that it isn't trying new ports, so its stuck in a death spiral that it will never escape. Sad that Sony implemented that way. Maybe it doesn't like the 718 error, and other UPnP servers handle that differently? Dunno.So you may not ever get your PS itself show the right NAT type, but I am curious as to what the games show.
Most of the games I play online don't show anything about the NAT. Its weird that with a Linux based firewall, they'll both show up with NAT Type 2 at the same time, so Linux is likely doing something very different.
If I put in the static port mappings, they both get a NAT Type 2, even without the Pure NAT enabled.
-
Confirmed, add the Static port mapping back in and both consoles now show NAT Type 2. Weird, wonder what the difference is. I'll have to do another log capture later and see what the differences in behavior are.
-
So I'm definitely at a loss... lol According to the UPnP RFC Sony isn't following the recommendations of how to handle error code 718. But I have no idea why that I see zero change in behavior miniupnp wise, but Playstation is reporting NAT Type 2 with static port mapping enabled, but no change in miniupnp response.
See below (public IP X'd out.):
First Playstation to bootup and get online.
Feb 19 11:20:05 Firewall miniupnpd[61453]: SSDP M-SEARCH from 10.0.0.19:50995 ST: urn:schemas-upnp-org:device:InternetGatewayDevice:1
Feb 19 11:20:05 Firewall miniupnpd[61453]: Single search found
Feb 19 11:20:05 Firewall miniupnpd[61453]: SendSSDPResponse(): 0 bytes to 10.0.0.19:50995 ST: HTTP/1.1 200 OK^M CACHE-CONTROL: max-age=120^M ST: urn:schemas-upnp-org:device:InternetGatewayDevice:1^M USN: uuid:2fdeeab1-42c9-19cc-8e38-93771b9fc28::urn:schemas-upnp-org:device:InternetGatewayDevice:1^M EXT:^M SERVER: FreeBSD/12.3-STABLE UPnP/1.1 MiniUPnPd/2.2.1^M LOCATION: http://10.0.0.254:2189/rootDesc.xml^M OPT: "http://schemas.upnp.org/upnp/1/0/"; ns=01^M 01-NLS: 1645287585^M BOOTID.UPNP.ORG: 1645287585^M CONFIGID.UPNP.ORG: 1337^M ^M
Feb 19 11:20:05 Firewall miniupnpd[61453]: HTTP REQUEST from 10.0.0.19:49778 : GET /rootDesc.xml (HTTP/1.1)
Feb 19 11:20:05 Firewall miniupnpd[61453]: Host: 10.0.0.254:2189
Feb 19 11:20:05 Firewall miniupnpd[61453]: HTTP REQUEST from 10.0.0.19:49779 : POST /ctl/IPConn (HTTP/1.1)
Feb 19 11:20:05 Firewall miniupnpd[61453]: Host: 10.0.0.254:2189
Feb 19 11:20:05 Firewall miniupnpd[61453]: SOAPAction: urn:schemas-upnp-org:service:WANIPConnection:1#GetExternalIPAddress
Feb 19 11:20:05 Firewall miniupnpd[61453]: HTTP REQUEST from 10.0.0.19:49780 : POST /ctl/IPConn (HTTP/1.1)
Feb 19 11:20:05 Firewall miniupnpd[61453]: Host: 10.0.0.254:2189
Feb 19 11:20:05 Firewall miniupnpd[61453]: SOAPAction: urn:schemas-upnp-org:service:WANIPConnection:1#AddPortMapping
Feb 19 11:20:05 Firewall miniupnpd[61453]: AddPortMapping: ext port 9308 to 10.0.0.19:9308 protocol UDP for: 10.0.0.19:9308 to 9308 (UDP) leaseduration=0 rhost=
Feb 19 11:20:05 Firewall miniupnpd[61453]: UPnP permission rule 1 matched : port mapping accepted
Feb 19 11:20:05 Firewall miniupnpd[61453]: Check protocol udp for port 9308 on ext_if em0 xxx.xxx.xxx.xxx, 859168D0
Feb 19 11:20:05 Firewall miniupnpd[61453]: fe00000a:22827 00000000:0 <=> 9308 859168d0:9308
