Can't get pfBlockerNG to block pornhub.com
-
New pfBlockerNG user. Latest version. Got things mostly working. Using Shallalist and UT1 Summary to block Adult and Porn and Gambling categories. 1bet.com gets blocked but pornhub.com does not. And the crazy thing is that I can ping pornhub.com and it resolves to 10.10.10.1!!!! WTF? How is that possible?
It's the same as the DNSBL Webserver Configuration Virtual IP Address. Not really sure what that's for. Yes, noob here.
porthub.wine resolves to 104. 21.28.246.
Help :(
-
@fullauto What does dig or nslookup say? It could be getting cached by your OS. (in Windows, ipconfig /flushdns)
-
Dnsbl wildcard block enabled?
Like *pornhub.comState killed from your device before each test?
The nasty thing is sometimes only a reboot of both devices pfS and test device helps to get a clear lookBrNP
-
Have a look at DoH on client side if you block only the DNS resolution it will not work.
-
Its a shame.... its a good site with a lot of valuable info.
-
@cool_corona
Yeah and I guess it's running on nginx -
Yeah that might kill the idea of blocking a request
-
@noplan
No, do it right!Use pfBlocker to block DoH Server, Block Apple DNS.
Use a NAT Roule to mode DNS to your pfSense.
Block DNSSEC for clients. -
-
i do that easily. I have Wildcard Blocking (TLD) enabled.
I create my own blacklist and I put pornhub.com
Reload all and that's it...Blocked.
I do no blocking of DoH or DoT. As long as the clients are pointing to the firewall for DNS you are good. Additional you can use NAT reflection to make sure any DNS query outside of port 53 get redirected to the firewall.The other method would be to grab a Steven Blacklist for Porn and use that but the way I prefer to handle things and the way I have things configured is that I block all porn and I have a custom black list where I add additional sites.
I also have custom Unbound configuration where I select certain /32s or /24s that are exempt from the DNSBL. -
Try blocking it using the ASN.
Create a custom feed under IP->IPv4 use the ASNAS29789
ASN found by pinging pornhub.com and doing an IP lookup on https://iplocation.io/
scroll to the middle'ish of th results to find the AS number.don't forget to assign the alias to a firewall rule.
-
@1of1000quadrillion said in Can't get pfBlockerNG to block pornhub.com:
AS29789
ASN blocking is dangerous. Unless its an ASN wholly owned by the public entity (facebook,google,nextlix) then you are just blackholing lots of sites. Blast radius is way to much with that technique.
-
-
@fullauto I suspect a DNS leak. I've seen this behavior as I didn't lock DNS to my specific server.
If you're using Windows with Edge, Edge actually has a feature that was allowing it to resolve URL's that shouldn't have worked, based on my DNS config. I.e. they resolved fine in command line (no flush needed) but not in Edge.
-
Have you tried regular expressions for the URL?
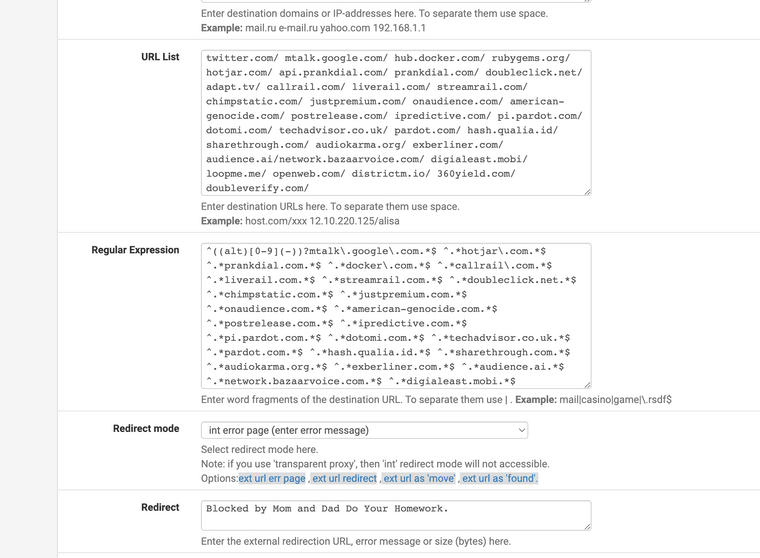
(Image: Most of my blocks are for learning purposes and for my research with my degree)
I don't like prankdial, hotjar, rubygems, docker, and some other ones that seemed to cause me some issues. I am sure a lot of mine do not need to be blocked, but how can you learn if you don't test stuff out? Here is an example.
