PfSense not allowing internet traffic from connected devices
-
Hello all,
Before explaining my situation, please be aware that my knowledge is limited regarding PfSense and networking in general. Therefore, if my explanation is missing anything, please let me know and I'Il try my best to add the required details.
I am running a virtualized instance of PfSense, through virtualbox. The install is stock (latest version, downloaded two days ago), with no custom modifications to the base settings (except the few changes I tried that I will detail later on). On the virtual machine settings, I am using two network interfaces: a NAT interface and a host-only interface called vboxnet0 (for which the DHCP server distributes IPs in the range 192.168.56.0/24).
The WAN and LAN seem correctly configured as I am able to ping 8.8.8.8 from both interfaces. The LAN is able to get an IP in the correct range (192.168.56.101).The host machine is connected to the internet through the ethernet interface (eno1) and uses the wireless interface as an access point with a DHCP server serving IPs in the range 10.10.0.0/16.
In order to use PfSense as my firewall, I have an iptables nat forwarding rules that forward all the traffic coming from 10.10.0.0/16 to vboxnet0. The rule is:iptables -t nat -A POSTROUTING -s 10.10.0.0/16 -o vboxnet0 -j MASQUERADEUsing this rule, I am able to access the PfSense admin interface through the devices connected to my access point. However, I am not able to access the internet at all even though I can ping 8.8.8.8 (or any other IP) from the LAN interface through the PfSense admin GUI.
I assume that the iptables rule is working since I can access the PfSense admin.
If I change the interface to eno1 in the iptable rule (eno1 is connected to the internet), the internet works fine, but I am not transiting my traffic through PfSense anymore for these devices.
I tried creating new firewall rules accepting all traffic from to and through the LAN and WAN interface but nothing worked, so I just reverted back to step 0.Does anybody have any idea as to how to have internet on the devices connected through the AP ? Is the iptables rule wrong or is it some setting in PfSense ?
Thank you !
-
@tarzan222 said in PfSense not allowing internet traffic from connected devices:
he LAN is able to get an IP in the correct range (192.168.56.101).
You meant to say WAN, not LAN, right ?
-
@gertjan I actually truly meant LAN. Both WAN and LAN get IPs that look correct to me ! WAN seems to be getting an IP from the ISP DHCP server (if I am not wrong), while LAN gets an IP from the 192.168.56.0/24 range that I specified when creating the Host-only interface on virtualbox.
-
@tarzan222 said in PfSense not allowing internet traffic from connected devices:
The LAN is able to get an IP in the correct range (192.168.56.101).
Ok, then this will go very wrong. A LAN interface should have an static IP and /mask setting. Surely not a DHCP client.
A WAN type interface can use a DCP client so it can obtain a IP, gateway, network/mask etc from an upsream DHCP server.
-
@gertjan thank you for your insight!
Will removing the DHCP server on the host-only interface and giving the LAN a static IP in PfSense solve my internet related issue on the devices connected to the AP ?I might be mixing things up but how is it able to ping the internet through the LAN if the interface is misconfigured ? I am not sure I get why it is able to do so from PfSense but not from a connected device, whose traffic is forwarded through the LAN's interface. I would be interested in understanding a little more on this !
-
I've finally had the time to test a few more things:
- I bridged the LAN interface with my wlan0 interface (the access point) and set up the DHCP server in PfSense, along with a static IP for the LAN (192.168.1.1). The DHCP distributes IPs ranging from 192.168.1.10 to .100.
- With the above configuration, my devices are able to pull IPs from the DHCP I just set up (gateway and dns set to 192.168.1.1). I am able to access the PfSense administration pannel and ping the VM. However, I am still not able to access the internet. The connected devices are appearing on DHCP Leases though.
I am still able to ping any IP from the LAN directly from the PfSense admin interface (Diag -> Ping).
netstat -rn shows that the interface is indeed using 192.168.1.1 as its route.
No gateways are set for the LAN, so the issue isn't coming from there.
Here are the ipv4 routes, over which I'm not spotting any problem:
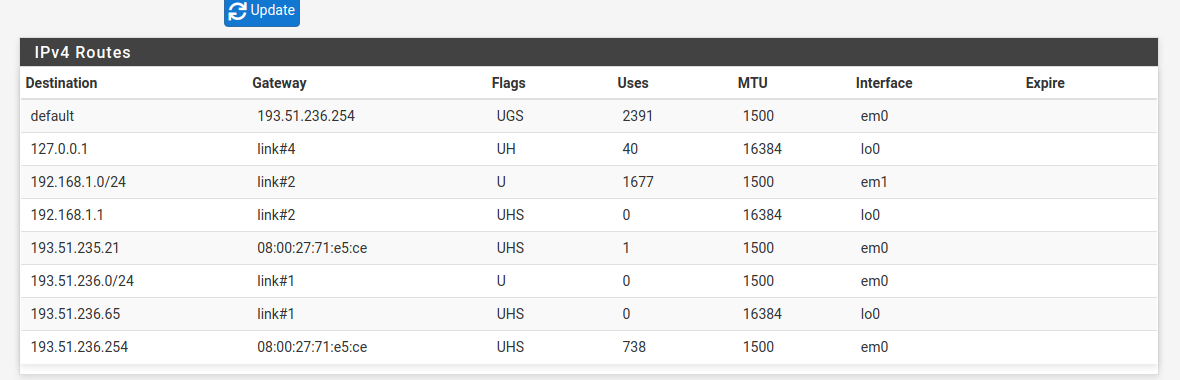
Is there anything I am still doing wrong ?
-
Also, I've just noticed I can't ping the WAN IP from the devices on the LAN. However, I can ping the WAN IP from Diag -> Ping with the LAN as the source.
-
Problem fixed by forcing the gateway on the AP to PfSense's LAN IP. I had it set up through /etc/network/interfaces but turns out I had to set it up via
route add default gw 192.168.1.1 wlan0