One tunnel multiple peers?
-
(sorry I have to post piece by piece)
on computer 1, begin creating a tunnel. You will get P1pubK (at this point, config is not complete, we will append things later)
on computer 2, begin creating a tunnel. You will get P2pubKin pfSense :
create tunnel, generate New keys and get/copy FWpubK (to be used in each computer config)
save this and it will pre-generate a non assigned interface (tun_wg0)
Go to interface assignments and "add" the pseudo-interface (OPTx) using tun-wg0
Now you have an interface for the tunnel -
Edit interfaces > OPTx and set a static IPv4 as 192.168.201.254/24
edit the tunnel
create a first peer using P1pubK as "Public Key" (WireGuard public key for this peer.) and allowed IPs is 192.168.201.1/32 (be sure it's a /32, not /24)
create a second peer using P2pubK and allowed IPs is 192.168.201.2/32the tunnel is ready, as well as its peers references.
Now we have to set the firewall > rules > OPTx
You may start with permit IPv4 - any source - any destnation (restrict if needed)Now we have to set the firewall > rules > WAN to accept connections from outside
Add rule IPv4 - UDP - any source to "this firewall (self)" on wireguard port (51820 for example) -
On computer 1, edit config :
[Interface] PrivateKey =[do not change what has been automatically generated] Address = 192.168.201.1/24 DNS = 192.168.201.254 [Peer] PublicKey = [FWpubK] AllowedIPs = 192.168.201.0/24, any subnet behind the target pfSense Endpoint = [pfSense public IP or FQDN]:51820On computer 2, edit config :
[Interface] PrivateKey =[do not change what has been automatically generated] Address = 192.168.201.2/24 DNS = 192.168.201.254 [Peer] PublicKey = [FWpubK] AllowedIPs = 192.168.201.0/24, any subnet behind the target pfSense Endpoint = [pfSense public IP or FQDN]:51820Now you should be able to ping from computer 1 to 192.168.201.254 (pfSense) and any machine in "subnet behind the target pfSense"
Note that you can't ping a machine by it's name : DNS resolver in pfSense may not accept it.
Go to Services > DNS Resolver and add OPTx to the list of "Nework Interfaces" (Interface IPs used by the DNS Resolver for responding to queries from clients.) -
that's all (sorry, could'nt post all in once due to AKISMET, reputation restrictions and "new user" 120 seconds delay between 2 posts !)
-
@f-meunier THANK YOU!

-
@swemattias
Happy to be helpful !
Have a nice day (or night !) -
@f-meunier
OK, for archive, I put the whole procedure back in one single thread (now that I'm not flagged as spammer by AKISMET anymore !...)wireguard white paper states : "This also means that two distinct peers should not share private keys, since in that situation a packet sent to one could be replayed to another, and the ensuing response would then cause the initiator to involuntarily roam from one peer to another. But one should not be sharing private keys in the first place, anyway.)
computer 1 will have it's own private key (P1privK)+ public key (P1pubK)
computer 2 will have P2privK+ P2pubKpfSense will have FWprivK + FWpubK
the whole tunnel will use subnet 192.168.201.0/24, where :
pfSense will have 192.168.201.254
computer 1 will have 192.168.201.1
computer 2 will have 192.168.201.2
on computer 1, begin creating a tunnel. You will get P1pubK (at this point, config is not complete, we will append things later)
on computer 2, begin creating a tunnel. You will get P2pubKin pfSense :
create tunnel, generate New keys and get/copy FWpubK (to be used in each computer config)
save this and it will pre-generate a non assigned interface (tun_wg0)
Go to interface assignments and "add" the pseudo-interface (OPTx) using tun-wg0
Now you have an interface for the tunnel
Edit interfaces > OPTx and set a static IPv4 as 192.168.201.254/24
edit the tunnel
create a first peer using P1pubK as "Public Key" (WireGuard public key for this peer.) and allowed IPs is 192.168.201.1/32 (be sure it's a /32, not /24)
create a second peer using P2pubK and allowed IPs is 192.168.201.2/32the tunnel is ready, as well as its peers references.
Now we have to set the firewall > rules > OPTx
You may start with permit IPv4 - any source - any destnation (restrict if needed)Now we have to set the firewall > rules > WAN to accept connections from outside
Add rule IPv4 - UDP - any source to "this firewall (self)" on wireguard port (51820 for example)
On computer 1, edit config :
[Interface] PrivateKey =[do not change what has been automatically generated] Address = 192.168.201.1/24 DNS = 192.168.201.254 [Peer] PublicKey = [FWpubK] AllowedIPs = 192.168.201.0/24, any subnet behind the target pfSense Endpoint = [pfSense public IP or FQDN]:51820On computer 2, edit config :
[Interface] PrivateKey =[do not change what has been automatically generated] Address = 192.168.201.2/24 DNS = 192.168.201.254 [Peer] PublicKey = [FWpubK] AllowedIPs = 192.168.201.0/24, any subnet behind the target pfSense Endpoint = [pfSense public IP or FQDN]:51820Now you should be able to ping from computer 1 to 192.168.201.254 (pfSense) and any machine in "subnet behind the target pfSense"
Note that you can't ping a machine by it's name : DNS resolver in pfSense may not accept it.