Feb 19 11:20:05 Firewall miniupnpd[61453]: 00000000:1900 00000000:0 <=> 9308 859168d0:9308
Feb 19 11:20:05 Firewall miniupnpd[61453]: 00000000:67 00000000:0 <=> 9308 859168d0:9308
Feb 19 11:20:05 Firewall miniupnpd[61453]: 0100007f:53 00000000:0 <=> 9308 859168d0:9308
Feb 19 11:20:05 Firewall miniupnpd[61453]: fe00000a:53 00000000:0 <=> 9308 859168d0:9308
Feb 19 11:20:05 Firewall miniupnpd[61453]: 0a01080a:123 00000000:0 <=> 9308 859168d0:9308
Feb 19 11:20:05 Firewall miniupnpd[61453]: 859168d0:26424 00000000:0 <=> 9308 859168d0:9308
Feb 19 11:20:05 Firewall miniupnpd[61453]: 1200080a:123 00000000:0 <=> 9308 859168d0:9308
Feb 19 11:20:05 Firewall miniupnpd[61453]: 859168d0:1487 00000000:0 <=> 9308 859168d0:9308
Feb 19 11:20:05 Firewall miniupnpd[61453]: 0502080a:123 00000000:0 <=> 9308 859168d0:9308
Feb 19 11:20:05 Firewall miniupnpd[61453]: 859168d0:35710 00000000:0 <=> 9308 859168d0:9308
Feb 19 11:20:05 Firewall miniupnpd[61453]: 0800080a:123 00000000:0 <=> 9308 859168d0:9308
Feb 19 11:20:05 Firewall miniupnpd[61453]: 859168d0:2987 00000000:0 <=> 9308 859168d0:9308
Feb 19 11:20:05 Firewall miniupnpd[61453]: 00000000:514 00000000:0 <=> 9308 859168d0:9308
Feb 19 11:20:05 Firewall miniupnpd[61453]: 01e6fa0a:123 00000000:0 <=> 9308 859168d0:9308
Feb 19 11:20:05 Firewall miniupnpd[61453]: fe14000a:123 00000000:0 <=> 9308 859168d0:9308
Feb 19 11:20:05 Firewall miniupnpd[61453]: fe0a000a:123 00000000:0 <=> 9308 859168d0:9308
Feb 19 11:20:05 Firewall miniupnpd[61453]: 0100007f:123 00000000:0 <=> 9308 859168d0:9308
Feb 19 11:20:05 Firewall miniupnpd[61453]: fe00000a:123 00000000:0 <=> 9308 859168d0:9308
Feb 19 11:20:05 Firewall miniupnpd[61453]: 859168d0:123 00000000:0 <=> 9308 859168d0:9308
Feb 19 11:20:05 Firewall miniupnpd[61453]: 00000000:123 00000000:0 <=> 9308 859168d0:9308
Feb 19 11:20:05 Firewall miniupnpd[61453]: 859168d0:1194 00000000:0 <=> 9308 859168d0:9308
Feb 19 11:20:05 Firewall miniupnpd[61453]: 00000000:0 00000000:0 <=> 9308 859168d0:9308
Feb 19 11:20:05 Firewall miniupnpd[61453]: redirecting port 9308 to 10.0.0.19:9308 protocol UDP for: 10.0.0.19:9308 to 9308 (UDP)
Feb 19 11:20:05 Firewall miniupnpd[61453]: use external ip xxx.xxx.xxx.xxx
Feb 19 11:20:05 Firewall miniupnpd[61453]: level=0 type=20
Feb 19 11:20:05 Firewall miniupnpd[61453]: sdl_index = 2 em1:0.c1.a2.20.12.31
Feb 19 11:20:05 Firewall miniupnpd[61453]: ST: urn:schemas-upnp-org:device:InternetGatewayDevice:1 (ver=1)
Feb 19 11:20:05 Firewall miniupnpd[61453]: SSDP M-SEARCH from 10.0.0.19:62353 ST: urn:schemas-upnp-org:device:InternetGatewayDevice:1
Feb 19 11:20:05 Firewall miniupnpd[61453]: Single search found
Feb 19 11:20:05 Firewall miniupnpd[61453]: SendSSDPResponse(): 0 bytes to 10.0.0.19:62353 ST: HTTP/1.1 200 OK^M CACHE-CONTROL: max-age=120^M ST: urn:schemas-upnp-org:device:InternetGatewayDevice:1^M USN: uuid:2fdeeab1-42c9-19cc-8e38-93771b9fc28::urn:schemas-upnp-org:device:InternetGatewayDevice:1^M EXT:^M SERVER: FreeBSD/12.3-STABLE UPnP/1.1 MiniUPnPd/2.2.1^M LOCATION: http://10.0.0.254:2189/rootDesc.xml^M OPT: "http://schemas.upnp.org/upnp/1/0/"; ns=01^M 01-NLS: 1645287585^M BOOTID.UPNP.ORG: 1645287585^M CONFIGID.UPNP.ORG: 1337^M ^M
Feb 19 11:20:05 Firewall miniupnpd[61453]: HTTP REQUEST from 10.0.0.19:49781 : GET /rootDesc.xml (HTTP/1.1)
