New install, RDP Ping rules not working
-
I have deployed an esxi host with a single NIC on my home network (192.168.1.51).
I have created an internal network on the esxi isolated from my home network (10.10.10.0/24). I have create pfsense vm with 2 interfaces WAN (home network - 192.168.1.71) and LAN (10.10.10.1), I have configured some rules to allow access to admin ports on the pfsense firewall from my home network and i can confirm they are working. I have created rules to allow rdp (NAT, port-forwarding) and ping from home network to lab network but these are not working. I have added a static route on my home router i can verify via tracert that it is getting as far as the pfsense firewall and then gets dropped. If i disable packet filtering on pfsense i can rdp successfully, this seems to indicate it can get through and maybe a problem with the rules. ALlo, if i run test port to the host on 3389 from pfsense gui it is successful. Also if i try to rdp and watch the pfsense logs i can see a green tick next to traffic rule in question.
I am wondering if i need a static route on the pfsense also or if i am missing something else in the basic config?
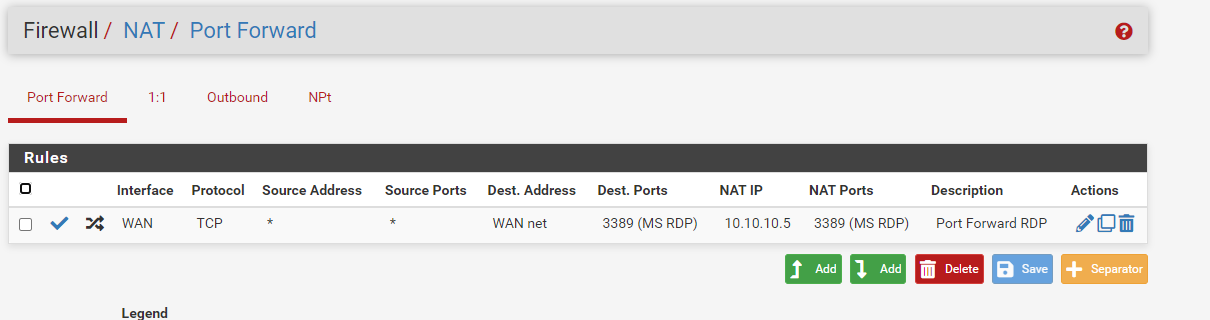
-
@longc
When you forwarding packets to a single IP, the destination address in the rule has to be single as well.
So you should select WAN address here. -
@viragomann do you mean in the NAT port forward rule "destination" should be the ip of the pfsense WAN interface?
-
@longc
That IP you want to forward. Could be the WAN interface address or a virtual IP, but it must be a unique IP. -
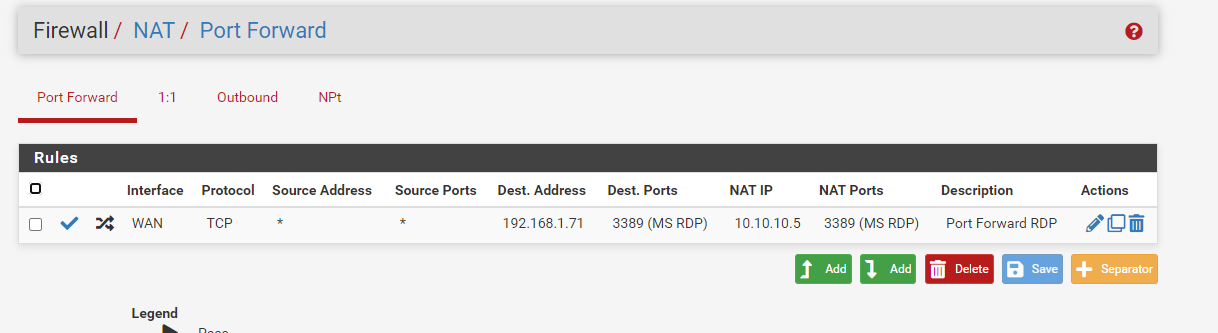
@viragomann like this?
-
@longc
Yes, the destination IP is ok, but consider that RDP also use UDP. So you to edit the rule and change it to TCP/UCP.When you want to forward pings you have to select ICMP there.
