Suricata 6.0.4_1 blocking Dropbox IPs even in the pass list (SOLVED)
-
Hi,
I am using pfsense 2.6.0-RELEASE, with Suricata 6.0.4_1 and the basic rules. It is blocking Dropbox, so I added these two IPs to the pass list:
162.125.0.0/16
108.160.160.0/20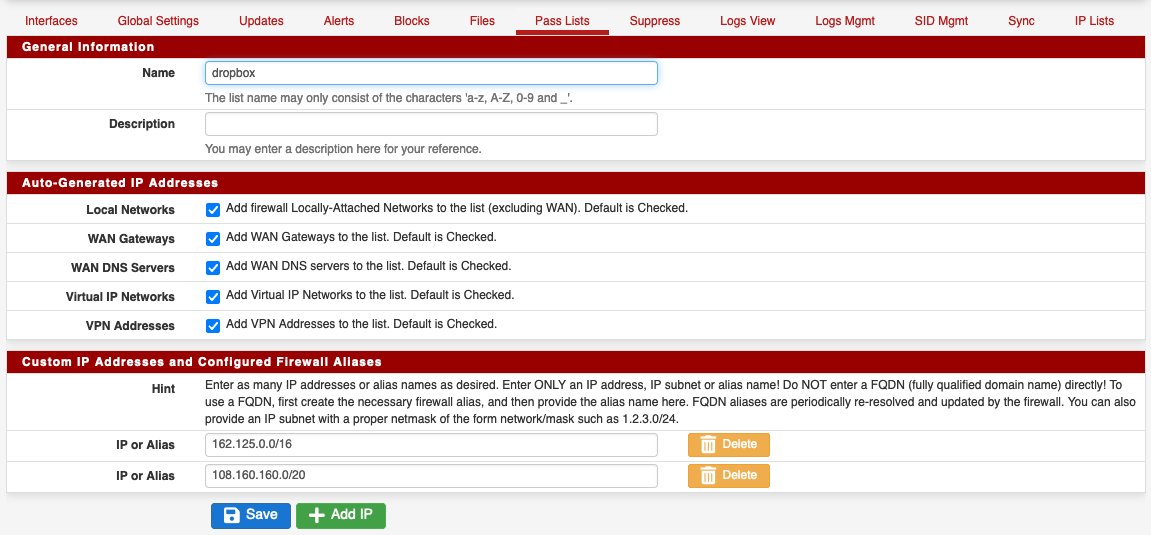
I expected the IPs in the Pass Lists to have precedence over Blocks (so they should pass as the name implies). But I still get Dropbox blocked from these IPs.
I also added the blocked rules to the disabled state, by clicking on the red X in the Alerts list:
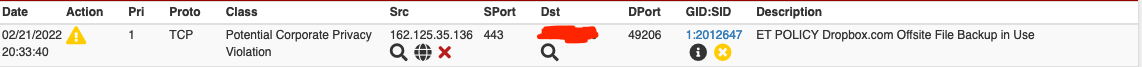
I also restarted the service, with no luck.
What am I doing wrong?
Thank you -
@zgtc Sorry, forgot to mention I am using Legacy mode, on my parent LAN interface (igb0)
-
@zgtc Restarting Suricata on the interface should update the list. You can check the active pass list on the interface, there's a button to view the pass list.
-
@steveits MMM I did, same result.
I think the problem is that I need to select my pass list in the Interface dropdown.
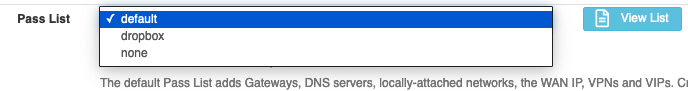
But then it would miss the IPs from the default list. It is really unclear to me how to COMBINE default and my list. This paragraph is really ambiguous for not expert users:
The default Pass List adds Gateways, DNS servers, locally-attached networks, the WAN IP, VPNs and VIPs. Create a Pass List with an alias to customize whitelisted IP addresses. This option will only be used when block offenders is on. Choosing "none" will disable Pass List generation.
