No Internet connection over Wireguard
-
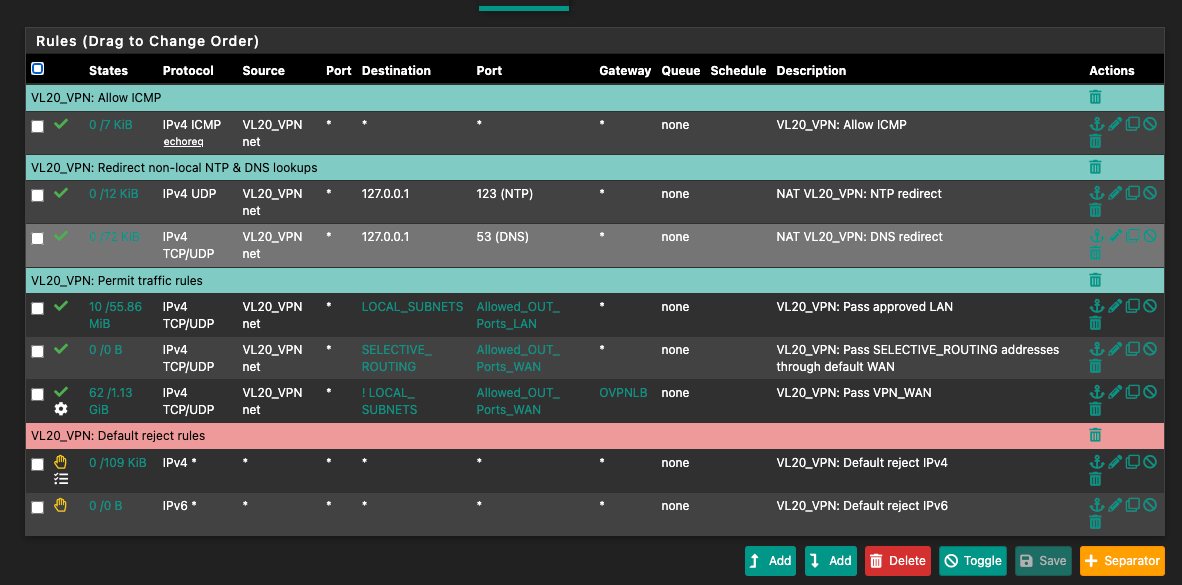
@the_dave This is the rule that would be routing the non "Selective_Routing" hosts out to the internet.
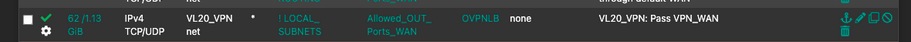
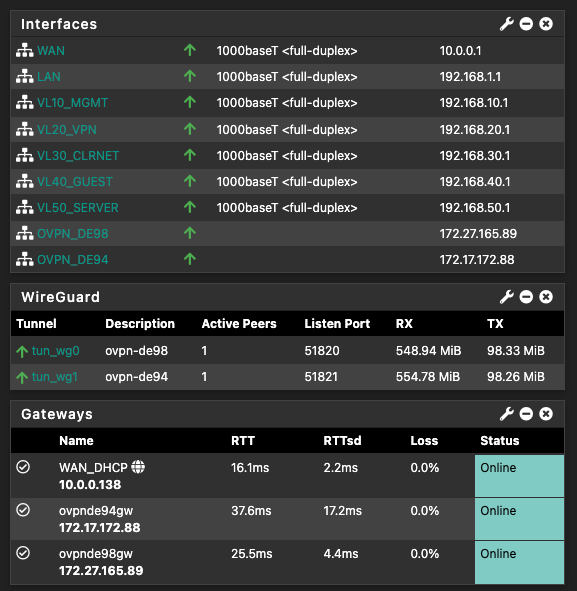
It clearly shows states in effect and that traffic is being routed (63/1.13 GiB). What is the gateway in that rule (OVPNLB)? Is that your wireguard tunnels?What does a traceroute out vlan20 show?