-
@viragomann still not working:(
If i go to the Diagnostics > TestPort in pfsense and run the test to the dst ip/port it is successful but only if i select "any" or "LAN" as the source address. If i select "WAN" it fails.
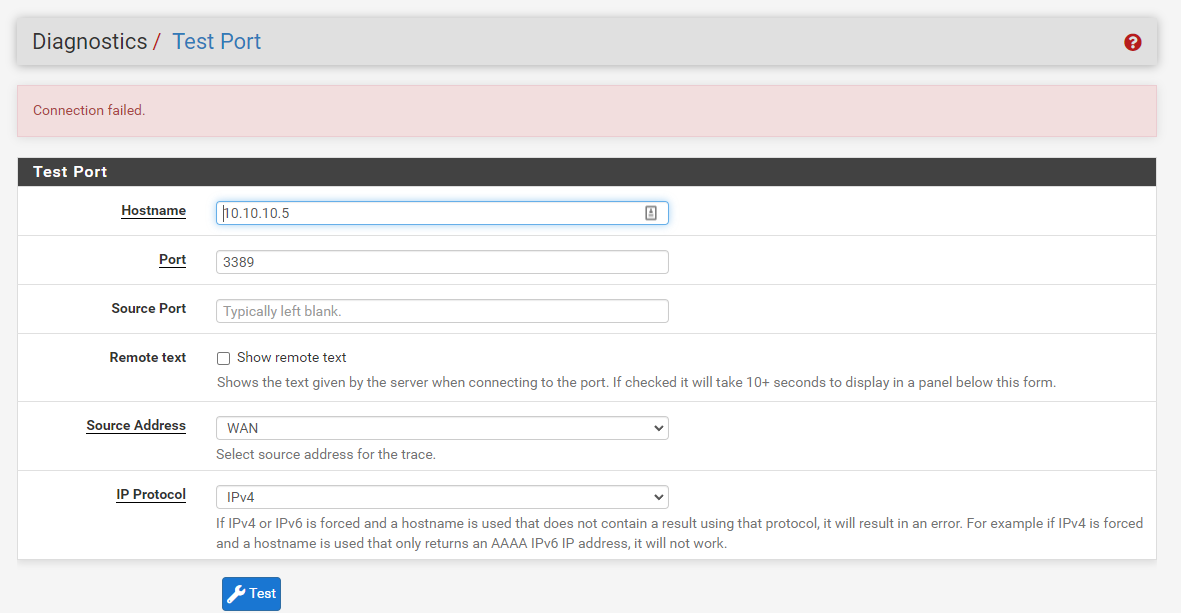
-
You testing is wrong.
Your RDP device isn't on the WAN network.
It might work with something that is called NAT reflection, that is ugly.
Change the source address to "any" and the test will work. If it still fails, your 10.10.10.5 does't have RDP active or accessible.To test a NAT rule, go to some device situated some where on the Internet, and test use the IP of your WAN - and port 3389.
Most often 'mstsc' will do.Btw : Microsoft didn't drop you a note that you should never (like never ever) expose an RDP device on the internet ?
RDP can be used from everywhere, but : over a VPN. -
@gertjan i think you should probably read my op properly.
-
@longc
Possibly the destination devices blocks connections from outside of its subnet?
However, if so, it should also not work, when pf filtering is disabled.To investigate, run a packet capture on port 3389 on the LAN interface, while you try to connect to RDP.
-
@viragomann rdp from a vm on the local network works fine and as you say when i have the pf disabled it works. See screenshot of packet capture on port 3389 below.