I always have had issues with Doubleclick.net they caused me so many issues with devices and human interaction with mouse and keyboards, I found all my items work better with them blocked. Notice ^.URL.com.$ try that.
Also check your Target rules if they are whitelisted it will override items by order like ACLs.
Also enable encrypted DNS
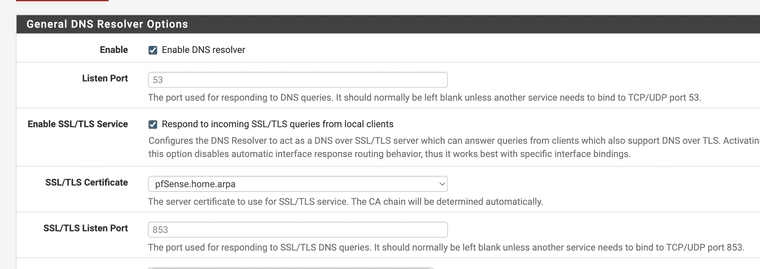
If the DNS is encrypted and using SSL it can't be hijacked, I would cry if they hijacked the update servers.
-
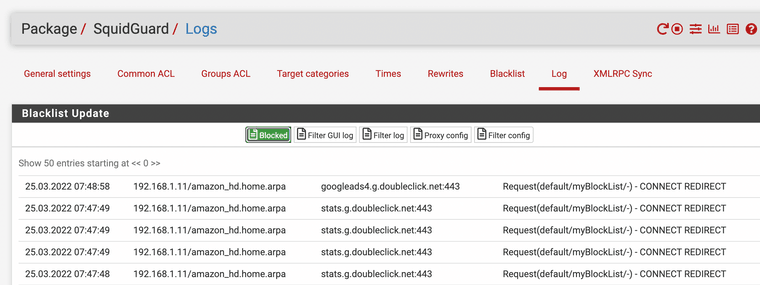
You can see it blocking all the variations of doubleclick.net now, it does not matter what differences are in the URL if the main part is the same it blocks it forever.
-
I have read through this thread but still unclear as to what the resolution would be. I too would like to block sites such as facebook, tik-tok, etc and thought I had it licked by creating a custom list in DNSBL but the sites are not getting blocked. I have squid installed but not running as I had some issues in the past where it locked up the system which I think were related to bad memory which I have resolved. I am new to this and still getting my feet wet so would like to get clarity on how to accomplish this. I am sure this has been talked about quite a bit so if there is a thread or instruction that covers the topic feel free to post the link and I will give it a shot. Thank you.
-
@lpd7 Can you provide details? nslookup results, etc. Are you blocking DoH? If not most browsers will bypass the configured DNS servers. Did you run an update in pfBlocker after changing settings?
-
@steveits said in Can't get pfBlockerNG to block pornhub.com:
@lpd7 Can you provide details? nslookup results, etc. Are you blocking DoH? If not most browsers will bypass the configured DNS servers. Did you run an update in pfBlocker after changing settings?
New to pFS and pFB so bear with me as I track down the info and educate myself as well.
Not sure which nslookup results you want to see so please elaborate, happy to provide.
Yes blocking DoH
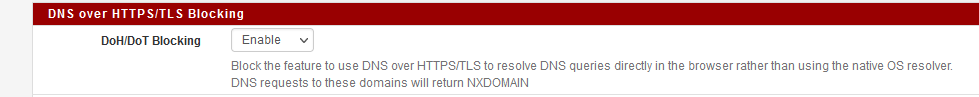
and selected all options in the blocking list
I usually run Cron after making changes but ran the Update twice just to make sure.
-
I don't know if this helps, I use Squidguard as it is designed for use with Squid Proxy. Here is some photos of it in action.
I feel this system should be simplified for parents and have scripts created to make this install with ease. You must have static addresses to make this work correctly. So it should have a quick install where you manually connect each device so it can auto populate the static addresses.
After it should create your certificates for you and let you install them.
