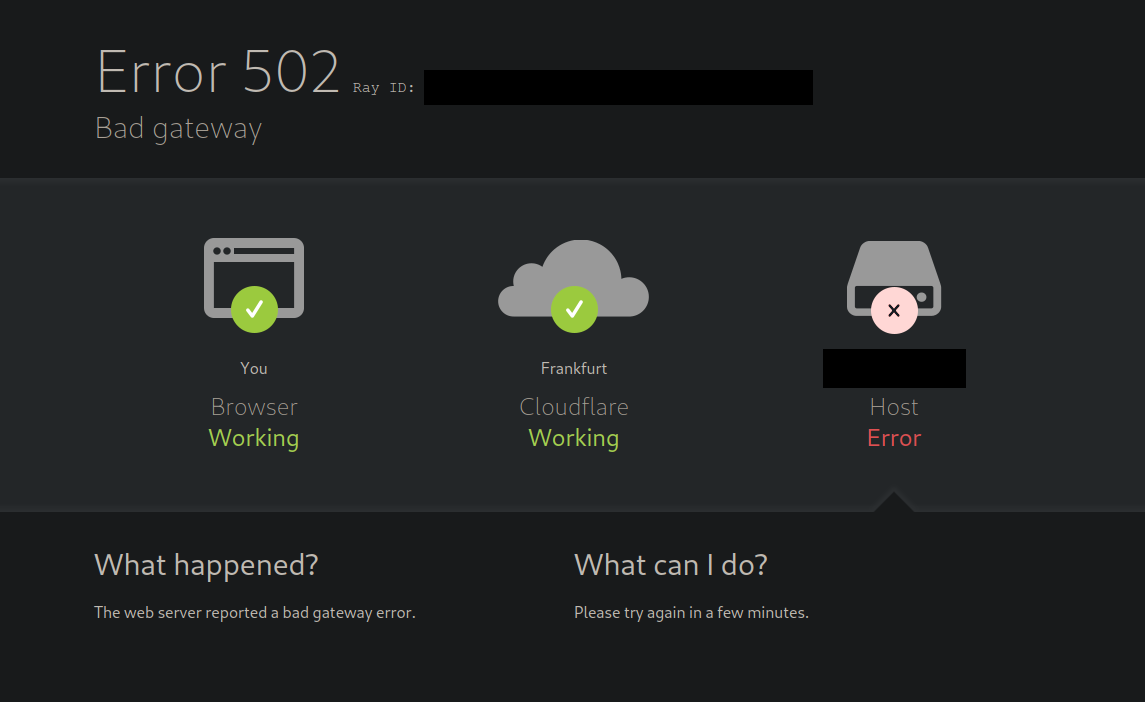
HAProxy 502 bad gateway with Cloudflare Proxy
-
@menethoran I should expand…
Cloud flare with proxy on is 1 proxy…
Your PfSense (I believe) is another (when you’re using haproxy) (2)
If you have a NAS that creates applications your working with, that’s ANOTHER proxy (3) (I use trueNAS personally)And 3 is too many proxies ;)
-
@menethoran can you elaborate on the WAN stuff a bit more? What had you changed?
Disabling the Cloudflare proxy does not seem to fix my issue with my services only working locally on one pc.
-
Okay, I disabled all the virtual ip stuff and the cloudflare proxy and the services are working again. I still would like to get that working ^^.
-
@klaussemmler
I would get rid of the bridge altogether and use switch. I don't see a reason not to use one. Switches are affordable and if you need managed switch you can get one from eBay.
Dell PowerConnect 2724 24 Port Gigabit Ethernet Managed Switch
-
@te7 This was just my missing experience with pfsense to try the LAN Bridge. I learned, that a dedicated switch is the way to go. Thanks for the advice! I will likely get a switch with multiple sfp+ ports as I have multiple devices with such ports. When I get one, I will come back to this topic, but this will take a bit of time. Here money is my limit ^^.
-
@menethoran said in HAProxy 502 bad gateway with Cloudflare Proxy:
@klaussemmler so, jumping over from my thread to hopefully help you.
One huge problem I had (other than not recognizing that WAN is not internet ;) ) was that I had too many proxies working against each other. If you are working with cloudflare (only one I can speak about as it’s the only one I use) is to set cloudflare to dns forwarder only, do not proxy) doing that alone solved all of the fight I was having
I don't think that disabling CloudFlare proxy is a sound advice. That will expose your IP address to the Internet and at the same time you will lose all of the benefits of using CloudFlare's cashing and protection against domain attacks. The whole point of using CloudFlare DNS proxy is hide your IP and let CloudFlare handle all bad guys out there trying to hack your web site or whatever you are hosting behind proxy.