-
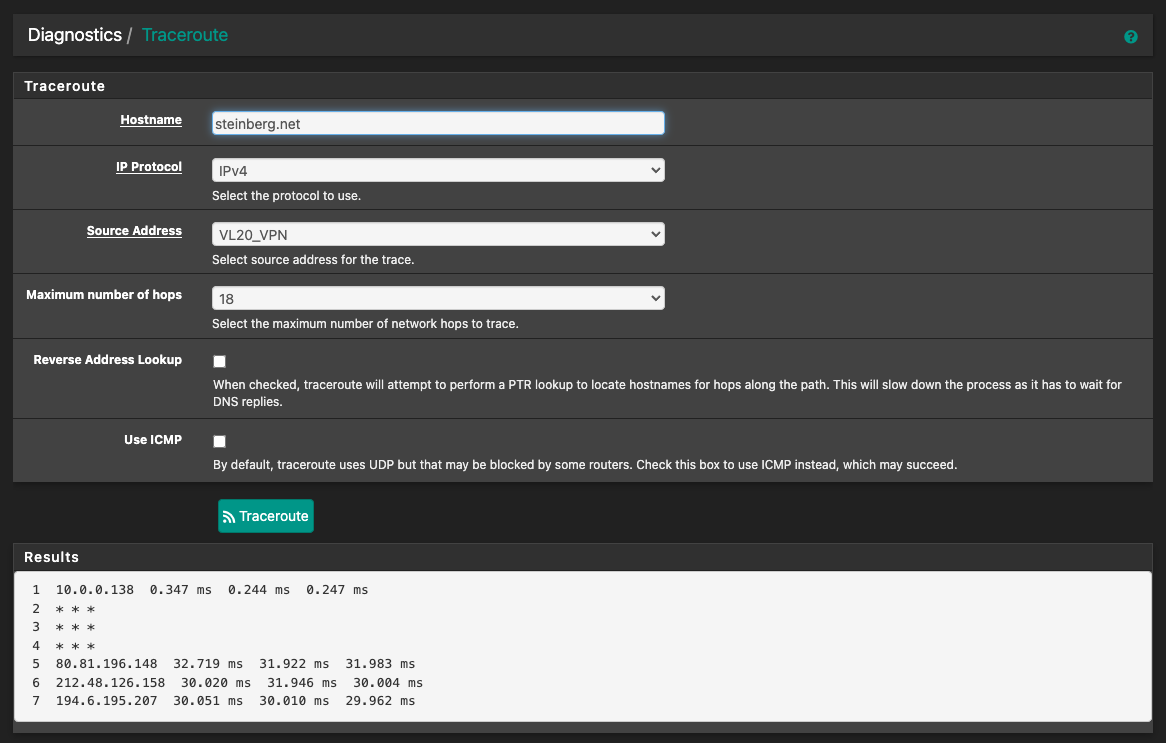
@dma_pf The traceroute seems fine, I even get internet now that I disabled the gateway monitoring for the wg interfaces. However connections take forever and are really unresponsive. Once a site is cached speeds on for example youtube are just fine. So it might have something to do with dns but I don't know where to look
-
@the_dave said in No Internet connection over Wireguard:
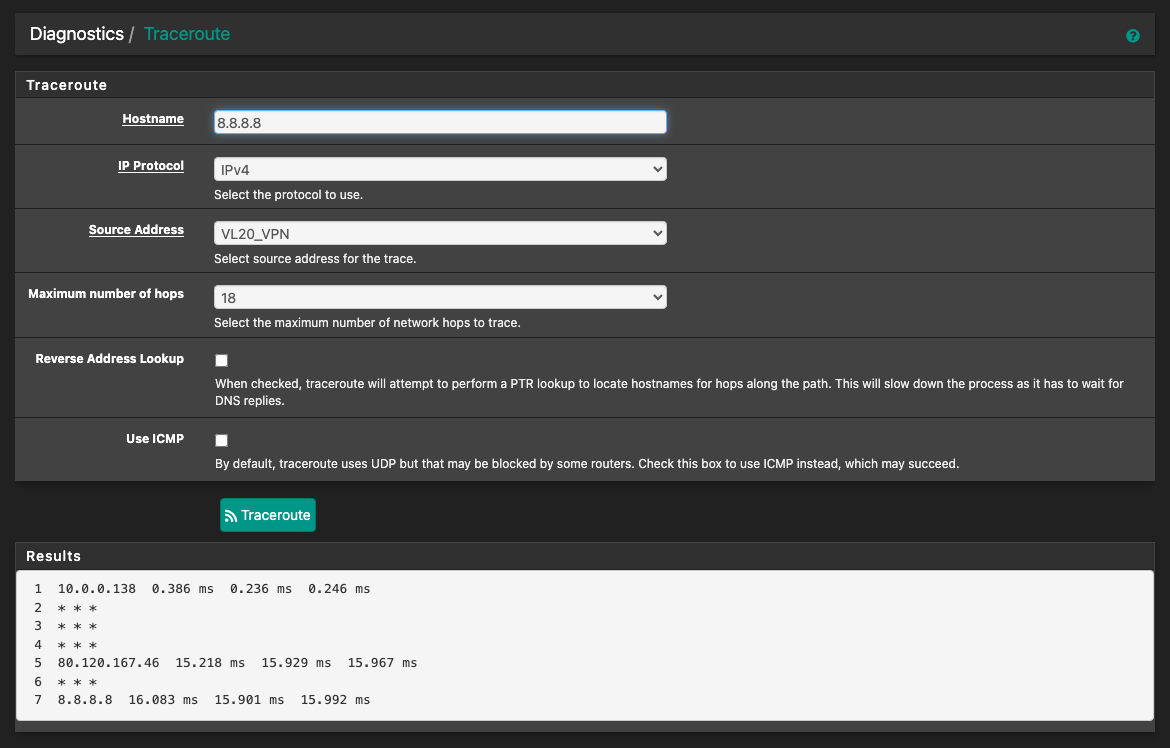
The traceroute seems fine
So by that you are saying that you can confirm that the traffic is being routed out the wiregurd tunnel?