Any help? Thank you
-
@zgtc What does View List show?
I have not tried the new feature to add IPs in Suricata. In the past we set up an alias, then put the alias in a Suricata pass list:
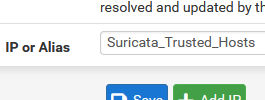
...then select that pass list on the interface -
@steveits said in Suricata 6.0.4_1 blocking Dropbox IPs even in the pass list:
@zgtc What does View List show?
It shows the IPs for the default pass list
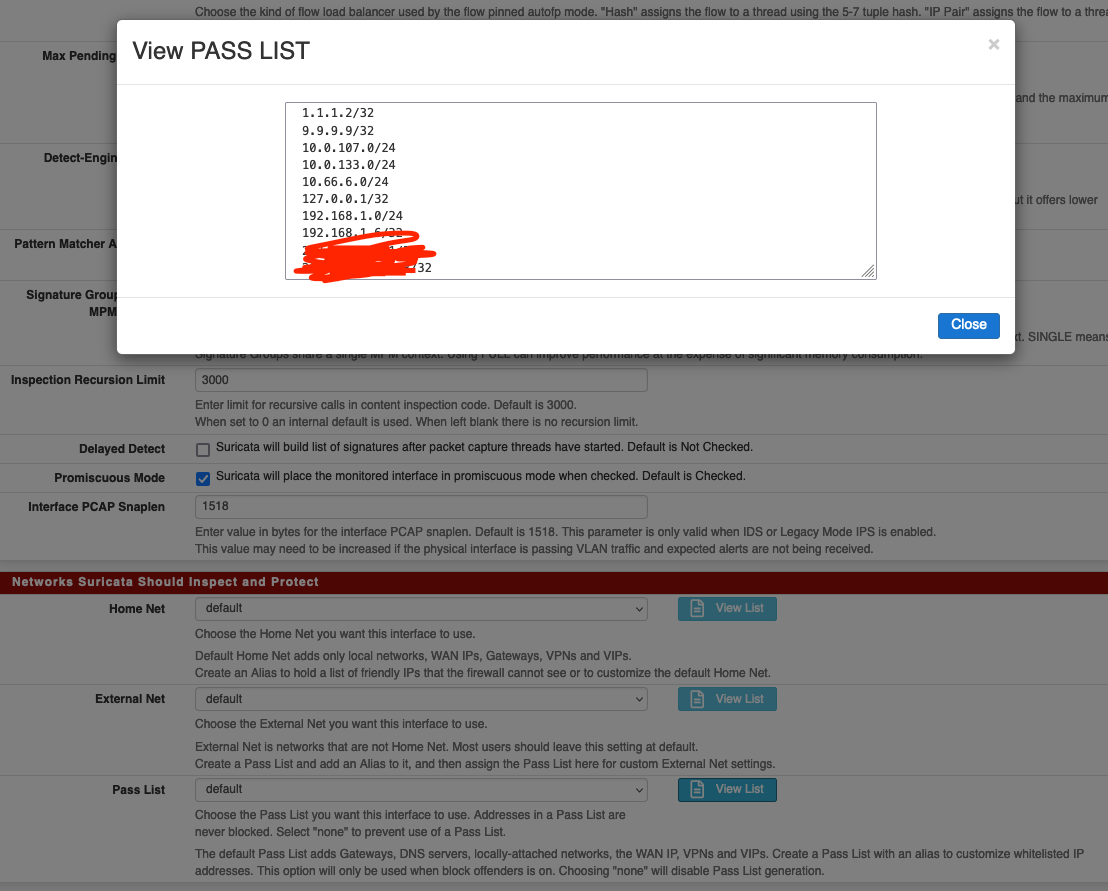
-
@steveits said in Suricata 6.0.4_1 blocking Dropbox IPs even in the pass list:
I have not tried the new feature to add IPs in Suricata. In the past we set up an alias, then put the alias in a Suricata pass list
I tried to add the IPs to the Firewall aliases, but got this message.
