Block Everything, except NTP
-
Been a while since posting... and everything has been great with pfsense.
I have a host that I want to block from getting out to the internet, except for gaining access to the internet NTP servers, and for some reason I just cannot get it to work. The block from the internet works, but I cannot get the allow NTP to work?
I am sure it is a simple issue, so would appreciate some feedback on where I am going wrong.
Here's the rules I have for the host in question...
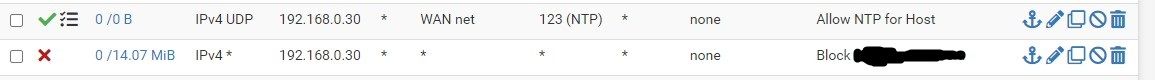
Any suggestions very much appreciated.
-
@gregoinc "WAN net" is not the internet. You can create a "RFC 1918-Alias" for easily blocking/allowing something like this.
-
@gregoinc assuming your expected NTP port is 123, you could make a rule that says allow, protocol tcp/udp from NETWORK to any destination, port 123. That’s it. Then the default drop will catch everything else. If you know the destination server or you have an alias you could specify that for the destination.
-
@gregoinc as mentioned "wan net" is not the internet, so unless your ntp server your client is wanting to talk to ntp server that is actually on your wan network that rule wouldn't work.
Your wan net is the actual network your wan is connected to, this might be some public block 64.53.x.x/21 like mine..
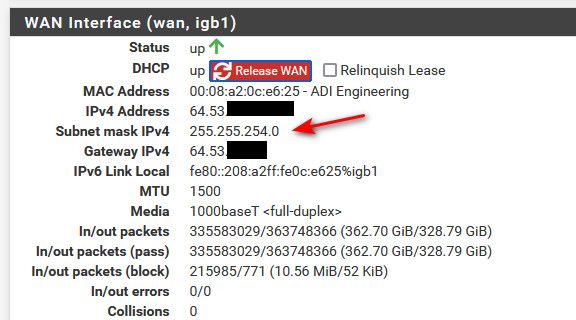
Or it might be the rfc1918 network if your pfsense behind a natting router. You can see what your wan network is by looking at your interfaces status and see what the mask is..
Just change that to any for destination if your client is going to talk to a bunch of ntp that you do not know where they are - like ntp pool. Or if you have your client pointed to specific ntp or list of specific ntp server then create rule to only those for destination, if you have a few of them, then use an alias to list all of the IPs of the ntp server it will talk to.
-
@gregoinc said in Block Everything, except NTP:
The block from the internet works, but I cannot get the allow NTP to work?
You could block all 'Internet' access, NTP included.
Fire up the NTP server on pfSense.
Check if it works.
Add a firewall rule that permits traffic from any device to pfSense (destination Firewall itself), protocol UDP, destination part 123.
Tell the DHCP server that it should give NTP IP when it deals out a lease :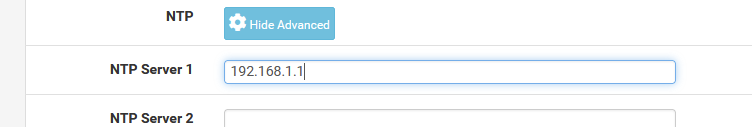
Where 192.168.1.1 is the IP LAN of pfSense.
Now your LAN devices will use (should use) pfSEnse as a time source.
-
@gertjan said in Block Everything, except NTP:
Now your LAN devices will use (should use) pfSEnse as a time source.
exactly! And even if they are hard coded to use something else, you could most likely redirect them - like how you can redirect dns to use pfsense and they wouldn't know any different ;)
-
@gertjan said in Block Everything, except NTP:
@gregoinc said in Block Everything, except NTP:
The block from the internet works, but I cannot get the allow NTP to work?
You could block all 'Internet' access, NTP included.
Fire up the NTP server on pfSense.
Check if it works.
Add a firewall rule that permits traffic from any device to pfSense (destination Firewall itself), protocol UDP, destination part 123.
Tell the DHCP server that it should give NTP IP when it deals out a lease :
Where 192.168.1.1 is the IP LAN of pfSense.
Now your LAN devices will use (should use) pfSEnse as a time source.
Hello Gertjan,
I tried your suggestion and it works like a charm. Appreciate all the feedback on this topic, was great to see all the information sharing.
Thanks, Mark