How to copy-paste information from OVPN file
-
@dimskraft said in How to copy-paste information from OVPN file:
Where is the reference to CA and CERT from within client connection?
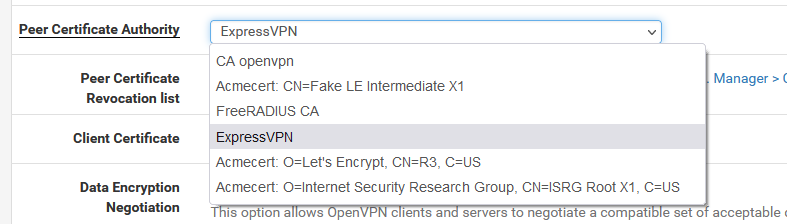
My VPN ISP gave a CA and and a certificate. I've created them in the CA and certificate in the pfSense Certifiate Manager.
Peer Certificate Authority :
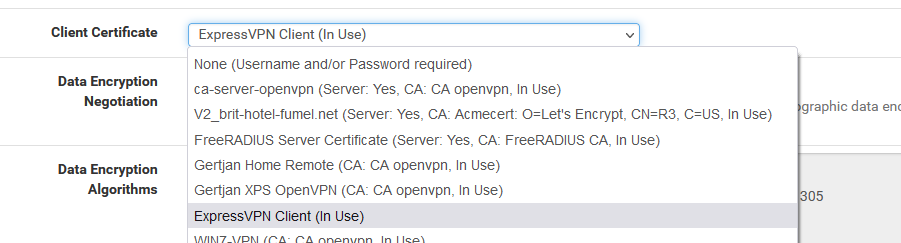
and Client Certificate :
@dimskraft said in How to copy-paste information from OVPN file:
And it doesn't work.
What was incorrect?Status > System Logs > OpenVPN
-
Yes, more consistent way was to choose server mode to SSL/TLS
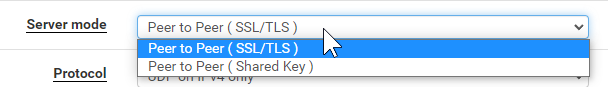
This made fields username/password to appear, but I left them empty. Other fields appeared and I filled them
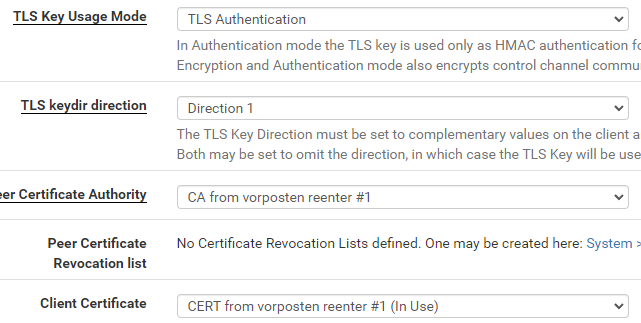
Nevertheless, I see
Mon Mar 7 08:20:46 2022 us=482944 TLS Error: incoming packet authentication failed from [AF_INET]MY.IP.ADD.RESS
Mon Mar 7 08:20:48 2022 us=877841 Authenticate/Decrypt packet error: packet HMAC authentication failedon server side. As if keys are incorrect, but I copy pasted them from ovpn file which works.
-
-
@gertjan yes, exactly the same here
-
They look the same ?!
They can't be the same, as these keys are random, and this is one used by Expre**VPN.Both sides use the same OpenVPN version ?
If you have a smart phone, you could test your OpebVPN server connection.
Use this app.On the OpenVPN server, export with
Import the file on your phone. The connection should work.