162.125.0.0/16
108.160.160.0/20
I don't expect to have to expand the whole range of IPs...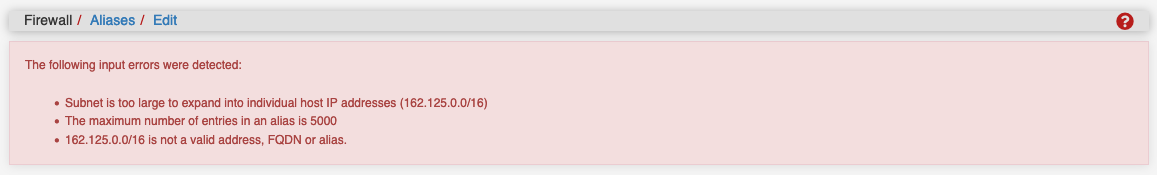
-
@zgtc The pass list in your message shows "default" is selected and you'd need to select "dropbox" to pick up your aliases, then restart Suricata on the interface.
When editing a pass list the "Auto-Generated IP Addresses" checkboxes basically comprise the default list.
Are you creating your alias as type Network? It works for me:
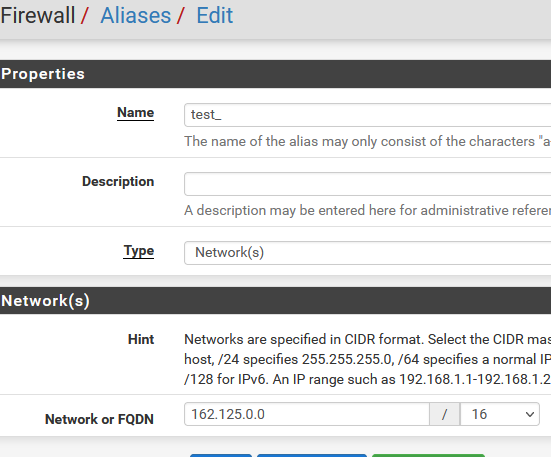
-
@steveits OK I selected the custom list and restarted the service on the interface, you are right, it mixes the default + custom IPs
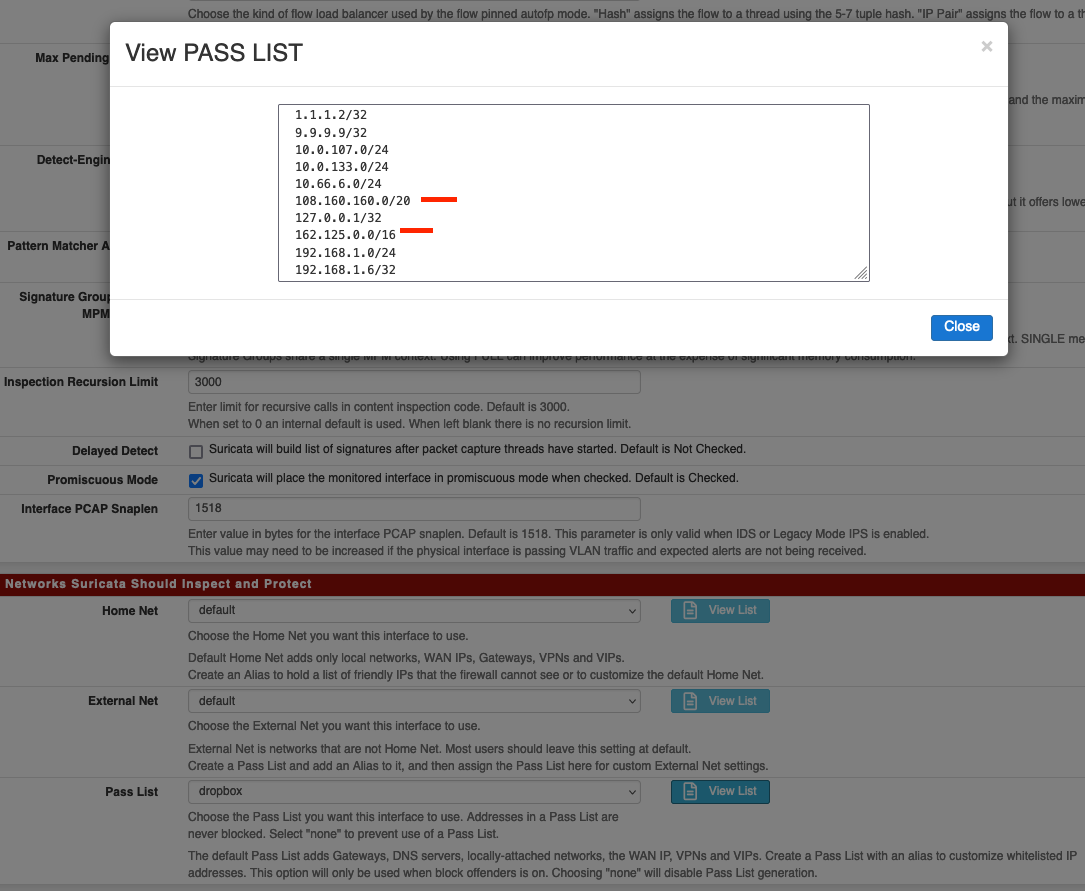
But Dropbox is still being blocked
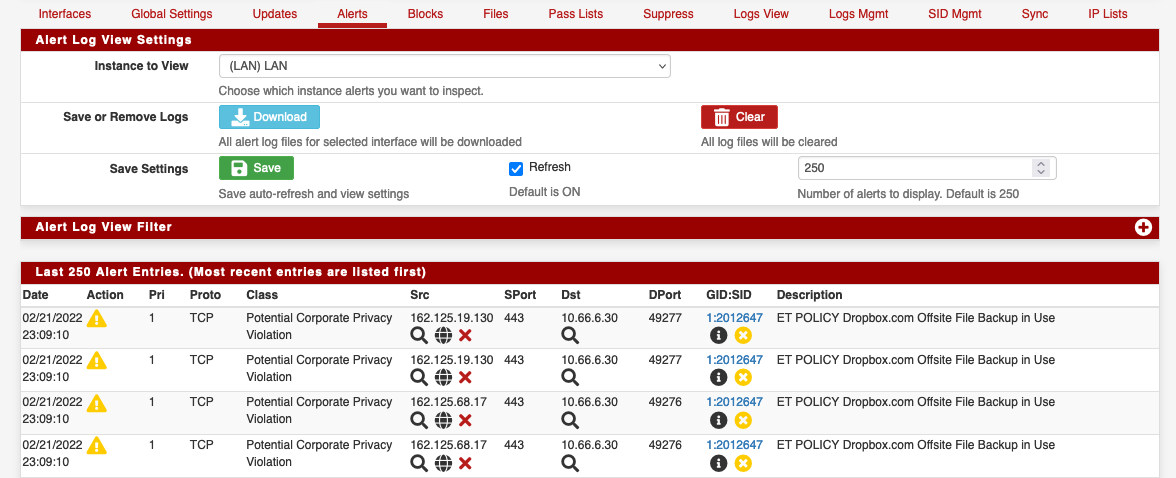
-
@zgtc OK, sorry.
I restarted the whole service and then the computer that runs the dropbox daemon. It now works!Well it logs in to the dropbox account, but still does not sync the files. Weird.
Thank you so much for the help anyway. Will keep trying.
-
@zgtc You're sure it wasn't blocked from before?
At any rate these are all Dropbox IPs? You could disable the Dropbox rule. I'm trying to remember what the X in a yellow circle icon is, normally it's a red X to disable the rule. Then it doesn't bother checking the rule at all, and doesn't need to run every packet through those entries on the pass list either.
The maintainer has posted in other threads but "policy" and "info" rulesets are intended more for informational tracking and not necessarily a list of things to block.
