NordVPN setup on pfsense - questions about basics
-
@pftdm007 Hybrid mode is the preferred mode. From there it splits the view into manual & automatic rules. I usually nerf all of the ISAKMP rules as I don't use IPSEC.
-
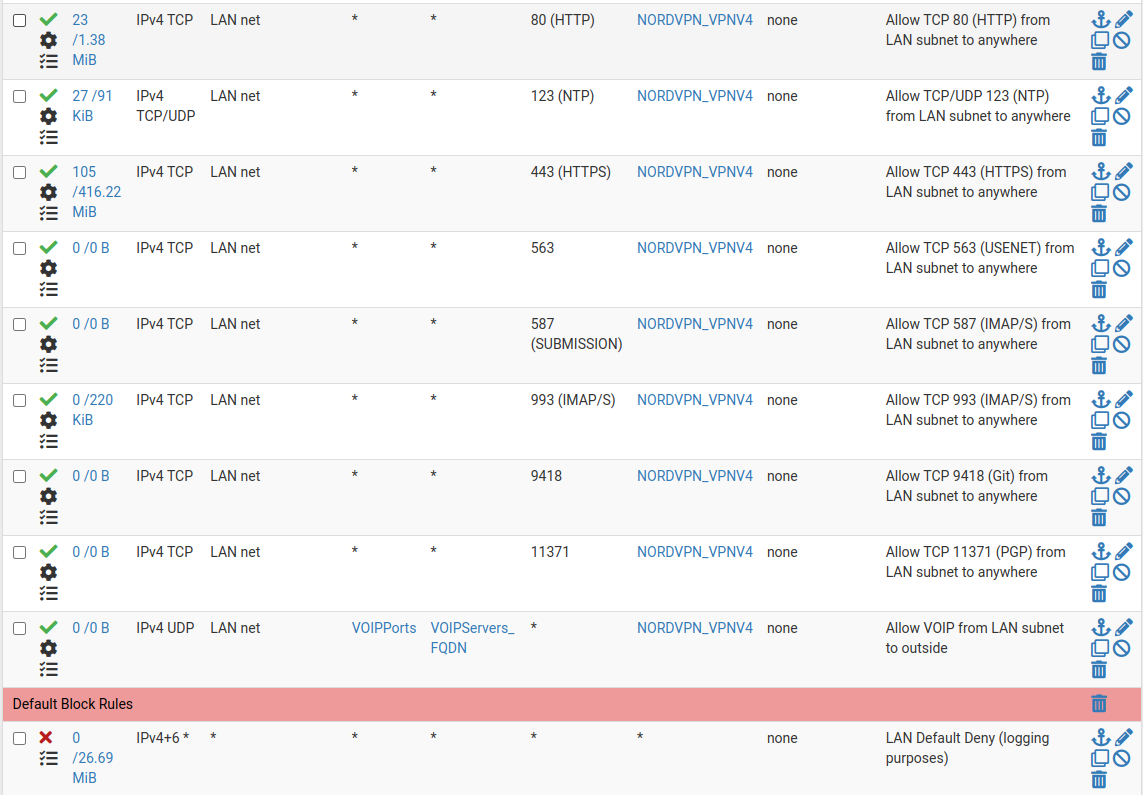
Sweet, things seems to work, with the minor exception that for some reasons, reddit.com is blocked by firewall rules.... So far I believe its the only one... I can see the blocked traffic in the firewall logs, and the rule that triggers the block is the "Lan Default Deny" rule of the LAN interface...
Can you see what's the problem with my rules? Not sure why it is blocked, and why reddit is the only site being blocked...
-
@pftdm007 Your rules allow web traffic. Maybe you're misinterpreting the log? Can you precisely correlate attempts to access Reddit with the blocks in the log? If everything else works except that one site then I would look at other things. Does Reddit allow access from known NordVPN endpoints? Are you using any sort of web filter, proxy or IDS, eg. pfBlocker, Squid/Squidguard, Snort, Suricata?
-
I really dont get it but I made it work... Every time I tried to access reddit.com, I saw alerts showing up pretty much at the same time in the FW logs.
