I can't get VLANs to work / No DHCP
-
@robh-0 Does your VLAN give out DHCP to things on other ports? If not do you have the rules on the new interface to allow UDP traffic?
-
@robh-0 I should add that I have the switch port on the main NIC configured to VLAN 4095
-
@rcoleman-netgate said in I can't get VLANs to work / No DHCP:
@robh-0 Does your VLAN give out DHCP to things on other ports? If not do you have the rules on the new interface to allow UDP traffic?
I have not configured any ports for DHCP. I have LAN, WAN, and this VLAN, and that's it. I'm currently getting DHCP on LAN from an Windows Server 2016, but if needed I can stop that and try it on pfSense. I will go configure that now and report back. Bear with me as it's limiting me here to one post every 2 minutes since I'm new.
Thanks in advance for the assistance!
-
OK, so I stopped DHCP on the Windows Server and added a pool to pfSense, and that works. I am troubleshooting this on an iPhone, so I configured a different DNS server in the pfSense pool so that I could validate that it is pfSense handing out DHCP and not the Windows Server. So, DHCP on the LAN port from pfSense does work.
-
@robh-0 What are the firewall rules for this new VLAN interface?
-
@rcoleman-netgate No rules at all, is that the issue?
-
@robh-0 As I noted before... you need to pass UDP traffic for DHCP to go through. Check your firewall logs - look for blocked traffic on your interface. Likely seeing UDP68 being blocked (DHCP).
LAN passes this out the gate as part of the initial configuration.
-
This is the log entry I had.
Mar 1 21:10:56 LAN Default deny rule IPv6 (1000000105) [fe80::cc2:d4e6:1721:58bf]:5353 [ff02::fb]:5353 UDP
It is just that one over and over, and that isn't even related. :(My rule on the VLAN now looks like this, but still no DHCP.
IPv4 * * * * * * none -
@rcoleman-netgate OK, let's troubleshoot this a little further back. I set up a laptop, put it in a switch port that's defined to be on this VLAN, set a static IP, and I can't ping the IP of the pfSense VLAN interface. So, this goes much deeper than just DHCP. There is something I'm missing, and I believe it's in how VMWare is configured to have this VLAN available.
-
@robh-0 To confirm check Diagnostics -> Packet Capture on the new interface and look for traffic. No traffic = nothing coming in to block (or pass).
-
@robh-0 said in I can't get VLANs to work / No DHCP:
I have the switch port on the main NIC configured to VLAN 4095
That a pass thru setting on a vswitch in esxi - what do you actually have the vlan ID set to on the actual physical switch port and pfsense?
There are couple of ways to go you could let esxi handle the vlans and set the vlan IDs on the vswitch or port groups, etc. or if you want pfsense to see the vlan IDs then on your vswitch/port group you would set vlan ID 4095 and it would pass through the tags..
-
@johnpoz The switch port is set to trunk/all. The physical interface in ESXi is set to port 4095.
I tried setting up another interface on the same port group with this VLAN (108) and that didn't work. There's just something I'm missing in the directions I linked to, because I don't have the exact same options they have documented.Packet capture came up blank, even with my test laptop on a switch port set to VLAN 108.
I can make all this work with Unifi, it just seems that putting pfSense on VMWare adds some complexity, and I know it's something simple and stupid that I'm not seeing.
-
@robh-0 Your PCAP came up empty -- so the pf is not seeing your traffic at all.
So there's something wrong upstream -- but it's not pfSense.
-
See if these help? This is what I'm trying now. If I understand correctly, this is the way that lets VMWare handle the VLAN?
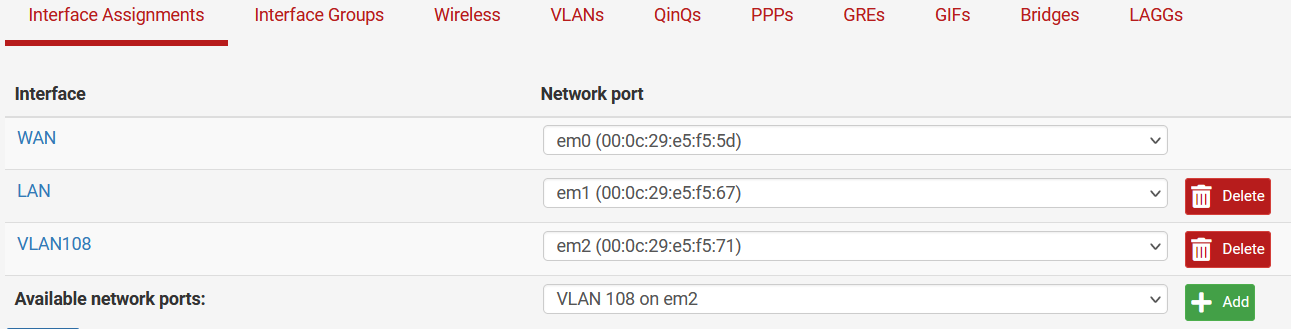
I have also tried this configuration but with VLAN108 interface assigned to the VLAN instead of the VMWare virtual NIC.