-
@steveits said in Suricata 6.0.4_1 blocking Dropbox IPs even in the pass list:
@zgtc You're sure it wasn't blocked from before?
These rules were red before, I clicked the red X and then they were converted into the yellow background X.
At any rate these are all Dropbox IPs? You could disable the Dropbox rule. I'm trying to remember what the X in a yellow circle icon is, normally it's a red X to disable the rule. Then it doesn't bother checking the rule at all, and doesn't need to run every packet through those entries on the pass list either.
The maintainer has posted in other threads but "policy" and "info" rulesets are intended more for informational tracking and not necessarily a list of things to block.
I really dont understand. In theory, if I understood correctly, you can manually remove a rule but clicking those red X in the Alerts list. But even if that was not the method, adding the IPs as I did with your help should be enough, no?
I'm lost :)
-
@zgtc If you're new to Suricata consider turning off blocking and just monitor Alerts until you weed out the incorrect ones. :) Then enable blocking later.
If you hover over the icons it will tell you what it will do:
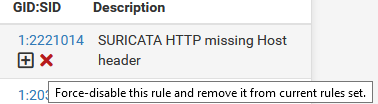
If clicked this would disable the rule and it won't trigger anymore. A disabled rule isn't checked at all, saves CPU.If the IP had already been blocked it would still be on the Blocked tab from that prior blocking, until it expires and is automatically removed.
-
@steveits said in Suricata 6.0.4_1 blocking Dropbox IPs even in the pass list:
@zgtc If you're new to Suricata consider turning off blocking and just monitor Alerts until you weed out the incorrect ones. :) Then enable blocking later.
As a last resort I will, of course. But I'd like to understand how the system works.
If you hover over the icons it will tell you what it will do:

If clicked this would disable the rule and it won't trigger anymore. A disabled rule isn't checked at all, saves CPU.You are suggesting in the capture that I should click the red cross to force disable a rule. This is what I did in the first place, and that is why the rules show a yellow cross instead, as we have mentioned above.
If the IP had already been blocked it would still be on the Blocked tab from that prior blocking, until it expires and is automatically removed.
Weirdly enough, the block list is not updated in the past 30 min, since I added the custom pass, but Dropbox still won't sync.
Thank you again for your patience
-
@zgtc This is getting even more weird. I disabled the IPS:
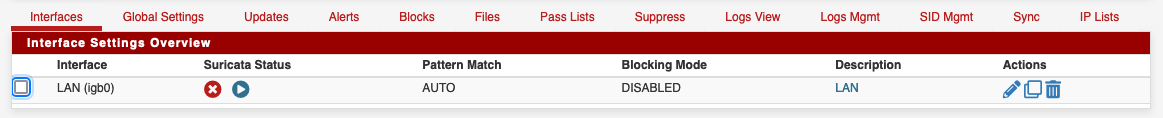
Then restarted both the interface service and the whole suricata daemon, and I still get blocks in the firewall logs!
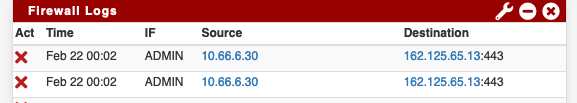
Will try stopping the whole daemon instead...
Same even with daemon stopped. I don't really understand it.
-
@zgtc Depending on timing the IP may still be in the blocked table? Suricata puts the IP in the table and then later removes it. pf blocks the IP because of the (hidden/internal) rule using that table. So ensure the Blocks tab is empty.
or possibly https://docs.netgate.com/pfsense/en/latest/troubleshooting/log-filter-blocked.html
-
Suricata blocks in Legacy Mode by adding IP addresses to a special hidden
pftable called snort2c. Any IP address placed in that table is blocked by the firewall. The IP remains in the table until one of three things happen:- the admin manually deletes the block using the option next to the IP on the BLOCKS tab;
- the periodic cron task (if enabled) removes the IP from the table after a set period of no further activity from that IP;
- or the firewall is rebooted. This clears the table because it is a RAM construct.