Feb 19 11:20:05 Firewall miniupnpd[61453]: Host: 10.0.0.254:2189
Feb 19 11:20:05 Firewall miniupnpd[61453]: HTTP REQUEST from 10.0.0.19:49782 : POST /ctl/IPConn (HTTP/1.1)
Feb 19 11:20:05 Firewall miniupnpd[61453]: Host: 10.0.0.254:2189
Feb 19 11:20:05 Firewall miniupnpd[61453]: SOAPAction: urn:schemas-upnp-org:service:WANIPConnection:1#GetExternalIPAddress
Feb 19 11:20:05 Firewall miniupnpd[61453]: HTTP REQUEST from 10.0.0.19:49783 : POST /ctl/IPConn (HTTP/1.1)
Feb 19 11:20:05 Firewall miniupnpd[61453]: Host: 10.0.0.254:2189
Feb 19 11:20:05 Firewall miniupnpd[61453]: SOAPAction: urn:schemas-upnp-org:service:WANIPConnection:1#AddPortMapping
Feb 19 11:20:05 Firewall miniupnpd[61453]: AddPortMapping: ext port 9308 to 10.0.0.19:9308 protocol UDP for: 10.0.0.19:9308 to 9308 (UDP) leaseduration=0 rhost=
Feb 19 11:20:05 Firewall miniupnpd[61453]: UPnP permission rule 1 matched : port mapping accepted
Feb 19 11:20:05 Firewall miniupnpd[61453]: updating existing port mapping 9308 UDP (rhost '') => 10.0.0.19:9308Second Playstation to bootup and get online:
Feb 19 11:20:59 Firewall miniupnpd[61453]: SSDP M-SEARCH from 10.0.0.18:56783 ST: urn:schemas-upnp-org:device:InternetGatewayDevice:1
Feb 19 11:20:59 Firewall miniupnpd[61453]: Single search found
Feb 19 11:20:59 Firewall miniupnpd[61453]: SendSSDPResponse(): 0 bytes to 10.0.0.18:56783 ST: HTTP/1.1 200 OK^M CACHE-CONTROL: max-age=120^M ST: urn:schemas-upnp-org:device:InternetGatewayDevice:1^M USN: uuid:2fdeeab1-42c9-19cc-8e38-93771b9fc28::urn:schemas-upnp-org:device:InternetGatewayDevice:1^M EXT:^M SERVER: FreeBSD/12.3-STABLE UPnP/1.1 MiniUPnPd/2.2.1^M LOCATION: http://10.0.0.254:2189/rootDesc.xml^M OPT: "http://schemas.upnp.org/upnp/1/0/"; ns=01^M 01-NLS: 1645287585^M BOOTID.UPNP.ORG: 1645287585^M CONFIGID.UPNP.ORG: 1337^M ^M
Feb 19 11:20:59 Firewall miniupnpd[61453]: HTTP REQUEST from 10.0.0.18:57528 : GET /rootDesc.xml (HTTP/1.1)
Feb 19 11:20:59 Firewall miniupnpd[61453]: Host: 10.0.0.254:2189
Feb 19 11:20:59 Firewall miniupnpd[61453]: HTTP REQUEST from 10.0.0.18:53101 : POST /ctl/IPConn (HTTP/1.1)
Feb 19 11:20:59 Firewall miniupnpd[61453]: Host: 10.0.0.254:2189
Feb 19 11:20:59 Firewall miniupnpd[61453]: SOAPAction: urn:schemas-upnp-org:service:WANIPConnection:1#GetExternalIPAddress
Feb 19 11:20:59 Firewall miniupnpd[61453]: HTTP REQUEST from 10.0.0.18:63652 : POST /ctl/IPConn (HTTP/1.1)
Feb 19 11:20:59 Firewall miniupnpd[61453]: Host: 10.0.0.254:2189
Feb 19 11:20:59 Firewall miniupnpd[61453]: SOAPAction: urn:schemas-upnp-org:service:WANIPConnection:1#AddPortMapping
Feb 19 11:20:59 Firewall miniupnpd[61453]: AddPortMapping: ext port 9308 to 10.0.0.18:9308 protocol UDP for: 10.0.0.18:9308 to 9308 (UDP) leaseduration=0 rhost=
Feb 19 11:20:59 Firewall miniupnpd[61453]: UPnP permission rule 0 matched : port mapping accepted
Feb 19 11:20:59 Firewall miniupnpd[61453]: port 9308 UDP (rhost '') already redirected to 10.0.0.19:9308
Feb 19 11:20:59 Firewall miniupnpd[61453]: Returning UPnPError 718: ConflictInMappingEntry
Feb 19 11:20:59 Firewall miniupnpd[61453]: level=0 type=20
Feb 19 11:20:59 Firewall miniupnpd[61453]: sdl_index = 2 em1:0.c1.a2.20.12.31