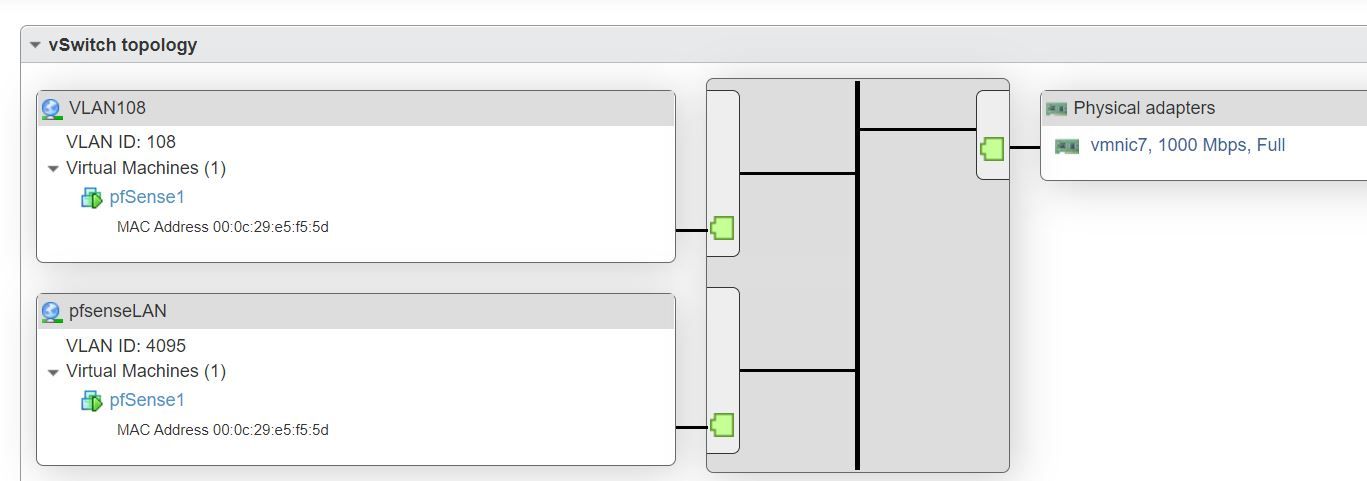
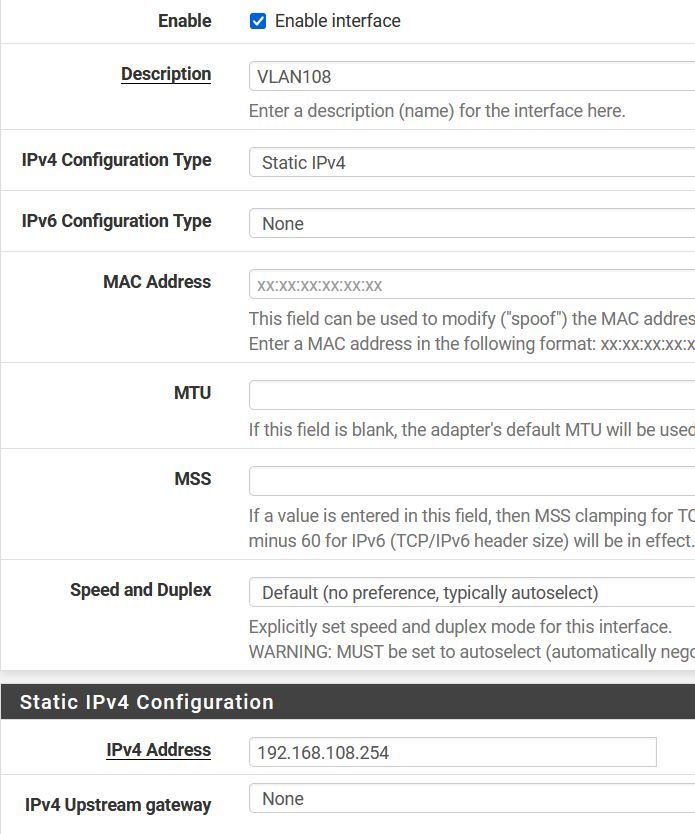
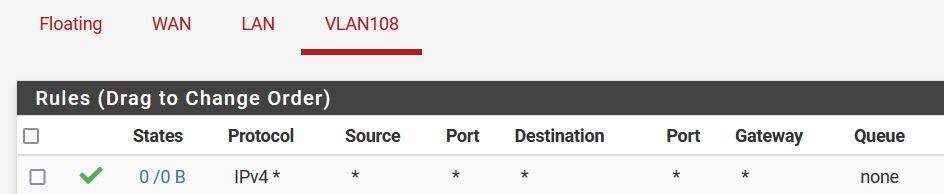
-
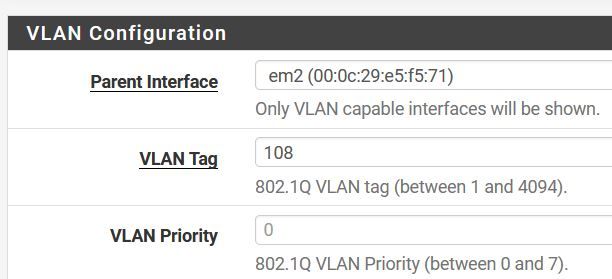
@robh-0 What is the VLAN interface set up as?