You need to use the BLOCKS tab to see what IPs are currently in the table and thus are being blocked. You can clear the entire table, or remove specific IP addresses using the icons and buttons on that tab.
Stopping or restarting the Suricat daemon has zero impact on the content of the snort2c table, thus it will not remove an existing block.
-
@steveits said in Suricata 6.0.4_1 blocking Dropbox IPs even in the pass list:
@zgtc Depending on timing the IP may still be in the blocked table? Suricata puts the IP in the table and then later removes it. pf blocks the IP because of the (hidden/internal) rule using that table. So ensure the Blocks tab is empty.
@bmeeks said in Suricata 6.0.4_1 blocking Dropbox IPs even in the pass list:
Suricata blocks in Legacy Mode by adding IP addresses to a special hidden
pftable called snort2c. Any IP address placed in that table is blocked by the firewall. The IP remains in the table until one of three things happen:- the admin manually deletes the block using the option next to the IP on the BLOCKS tab;
- the periodic cron task (if enabled) removes the IP from the table after a set period of no further activity from that IP;
- or the firewall is rebooted. This clears the table because it is a RAM construct.
You need to use the BLOCKS tab to see what IPs are currently in the table and thus are being blocked. You can clear the entire table, or remove specific IP addresses using the icons and buttons on that tab.
Stopping or restarting the Suricat daemon has zero impact on the content of the snort2c table, thus it will not remove an existing block.
OK, NOW it started sync'ing! Thank you so much both of you. Man I am so stupid, the Blocks list was always there, I simply didn't think about removing the items. That's in part why I was asking how to make the Pass list more relevant to the Blocks list.
In any case, next question. I disabled all Dropbox related items from the ET Policy file, then removed the items from the block list:

Then restarted the service in the LAN interface... And the
Offsite File Backup in usestill gets added again to the Blocks list.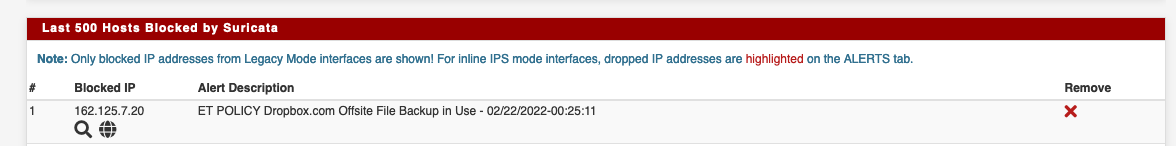
And of course blocked by the Firewall
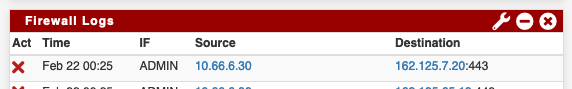
I don't get it.
-
One other possibility is that you have a duplicate Suricata process running on the same interface. If so, that instance would not honor any Pass List changes.
Run this command from a shell prompt on the firewall:
ps -ax | grep suricataSee if it shows any duplicate interfaces. If so, go to the GUI and stop all Suricata instances. Then return to the shell prompt, run the command above again, and if any Suricata processes remain kill them with this command:
kill -9 <pid>where <pid> is the Process ID of the remaining Suricata process.
You also need to validate that Suricata has actually loaded your Pass List. Go to the LOGS VIEW tab and choose the
suricata.logfile for the interface. Look through that log and be sure it shows your Dropbox IP networks being added during startup. -
@bmeeks said in Suricata 6.0.4_1 blocking Dropbox IPs even in the pass list:
One other possibility is that you have a duplicate Suricata process running on the same interface.
YOU NAILED IT! I would have never guessed by myself, thank you so much!
You also need to validate that Suricata has actually loaded your Pass List. Go to the LOGS VIEW tab and choose the
suricata.logfile for the interface. Look through that log and be sure it shows your Dropbox IP networks being added during startup.That part was OK, but thank you again