See small example of CloudFlare firewall activity for my domain in the past 24hrs.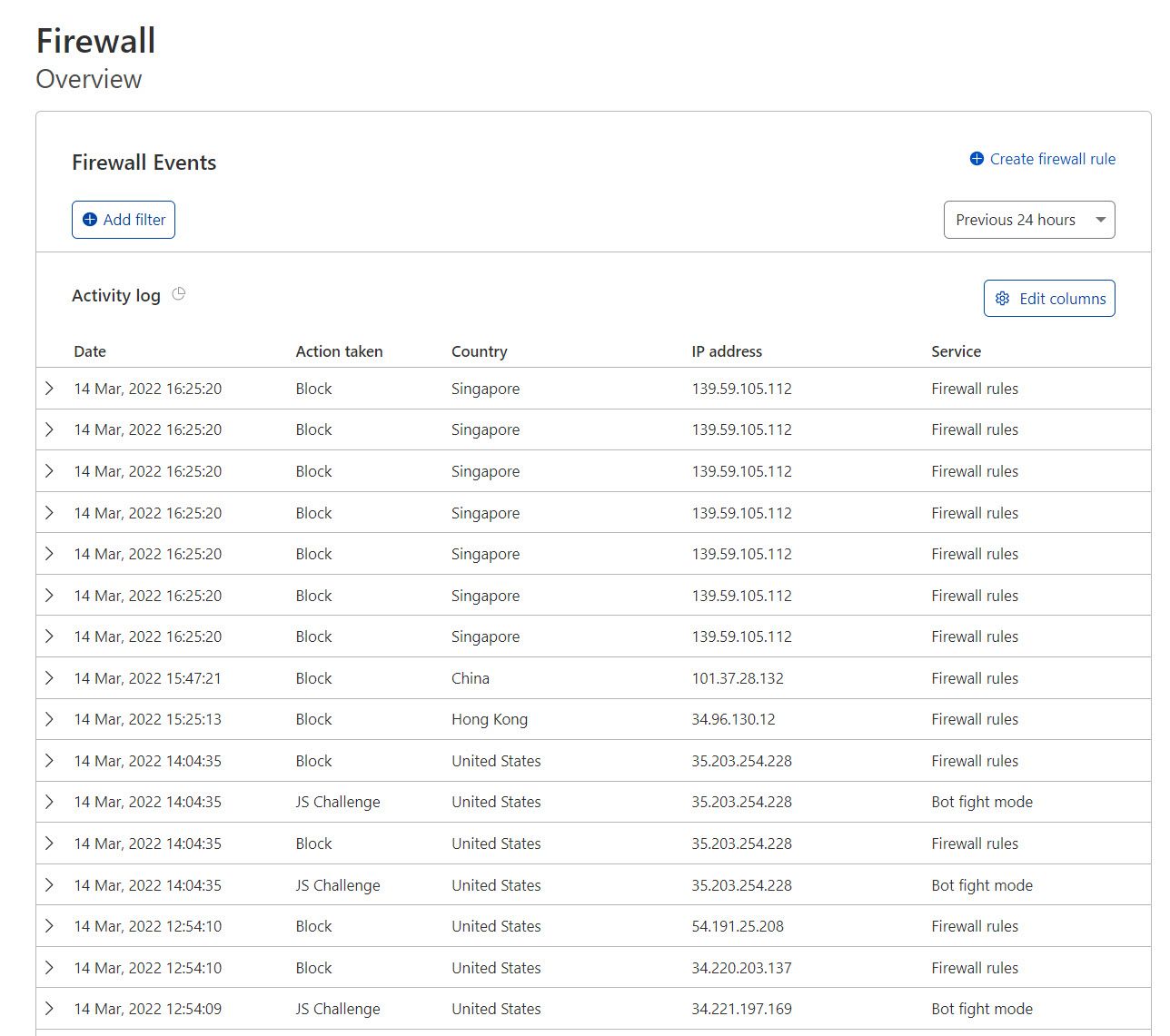
-
@te7 That is true. I will revisit this when I got my switch and see if it works better then. With the cloudflare proxy feature I always get timeouts when using my services. Pining them works fine though. I have neither an idea nor an solution for this problem yet.
-
@klaussemmler
That points to your pfSense rules and HAProxy settings. You are close and using switch will make it easier to troubleshoot everything.