Go to Services > DNS Resolver and add OPTx to the list of "Nework Interfaces" (Interface IPs used by the DNS Resolver for responding to queries from clients.)Now you can ping by names, not only IPs.
-
@swemattias So @f-meunier I read your posts twice, compared to what I have setup so far, saw one mistake. Than I rebuilt my peer setup from scratch.
So this is my Device 1s wg-conf:[Interface] PrivateKey = <Device 1 private key> Address = 172.16.16.1/24 DNS = 172.16.16.254 [Peer] PublicKey = <Server/pfSense public key or in your words FWpubk> AllowedIPs = 172.16.16.0/24, 10.0.0.0/24 Endpoint = wg.domain.io:58220The connections works and I get a handshake but I cannot reach anything on the inside or ping .254.
-
@swemattias
you can check "dynamic endpoint" if you have a "computer to network" situation,(give an endpoint address or fqdn only in "site to site" configuration)
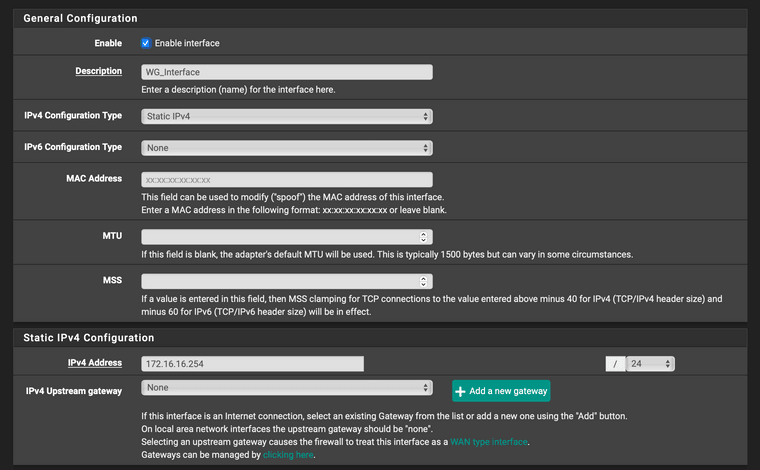
what is the WG_INTERFACE (OPT3) configuration ?
what is the rule on WAN ?
what is the rule on WG_INTERFACE ?Also, show the peer status if you can.
-
@swemattias
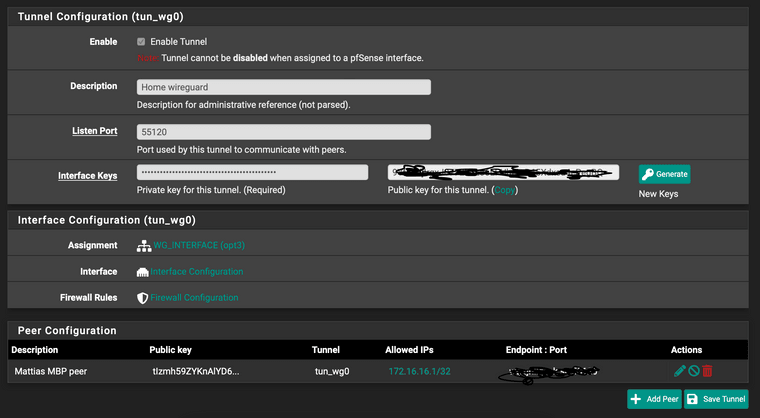
I see on tunnel config : listen port 55120
but you set the other side's "Endpoint = wg.domain.io:58220"
This should be the same port.
Thus, should be "Endpoint = wg.domain.io:55120" -
@f-meunier said in One tunnel multiple peers?:
@swemattias
I see on tunnel config : listen port 55120
but you set the other side's enpoint port as 58220
This should be the same portThat is just mistake from my side during preparing the post. Ofc I have the same port.
-
@f-meunier Here are those configs:

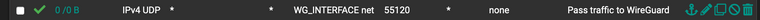
-
@swemattias
please try checking "dynamic"
Doing so, you only have to set parameters on the "fixed" side...