They were for IP's
- 146.75.33.140 -> blocked by pfblocker GeoIP
- 146.75.37.140 -> blocked by pfblocker GeoIP
- 151.101.193.140 -> blocked by "LAN default Deny"
It seems that these IP's are reddit servers (at least 151... is). This morning I have whitelisted the two "146.75...." in pfblocker, and "151...." is no longer showing up in the FW alerts...
What I don't get is why these IP's have been flagged and blocked right after I activated the VPN....
-
@pftdm007 Aha, pfBlocker. I thought it would be something like that.
What I don't get is why these IP's have been flagged and blocked right after I activated the VPN
Companies use content delivery networks (CDNs) all around the world to deliver their content faster to local users. By using the VPN and whatever location endpoint you selected, you are likely being directed to a CDN whose IP just happens to be on someone's block list.
-
Thanks for your help & guidance!!! I think this is SOLVED!
-
Unfortunately, I'm back with major issues. After setting up everything, at first it seemed to work well but its not.
Issue 1: ISP (public) IP is randomly visible depending if pfsense has been freshly rebooted or not, and if openvpn works.
At first when I setup everything as per the above discussions, everything seemed to work well. I did a "whats my ip" on several locations to check if my public IP was visible. Google and many other sites (like whatsmyip.org) reported my VPN remote IP. However, DuckDuckGo could somehow still get my real IP. I tried with 4 different browsers, used safe mode (firefox) to disable potentially interfering plugins, to no avail...
I rebooted pfsense and my computer but it didnt help. NordVPN have been useless blaming a plugin in my browser.
Today as I was on the web, I lost connectivity (issue #3 below). The "resolution" was to restart OpenVPN, however, after doing so, my real IP is now visible to all, including google and the other sites.
There seems to be a major bug with OpenVPN or something is fundamentally wrong with my setup. Help is welcome as the VPN is currently useless.
Issue 2: Connection issues and real IP suddenly visible to all
I'm browsing the web when suddenly my browser returns 404 errors (firefox -> We’re having trouble finding that site). Next thing I know, my real IP is visible to everybody. I login to pfsense and everything seems to be OK (AFAIK) (openvpn service is running, no errors in logs, etc). I decide to reboot pfsense then I'm back to "normal" with issue 1 still ongoing.
Issue 3: The internet connection drops off
Today the connection randomly dropped off. I restarted the OpenVPN service which restored the connection but made my real IP again visible to all. While the connection was down, the service displayed as running but the widget on the main page said "Offline, 100% packetloss". Unfortunately I cannot see anything wrong in the system logs other than:
Mar 13 16:24:10 openvpn 42217 SIGTERM[soft,exit-with-notification] received, process exiting Mar 13 16:24:10 openvpn 42217 /usr/local/sbin/ovpn-linkdown ovpnc1 1500 1584 XXX.XXX.XXX.XXX 255.255.255.0 init Mar 13 16:24:10 openvpn 42217 Closing TUN/TAP interface Mar 13 16:24:09 openvpn 42217 SIGTERM received, sending exit notification to peer Mar 13 16:24:09 openvpn 42217 event_wait : Interrupted system call (code=4) Mar 13 16:24:04 openvpn 42217 MANAGEMENT: Client disconnected Mar 13 16:24:04 openvpn 42217 MANAGEMENT: CMD 'status 2' Mar 13 16:24:04 openvpn 42217 MANAGEMENT: CMD 'state 1' Mar 13 16:24:04 openvpn 42217 MANAGEMENT: Client connected from /var/etc/openvpn/client1/sock Mar 13 16:23:47 openvpn 42217 MANAGEMENT: Client disconnected Mar 13 16:23:47 openvpn 42217 MANAGEMENT: CMD 'status 2' Mar 13 16:23:47 openvpn 42217 MANAGEMENT: CMD 