-
@te7 I also tried the packet capture feature and get tcp traffic but it seems like it never reached the service defined in the haproxy backend. Without the cloudflare proxy, everything works, but this is not optimal. This could also be a funky issue with lan bridging and if that is the case the switch could fix that. It is fascinating how many tools pfsense provides for debugging out of the box. I do not understand all tools but I try to learn about them step by step.
-
I now tried some other things:
- Using the cloudflare origin certificate on the haproxy frontend and as webConfigurator certificate -> did not change anything.
- Setting the SSL/TLS encryption mode in cloudflare to flexible intsead of full or full (strict) -> did also not fix it. Without the cloudflare proxy, the full (strict) mode works fine.
These where some things I saw as suggestion to fix the problem. Sadly without success.
-
@klaussemmler Have you found an solution of this issue? I had the same setup and the same problem as you had.
-
@jycai I have installed a Mikrotik CRS305 as Switch in my Network and at least the odd kde connect behaviour is fixed.
But the cloudflare issue still remains.
-
I now tried to setup up everything with squid reverse proxy instead of haproxy but the issue with cloudflare proxy still remains. So it should not be a problem with haproxy itself.
-
It seems like I have found the answer!
Cloudflare DNS Proxy only works with http/https traffic on free tier. If non http/https traffic is used, for example when using a minecraft server, the DNS Proxy does not work.
This is where I got the information from:
https://community.cloudflare.com/t/cloudflare-minecraft-proxy/167417
-
@klaussemmler Some people mention pfBlockerNG is blocking traffic from Cloudflare proxied server, but my website still not work after I completely removed pfBlockerNG and reboot pfSense .
-
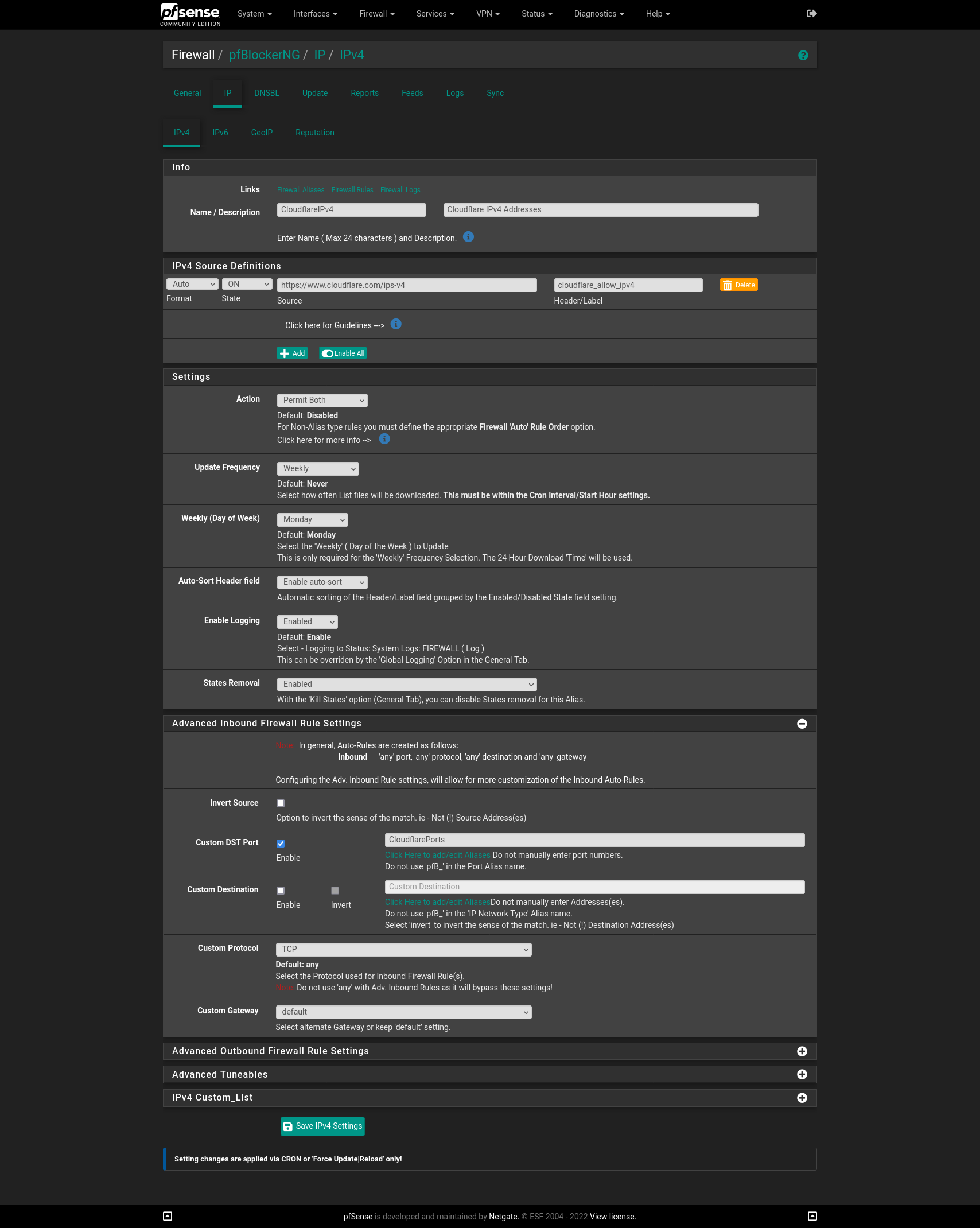
@jycai Have you whitelisted the cloudflare ips in your pfSense? You can actually do this automated with pfBlockerng.