After it should walk you threw how to set up WPAD this is a must for auto proxy use.
https://docs.netgate.com/pfsense/en/latest/recipes/http-client-proxy-wpad.html
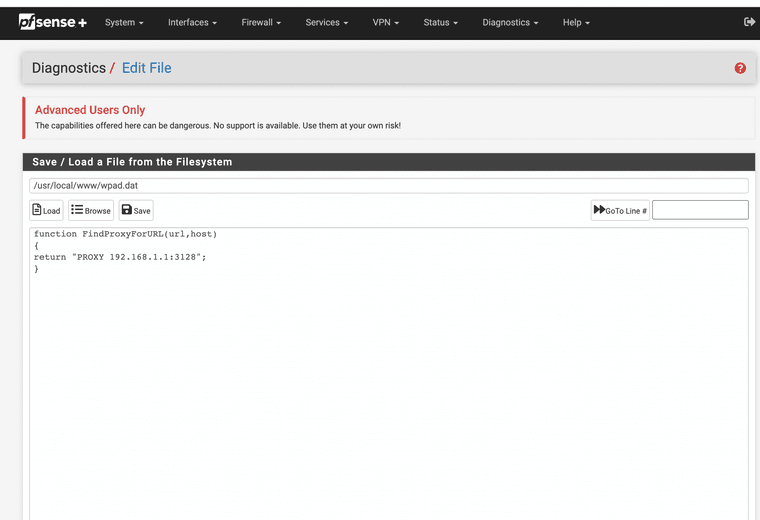
Just edit a path to the file and save it. This is needed for use with windows and other devices to find the proxy automatically.
Next you need your websites you want blocked. Example of how it works for me.
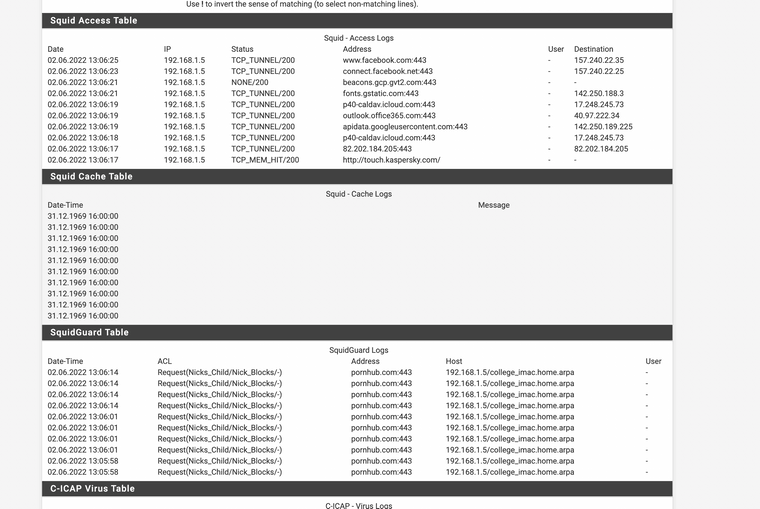
(Image: Url Blocker working under Squidguard Table)
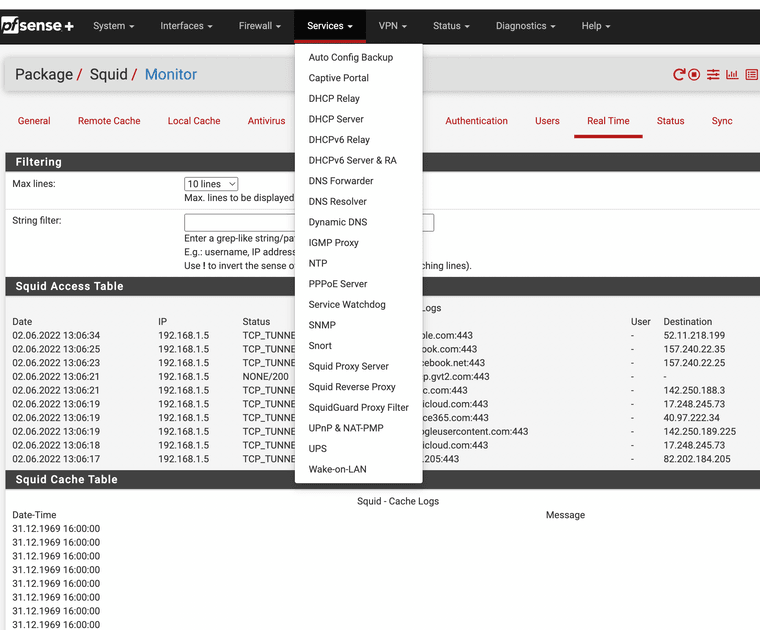
(Image: Once package is installed use SquidGuard Proxy Filter)