Interfaces -> Assignments -->> VLANs tab
-
I'm seeing my ICMPs in the packet capture now.
00:06:57.805004 IP 192.168.180.100 > 192.168.180.1: ICMP echo request, id 18010, seq 1111, length 9
00:06:57.805449 IP 192.168.180.1 > 192.168.180.100: ICMP echo reply, id 18010, seq 1111, length 9
00:06:58.242111 IP 192.168.180.100.42154 > 34.107.221.82.80: tcp 1
00:06:58.242119 IP 192.168.180.100.16373 > 34.107.221.82.80: tcp 1
00:06:58.308145 IP 34.107.221.82.80 > 192.168.180.100.42154: tcp 0
00:06:58.308184 IP 34.107.221.82.80 > 192.168.180.100.16373: tcp 0 -
@robh-0 Looks like you changed something that makes the traffic pass. Well done! DHCP should work now, too
-
Crap, that packet capture was invalid, I had the wrong interface selected. I'm still seeing nothing on the VLAN. That was the WAN interface.
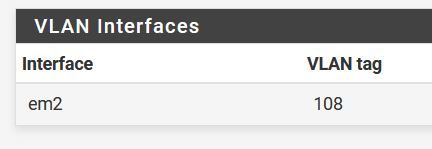
-
@robh-0 that looks wrong completely..
And trunk all means nothing... Where is the vlan tagged on your switch for 108, sure you trunk it to the physical interface on esxi device... But still has to be tagged... trunk all is nonsense term.. What vlans were allowed, what vlans were setup on the switch.
Where is the access port for your devices you want in vlan 108..
Why are you setting vlan 108 on a switch port? unless you tagged that into esxi on vlan 108.. You wouldn't set any vlan in pfsense then.
I have gone over there countless times here on the forums... Let me see if I can dig up one of the old threads..
Where is the setup in pfsense.. your calling it pfsense lan.. but you have that on vlan id set to 4095.. So what tags were you sending it - sure couldn't be 4095, that is special ID in esxi to pass through tags, like 108..
edit: btw
ESXi 6.5.0, Update 1
That is OLD!!! it sure doesn't support freebsd 12.3 that 2.6 runs on... Current version of esxi is 7.0 update 3c.. Why are you using esxi from 2017, that is EOL?
If your going to create a vlan 108 port group, then you would create a new virtual nic for pfsense and use it for that network, but there would be not vlan in pfsense - pfsense would see that as an untagged network.
-
@johnpoz These are Unifi switches, so what would normally be called a trunk is called "ALL" in the Unifi world.
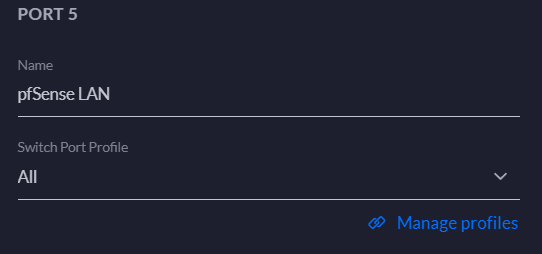
This is passing all VLANs to the physical NIC in the host.
I have also tried this configuration without VLANs in pfSense, using instead the port group that is assigned to VLAN 108, and that does not work either.
As to why I'm running such an old ESXi - It's a home server. I've only upgraded it once in its lifetime. It is in a secure environment, and it's only my wife and I at home. Yes, I run stuff on it that I need to be running, but for the most part I do this so that I'm not completely hands-off working in production networks, as I moved into InfoSec and then InfoSec Audit several years ago.