-
@gertjan sorry, not EXACTLY the same :)
-
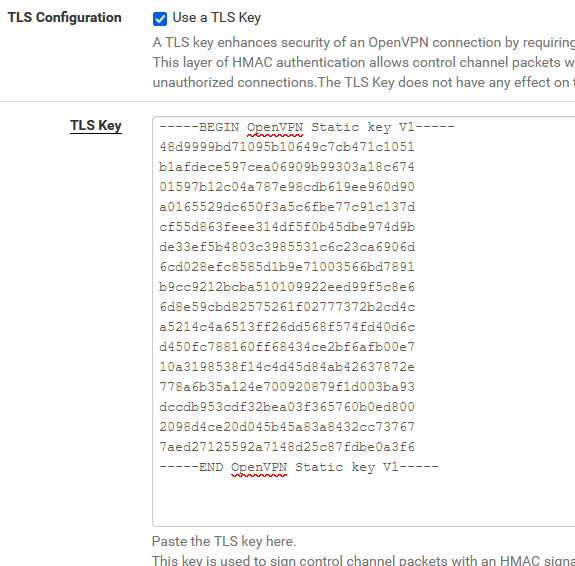
I tried to generate key on pfSense side and copy it to server and ti didn't help :(
my server config is fllowing:
server 192.168.255.0 255.255.255.0 verb 3 key /etc/openvpn/pki/private/VPN.SERVERNAME.COM.key ca /etc/openvpn/pki/ca.crt cert /etc/openvpn/pki/issued/VPN.SERVERNAME.COM.crt dh /etc/openvpn/pki/dh.pem tls-auth /etc/openvpn/pki/ta.key key-direction 0 keepalive 10 60 persist-key persist-tun proto udp # Rely on Docker to do port mapping, internally always 1194 port 1194 dev tun0 status /tmp/openvpn-status.log user nobody group nogroup comp-lzo no ### Route Configurations Below route 192.168.254.0 255.255.255.0 ### Push Configurations Below push "block-outside-dns" push "dhcp-option DNS 8.8.8.8" push "dhcp-option DNS 8.8.4.4" push "comp-lzo no"and my working client file is following
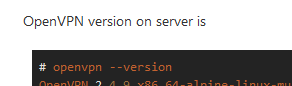
client nobind dev tun remote-cert-tls server remote VPN.SERVERNAME.COM 1194 udp key vorposten.key ca ca.crt cert vorposten.crt tls-auth ta.key 1 redirect-gateway def1OpenVPN version on server is
# openvpn --version OpenVPN 2.4.9 x86_64-alpine-linux-musl [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [MH/PKTINFO] [AEAD] built on Apr 20 2020 library versions: OpenSSL 1.1.1g 21 Apr 2020, LZO 2.10 Originally developed by James Yonan Copyright (C) 2002-2018 OpenVPN Inc <sales@openvpn.net> Compile time defines: enable_async_push='no' enable_comp_stub='no' enable_crypto='yes' enable_crypto_ofb_cfb='yes' enable_debug='yes' enable_def_auth='yes' enable_dlopen='unknown' enable_dlopen_self='unknown' enable_dlopen_self_static='unknown' enable_fast_install='yes' enable_fragment='yes' enable_iproute2='yes' enable_libtool_lock='yes' enable_lz4='yes' enable_lzo='yes' enable_management='yes' enable_multihome='yes' enable_pam_dlopen='no' enable_pedantic='no' enable_pf='yes' enable_pkcs11='no' enable_plugin_auth_pam='yes' enable_plugin_down_root='yes' enable_plugins='yes' enable_port_share='yes' enable_selinux='no' enable_server='yes' enable_shared='yes' enable_shared_with_static_runtimes='no' enable_small='no' enable_static='yes' enable_strict='no' enable_strict_options='no' enable_systemd='no' enable_werror='no' enable_win32_dll='yes' enable_x509_alt_username='no' with_aix_soname='aix' with_crypto_library='openssl' with_gnu_ld='yes' with_mem_check='no' with_sysroot='no'I don't know how to know version of pfSense' OpenVPN
Version of pfSense itself is
2.5.1-RELEASE (amd64) built on Mon Apr 12 07:50:14 EDT 2021 FreeBSD 12.2-STABLE -
@gertjan my server is https://github.com/kylemanna/docker-openvpn
pfSense is a client
-
Use the same command on pfSense ;)
Your (old now) pfSEnse 2.5.1 is using (I don't recall any more) OpenVPN 2.5.2 ?
2.5.x on the client side, and 2.4.x on the server side (probably time to upgrade your docker and pfSEnse) should work.
But there is a but.
If you use mixed versions on both sides, you should really read the changelogs : https://community.openvpn.net/openvpn/wiki/ChangesInOpenvpn25, just to make sure you not using an option that changed somewhat.Did the phone app test work ?
What about an easy bare bone setup with certs, just a user/password + no -or minimal) crypto) stuff.
That is, if you control the server side and have access to the server log file. -
This post is deleted!