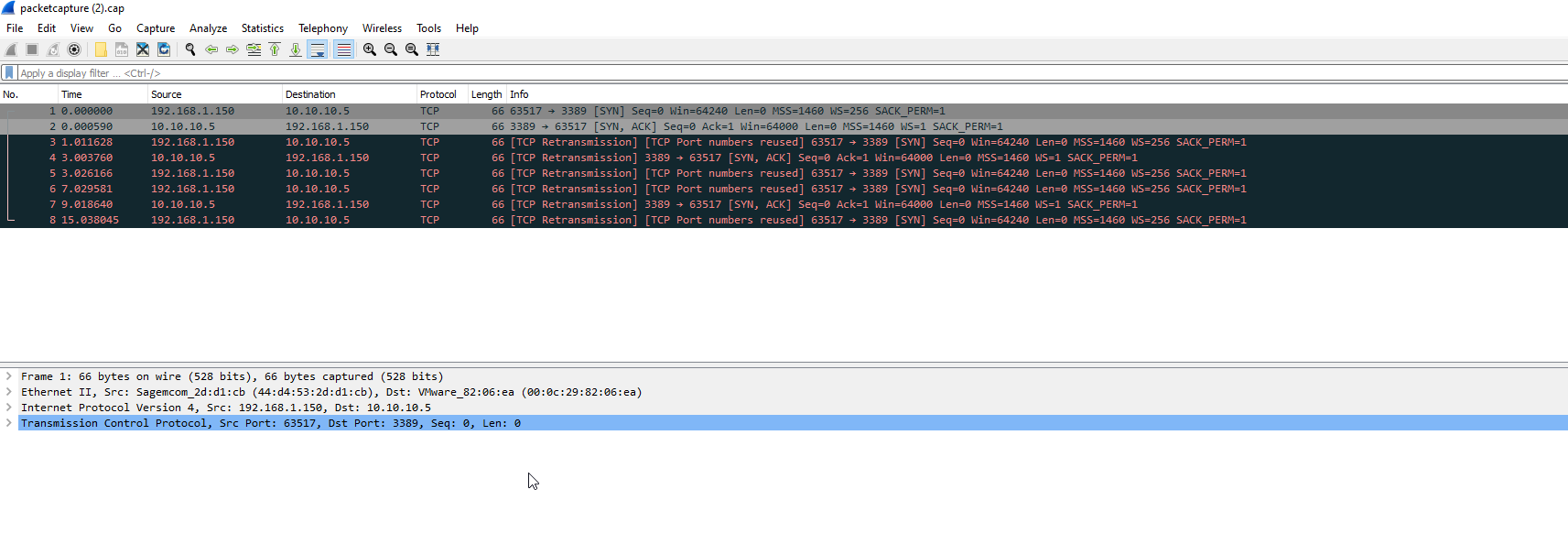
-
@longc
I didn't see your WAN rules, but the only thing I can think of is it is blocked by the "block private network" rule. -
@viragomann have checked that also.
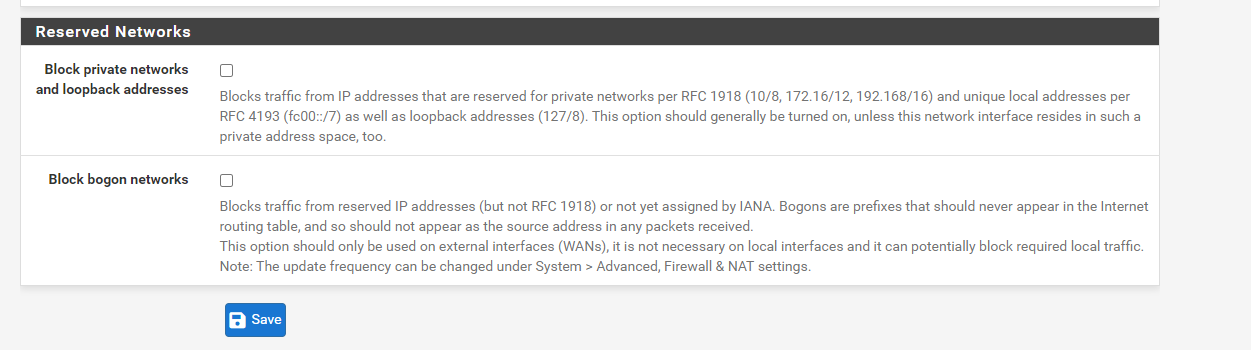
-
@viragomann so this is working now but I am not entirely sure how . I kind of stumbled on the "fix".
I have a Google nest for home wifi with multiple ap's around the house. This nest router has its own DHCP service on the 192.168.86.0/24 network. Anyway if I put my test device on this network everything works as expected with pfsense. I don't know is it because it is a different network to the wan interface of the pfsense.