'state 1' Mar 13 16:23:47 openvpn 42217 MANAGEMENT: Client connected from /var/etc/openvpn/client1/sock Mar 13 16:23:37 openvpn 42217 MANAGEMENT: Client disconnected Mar 13 16:23:37 openvpn 42217 MANAGEMENT: CMD 'status 2' Mar 13 16:23:37 openvpn 42217 MANAGEMENT: CMD 'state 1' Mar 13 16:23:37 openvpn 42217 MANAGEMENT: Client connected from /var/etc/openvpn/client1/sock Mar 13 16:23:37 openvpn 42217 MANAGEMENT: Client disconnected Mar 13 16:23:37 openvpn 42217 MANAGEMENT: CMD 'status 2' Mar 13 16:23:37 openvpn 42217 MANAGEMENT: CMD 'state 1' Mar 13 16:23:37 openvpn 42217 MANAGEMENT: Client connected from /var/etc/openvpn/client1/sock Mar 13 16:22:53 openvpn 42217 MANAGEMENT: Client disconnected Mar 13 16:22:53 openvpn 42217 MANAGEMENT: CMD 'status 2' Mar 13 16:22:53 openvpn 42217 MANAGEMENT: CMD 'state 1' Mar 13 16:22:53 openvpn 42217 MANAGEMENT: Client connected from /var/etc/openvpn/client1/sock Mar 13 16:22:45 openvpn 42217 MANAGEMENT: Client disconnected Mar 13 16:22:45 openvpn 42217 MANAGEMENT: CMD 'status 2' Mar 13 16:22:45 openvpn 42217 MANAGEMENT: CMD 'state 1' Mar 13 16:22:45 openvpn 42217 MANAGEMENT: Client connected from /var/etc/openvpn/client1/sock Mar 13 16:22:34 openvpn 42217 MANAGEMENT: Client disconnected Mar 13 16:22:34 openvpn 42217 MANAGEMENT: CMD 'status 2' Mar 13 16:22:34 openvpn 42217 MANAGEMENT: CMD 'state 1' Mar 13 16:22:34 openvpn 42217 MANAGEMENT: Client connected from /var/etc/openvpn/client1/sock Mar 13 16:22:34 openvpn 42217 MANAGEMENT: Client disconnected Mar 13 16:22:34 openvpn 42217 MANAGEMENT: CMD 'status 2' Mar 13 16:22:34 openvpn 42217 MANAGEMENT: CMD 'state 1' Mar 13 16:22:34 openvpn 42217 MANAGEMENT: Client connected from /var/etc/openvpn/client1/sock Mar 13 16:17:29 openvpn 42217 Control Channel: TLSv1.3, cipher TLSv1.3 TLS_AES_256_GCM_SHA384, peer certificate: 4096 bit RSA, signature: RSA-SHA512 Mar 13 16:17:29 openvpn 42217 Incoming Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key Mar 13 16:17:29 openvpn 42217 Outgoing Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key Mar 13 16:17:29 openvpn 42217 WARNING: 'comp-lzo' is present in remote config but missing in local config, remote='comp-lzo' Mar 13 16:17:29 openvpn 42217 WARNING: 'link-mtu' is used inconsistently, local='link-mtu 1633', remote='link-mtu 1634' Mar 13 16:17:27 openvpn 42217 VERIFY OK: depth=0, CN=xxxxxxx.nordvpn.com Mar 13 16:17:27 openvpn 42217 VERIFY EKU OK Mar 13 16:17:27 openvpn 42217 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication Mar 13 16:17:27 openvpn 42217 Validating certificate extended key usage Mar 13 16:17:27 openvpn 42217 VERIFY KU OKNow I am looking for guidance and help with these issues.
Is the issue with my config, the VPN provider or pfsense itself (openvp service, etc)...?
-
OK I have finally found the issue and how to fix but its creating a major issue.
Under System > Routing, I changed the default IPV4 gateway to "NORDVPN" and now everything seems to be working as intended only on my VLANs that have to go thru the VPN, but traffic on the other VLANs cannot reach the web.
Most errors seems to be based on DNS resolution. I have specified DNS servers on the DHCP server of these VLANs so they can get DNS resolution and bypass Unbound and their FW rules are pretty much open and have "*" as gateway.
Do I need to do something special for the VLAN's that do not have to go thru the VPN?
-
-
@bob-dig
Just to be clear:
System > Routing > Default Gateway=my ISP -> VLAN's to be behind VPN are DNS leaky, VLAN to be excluded from VPN works normally.
System > Routing > Default Gateway=NordVPN -> VLAN's to be behind VPN are working normally, VLAN to be excluded from VPN works normally
That's why I switched the default gateway under System>Routing...