Feb 19 11:20:59 Firewall miniupnpd[61453]: ST: urn:schemas-upnp-org:device:InternetGatewayDevice:1 (ver=1)
Feb 19 11:20:59 Firewall miniupnpd[61453]: SSDP M-SEARCH from 10.0.0.18:56271 ST: urn:schemas-upnp-org:device:InternetGatewayDevice:1
Feb 19 11:20:59 Firewall miniupnpd[61453]: Single search found
Feb 19 11:20:59 Firewall miniupnpd[61453]: SendSSDPResponse(): 0 bytes to 10.0.0.18:56271 ST: HTTP/1.1 200 OK^M CACHE-CONTROL: max-age=120^M ST: urn:schemas-upnp-org:device:InternetGatewayDevice:1^M USN: uuid:2fdeeab1-42c9-19cc-8e38-93771b9fc28::urn:schemas-upnp-org:device:InternetGatewayDevice:1^M EXT:^M SERVER: FreeBSD/12.3-STABLE UPnP/1.1 MiniUPnPd/2.2.1^M LOCATION: http://10.0.0.254:2189/rootDesc.xml^M OPT: "http://schemas.upnp.org/upnp/1/0/"; ns=01^M 01-NLS: 1645287585^M BOOTID.UPNP.ORG: 1645287585^M CONFIGID.UPNP.ORG: 1337^M ^M
Feb 19 11:20:59 Firewall miniupnpd[61453]: HTTP REQUEST from 10.0.0.18:51145 : GET /rootDesc.xml (HTTP/1.1)
Feb 19 11:20:59 Firewall miniupnpd[61453]: Host: 10.0.0.254:2189
Feb 19 11:20:59 Firewall miniupnpd[61453]: HTTP REQUEST from 10.0.0.18:51146 : POST /ctl/IPConn (HTTP/1.1)
Feb 19 11:20:59 Firewall miniupnpd[61453]: Host: 10.0.0.254:2189
Feb 19 11:20:59 Firewall miniupnpd[61453]: SOAPAction: urn:schemas-upnp-org:service:WANIPConnection:1#GetExternalIPAddress
Feb 19 11:20:59 Firewall miniupnpd[61453]: HTTP REQUEST from 10.0.0.18:51147 : POST /ctl/IPConn (HTTP/1.1)
Feb 19 11:20:59 Firewall miniupnpd[61453]: Host: 10.0.0.254:2189
Feb 19 11:20:59 Firewall miniupnpd[61453]: SOAPAction: urn:schemas-upnp-org:service:WANIPConnection:1#AddPortMapping
Feb 19 11:20:59 Firewall miniupnpd[61453]: AddPortMapping: ext port 9308 to 10.0.0.18:9308 protocol UDP for: 10.0.0.18:9308 to 9308 (UDP) leaseduration=0 rhost=
Feb 19 11:20:59 Firewall miniupnpd[61453]: UPnP permission rule 0 matched : port mapping accepted
Feb 19 11:20:59 Firewall miniupnpd[61453]: port 9308 UDP (rhost '') already redirected to 10.0.0.19:9308
Feb 19 11:20:59 Firewall miniupnpd[61453]: Returning UPnPError 718: ConflictInMappingEntry
Feb 19 11:21:17 Firewall miniupnpd[61453]: SSDP M-SEARCH from 10.0.0.18:60736 ST: urn:schemas-upnp-org:device:InternetGatewayDevice:1
Feb 19 11:21:17 Firewall miniupnpd[61453]: Single search found
Feb 19 11:21:17 Firewall miniupnpd[61453]: SendSSDPResponse(): 0 bytes to 10.0.0.18:60736 ST: HTTP/1.1 200 OK^M CACHE-CONTROL: max-age=120^M ST: urn:schemas-upnp-org:device:InternetGatewayDevice:1^M USN: uuid:2fdeeab1-42c9-19cc-8e38-93771b9fc28::urn:schemas-upnp-org:device:InternetGatewayDevice:1^M EXT:^M SERVER: FreeBSD/12.3-STABLE UPnP/1.1 MiniUPnPd/2.2.1^M LOCATION: http://10.0.0.254:2189/rootDesc.xml^M OPT: "http://schemas.upnp.org/upnp/1/0/"; ns=01^M 01-NLS: 1645287585^M BOOTID.UPNP.ORG: 1645287585^M CONFIGID.UPNP.ORG: 1337^M ^M
Feb 19 11:21:17 Firewall miniupnpd[61453]: HTTP REQUEST from 10.0.0.18:51202 : GET /rootDesc.xml (HTTP/1.1)
Feb 19 11:21:17 Firewall miniupnpd[61453]: Host: 10.0.0.254:2189
Feb 19 11:21:17 Firewall miniupnpd[61453]: HTTP REQUEST from 10.0.0.18:51203 : POST /ctl/IPConn (HTTP/1.1)
Feb 19 11:21:17 Firewall miniupnpd[61453]: Host: 10.0.0.254:2189
Feb 19 11:21:17 Firewall miniupnpd[61453]: SOAPAction: urn:schemas-upnp-org:service:WANIPConnection:1#GetExternalIPAddress