The ipv4 ips can be found here: https://www.cloudflare.com/ips-v4
The ipv6 ips can be found here: https://www.cloudflare.com/ips-v6My pfBlockerng config for ipv4 looks like this (The alias at Custom DST Port contains port 80 and 443):
-
@klaussemmler Thank you I added the Cloudlfare IPs whitelist in pfBlockerNG as you suggest, however the Clourflare proxied still not working with Haproxy SSL offload on my nextcloud website. I don't get the error as 502, but missing half page info. It is working when Cloudlfare proxied is off.
I am runing version 2.6 and will try 2.52 and 2.4 later on to see if it makes a difference.
-
@jycai Okay, interesting. Another thing that could cause problems with cloudflare is the encryption mode in the SSL/TLS menu. Try the modes flexible, full and full (strict) and see, if this fixes your problem.
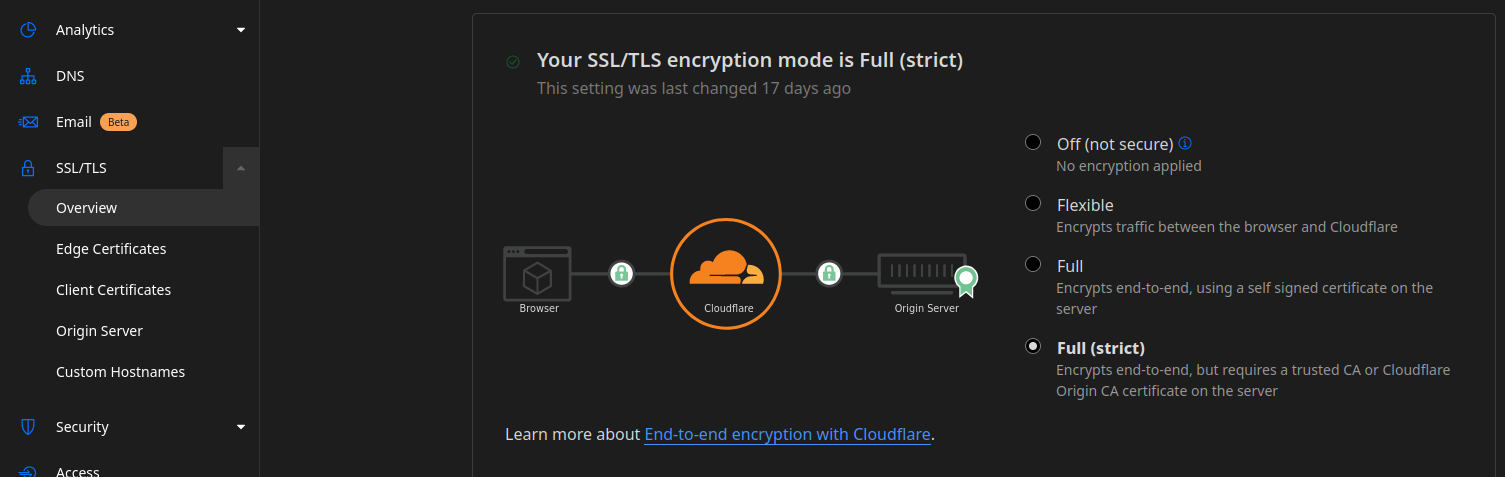
-
@klaussemmler
Flexible mode - no connection at all
Full - Load half page
Full(strict) - Error 526
V2.6, V2.52 and V2.4 with Acme or Cloudflare origin server certificate - all the same result.
-
@jycai I am kinda out of ideas. But you can try to toggle the options in SSL/TLS -> Edge Cetificates.
And are you sure you use the correct certificates for all servers?