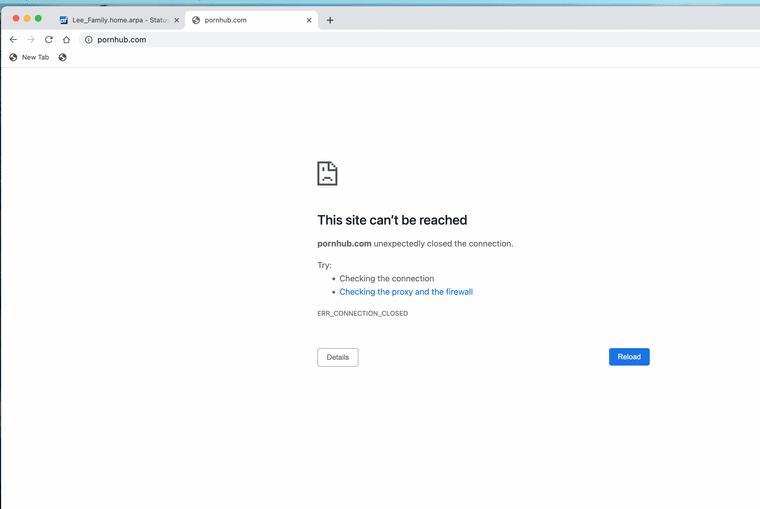
(Image: What happens when the URL is tested)
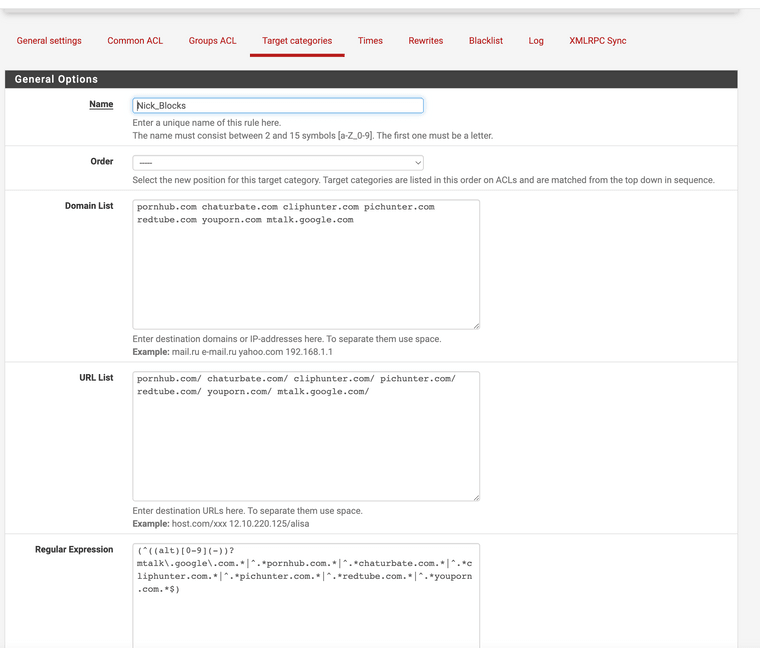
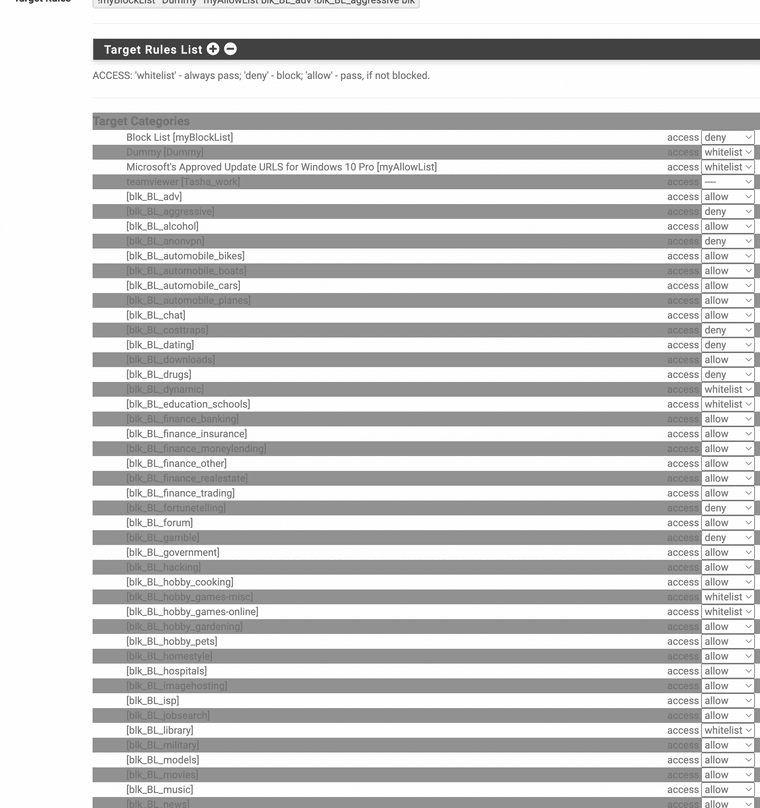
(Image: Target Categories)
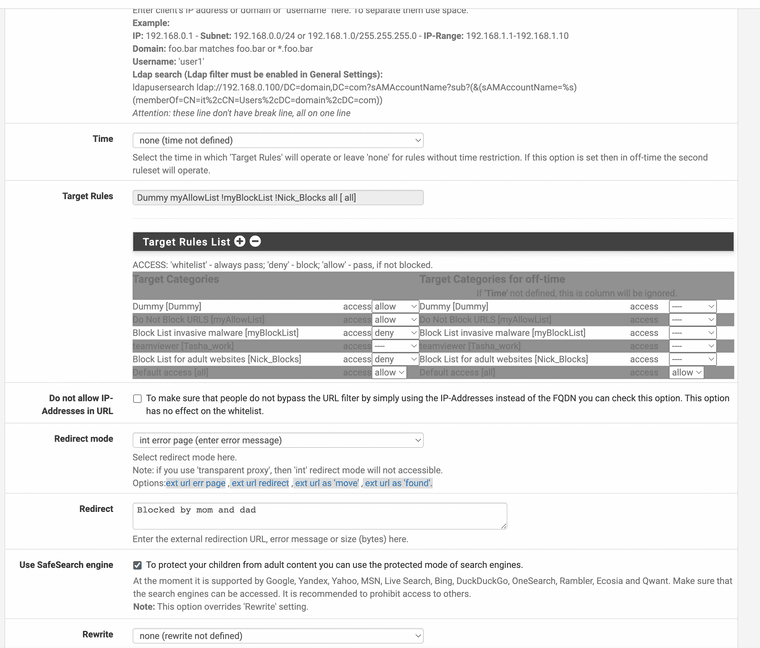
(Make a Profile and attach the IP addresses of the system you want blocked for adult websites, you must also have a dummy profile for it to work that takes the place of position one)
A nice how to guide I have found to get this system to work.
Configure pfSense as HTTPS \ SSL Proxy filter using Squid and SquidGuard! (n.d.). Retrieved June 2, 2022, from https://forum.it-monkey.net/index.php?topic=23.0
Make sure you let the loopback and local subnets use the proxy
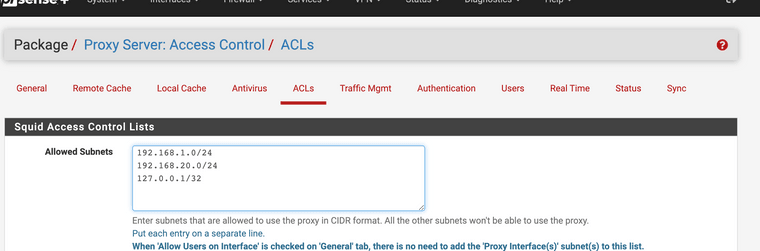
This all works with the HTTP get requests and headers. So no harm done. It is so simple however I worked in IT for over 15 combined years. Yes this needs to be simple for the average Parent and it can be done. There is some great guides for this version, and I for one use it and it blocks what you want blocked. You can even set up timers for no access in the middle of the night.