Feb 19 11:21:17 Firewall miniupnpd[61453]: HTTP REQUEST from 10.0.0.18:51204 : POST /ctl/IPConn (HTTP/1.1)
Feb 19 11:21:17 Firewall miniupnpd[61453]: Host: 10.0.0.254:2189
Feb 19 11:21:17 Firewall miniupnpd[61453]: SOAPAction: urn:schemas-upnp-org:service:WANIPConnection:1#AddPortMapping
Feb 19 11:21:17 Firewall miniupnpd[61453]: AddPortMapping: ext port 9308 to 10.0.0.18:9308 protocol UDP for: 10.0.0.18:9308 to 9308 (UDP) leaseduration=0 rhost=
Feb 19 11:21:17 Firewall miniupnpd[61453]: UPnP permission rule 0 matched : port mapping accepted
Feb 19 11:21:17 Firewall miniupnpd[61453]: port 9308 UDP (rhost '') already redirected to 10.0.0.19:9308
Feb 19 11:21:17 Firewall miniupnpd[61453]: Returning UPnPError 718: ConflictInMappingEntry
Feb 19 11:21:18 Firewall miniupnpd[61453]: level=0 type=20
Feb 19 11:21:18 Firewall miniupnpd[61453]: sdl_index = 2 em1:0.c1.a2.20.12.31
Feb 19 11:21:18 Firewall miniupnpd[61453]: ST: urn:schemas-upnp-org:device:InternetGatewayDevice:1 (ver=1)
Feb 19 11:21:18 Firewall miniupnpd[61453]: SSDP M-SEARCH from 10.0.0.18:64158 ST: urn:schemas-upnp-org:device:InternetGatewayDevice:1
Feb 19 11:21:18 Firewall miniupnpd[61453]: Single search found
Feb 19 11:21:18 Firewall miniupnpd[61453]: SendSSDPResponse(): 0 bytes to 10.0.0.18:64158 ST: HTTP/1.1 200 OK^M CACHE-CONTROL: max-age=120^M ST: urn:schemas-upnp-org:device:InternetGatewayDevice:1^M USN: uuid:2fdeeab1-42c9-19cc-8e38-93771b9fc28::urn:schemas-upnp-org:device:InternetGatewayDevice:1^M EXT:^M SERVER: FreeBSD/12.3-STABLE UPnP/1.1 MiniUPnPd/2.2.1^M LOCATION: http://10.0.0.254:2189/rootDesc.xml^M OPT: "http://schemas.upnp.org/upnp/1/0/"; ns=01^M 01-NLS: 1645287585^M BOOTID.UPNP.ORG: 1645287585^M CONFIGID.UPNP.ORG: 1337^M ^M
Feb 19 11:21:18 Firewall miniupnpd[61453]: HTTP REQUEST from 10.0.0.18:51208 : GET /rootDesc.xml (HTTP/1.1)
Feb 19 11:21:18 Firewall miniupnpd[61453]: Host: 10.0.0.254:2189
Feb 19 11:21:18 Firewall miniupnpd[61453]: HTTP REQUEST from 10.0.0.18:51209 : POST /ctl/IPConn (HTTP/1.1)
Feb 19 11:21:18 Firewall miniupnpd[61453]: Host: 10.0.0.254:2189
Feb 19 11:21:18 Firewall miniupnpd[61453]: SOAPAction: urn:schemas-upnp-org:service:WANIPConnection:1#GetExternalIPAddress
Feb 19 11:21:18 Firewall miniupnpd[61453]: HTTP REQUEST from 10.0.0.18:51210 : POST /ctl/IPConn (HTTP/1.1)
Feb 19 11:21:18 Firewall miniupnpd[61453]: Host: 10.0.0.254:2189
Feb 19 11:21:18 Firewall miniupnpd[61453]: SOAPAction: urn:schemas-upnp-org:service:WANIPConnection:1#AddPortMapping
Feb 19 11:21:18 Firewall miniupnpd[61453]: AddPortMapping: ext port 9308 to 10.0.0.18:9308 protocol UDP for: 10.0.0.18:9308 to 9308 (UDP) leaseduration=0 rhost=
Feb 19 11:21:18 Firewall miniupnpd[61453]: UPnP permission rule 0 matched : port mapping accepted
Feb 19 11:21:18 Firewall miniupnpd[61453]: port 9308 UDP (rhost '') already redirected to 10.0.0.19:9308
Feb 19 11:21:18 Firewall miniupnpd[61453]: Returning UPnPError 718: ConflictInMappingEntry -
@saber
I think you mentioned in an earlier post that you have a linux firewall that works.Is that a similar config? I.e. miniupnpd with pf?
If it is, you could run it with the same debug level, and perhaps diff the responses from miniupnpd (via packet compare) that say the port is already taken.