For the FW rules, the pass rules for the VLAN's to be behind VPN have their gateway = NordVPN, and for the pass rules of the VLAN to be excluded from VPN, gateway = *
Not sure what I'm / have been doing wrong..... It make sense to me and should work. Traffic from VLAN's to be behind VPN is matching a pass rule with gateway = NordVPN, traffic is passed to a matching NAT rule which forwards traffic to NordVPN.
Why is it leaking in the first place? FYI my rules for the leaky VLAN's are in one of my previous posts on this thread. Do you spot anything wrong?
EDIT: I forgot to mention: the DHCP server of the VLAN's to be behind VPN have NO DNS servers specified. I relied on the tooltip saying that if no DNS are specified, the interface's IP will be used for DNS resolving:
Leave blank to use the system default DNS servers: this interface's IP if DNS Forwarder or Resolver is enabled, otherwise the servers configured on the System / General Setup page.
-
@pftdm007 said in NordVPN setup on pfsense - questions about basics:
EDIT: I forgot to mention: the DHCP server of the VLAN's to be behind VPN have NO DNS servers specified. I relied on the tooltip saying that if no DNS are specified, the interface's IP will be used for DNS resolving:
I would do it the other way around, don't use unbound for the VPN-VLANs, they should use external DNS and use unbound only for the non VPN-VLANs.
-
@bob-dig
Hey there, I use DNSBL and pfblocker on the VLAN's behind VPN. The VLAN to be excluded of VPN is a DMZ thats why I dont use Unbound on it and pass cloudflare DNS servers directly to its clients.
But using Unbound should it matter?
The way I see it: Client asks for DNS resolution from the VLAN interface > Unbound gets the query > Forwarding mode is enabled, so the request is passed to the DNS servers under System > General Setup which are Nord's DNS servers.
-
@pftdm007 Those servers can be awful. But it is all a matter of priorities. Because unbound is centralized in pfSense, there is only one, you have to watch closely for DNS leakage. I myself prioritize the non-vpn traffic, DNS resolution etc. and don't use DNSBL on those vpn-hosts, they just get 8.8.8.8 as their DNS and it is done.
-
@bob-dig
I was wrong, I'm using OpenDNS not cloudflare..... but thats outside of the point of this thread
I take that what I want to do, pfsense cant do it?
-
@pftdm007 said in NordVPN setup on pfsense - questions about basics:
I take that what I want to do, pfsense cant do it?
This thread is long already, so what is it, what you want to do?
-
@bob-dig
Its simple: If pfsense's default gateway is set to "default", pfsense DNS LEAKS on the VLAN's behind VPN. This is why I switched the default gateway to NordVPN (which you explicitely told me not to do). When the default gateway is switched to NORDVPN, DNS leakage stops.
From posts above:
Default Gateway=my ISP -> VLAN's to be behind VPN are DNS leaky, VLAN to be excluded from VPN works normally.
Default Gateway=NordVPN -> VLAN's to be behind VPN are working normally, VLAN to be excluded from VPN works normallyWhat's the problem with switching the default gateway to NordVPN?
FYI (and for others), issues before post starting with
OK I have finally found the issue and how to fix but its creating a major issue.
have been resolved for the most part. Now I am just trying to use the default gateway without pfsense leaking.... In other words I'm trying to understand why following Nord's instructions are not working with VLAN's.
-
@pftdm007 It has nothing to do with VLANs. I think in the nord tutorial, they are using only their dns servers for everything. You can do this, make them the only ones under General Setup and Enable Forwarding Mode in the resolver, no more leakage. But again, now you are using them for everything.
-
@Bob-Dig
Please look at my previous posts (I know this thread is getting long...)
FW mode is already enabled in Unbound, and Nord's DNS servers are already set in General Setup. This is leaking. The only thing I found to stop the "leakage" is to change the default gateway
@pftdm007 said in NordVPN setup on pfsense - questions about basics:
The way I see it: Client asks for DNS resolution from the VLAN interface > Unbound gets the query > Forwarding mode is enabled, so the request is passed to the DNS servers under System > General Setup which are Nord's DNS servers.
-
@pftdm007 said in NordVPN setup on pfsense - questions about basics:
FW mode is already enabled in Unbound, and Nord's DNS servers are already set in General Setup. This is leaking.
Who says that it is leaking, a leaking testsite? Would be curious to know about the exact results.
Also you should create this alias I told you and make more general rules with that instead of doing it on a per port basis.