Captive portal, certificates and chrome-Edge
-
Hello.
I currently have the captive portal running on pfsense 2.6 correctly. Pfsense is directly connected to my internet provider and allows my different internal networks to access the internet. That is to say, I do not have a DNS server, nor a web server with a public IP, my entire network is internal.
When I connect via Wi-Fi to the captive portal, it automatically opens the browser, it gives me a certificate error and in advanced options I select that I accept the risk and then the screen to enter username and password appears. This only happens with firefox, since chrome and edge do not give an option to accept the certificate. I have tried to create other certificates from the administrator but it still does not work. Is there any way to solve it without having a public IP?
Thanks. -
@jperezme said in Captive portal, certificates and chrome-Edge:
When I connect via Wi-Fi to the captive portal, it automatically opens the browser,
Using what URL ?
it gives me a certificate error and in advanced options
A certificate has to have the URL, or, to be more precise, the host name incorporated into the certificate.
All this has nothing to do with IP addresses, they can RFC1818, or not.
Example : visit https://www.microsoft.com
When the page is loaded, the browser already shows the "very important" part :
as said : it's "microsoft.com", the domain name, (the www is there only for 'known to humans' reasons).
Now, inspect the certificate :
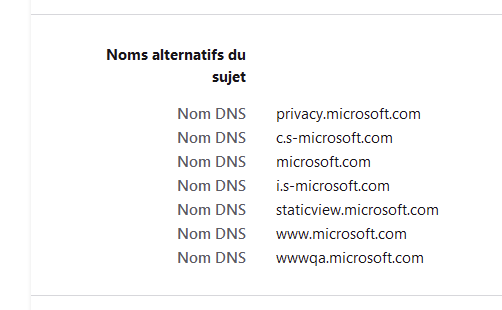
as you can see, microsoft.com and www.microsoft.com are part of the certificate.
If this was not the case, your browser will yell at you for this reasons.Another reaso to yell : the organisation that created the certificate has to be trusted by your browser. In this case, it's Microsoft itself, they use a 'master' certificate (trusted by every browser on the planet) so they can be a their own 'CA' and emit certificates that are trusted by all browsers.
So, yes, you can make yourself a CA, and use that CA to create a certificate that says it is "portal.your-pfsense.local" so the browser will trust that certificate.
But it will not trust the CA you made.
You can, of course, add your own CA to your browser's trusted CA list.Look around in the forum, yo will find many threads about the same subject.
When you visit the pfSense GUI using https, you see the same 'error' messages from your browser. The solution will be the same.A final solution would need a real domain name (you have to rent one).
Then use the pfSense acme package, and get certificates for free, these will be accepted by any browser. This solution is not needed when you as the admin visit the pfSense https GUI ones in a while. You know why and what to do.
But if you use a captive portal and you want to use the https portal access, you have to have a certificate that is trusted 'out of the box' by everybody, as you can't ask to everybody upfront "whatever you see when you connect to our wifi, accept it". Why would they, the unknown to you portal users, trust you ? -
@gertjan said in Captive portal, certificates and chrome-Edge:
@jperezme said in Captive portal, certificates and chrome-Edge:
When I connect via Wi-Fi to the captive portal, it automatically opens the browser,
Using what URL ?
Before i got http:\172.30.0.1 but then i have added portal.mydomain.local on host overrides in dns resolver.
A final solution would need a real domain name (you have to rent one).
Then use the pfSense acme package, and get certificates for free, these will be accepted by any browser. This solution is not needed when you as the admin visit the pfSense https GUI ones in a while. You know why and what to do.
But if you use a captive portal and you want to use the https portal access, you have to have a certificate that is trusted 'out of the box' by everybody, as you can't ask to everybody upfront "whatever you see when you connect to our wifi, accept it". Why would they, the unknown to you portal users, trust you ?Forgive my ignorance, but I don't understand how I can configure an external domain for my captive portal to work if my local network is internal.