It wouldn't fix anything, but could point to a deeper reason why the playstation isn't trying new ports each time.
Prior to the patch, my windows/Call of Duty client would randomly pick new ports forever, filling up the UPnP mapping table without bounds. After the patch, it gets the 718 error the first time, picks a new port and the second one sticks.
-
@encrypt1d said in UPnP Fix for multiple clients/consoles playing the same game:
@saber
I think you mentioned in an earlier post that you have a linux firewall that works.Is that a similar config? I.e. miniupnpd with pf?
If it is, you could run it with the same debug level, and perhaps diff the responses from miniupnpd (via packet compare) that say the port is already taken.
It wouldn't fix anything, but could point to a deeper reason why the playstation isn't trying new ports each time.
Prior to the patch, my windows/Call of Duty client would randomly pick new ports forever, filling up the UPnP mapping table without bounds. After the patch, it gets the 718 error the first time, picks a new port and the second one sticks.
I've removed the Linux firewall, mostly because I prefer PFSense but I'm really curious now what Linux does differently with how it handles multiple devices asking for the same port. I'll see if I can standup a Linux firewall in a VM and put the Playstation's in the same VLAN and log the miniupnp / packet capture to try and narrow down what the differences are if any.
To answer your question, Linux isn't the same as Packet Filter. Linux uses IPTables / Netfilter. While BSD / Unix based OS's use Packet Filter.
I thought for sure I'd see a difference in the miniupnp responses considering both Playstations now show a NAT Type 2 with Static Port mapping enabled, but nothing. Miniupnp responded the exact same way, yet Playstation is reporting a different NAT Type...
What is kind of funny, if not a little ironic is that Playstation 4 based Operating System is FreeBSD.... lol
-
I'll hopefully save you some time on setting up that test firewall. If it will running miniupnpd & pf, it will not work at all if the firewall's wan ip is a private RFC1918 address. I'd say there's low value in choosing that config for your test anyway, since the outcome would likely be the same. I'd go with a different implementation.
I have a separate thread tracking that bug, and I have proposed a code change to the miniupnp developers. You can catch up on these threads if you are interested.
https://forum.netgate.com/topic/169773/miniupnp-full-cone-double-natincorrectly-adding-rules
https://github.com/miniupnp/miniupnp/issues/598 -
@encrypt1d said in UPnP Fix for multiple clients/consoles playing the same game:
I'll hopefully save you some time on setting up that test firewall. If it will running miniupnpd & pf, it will not work at all if the firewall's wan ip is a private RFC1918 address. I'd say there's low value in choosing that config for your test anyway, since the outcome would likely be the same. I'd go with a different implementation.
I have a separate thread tracking that bug, and I have proposed a code change to the miniupnp developers. You can catch up on these threads if you are interested.
https://forum.netgate.com/topic/169773/miniupnp-full-cone-double-natincorrectly-adding-rules
https://github.com/miniupnp/miniupnp/issues/598That saved me a TON of time. CGNAT what a pain. I'm spending extra with my ISP to get a Public IP so I'm not behind a CGNAT.
I'll have to see if I can find some old hardware to throw a Linux Firewall distro on it and see what is different. The problem is always time.
-
Had some time to perform further testing just now.
I disabled NAT Reflection mode for port forwards and unchecked both Enable NAT Reflection for 1:1 NAT and Enable automatic outbound NAT for Reflection and the patch still works.
Tested, PC + PS5, Warzone, both in the same lobby/match at the same time. Both devices reported open NAT.
Pre-patch this wasn't possible.
-
@rivageeza and no static port mappings in NAT Outbound Rules?
-
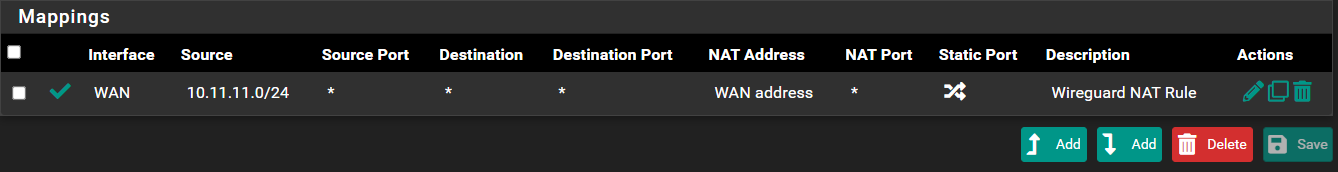
@m0nji nothing to do with the PC or consoles. I used to but I removed them and retested last week.
I did create one rule over the weekend but that's for Wireguard, my LAN is 10.10.10.1/24, PS5 is 10.10.10.30 and PC 10.10.10.38.