(client side will "use" these params in the [Peer] section) -
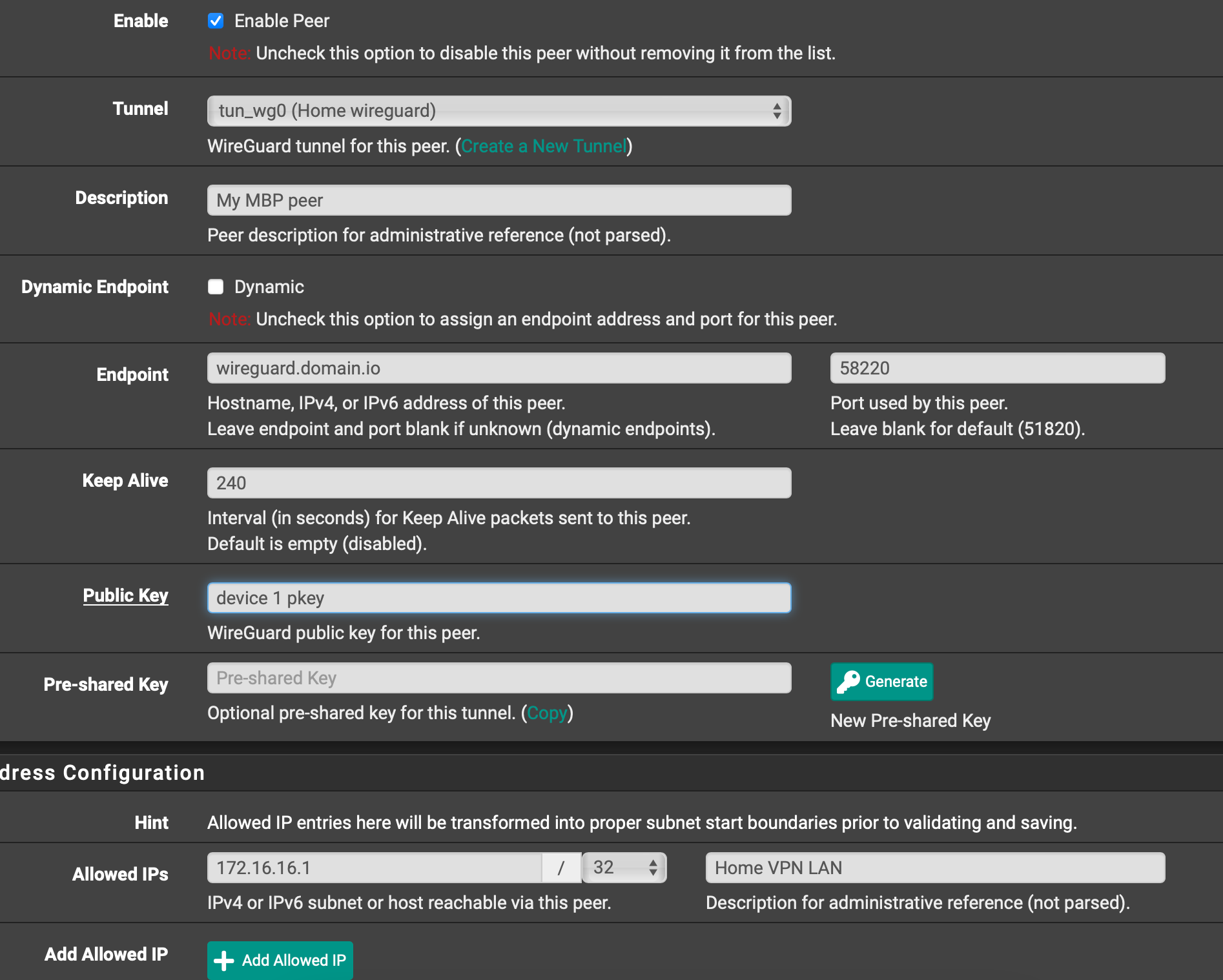
according to your screenshots, you should have :
[Interface] PrivateKey = <Device 1 private key> Address = 172.16.16.1/24 DNS = 172.16.16.254 [Peer] PublicKey = <Server/pfSense public key or in your words FWpubk> AllowedIPs = 172.16.16.0/24, 10.0.0.0/24 Endpoint = wg.domain.io:55120pinging 172.16.16.254 from client works ?
-
@f-meunier That didn't help, setting it to Dynamic, I can surf and write this through this tunnel, but I cannot reach the inside.
-
@swemattias
also confirm in pfSense' peer config that "Public Key : device 1 pkey" is the public key of the client(not the private key from [Interface] PrivateKey)
-
@swemattias
sorry, I did not understand the situation.
You have a computer connecting to the pfSense through the WG tunnel, you manage to surf through but can't access internal network 10.0.0.x /24 ?according to your config, it's not a "catch all" tunnel. Your computer access to the internet will not use the tunnel, but its local router/gateway directly...
-
@f-meunier Yes I am testing with my computer to see if it works.
First question - yes. Switching to 4G network activating the tunnel.
I cannot ping anything on either 172.16.16.0/24 or 10.0.0.0/24. -
let's summarize.
Your computer client should have 2 interfaces :
LAN interface (let's say 192.168.1.1/24)
wireguard interface : 172.16.16.1/24client config is
[Interface] PrivateKey = <Device 1 private key> Address = 172.16.16.1/24 DNS = 172.16.16.254 [Peer] PublicKey = <Server/pfSense public key or in your words FWpubk> AllowedIPs = 172.16.16.0/24, 10.0.0.0/24 Endpoint = wg.domain.io:55120pfsense has public IP wg.domain.io
LAN interface IP is 10.0.0.254/24
wireguard tunnel (tun_wg0) is bound to interface WG_INTERFACE
WG_INTERFACE has static IPv4 172.16.16.254/24
tunnel listen port = 55120 -
On the client computer side, what is the output of "route print -4" ?