Do not forget you must set up your access control lists. This is the packet filter that uses ports and IP addresses also.
This is mine.
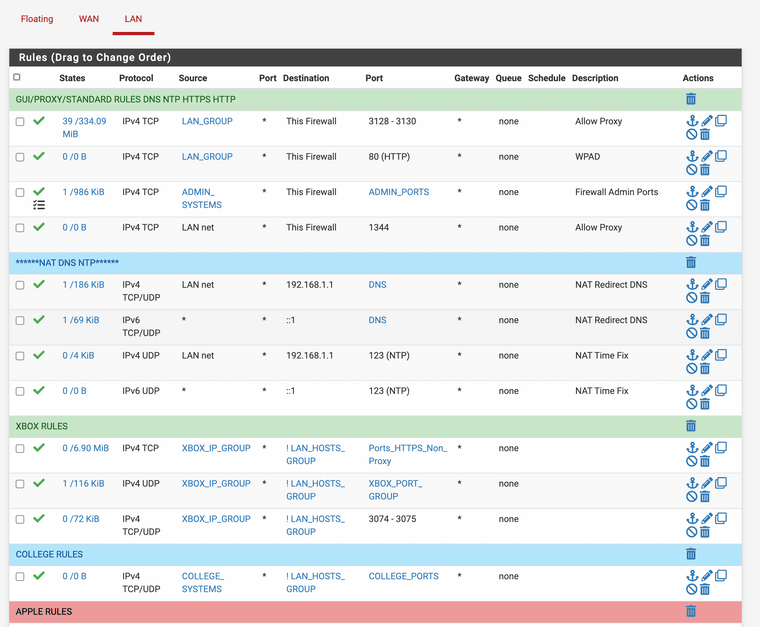
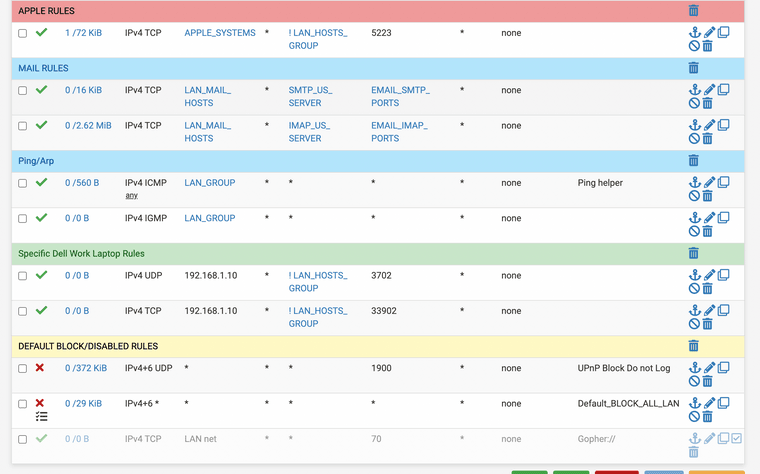
(image: ACLS)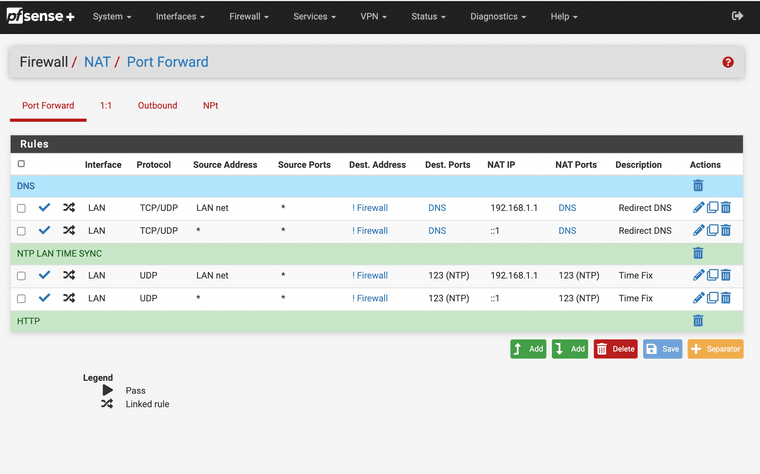
(image: NAT Port Forwards for DNS and NTP so the firewall handles all requests)