Wireguard rule below
-
@jimp
I applied the patch fix for upnp reboot Pfsense deleted all rules
under portforward and hybrid outbound NAT Reboot Pfsense,
Network address translation all unchecked and disabled,
enabled UPnP & NAT-PMP and added ACL rules,
Tested upnp with warframe, Call of Duty Vanguard, Overwatch, Borderlands
StatusUPnP & NAT-PMP UPnP & NAT-PMP Rules the Playstation connections
were listed, but i could not connect to the servers or play.I had to recreate all portforward and hybrid outbound NAT in order
for the playstation to connect,NAT-2
but now the StatusUPnP & NAT-PMP UPnP & NAT-PMP Rules and
Shell Output - pfSsh.php playback pfanchordrill are empty
when PlayStation is connected and playing games.BEFORE CREATING portforward and hybrid outbound NAT RULES
Shell Output - grep miniupnpd /tmp/rules.debug
binat-anchor "miniupnpd"
nat-anchor "miniupnpd"
rdr-anchor "miniupnpd"
anchor "miniupnpd"Shell Output - pfSsh.php playback pfanchordrill
listed all connectionsStatusSystem LogsSystemRouting
Mar 2 14:16:17 miniupnpd 18758 HTTP listening on port xxxx
Mar 2 14:16:17 miniupnpd 18758 no HTTP IPv6 address, disabling IPv6
Mar 2 14:16:17 miniupnpd 18758 Listening for NAT-PMP/PCP traffic on port xxxxI remove and apply the patch following the advice in this post but with no luck
I see the connection under Shell Output - pfSsh.php playback pfanchordrill
and StatusUPnP & NAT-PMP UPnP & NAT-PMP but cannot connect to server can't play
put rules back in place every thing works. -
@yorke Please start a new thread for your issue, it doesn't sound related to this. You have some other type of problem with UPnP.
-
@rivageeza I can confirm that this setup after applying the patch works with 2 PCs trying to play Call Of Duty Vanguard, It took rebooting the pfsense box and both my pc's, I can run Call of Duty Vanguard without any problems with both PCs having an open NAT. My setup runs a VLAN with both PCs on that VLAN.
Before Applying the Patch - Had same setup as you mention. I could launch Vanguard on PC1 and get to the multiplayer screen and it would show Open but sometimes moderate. While PC1 was sitting in the multiplayer screen waiting to start a match, i tried to launch Vanguard on PC2. I was able to get to the "Connecting to services" screen during bootup until I was met with the "Disconnected from Server" which forces me to exit to desktop.
After Applying the Patch - Keeping the same setup you mention. Only difference is I rebooted the pfsense box and also shutdown both computers while the pfsense box was rebooting. Gave it a good 5 minutes and turned both computers on. Started PC1 with vanguard, boots up as usual to multiplayer screen and an Open NAT this time. Booted up PC2 vanguard and it passes the initial "connecting to services" screen and I can get into multiplayer. PC2 also showed and Open NAT.
-
@fusioncha0s he is not using this specific config anymore. you have to scroll down a bit ;)
-
@m0nji thank you for letting me know. I have also disabled NAT Reflection mode for port forwards and unchecked both Enable NAT Reflection for 1:1 NAT and Enable automatic outbound NAT for Reflection with the patch and both my pc's run Vanguard without and issue and contains Open NAT for both. I still have my outbound setup though along with my ACL's.
-
Can anyone that has this patch applied tell me what result running this test is returning?
https://github.com/automation-stack/nat-discovery
Used to use PF a while back before I noticed it didn’t support 2 PCs playing Halo (1 person would get kicked out)
Really want to make the switch to pfsense but the only reason I stay with WRT is because I get full cone NAT, which is the best for gaming.
Thanks!
-
@chief said in UPnP Fix for multiple clients/consoles playing the same game:
I get full cone NAT
@chief You'll want to read up on this thread. Those of us behind a full cone double NAT aren't fully operational with this patch (yet). Once they issue a miniupnpd release, and pfSense includes it, it will work, assuming nothing else gets broken of course. I am running a version I built myself, and both STUN and the "Override WAN address" options work flawlessly on 2.6.0 CE. Without the additional miniupnpd fix, only those with public IPs on their WAN interface can successfully use UPNP.
https://forum.netgate.com/topic/169773/miniupnp-full-cone-double-natincorrectly-adding-rules
-
@chief said in UPnP Fix for multiple clients/consoles playing the same game:
https://github.com/automation-stack/nat-discovery
Also a note on using a tool like the automation-stack/nat-discovery link posted above:
Without manual changes, this will never result in anything other than a restricted NAT result if run on a host behind the firewall. The tool does not actually make any UPNP port mapping requests, so its tests will not be NATed as desired or allowed back through the firewall. You can probably add the NAT/FW rules yourself to make that work, however ...
The STUN implementation included in miniupnpd includes a very similar check, which runs directly from the firewall itself when STUN is enabled. Assuming you have the firewall rule to allow the inbound connection attempts directly to the firewall WAN IP, it does in fact report a fully open NAT.