I even get internet now that I disabled the gateway monitoring for the wg interfaces.
That would indicate that the monitor was experiencing packet loss and marked the interface as down. That can happen even if the there was no issue with the other end of the tunnel, like if you were monitoring an IP that was a way upstream of the other end of the tunnel and the packets got lost in the net and did not get to their destination. I'm assuming you have not experienced any issues on your WAN? What IP address were you using for the monitor? Are you using a VPN provider? If so, try a ping to their DNS server. If you get a response use that as the monitor IP. If not, then do a traceroute and try to ping the second IP in the route and if you get response, if so use uses that IP as the monitor.
Once a site is cached speeds on for example youtube are just fine. So it might have something to do with dns
Try to ping from that vlan to both an ip address (8.8.8.8) and a FQDN that is not cashed (yamaha.com responds). Do they both succeed? What are your response times?
-
I actually disabled the gateway monitoring because of this bug report. The actual monitoring process worked just fine. On the WAN interface everything works just fine. I noticed that websites either time out or load completely normal.
The response times don't seem that bad
-
@the_dave Update: I just added another loadbalanced gateway with mullvad to test if ovpn is the problem but results are exactly the same. I've also just checked internet on vl10 which uses dns over the wg interfaces and it works just fine. I think we can rule out the dns then, I just have no idea what to check now
-
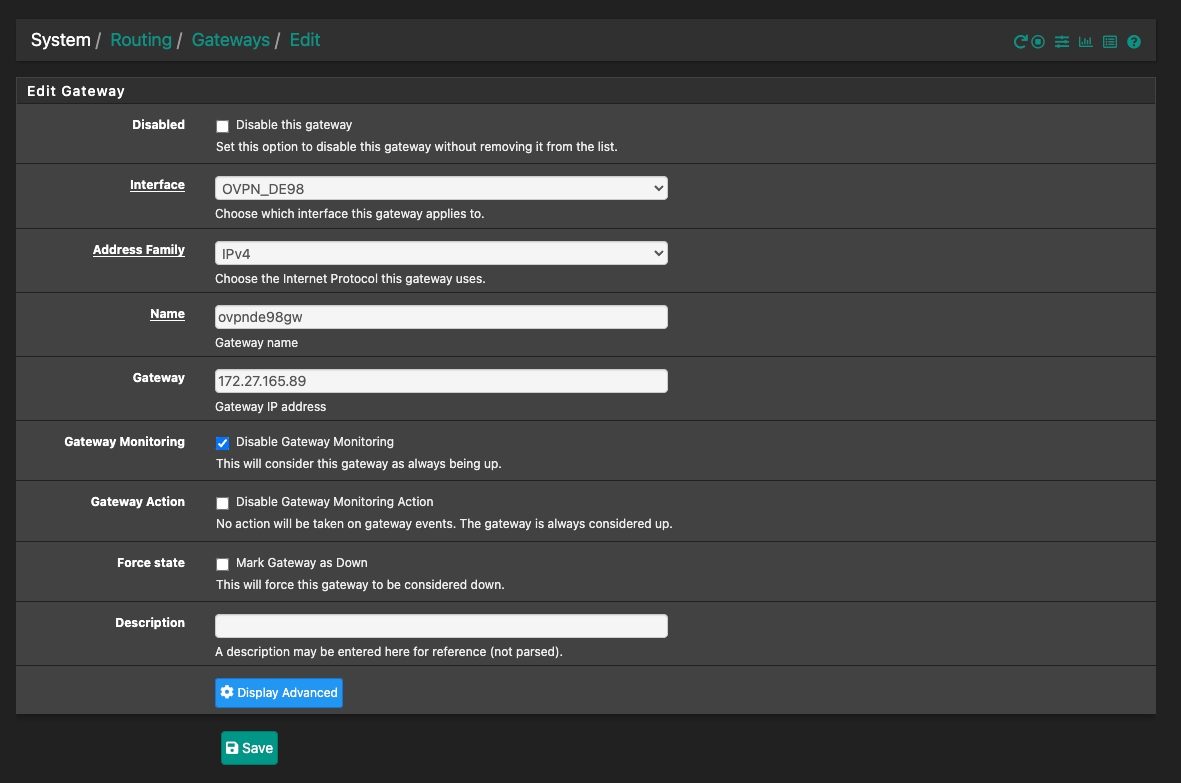
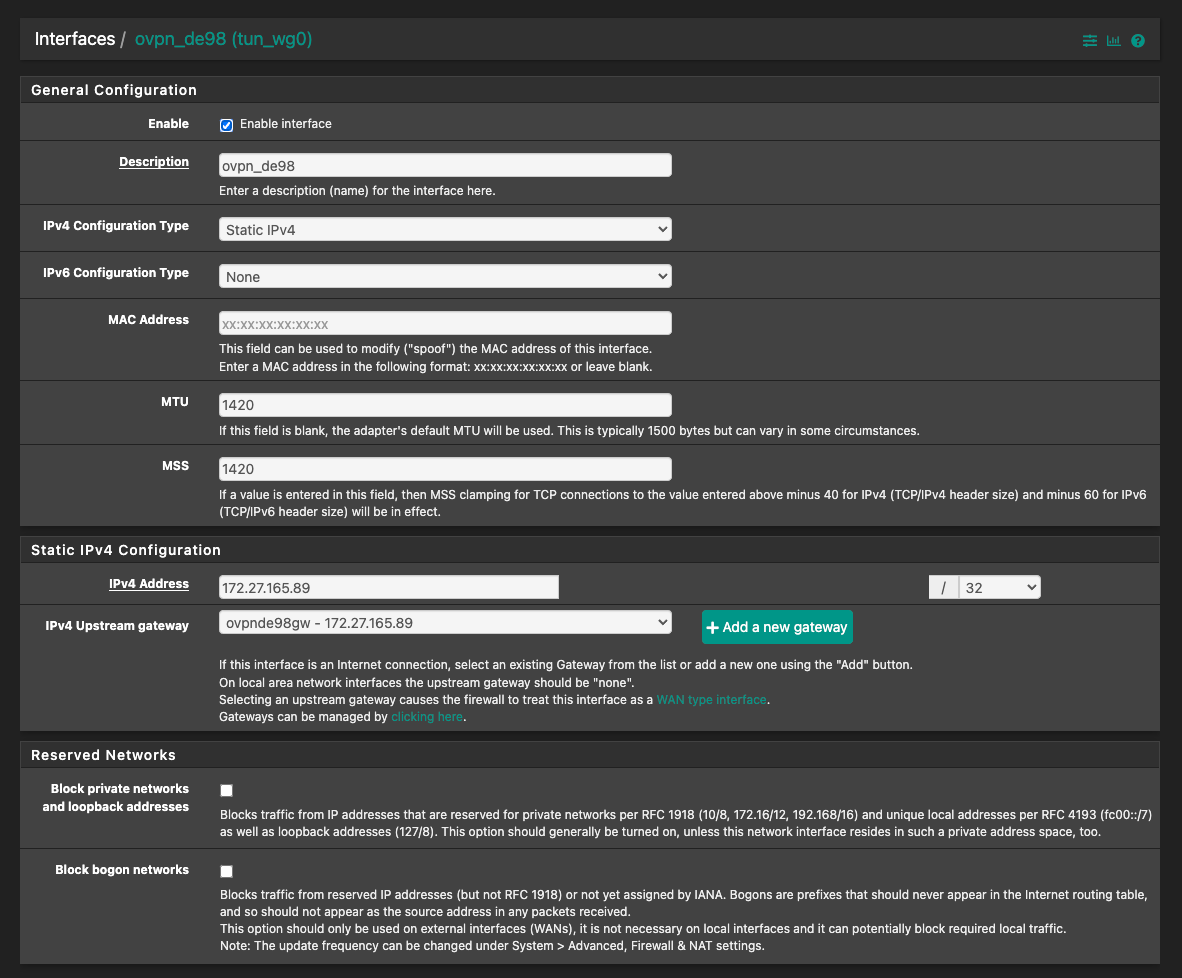
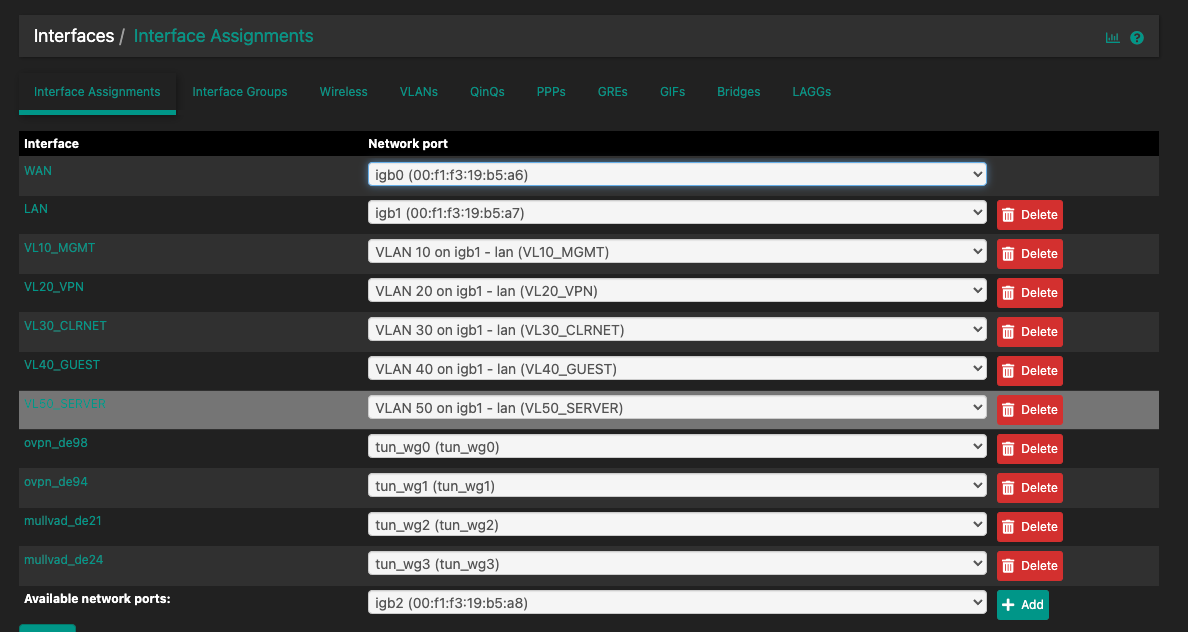
@the_dave Any chance that you can post some screenshots of your Interface assignment (Interfaces/ovpn-de98(tun_wg0)) and routing (System/Routing/Gateways/Edit)? On those interfaces the are the MTU and MSS values set to 1420? In not, set them that way and test.
-
@dma_pf I've followed the guide from Christian McDonald, so everything should be fine and 1420 is in the config
-
@the_dave I noticed that you are using Mullvad. There have been issues with their service (DNS hijacking) that have been reported on these forums. See if this helps: lhttps://forum.netgate.com/topic/166804/unbound-dns-resolver-through-wireguard-tunnel-mullvad-vpn?_=1645552497387
-
@dma_pf Thanks for directing me to the post, the problem is the configuration I use relies on the wg interface being the dns host. So I'd need to change the setting of the DNS resolver and forwarder and I'm a bit overwhelmed configuring that as the config from the guide is kind of complex for my level of understanding
Not sure if that is relevant, but I use the pfSense behind the isp's modem in dmz mode because passthrough is unfortionately not availible on a hybrid modem -
@the_dave It sounds like a DNS issue to me.
Are you using unbound as a DNS Resolver or Forwarder? If you are using it as a DNS resolver try to change the Outgoing interface to your WAN and see if that fixes it (Services-->DNS Resolver-->Outgoing Network Interface-->WAN).
As @dma_pf mentioned, Mullvad hijacks DNS requests, so if you have your WG interface set as the outgoing interface for the DNS resolver, you will have issues. It can be done (to avoid DNS leaks through WAN), but you need to get a special Mullvad internal IP as described here.
-
@packetpirate Thanks for the reply. I use the DNS resolver with Unbound. I looked further into the issue I have and it turns out that one wg connection seems to work just fine but as soon as I configure the loadbalanced mode I have the dns issues. I have no idea why this happens but I'm not willing to put more time in this. I switched to opnsense right now with pretty much the same configuration from the same guy that also posted about the solution to Mullvad's dns hijacking issues and it works completely fine so I'll stick with it for a while.