Mar 18 10:05:43 firewall miniupnpd[782]: STUN: Performing with host=stun.sipgate.net and port=3478 ... Mar 18 10:05:43 firewall miniupnpd[782]: resolve_stun_host: stun.sipgate.net:3478 => 217.10.68.152:3478 Mar 18 10:05:43 firewall miniupnpd[782]: perform_stun: local ports 38769 13999 4669 15715 Mar 18 10:05:43 firewall miniupnpd[782]: wait_for_stun_responses: waiting 3 secs and 0 usecs Mar 18 10:05:43 firewall miniupnpd[782]: wait_for_stun_responses: received responses: 1 Mar 18 10:05:43 firewall miniupnpd[782]: wait_for_stun_responses: waiting 3 secs and 0 usecs Mar 18 10:05:43 firewall miniupnpd[782]: wait_for_stun_responses: received responses: 3 Mar 18 10:05:43 firewall miniupnpd[782]: wait_for_stun_responses: waiting 3 secs and 0 usecs Mar 18 10:05:43 firewall miniupnpd[782]: wait_for_stun_responses: received responses: 4 Mar 18 10:05:43 firewall miniupnpd[782]: parse_stun_response: Type 0x0101, Length 68, Magic Cookie 2112a442 Mar 18 10:05:43 firewall miniupnpd[782]: parse_stun_response: MAPPED-ADDRESS X.X.X.X:38769 Mar 18 10:05:43 firewall miniupnpd[782]: parse_stun_response: SOURCE-ADDRESS 217.10.68.152:3478 Mar 18 10:05:43 firewall miniupnpd[782]: parse_stun_response: CHANGED-ADDRESS 217.116.122.136:3479 Mar 18 10:05:43 firewall miniupnpd[782]: parse_stun_response: XOR-MAPPED-ADDRESS X.X.X.X:38769 Mar 18 10:05:43 firewall miniupnpd[782]: parse_stun_response: SOFTWARE Vovida.org 0.96 Mar 18 10:05:43 firewall miniupnpd[782]: parse_stun_response: Type 0x0101, Length 68, Magic Cookie 2112a442 Mar 18 10:05:43 firewall miniupnpd[782]: parse_stun_response: MAPPED-ADDRESS X.X.X.X:13999 Mar 18 10:05:43 firewall miniupnpd[782]: parse_stun_response: SOURCE-ADDRESS 217.10.68.152:3479 Mar 18 10:05:43 firewall miniupnpd[782]: parse_stun_response: CHANGED-ADDRESS 217.116.122.136:3479 Mar 18 10:05:43 firewall miniupnpd[782]: parse_stun_response: XOR-MAPPED-ADDRESS X.X.X.X:13999 Mar 18 10:05:43 firewall miniupnpd[782]: parse_stun_response: SOFTWARE Vovida.org 0.96 Mar 18 10:05:43 firewall miniupnpd[782]: parse_stun_response: Type 0x0101, Length 68, Magic Cookie 2112a442 Mar 18 10:05:43 firewall miniupnpd[782]: parse_stun_response: MAPPED-ADDRESS X.X.X.X:4669 Mar 18 10:05:43 firewall miniupnpd[782]: parse_stun_response: SOURCE-ADDRESS 217.116.122.136:3478 Mar 18 10:05:43 firewall miniupnpd[782]: parse_stun_response: CHANGED-ADDRESS 217.116.122.136:3479 Mar 18 10:05:43 firewall miniupnpd[782]: parse_stun_response: XOR-MAPPED-ADDRESS X.X.X.X:4669 Mar 18 10:05:43 firewall miniupnpd[782]: parse_stun_response: SOFTWARE Vovida.org 0.96 Mar 18 10:05:43 firewall miniupnpd[782]: parse_stun_response: Type 0x0101, Length 68, Magic Cookie 2112a442 Mar 18 10:05:43 firewall miniupnpd[782]: parse_stun_response: MAPPED-ADDRESS X.X.X.X:15715 Mar 18 10:05:43 firewall miniupnpd[782]: parse_stun_response: SOURCE-ADDRESS 217.116.122.136:3479 Mar 18 10:05:43 firewall miniupnpd[782]: parse_stun_response: CHANGED-ADDRESS 217.116.122.136:3479 Mar 18 10:05:43 firewall miniupnpd[782]: parse_stun_response: XOR-MAPPED-ADDRESS X.X.X.X:15715 Mar 18 10:05:43 firewall miniupnpd[782]: parse_stun_response: SOFTWARE Vovida.org 0.96 Mar 18 10:05:43 firewall miniupnpd[782]: STUN: ext interface igb0 with IP address Y.Y.Y.Y is now behind unrestricted NAT 1:1 with public IP address X.X.X.X: Port forwarding is now enabled